Cross-chain bridges have emerged as the critical infrastructure connecting the fragmented landscape of blockchain networks, enabling seamless asset transfers and communication between different blockchain ecosystems that would otherwise remain isolated. These sophisticated technological solutions address one of the most fundamental challenges in the cryptocurrency space: the lack of native interoperability between blockchain networks, which has historically limited the potential for a truly interconnected decentralized economy.
The proliferation of blockchain networks has created a multi-chain universe where each network offers unique advantages in terms of security, scalability, transaction costs, and specialized functionality. However, this diversity has also resulted in significant fragmentation, with valuable assets and applications locked within individual blockchain silos. Cross-chain bridges serve as the connective tissue that binds these disparate networks together, facilitating the movement of tokens, data, and even smart contract functionality across blockchain boundaries.
Understanding cross-chain bridge technology requires examining the fundamental architectural challenges of blockchain interoperability, the various technical approaches to solving these challenges, and the evolving landscape of bridge implementations that range from simple token transfer mechanisms to sophisticated protocols enabling complex cross-chain interactions. The importance of these systems extends beyond mere asset transfers to encompass the broader vision of a unified blockchain ecosystem where users can seamlessly interact with applications and services regardless of the underlying blockchain infrastructure.
As the blockchain ecosystem continues to mature and diversify, the role of cross-chain bridges becomes increasingly critical to the realization of Web3’s promise of a decentralized, interconnected digital economy. These systems enable developers to build applications that leverage the unique strengths of multiple blockchain networks while providing users with the flexibility to choose optimal networks for different types of transactions and interactions without being constrained by network-specific limitations.
The Architecture of Blockchain Interoperability
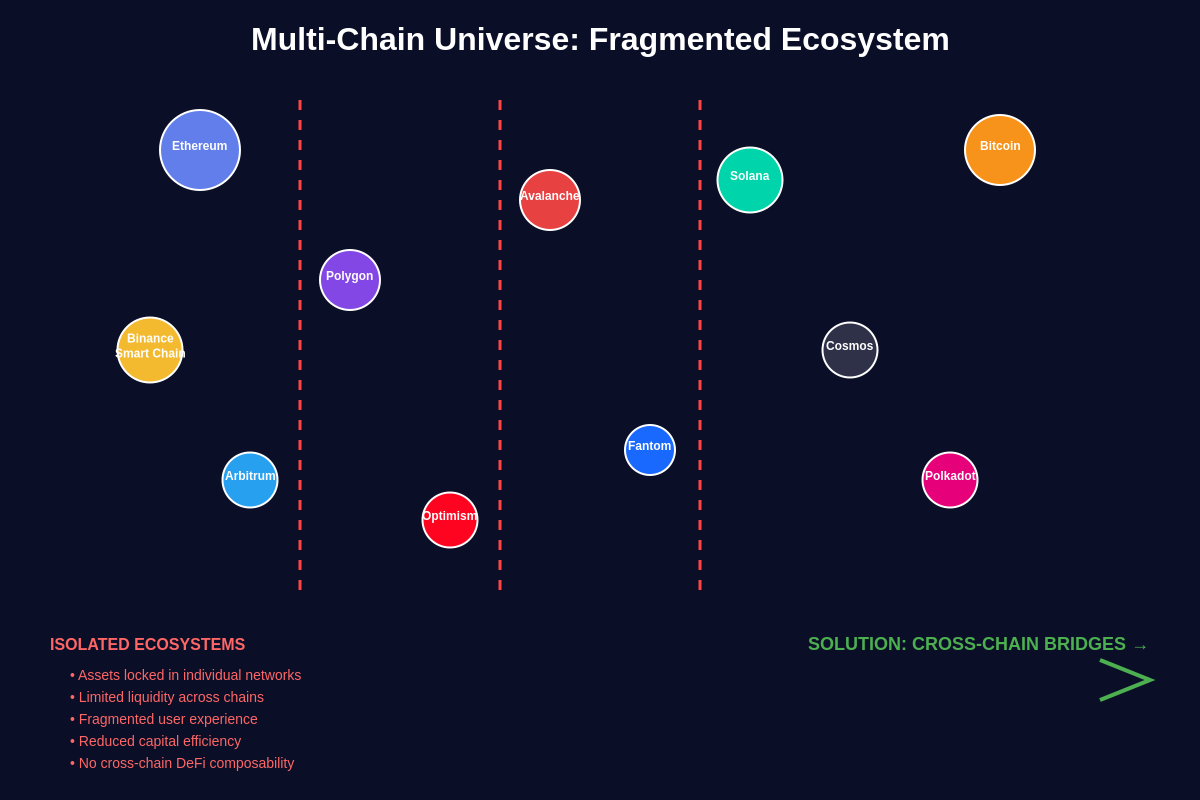
Cross-chain bridge architecture represents one of the most complex challenges in blockchain technology, requiring sophisticated solutions to enable communication and asset transfers between networks that were designed to operate independently. The fundamental architecture of these bridges involves multiple components working in coordination to validate transactions on one blockchain, lock or burn assets as appropriate, and mint or release corresponding assets on the destination blockchain while maintaining security and preventing double-spending attacks.
The core architectural challenge stems from the fact that blockchain networks operate as isolated systems with their own consensus mechanisms, cryptographic standards, and data structures. When designing a cross-chain bridge, developers must create a system that can reliably read the state of multiple blockchains, validate transactions according to each network’s specific rules, and coordinate asset movements without compromising the security guarantees of either network.
