The Escalating Crisis of Exchange Security
The cryptocurrency industry has witnessed an unprecedented surge in exchange hacks during 2024, with over $2 billion in digital assets stolen from centralized platforms in what security experts are calling the worst year for exchange security on record. These sophisticated attacks have exposed fundamental vulnerabilities in how cryptocurrency exchanges protect user funds while highlighting the critical importance of security infrastructure in the rapidly evolving digital asset ecosystem.
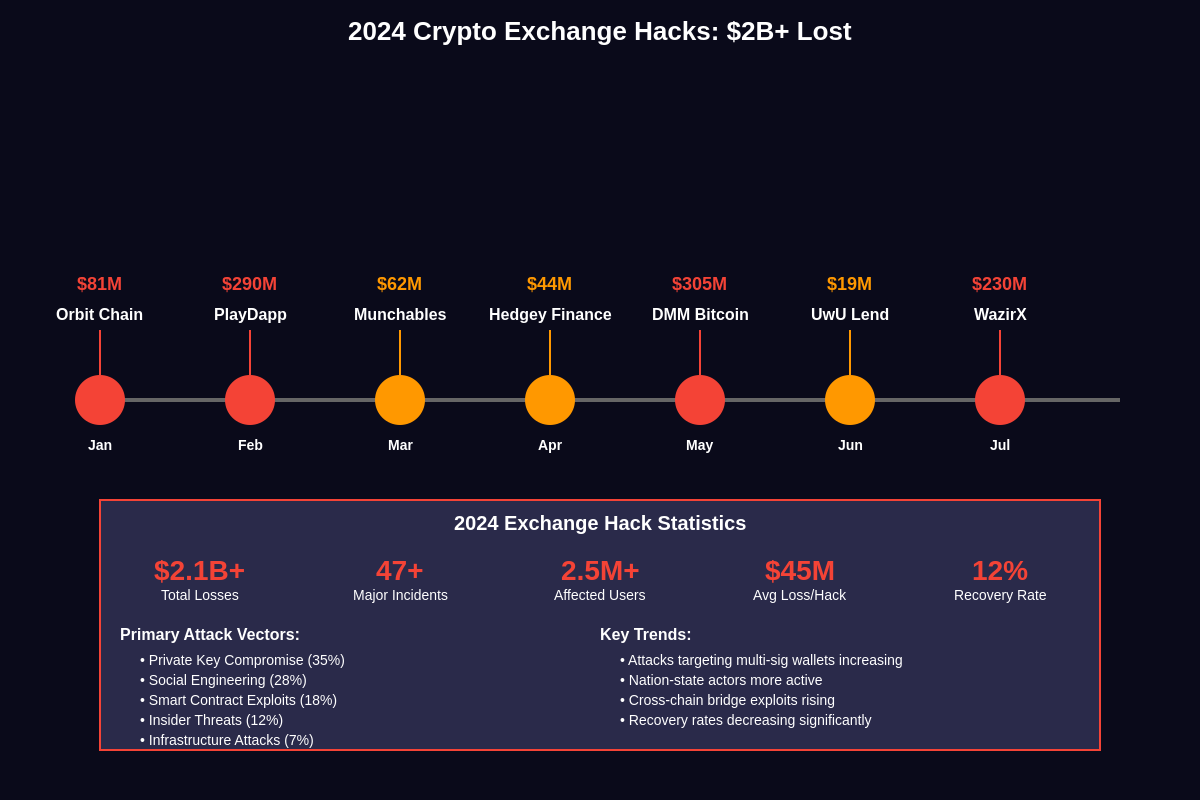
The scale and sophistication of 2024’s exchange hacks represent a dramatic escalation from previous years, with attackers employing increasingly advanced techniques including social engineering, insider threats, smart contract exploits, and multi-vector attacks that bypass traditional security measures. Major exchanges that were previously considered secure have fallen victim to breaches that have not only resulted in massive financial losses but also undermined confidence in centralized cryptocurrency infrastructure.