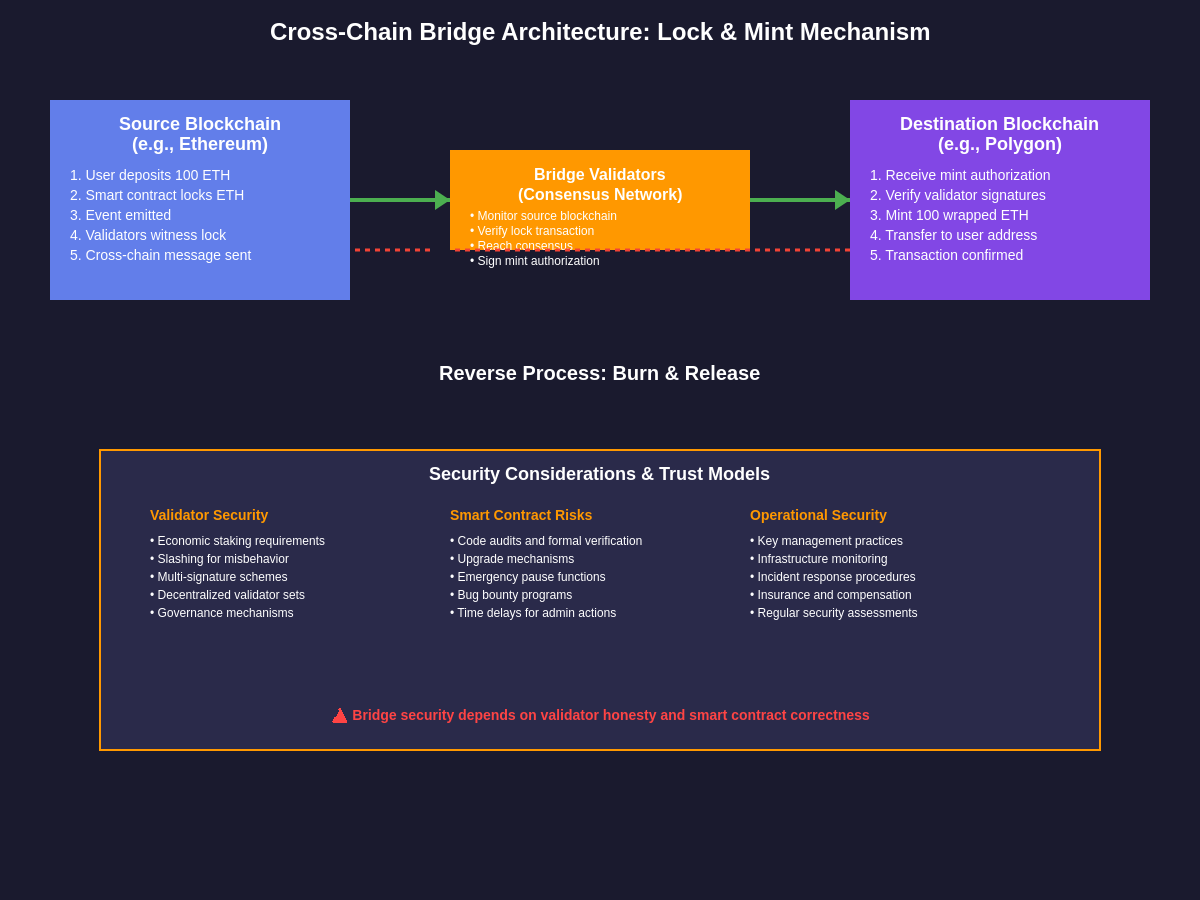
Traditional bridge architectures typically employ a lock-and-mint mechanism where assets are locked in a smart contract on the source blockchain while corresponding wrapped tokens are minted on the destination blockchain. This approach requires sophisticated validation mechanisms to ensure that tokens are only minted when assets are properly locked, and that the total supply of wrapped tokens never exceeds the amount of locked assets. The complexity increases significantly when supporting bidirectional transfers and multiple asset types across numerous blockchain networks.
Advanced bridge architectures are exploring more sophisticated approaches including atomic swaps, which enable direct peer-to-peer exchanges without requiring trusted intermediaries, and state channel solutions that can facilitate high-frequency cross-chain interactions with minimal on-chain overhead. These approaches offer different trade-offs in terms of security, scalability, and implementation complexity, with the optimal choice depending on the specific use case and performance requirements.
The emergence of purpose-built interoperability protocols represents a significant evolution in bridge architecture, with projects developing specialized blockchain networks designed specifically to facilitate cross-chain communication. These protocols often implement novel consensus mechanisms optimized for validating cross-chain transactions and maintaining security across multiple connected networks, representing a fundamental shift from ad-hoc bridge solutions to comprehensive interoperability infrastructure.
Understanding Cross-Chain Bridge Architecture

The fundamental architecture of cross-chain bridges involves complex cryptographic and economic mechanisms designed to ensure the secure and reliable transfer of assets between blockchain networks that operate under different consensus mechanisms, security models, and technical specifications. At its core, a cross-chain bridge must solve the challenge of creating trust and verification between networks that have no native awareness of each other’s state or transactions.
The most common implementation involves a lock-and-mint mechanism where assets are locked in a smart contract on the source blockchain while equivalent wrapped tokens are minted on the destination blockchain. This process requires sophisticated verification systems that can monitor the state of the source blockchain, confirm that assets have been properly locked, and trigger the minting process on the destination network. The reverse process, known as burn-and-release, involves destroying the wrapped tokens on the destination blockchain while releasing the original assets from the lock contract on the source blockchain.
Validator networks play a crucial role in most bridge architectures, serving as the trusted entities responsible for monitoring cross-chain transactions and facilitating the transfer process. These validators must stake significant amounts of capital as collateral, creating economic incentives for honest behavior while establishing penalties for malicious actions. The security of the entire bridge system depends heavily on the integrity and reliability of these validator networks, making their selection, governance, and operation critical factors in bridge design and implementation.