Historical Context and Evolution of Exchange Attacks
Cryptocurrency exchange hacks have been a persistent threat since the early days of digital assets, with the infamous Mt. Gox collapse in 2014 serving as a watershed moment that highlighted the risks of centralized custody. However, the attacks witnessed in 2024 demonstrate a significant evolution in both the scale and sophistication of these security breaches, with hackers employing state-of-the-art techniques that exploit both technical vulnerabilities and human factors.
The progression from simple private key theft to complex multi-stage attacks reflects the maturation of both the cryptocurrency ecosystem and the criminal organizations targeting it. Modern exchange hacks often involve months of reconnaissance, sophisticated social engineering campaigns, and coordinated attacks across multiple vectors that can overwhelm even well-prepared security teams. The financial incentives driving these attacks have grown exponentially as cryptocurrency adoption has increased, creating a lucrative target for organized cybercriminal groups.
Early exchange hacks were often the result of poor security practices, inadequate infrastructure, or simple theft by insiders. Today’s attacks represent a quantum leap in sophistication, with attackers demonstrating deep technical knowledge of exchange architecture, blockchain networks, and security protocols. Professional traders monitoring major exchange security incidents and their market impact have observed how these breaches create immediate volatility and long-term trust issues that affect the entire cryptocurrency market.
Major 2024 Exchange Breaches and Attack Vectors
The year 2024 has been marked by several high-profile exchange breaches that have collectively resulted in over $2 billion in losses, representing the largest annual total in cryptocurrency history. These attacks have targeted exchanges across the spectrum, from major international platforms with millions of users to smaller regional exchanges that serve specific markets or trading pairs.
The WazirX hack in July 2024 stands as one of the most significant breaches of the year, with attackers successfully stealing over $230 million in various cryptocurrencies through a sophisticated compromise of the exchange’s multi-signature wallet system. The attack demonstrated how even advanced security measures like multi-signature requirements can be circumvented through social engineering and insider compromise, leading to fundamental questions about the security of centralized custody solutions.
DMM Bitcoin’s $305 million hack in May 2024 represents another watershed moment in exchange security, with attackers exploiting vulnerabilities in the exchange’s withdrawal processing system to drain user funds over several hours before the breach was detected. The attack highlighted the critical importance of real-time monitoring systems and the challenges exchanges face in balancing user convenience with security requirements.
The sophistication of these attacks is evidenced by their multi-stage nature, often involving initial reconnaissance phases where attackers gather intelligence about exchange infrastructure, employee information, and security protocols. Advanced persistent threat groups have been observed spending months infiltrating exchange networks, moving laterally through systems, and positioning themselves for maximum impact before executing their final attacks.
Technical Analysis of Attack Methodologies
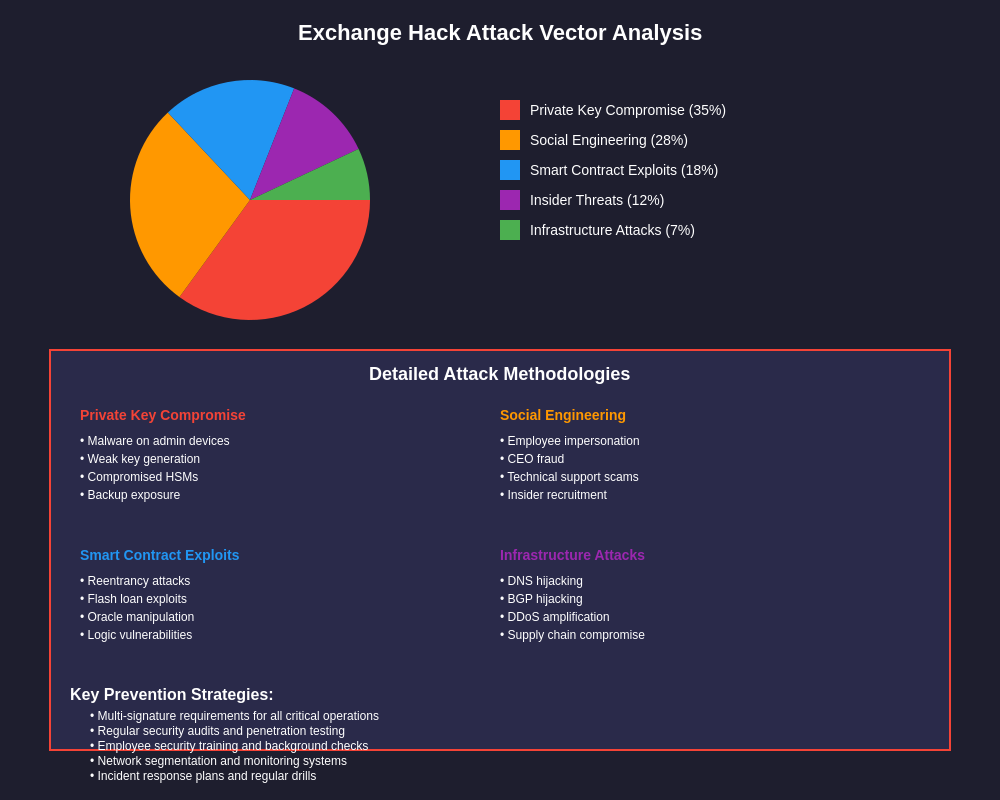
Modern cryptocurrency exchange hacks employ a diverse array of attack vectors that exploit both technical vulnerabilities and human factors in ways that traditional security measures often fail to address. These attacks typically begin with extensive reconnaissance phases where cybercriminals gather intelligence about target exchanges through social media analysis, employee profiling, and technical infrastructure mapping.
Social engineering attacks have become increasingly sophisticated, with attackers creating detailed profiles of exchange employees and using advanced psychological manipulation techniques to gain access to sensitive systems. These attacks often involve impersonation of trusted parties, creation of false urgency scenarios, and exploitation of organizational hierarchies to bypass security protocols. The success of these attacks demonstrates that even technically sophisticated security measures can be undermined by human factors.
Technical attack vectors include exploitation of smart contract vulnerabilities in DeFi integrations, compromise of hot wallet systems through various means, and attacks on exchange infrastructure including databases, trading engines, and withdrawal processing systems. Many successful attacks combine multiple vectors, using initial access gained through social engineering to escalate privileges and access critical systems that would otherwise be protected.
The emergence of supply chain attacks targeting exchange service providers represents a particularly concerning development, with attackers compromising third-party vendors to gain access to multiple exchange systems simultaneously. These attacks demonstrate the interconnected nature of modern cryptocurrency infrastructure and the challenges exchanges face in securing complex vendor relationships while maintaining operational efficiency.
Security Infrastructure and Custody Models
The security infrastructure employed by cryptocurrency exchanges varies dramatically based on their size, regulatory requirements, and risk tolerance, with different custody models offering varying levels of protection against different types of attacks. Traditional centralized exchanges typically employ a combination of hot wallets for operational liquidity, cold storage systems for the majority of user funds, and various intermediate security measures designed to balance security with operational requirements.