Types of Cross-Chain Bridge Solutions
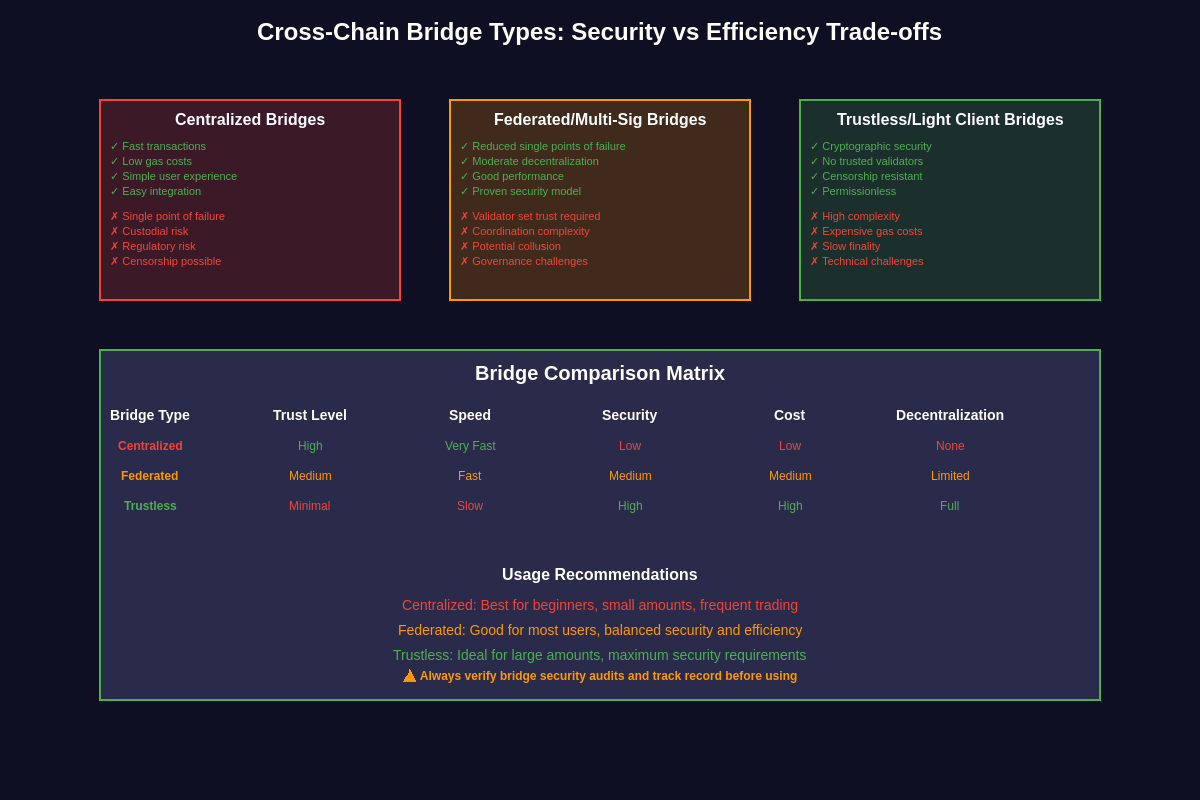
The cross-chain bridge landscape encompasses several distinct architectural approaches, each offering different trade-offs between security, decentralization, speed, and cost. Understanding these various approaches is essential for users, developers, and investors seeking to navigate the complex interoperability ecosystem and make informed decisions about which solutions best meet their specific requirements.
Centralized bridges represent the simplest implementation, relying on trusted third parties to facilitate cross-chain transfers. These solutions typically offer fast transaction processing and user-friendly interfaces, making them attractive for mainstream users who prioritize convenience over decentralization. However, centralized bridges introduce significant counterparty risk, as users must trust the bridge operator to maintain custody of their assets and execute transfers honestly. This centralization also creates single points of failure that can be exploited by malicious actors or compromised by regulatory authorities.
Federated bridges attempt to balance security and efficiency by distributing trust among a consortium of validators or trusted entities. These systems reduce the single-point-of-failure risk associated with centralized bridges while maintaining relatively fast processing times and lower operational complexity compared to fully decentralized solutions. The security model relies on the assumption that a majority of federation members will remain honest, creating a multi-signature arrangement that requires consensus for cross-chain operations.
Trustless or decentralized bridges represent the most ambitious approach to cross-chain interoperability, attempting to eliminate reliance on trusted third parties through the use of cryptographic proofs, economic incentives, and consensus mechanisms. These solutions often employ techniques such as light client verification, fraud proofs, or validity proofs to verify cross-chain transactions without requiring users to trust external validators. While these approaches offer the highest level of security and decentralization, they typically involve greater complexity, higher costs, and longer transaction finalization times.
Major Cross-Chain Bridge Protocols
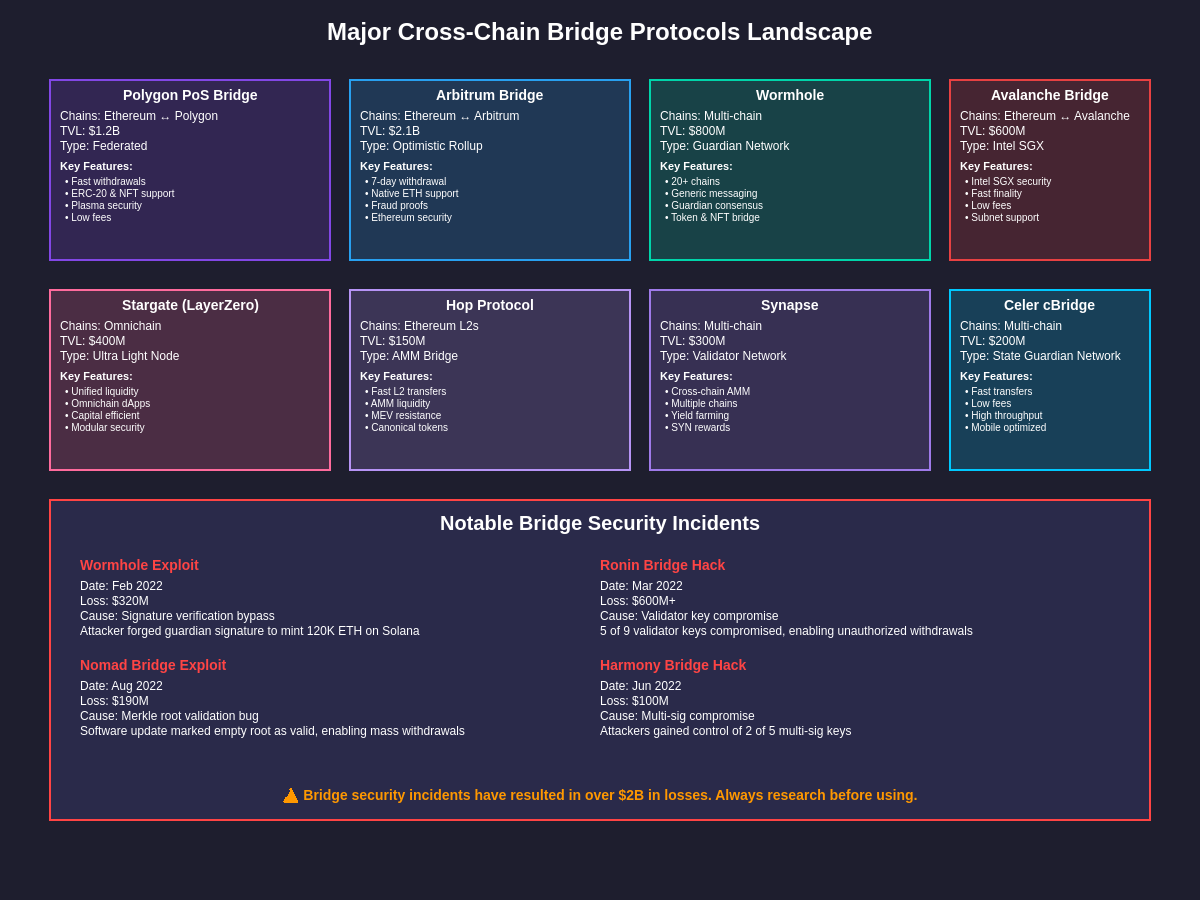
The cross-chain bridge ecosystem features numerous protocols, each implementing different approaches to solving the interoperability challenge while targeting specific use cases, blockchain networks, and user requirements. Professional traders monitoring cross-chain protocol performance and bridge token prices should understand the fundamental differences between these protocols as they directly impact security, efficiency, and long-term viability.