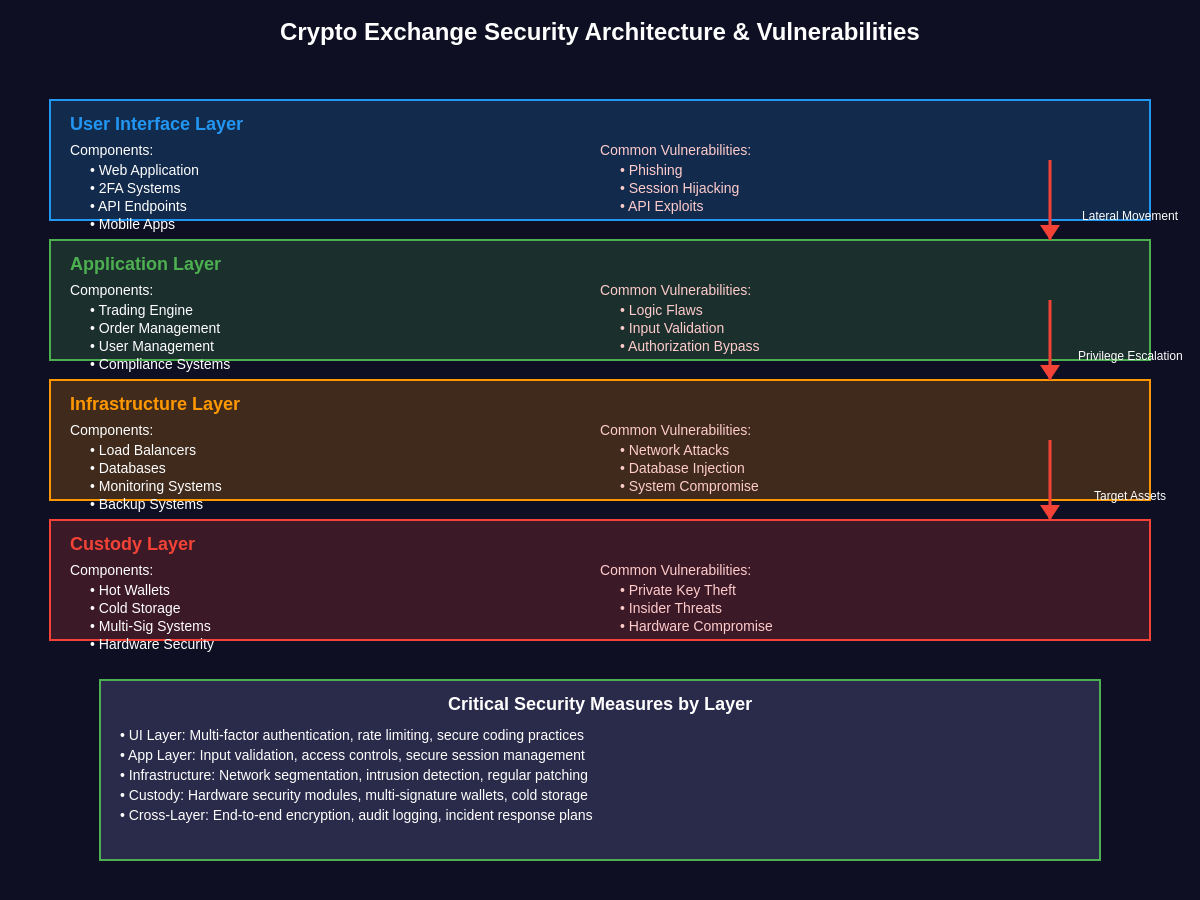
Hot wallet security represents one of the most critical components of exchange security infrastructure, as these systems must maintain internet connectivity to process withdrawals and trading operations while protecting against various attack vectors. Advanced exchanges implement multi-signature requirements, hardware security modules, and sophisticated monitoring systems to protect hot wallet operations, though these measures are not foolproof against determined attackers.
Cold storage systems, while generally more secure than hot wallets, face their own unique challenges including key management complexity, operational overhead for fund movement, and the risk of insider threats from personnel with access to cold storage systems. The optimal ratio between hot and cold wallet holdings remains a subject of ongoing debate, with different exchanges adopting different strategies based on their risk profiles and operational requirements.
Emerging custody solutions including multi-party computation systems, institutional custody providers, and hybrid models that combine centralized and decentralized elements represent potential improvements to traditional exchange security models. However, these solutions also introduce new complexities and potential vulnerabilities that must be carefully evaluated against their security benefits.
Regulatory Response and Compliance Challenges
The wave of exchange hacks in 2024 has prompted significant regulatory responses from authorities worldwide, with many jurisdictions implementing new requirements for exchange security standards, insurance coverage, and incident reporting. These regulatory developments reflect growing recognition that cryptocurrency exchanges have become critical financial infrastructure that requires appropriate oversight and protection standards.
The European Union’s Markets in Crypto-Assets regulation has established some of the most comprehensive security requirements for cryptocurrency exchanges, including mandatory segregation of customer funds, minimum capital requirements, and detailed incident reporting obligations. Similar regulatory frameworks are being developed in other major jurisdictions, creating a complex compliance landscape for international exchanges.
However, regulatory fragmentation creates challenges for exchanges operating across multiple jurisdictions, with different requirements for security standards, reporting obligations, and liability frameworks. The global nature of cryptocurrency markets means that regulatory gaps in any jurisdiction can create vulnerabilities that affect the entire ecosystem, highlighting the need for international coordination on exchange security standards.