Polygon PoS Bridge stands as one of the most established and widely-used bridge solutions, facilitating asset transfers between Ethereum and Polygon’s proof-of-stake sidechain. The protocol employs a validator-based consensus mechanism where a set of validators stake MATIC tokens and collectively manage the bridge operations. Users can deposit assets on Ethereum, which are then locked in bridge contracts while equivalent amounts are minted on Polygon, enabling faster and cheaper transactions while maintaining exposure to Ethereum-based assets. The bridge supports various asset types including ETH, ERC-20 tokens, and NFTs, making it a comprehensive solution for cross-chain asset management.
Arbitrum Bridge represents a different approach to cross-chain connectivity, focusing specifically on the transfer of assets between Ethereum and Arbitrum’s optimistic rollup layer-2 solution. Rather than connecting to external blockchain networks, this bridge enables users to move assets between Ethereum’s main layer and Arbitrum’s scaling solution, effectively providing a pathway for leveraging Ethereum’s security while benefiting from improved transaction throughput and reduced costs. The bridge utilizes optimistic verification mechanisms and challenge periods to ensure transaction validity while minimizing trust assumptions.
Avalanche Bridge facilitates interoperability between Ethereum and Avalanche’s C-Chain, enabling users to move ERC-20 tokens and ETH between these networks. The protocol employs a unique architecture that combines centralized operation with decentralized verification, using Avalanche’s subnet technology to create a dedicated blockchain for bridge operations. This approach allows for fast transaction processing while maintaining security through Avalanche’s consensus mechanism and the ability for users to verify bridge operations independently.
Wormhole has established itself as one of the most comprehensive cross-chain messaging protocols, supporting asset transfers and arbitrary message passing between multiple blockchain networks including Ethereum, Solana, Terra, Binance Smart Chain, and others. The protocol employs a network of guardians who validate cross-chain messages and facilitate transfers, creating a unified interface for cross-chain operations across diverse blockchain ecosystems. Wormhole’s support for both asset transfers and general message passing makes it particularly valuable for complex cross-chain applications that require more than simple token transfers.
Security Models and Trust Assumptions
The security of cross-chain bridges represents one of the most critical and complex aspects of their design, as these protocols must maintain the integrity of assets and transactions across networks with fundamentally different security models, consensus mechanisms, and trust assumptions. Understanding these security considerations is essential for users seeking to minimize risk while leveraging cross-chain functionality, as bridge vulnerabilities have historically resulted in some of the largest losses in the DeFi ecosystem.
External validation represents one of the most common security models employed by cross-chain bridges, where a set of validators or guardians are responsible for monitoring cross-chain transactions and facilitating transfers. The security of this model depends entirely on the integrity of the validator set, the economic incentives that ensure honest behavior, and the mechanisms in place to detect and penalize malicious actions. Users must trust that a majority of validators will remain honest and that the economic penalties for dishonest behavior exceed the potential rewards for attacks.
Light client verification offers a more trustless approach to cross-chain security by enabling bridges to verify the state of remote blockchains without relying on external validators. This method involves implementing simplified payment verification clients that can process block headers and merkle proofs to confirm the inclusion of specific transactions in remote blockchain networks. While this approach significantly reduces trust assumptions, it also introduces complexity and computational overhead that can impact bridge performance and cost-effectiveness.
Optimistic verification models assume that cross-chain transactions are valid by default while providing mechanisms for users to challenge invalid transactions within a specified time window. This approach enables faster transaction processing and lower costs while maintaining security through economic incentives that make fraudulent transactions economically unviable. However, optimistic models introduce withdrawal delays that can impact user experience and capital efficiency, as users must wait for challenge periods to expire before accessing their transferred assets.
Economic security represents a fundamental component of all bridge security models, as the value secured by a bridge cannot safely exceed the economic cost of attacking it. This relationship creates important limitations on bridge capacity and highlights the importance of robust tokenomics, slashing mechanisms, and insurance funds that can compensate users in the event of bridge failures or attacks. Investors analyzing bridge protocol tokens and their market dynamics should carefully evaluate these economic security models when assessing investment opportunities.
Technical Implementation Challenges
The implementation of cross-chain bridges involves numerous technical challenges that span cryptography, distributed systems, blockchain technology, and user experience design. These challenges must be addressed to create bridges that are secure, efficient, scalable, and accessible to both technical and non-technical users seeking to leverage cross-chain functionality.