Insurance requirements for cryptocurrency exchanges represent a particularly complex regulatory challenge, as traditional insurance models struggle to address the unique risks associated with digital asset custody. Market participants analyzing cryptocurrency exchange security incidents and regulatory responses observe how regulatory uncertainty affects exchange operations and user confidence across different jurisdictions.
Economic Impact and Market Consequences
The economic impact of cryptocurrency exchange hacks extends far beyond the immediate losses suffered by affected exchanges and their users, creating ripple effects throughout the cryptocurrency ecosystem that affect prices, trading volumes, and institutional adoption patterns. The $2 billion in losses recorded in 2024 represents not only direct financial damage but also broader economic costs including reduced market confidence, increased regulatory scrutiny, and elevated insurance costs across the industry.
Immediate market reactions to major exchange hacks typically involve significant price volatility for affected cryptocurrencies, temporary liquidity shortages as traders move funds to secure platforms, and broader selling pressure as investors reassess the risks associated with centralized exchanges. These market movements can be particularly severe when hacks affect major exchanges with substantial trading volumes or when they involve widely held cryptocurrencies.
The long-term economic consequences of exchange hacks include reduced institutional adoption as professional investors become more cautious about cryptocurrency infrastructure, increased compliance costs as regulatory requirements become more stringent, and higher operational costs for exchanges as they invest in enhanced security measures. These factors contribute to a challenging business environment for legitimate exchanges while potentially benefiting those with superior security practices.
Insurance markets for cryptocurrency exchanges have been significantly affected by the increase in hack frequency and severity, with many insurers reducing coverage limits, increasing premiums, or exiting the market entirely. This insurance crisis creates additional challenges for exchanges seeking to protect themselves and their users against security breaches while maintaining competitive operational costs.
User Impact and Fund Recovery Challenges
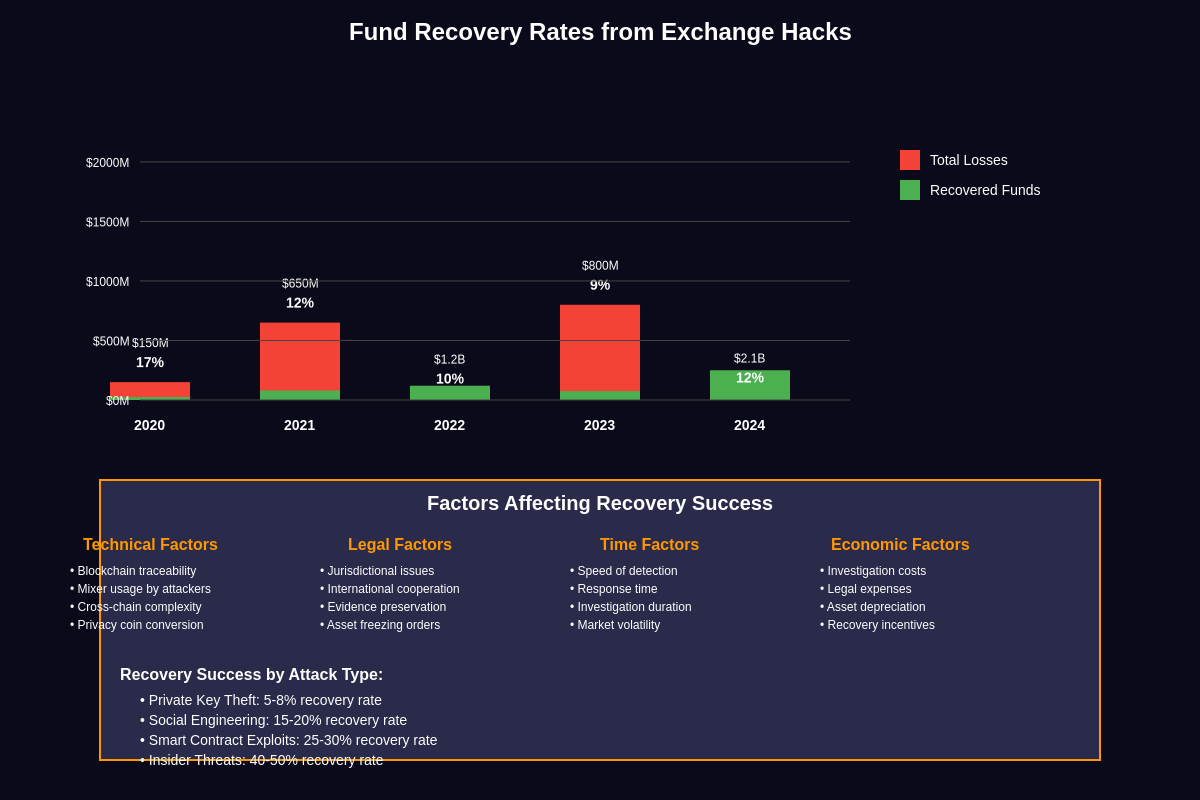
The human cost of cryptocurrency exchange hacks extends beyond financial losses to include psychological trauma, loss of trust in cryptocurrency systems, and significant challenges in recovering stolen funds. Users affected by exchange hacks often face lengthy legal processes, uncertainty about fund recovery, and difficult decisions about continued participation in cryptocurrency markets.
Fund recovery efforts following exchange hacks face numerous challenges including the pseudonymous nature of blockchain transactions, the global distribution of stolen funds across multiple jurisdictions, and the technical complexity of tracing cryptocurrency movements through mixing services and decentralized exchanges. While some high-profile cases have resulted in successful fund recovery, the majority of stolen cryptocurrency remains permanently lost to victims.