State verification across different blockchain networks presents one of the most fundamental technical challenges in bridge development, as each network operates under different consensus mechanisms, block structures, and state representation formats. Bridges must implement sophisticated verification systems that can understand and validate the state of multiple blockchain networks while ensuring that verification processes cannot be compromised or manipulated by malicious actors.
Finality differences between blockchain networks create significant complexity for bridge operations, as networks achieve transaction finality at different speeds and through different mechanisms. Proof-of-work networks like Bitcoin and Ethereum (pre-merge) require multiple block confirmations to achieve probabilistic finality, while proof-of-stake networks can achieve deterministic finality more quickly. Bridges must account for these differences to ensure that cross-chain transfers are not vulnerable to reorganizations or finality reversions that could compromise transaction integrity.
Network congestion and variable transaction costs on different blockchain networks create operational challenges for bridge protocols that must maintain consistent service levels across diverse network conditions. Bridges operating between high-throughput, low-cost networks and congested, expensive networks must implement dynamic fee mechanisms and transaction optimization strategies to remain economically viable while providing acceptable user experiences.
Smart contract risk represents a significant implementation challenge, as bridge contracts must handle complex logic for asset locking, validation, and release while remaining secure against various attack vectors including reentrancy, front-running, and flash loan exploits. The immutable nature of smart contracts means that bugs or vulnerabilities discovered after deployment can result in permanent loss of user funds, making thorough testing and formal verification critical components of bridge development.
Cross-Chain Bridge Security Incidents
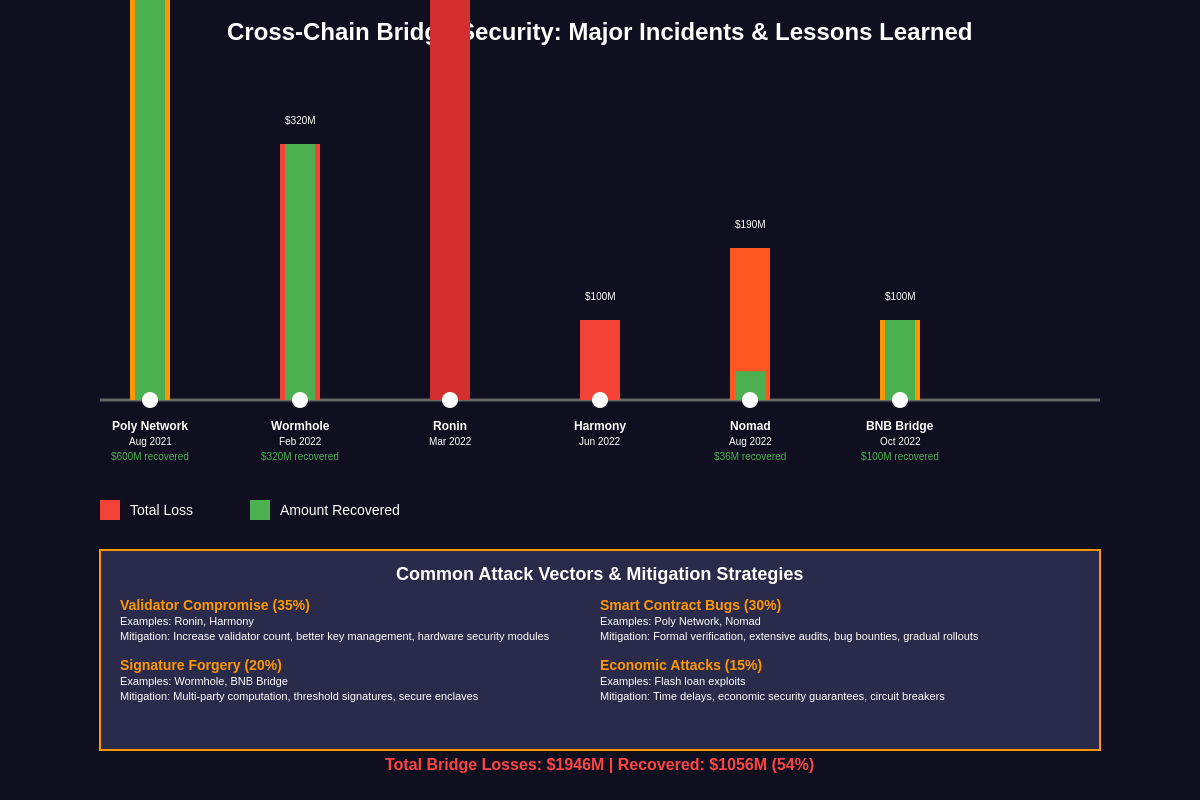
The history of cross-chain bridges is unfortunately marked by numerous high-profile security incidents that have resulted in hundreds of millions of dollars in losses and highlighted the significant risks associated with cross-chain infrastructure. These incidents provide valuable lessons about bridge security, user education, and the importance of robust security practices in the development and operation of cross-chain protocols.
The Wormhole bridge exploit in February 2022 stands as one of the most significant cross-chain security incidents to date, resulting in the loss of approximately 120,000 ETH worth over $320 million at the time of the attack. The exploit involved a sophisticated attack on the bridge’s signature verification system, where an attacker was able to forge a valid guardian signature and mint 120,000 wrapped ETH on Solana without depositing the corresponding assets on Ethereum. This incident highlighted the critical importance of secure signature schemes and the risks associated with centralized validation in bridge architectures.
The Ronin bridge hack in March 2022 demonstrated the vulnerabilities inherent in federated bridge models, as attackers compromised five of the nine validator keys required to approve transactions on the bridge connecting Ethereum to the Ronin sidechain used by the popular Axie Infinity game. The attack resulted in the theft of over $600 million in cryptocurrency, making it one of the largest DeFi exploits in history. This incident underscored the importance of validator security, key management practices, and the trade-offs between efficiency and decentralization in bridge design.