The legal frameworks governing exchange hack victims vary significantly across jurisdictions, with some regions providing stronger protections for affected users while others offer limited recourse. The classification of cryptocurrency as property, currency, or securities in different jurisdictions affects the legal remedies available to hack victims and the obligations of exchanges to compensate affected users.
User education and awareness initiatives have become increasingly important as exchange hacks have become more frequent and sophisticated. However, many users lack the technical knowledge necessary to properly evaluate exchange security practices or implement personal security measures that could reduce their exposure to exchange-related risks.
Advanced Persistent Threats and Nation-State Actors
The involvement of advanced persistent threat groups and potentially nation-state actors in cryptocurrency exchange hacks represents a significant escalation in the threat landscape, with attacks demonstrating levels of sophistication and resources that suggest state-level backing. These groups employ advanced techniques including zero-day exploits, sophisticated social engineering campaigns, and long-term infiltration strategies that can remain undetected for months or years.
The Lazarus Group, attributed to North Korea, has been linked to numerous high-profile cryptocurrency exchange hacks including recent attacks that have netted hundreds of millions of dollars. These attacks demonstrate capabilities that include custom malware development, sophisticated spear-phishing campaigns, and advanced techniques for moving and laundering stolen cryptocurrency through complex networks of intermediary services.
The geopolitical implications of nation-state involvement in cryptocurrency exchange hacks extend beyond financial crime to include questions about economic warfare, sanctions evasion, and the use of cryptocurrency systems to fund illegal activities. Professional security analysts utilizing advanced threat intelligence and market analysis tools track how these sophisticated attacks affect both individual exchanges and broader market dynamics.
Attribution of advanced cryptocurrency attacks remains extremely challenging due to the technical sophistication of the attackers, the use of proxy groups and criminal partnerships, and the global nature of cryptocurrency networks that obscure the origins and destinations of attack traffic. This attribution challenge complicates both law enforcement responses and private sector defense efforts.
Emerging Technologies and Defense Mechanisms
The cryptocurrency exchange industry has responded to the escalating threat landscape by implementing increasingly sophisticated defense mechanisms including artificial intelligence-powered fraud detection, behavioral analysis systems, and advanced cryptographic techniques that provide enhanced security without compromising operational efficiency.
Multi-party computation systems represent one of the most promising developments in exchange security, enabling the creation of cryptographic protocols that allow multiple parties to jointly compute functions over their inputs while keeping those inputs private. These systems can eliminate single points of failure in key management while maintaining the operational flexibility required for high-volume trading operations.