The Nomad bridge exploit in August 2022 illustrated how implementation bugs can lead to catastrophic failures in cross-chain infrastructure, as a routine software update inadvertently marked an empty merkle tree root as valid, effectively allowing anyone to withdraw funds from the bridge without proper verification. The incident quickly escalated into a chaotic free-for-all as hundreds of users copied successful withdrawal transactions, ultimately draining the bridge of nearly $200 million in assets. This event highlighted the critical importance of formal verification, comprehensive testing, and staged deployment practices in bridge development.
These incidents have collectively contributed to a more mature understanding of cross-chain security risks and have driven improvements in bridge design, security practices, and user education. Modern bridge protocols increasingly employ multiple layers of security, including time delays for large withdrawals, anomaly detection systems, and insurance mechanisms designed to protect users against various types of attacks and failures.
Emerging Technologies and Solutions
The cross-chain bridge ecosystem continues to evolve rapidly as developers explore new technologies and approaches to address the limitations and challenges of current solutions. These emerging technologies promise to improve security, reduce costs, increase speed, and enhance the overall user experience of cross-chain interactions while maintaining or improving upon existing security guarantees.
Zero-knowledge proofs represent one of the most promising technological developments for cross-chain bridge security and efficiency, as they enable bridges to verify the validity of cross-chain transactions without revealing sensitive information or requiring extensive on-chain computation. ZK-based bridges can implement light client verification more efficiently, reduce verification costs, and enable faster transaction finalization while maintaining strong security guarantees. Projects like zkBridge and Succinct Labs are pioneering the application of zero-knowledge technology to cross-chain communication, demonstrating the potential for this technology to revolutionize bridge architecture.
Rollup-based interoperability solutions leverage the security and scalability benefits of layer-2 rollup technology to create more efficient cross-chain communication protocols. These solutions can reduce the trust assumptions required for cross-chain transfers while benefiting from the security of underlying layer-1 networks like Ethereum. Optimistic and zk-rollup technologies are being adapted for cross-chain use cases, enabling faster and cheaper inter-network communication while maintaining high security standards.
Cosmos Inter-Blockchain Communication (IBC) protocol represents a fundamentally different approach to cross-chain interoperability, focusing on native cross-chain communication rather than bridging between incompatible networks. IBC enables secure and permissionless communication between blockchains built with the Cosmos SDK, creating a network of interoperable chains that can share assets and data without requiring external bridge infrastructure. This approach demonstrates the potential for designing blockchain networks with native interoperability rather than retrofitting connectivity through bridge protocols.
Shared security models, such as those implemented by Polkadot’s parachain architecture and Ethereum’s upcoming shared security initiatives, offer alternative approaches to cross-chain interoperability that eliminate many of the trust assumptions and security risks associated with traditional bridge protocols. These models enable multiple blockchain networks to share the security of a central relay chain or beacon chain, creating natural interoperability between networks without requiring complex bridge infrastructure.
Economic Models and Tokenomics
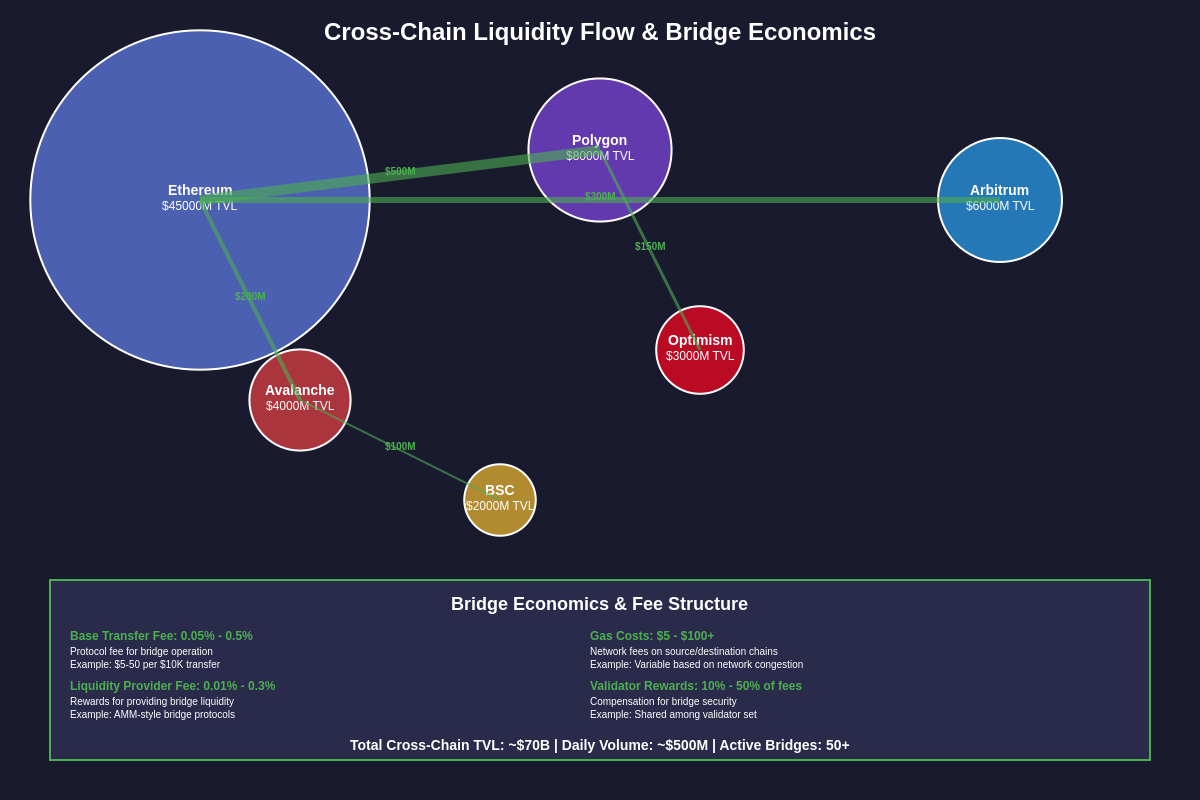
The economic design of cross-chain bridge protocols plays a crucial role in their long-term sustainability, security, and adoption, as these systems must balance the needs of users seeking efficient cross-chain transfers with the requirements of validators, liquidity providers, and other ecosystem participants who provide the infrastructure and security necessary for bridge operation.