Zero-knowledge proof systems offer another avenue for improving exchange security by enabling verification of transactions and user credentials without revealing sensitive information. These systems can provide enhanced privacy protection for users while enabling exchanges to maintain compliance with regulatory requirements and detect suspicious activities.
Decentralized exchange protocols and hybrid custody models represent alternative approaches to traditional centralized exchange security, offering different trade-offs between security, performance, and user experience. While these systems are not immune to attacks, they can reduce the concentration of risk associated with traditional centralized custody models.
Insurance and Risk Management Strategies
The insurance landscape for cryptocurrency exchanges has evolved dramatically in response to the increasing frequency and severity of security breaches, with specialized insurers developing new products specifically designed to address the unique risks associated with digital asset custody and trading operations.
Cryptocurrency-specific insurance policies typically cover a range of risks including theft of digital assets from hot and cold storage systems, social engineering attacks, insider threats, and business interruption costs resulting from security incidents. However, these policies often include significant exclusions and limitations that can leave exchanges exposed to certain types of losses.
Risk management strategies for cryptocurrency exchanges have become increasingly sophisticated, incorporating advanced threat modeling, penetration testing, red team exercises, and continuous security monitoring to identify and address vulnerabilities before they can be exploited by attackers. These strategies require significant investment in both technology and personnel, creating operational challenges for smaller exchanges.
The development of industry-wide security standards and best practices has accelerated in response to the increasing threat landscape, with organizations like the Cryptocurrency Security Standard providing frameworks for evaluating and improving exchange security practices. However, implementation of these standards remains voluntary in many jurisdictions, creating inconsistencies in security practices across the industry.
Forensic Analysis and Investigation Techniques
The investigation of cryptocurrency exchange hacks requires specialized forensic techniques that combine traditional cybersecurity investigation methods with blockchain analysis and cryptocurrency tracing capabilities. These investigations often involve multiple law enforcement agencies across different jurisdictions, creating coordination challenges that can impede effective response to major incidents.
Blockchain forensics has emerged as a critical discipline for investigating cryptocurrency-related crimes, with specialized firms developing advanced techniques for tracing cryptocurrency movements, identifying suspicious patterns, and connecting blockchain transactions to real-world identities. However, the pseudonymous nature of many cryptocurrency networks and the availability of privacy-enhancing technologies create significant challenges for investigators.
The time-sensitive nature of cryptocurrency investigations creates additional pressure on forensic teams, as attackers can quickly move stolen funds through multiple intermediary services and convert them to other assets or cash out through various channels. Rapid response capabilities and international cooperation become critical factors in successful investigation outcomes.
Digital evidence preservation in cryptocurrency investigations requires specialized knowledge of blockchain networks, wallet technologies, and exchange systems to ensure that critical evidence is properly collected and maintained throughout the investigation process. The technical complexity of these systems can create challenges for traditional law enforcement personnel who may lack specialized cryptocurrency knowledge.
International Cooperation and Law Enforcement
The global nature of cryptocurrency exchange hacks necessitates unprecedented levels of international cooperation between law enforcement agencies, regulatory bodies, and private sector organizations to effectively investigate and prosecute cybercriminals operating across multiple jurisdictions.
Mutual legal assistance treaties and other international cooperation mechanisms have been adapted to address the unique challenges posed by cryptocurrency-related crimes, though significant gaps remain in many jurisdictions’ abilities to effectively investigate and prosecute these cases. The rapid evolution of cryptocurrency technology often outpaces the development of appropriate legal frameworks and investigative capabilities.
Information sharing between exchanges, security firms, and law enforcement agencies has become increasingly important for identifying attack patterns, tracking stolen funds, and preventing additional incidents. However, privacy concerns, competitive considerations, and regulatory requirements can create barriers to effective information sharing that may impede collective defense efforts.
The establishment of specialized law enforcement units focused on cryptocurrency crimes represents an important development in the global response to exchange hacks and other digital asset-related crimes. These units combine traditional investigative techniques with specialized knowledge of cryptocurrency technologies and networks to improve investigation outcomes.