Fee structures in cross-chain bridges typically involve multiple components including base transfer fees, gas costs for transaction execution on both source and destination networks, and potential premium fees for faster processing or enhanced security features. These fee structures must be carefully designed to ensure that bridges remain economically viable while providing competitive pricing compared to alternative cross-chain solutions. Market participants tracking multi-chain ecosystem tokens and their price movements can gain insights into the economic health and competitive positioning of different bridge protocols.
Validator incentives represent a critical component of bridge tokenomics, as these systems must attract and retain high-quality validators while ensuring that validation remains economically rational across different market conditions. Validator rewards typically come from a combination of transaction fees, protocol token emissions, and potential MEV (Maximal Extractable Value) opportunities, creating complex economic relationships that must be carefully balanced to maintain network security and decentralization.
Liquidity provision mechanisms in some bridge designs require substantial capital commitments from liquidity providers who must lock assets in bridge contracts to facilitate transfers. These providers must be compensated appropriately for the capital costs, smart contract risks, and potential impermanent loss associated with providing bridge liquidity. The design of these incentive mechanisms significantly impacts bridge capital efficiency and the cost of cross-chain transfers.
Token governance models in bridge protocols often involve native tokens that provide holders with voting rights over protocol parameters, upgrade decisions, and treasury management. These governance tokens create additional value accrual mechanisms for bridge protocols while enabling decentralized decision-making about protocol evolution and risk management. However, governance token designs must carefully balance decentralization with the need for timely decision-making in response to security threats or technical issues.
Regulatory Considerations and Compliance
The regulatory landscape surrounding cross-chain bridges presents complex challenges as these protocols often facilitate the movement of assets across different jurisdictions and may trigger various regulatory requirements related to money transmission, securities laws, and anti-money laundering compliance. Understanding these regulatory considerations is essential for bridge operators, users, and investors seeking to navigate the evolving legal environment.
Money transmission regulations in many jurisdictions may apply to cross-chain bridge operations, as these protocols facilitate the transfer of value between different networks and may be considered custodial services depending on their specific implementation. Bridge operators may need to obtain money transmitter licenses, implement compliance programs, and maintain regulatory reporting capabilities to operate legally in various jurisdictions.
Securities law implications can arise when bridge protocols issue governance tokens or reward tokens that may be considered securities under applicable regulations. The distribution, trading, and governance rights associated with these tokens must be carefully structured to comply with securities laws while maintaining the decentralized nature of bridge protocols. Recent regulatory enforcement actions and guidance have highlighted the importance of securities law compliance in DeFi protocols, including cross-chain bridges.
Anti-money laundering (AML) and know-your-customer (KYC) requirements present significant challenges for cross-chain bridge protocols, as these systems often prioritize privacy and permissionless access while regulatory authorities increasingly demand transaction monitoring and user identification capabilities. Bridge operators must balance regulatory compliance requirements with user privacy expectations and the decentralized ethos of cryptocurrency.
Cross-border regulatory coordination becomes particularly complex for cross-chain bridges that facilitate transfers between networks operating under different regulatory regimes. These protocols must navigate potentially conflicting regulatory requirements while maintaining consistent service levels and user experiences across jurisdictions.
Future Developments and Industry Trends
The cross-chain bridge industry continues to evolve rapidly as technological advances, regulatory developments, and market dynamics drive innovation and adoption across the broader blockchain ecosystem. Understanding these trends is crucial for stakeholders seeking to position themselves strategically in the expanding interoperability market.
Standardization efforts across the industry are beginning to emerge as bridge protocols seek to improve compatibility, reduce integration costs, and enhance security through shared standards and best practices. Organizations like the Interchain Foundation and various blockchain industry groups are working to develop common protocols, security frameworks, and technical standards that could significantly improve the interoperability landscape.
Integration with traditional financial infrastructure represents a significant opportunity for cross-chain bridge protocols, as banks, payment processors, and other financial institutions explore blockchain technology for various use cases. Bridges that can facilitate seamless integration between public blockchains and permissioned financial networks may capture substantial value from this convergence of traditional and decentralized finance.
Artificial intelligence and machine learning technologies are increasingly being integrated into bridge protocols to improve security monitoring, anomaly detection, and risk management capabilities. These technologies can help identify suspicious transaction patterns, optimize fee structures, and enhance the overall security posture of cross-chain infrastructure.
Multi-chain wallet integration and user experience improvements continue to drive bridge adoption, as wallet providers and DeFi platforms seek to abstract away the complexity of cross-chain interactions for end users. Seamless cross-chain functionality integrated directly into wallet interfaces and DeFi applications represents a key driver of mainstream adoption for bridge technology.
The development of intent-based architectures and account abstraction technologies promises to further simplify cross-chain interactions by enabling users to express their desired outcomes without needing to understand the underlying technical complexity of cross-chain transfers. These technologies could significantly reduce the barriers to entry for cross-chain DeFi participation.
Investment Opportunities and Risk Assessment
The cross-chain bridge sector presents numerous investment opportunities across different risk profiles, from established bridge protocols with proven track records to emerging technologies that could reshape the interoperability landscape. Professional investors utilizing comprehensive DeFi analytics and cross-chain metrics can identify promising opportunities while managing the inherent risks associated with this rapidly evolving sector.
Protocol token investments offer direct exposure to bridge protocol success through governance tokens that may accrue value from fee generation, network growth, and ecosystem development. However, these investments carry significant risks including smart contract vulnerabilities, regulatory uncertainty, and intense competition from alternative interoperability solutions. Investors must carefully evaluate tokenomics, technical security, team credentials, and competitive positioning when considering protocol token investments.
Infrastructure plays represent indirect exposure to cross-chain bridge growth through investments in validators, node operators, and service providers that support bridge networks. These opportunities may offer more stable returns compared to protocol tokens while benefiting from the overall growth of cross-chain activity, though they require technical expertise and operational capabilities that may not be suitable for all investors.
Ecosystem investments in applications, wallets, and services built on top of cross-chain infrastructure can provide exposure to bridge adoption without direct exposure to bridge protocol risks. As cross-chain functionality becomes more integrated into DeFi applications and wallet interfaces, companies providing these services may benefit from increased user adoption and transaction volume.
Risk management in bridge investments requires careful consideration of technical risks, regulatory risks, competitive risks, and market risks that can significantly impact investment outcomes. The history of bridge exploits and failures highlights the importance of thorough due diligence, diversification across multiple protocols, and careful position sizing when investing in this sector.
Building the Interoperable Future
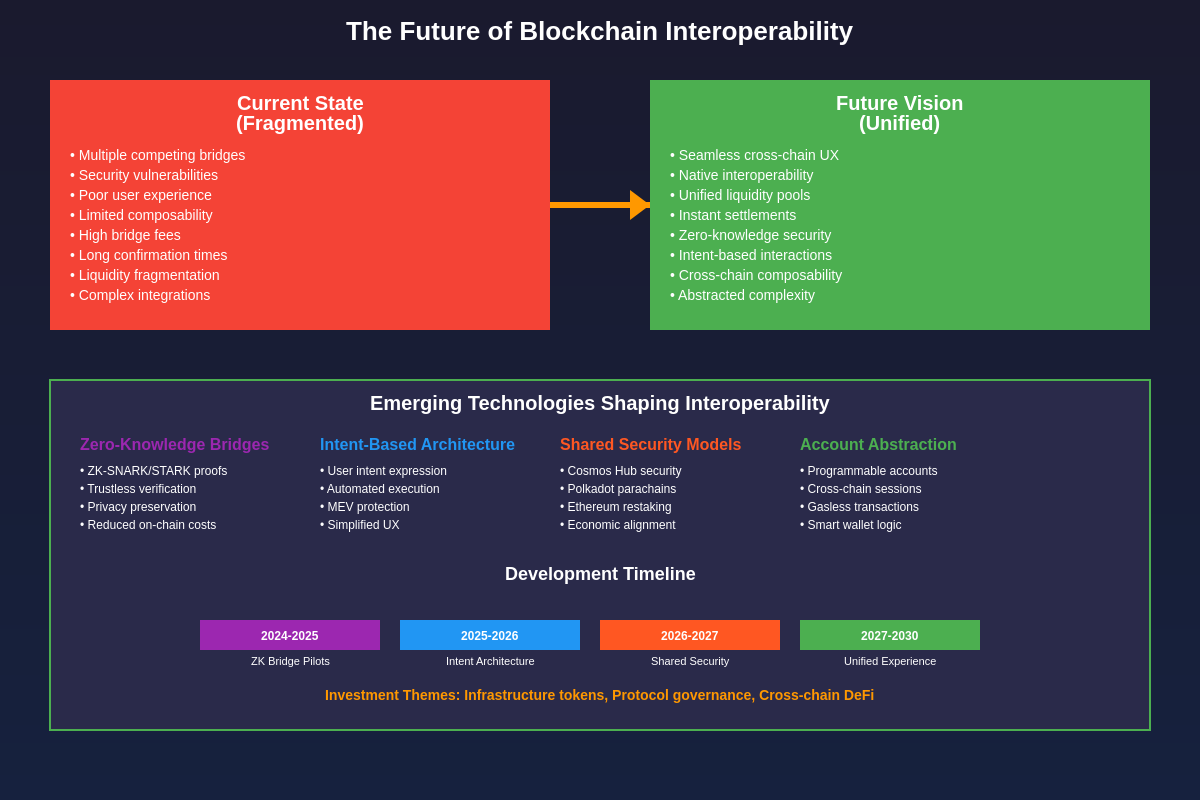
Cross-chain bridges represent far more than technical solutions to blockchain connectivity challenges; they embody the fundamental vision of a unified, interoperable blockchain ecosystem where users can seamlessly access the full spectrum of decentralized applications, financial services, and digital assets regardless of their underlying network infrastructure. As the blockchain space continues to mature and diversify, the importance of robust, secure, and efficient cross-chain infrastructure will only continue to grow.
The evolution from isolated blockchain networks to a connected multi-chain ecosystem parallels the development of the internet itself, where initially separate networks gradually connected to form the global information infrastructure we rely on today. Cross-chain bridges serve as the protocols and infrastructure that enable this connectivity, much like TCP/IP and other networking protocols enabled the early internet to flourish and scale to global proportions.
The success of cross-chain bridge technology will ultimately be measured not by the complexity of the underlying protocols or the sophistication of the cryptographic mechanisms, but by the seamless user experiences they enable and the economic opportunities they unlock. Users should be able to access the best applications, highest yields, and most innovative financial products across the entire blockchain ecosystem without being constrained by the arbitrary boundaries of individual networks.
The road ahead for cross-chain interoperability remains challenging, with significant technical, economic, and regulatory hurdles yet to be overcome. However, the rapid pace of innovation, the substantial investment being directed toward interoperability solutions, and the clear market demand for cross-chain functionality suggest that these challenges will be addressed through continued development and iteration.
Advanced traders and institutional investors require sophisticated analytical tools and real-time cross-chain data to navigate the complex interoperability landscape and capitalize on the opportunities created by an increasingly connected blockchain ecosystem. The future of decentralized finance depends on the successful development and adoption of secure, efficient, and user-friendly cross-chain infrastructure that can support the next generation of blockchain applications and financial innovations.
Disclaimer: This article is for educational and informational purposes only and should not be construed as financial advice. Cross-chain bridge protocols involve significant technical and financial risks, including the potential for total loss of transferred assets due to smart contract vulnerabilities, bridge exploits, or protocol failures. The cross-chain bridge space is highly experimental and rapidly evolving, with new risks and challenges emerging regularly. Always conduct thorough research, understand the specific risks associated with each bridge protocol, and never invest more than you can afford to lose. Past performance of bridge protocols does not guarantee future results, and the regulatory environment for cross-chain infrastructure remains uncertain and subject to change. The author and publisher are not responsible for any financial losses that may occur from using cross-chain bridge protocols or acting on the information provided in this article.