Market Structure and Competitive Implications
The wave of exchange hacks in 2024 has created significant competitive implications within the cryptocurrency exchange industry, with security practices becoming an increasingly important differentiator for exchanges seeking to attract and retain users. Exchanges with superior security track records have gained market share at the expense of those that have suffered breaches or that are perceived as having inadequate security measures.
The concentration of trading volume among a small number of major exchanges creates systemic risks for the cryptocurrency ecosystem, as successful attacks against these platforms can have disproportionate market impacts. This concentration dynamic is driven partly by user preferences for established exchanges with better security reputations, creating barriers to entry for new exchanges and potentially reducing competition in the market.
Insurance costs and regulatory compliance requirements have become significant operational expenses for cryptocurrency exchanges, with these costs varying dramatically based on the exchange’s security practices, regulatory jurisdiction, and risk profile. These cost differences can create competitive advantages for exchanges in favorable regulatory environments or those with superior security capabilities.
The development of institutional-grade custody solutions has created new competitive dynamics in the exchange industry, with traditional exchanges competing against specialized custody providers and new hybrid models that combine trading and custody services. Professional institutional investors utilizing comprehensive exchange analysis and security assessment tools increasingly factor security practices into their platform selection decisions.
Technological Innovation and Security Evolution
The cryptocurrency exchange industry’s response to escalating security threats has driven significant technological innovation in areas including cryptographic key management, fraud detection, user authentication, and incident response systems. These innovations often emerge from the collaboration between exchanges, security vendors, and academic researchers working to address specific vulnerabilities or attack vectors.
Hardware security modules have become increasingly sophisticated, with new generations offering enhanced protection against physical and logical attacks while providing the performance characteristics required for high-volume trading operations. These systems represent critical infrastructure for exchange security but require specialized expertise to implement and maintain effectively.
Behavioral analysis and machine learning systems have shown promise for detecting suspicious activities and potential security threats before they can cause significant damage. However, these systems also create new challenges including false positive rates, adversarial attacks designed to evade detection, and the need for continuous updating to address evolving threat patterns.
The integration of decentralized technologies into centralized exchange infrastructure represents an emerging trend that could provide enhanced security benefits while maintaining the performance and user experience advantages of centralized systems. These hybrid approaches require careful design to avoid introducing new vulnerabilities while capturing the security benefits of decentralized architectures.
User Education and Security Awareness
The frequency and sophistication of cryptocurrency exchange hacks have highlighted the critical importance of user education and security awareness programs that help individuals protect themselves and make informed decisions about platform selection and fund management. However, the technical complexity of cryptocurrency systems creates significant challenges for developing effective educational materials that are both comprehensive and accessible.
Security awareness training for cryptocurrency users must address a wide range of topics including exchange selection criteria, personal security practices, fund diversification strategies, and incident response procedures. The rapid evolution of attack techniques and security technologies requires continuous updating of educational materials and training programs to remain relevant and effective.
The responsibility for user education is distributed across multiple stakeholders including exchanges, regulatory bodies, industry associations, and independent security researchers. This distributed approach can create inconsistencies in messaging and gaps in coverage that may leave some users inadequately prepared to protect themselves against various threats.
Social engineering attacks targeting cryptocurrency users have become increasingly sophisticated, requiring educational programs that address both technical security measures and psychological manipulation techniques used by attackers. These programs must help users develop critical thinking skills and healthy skepticism while avoiding creating excessive fear or paranoia that could discourage legitimate cryptocurrency adoption.
Future Threat Landscape and Predictions
The threat landscape facing cryptocurrency exchanges continues to evolve rapidly, with security experts predicting that future attacks will become even more sophisticated as attackers adapt to improved defensive measures and target new vulnerabilities in emerging technologies and business models.
The integration of artificial intelligence and machine learning technologies into attack methodologies is expected to increase both the sophistication and scale of future exchange hacks, with AI-powered systems potentially enabling automated vulnerability discovery, social engineering at scale, and adaptive attack strategies that can evolve in real-time to overcome defensive measures.
Quantum computing represents a long-term threat to cryptocurrency security infrastructure, with the potential to compromise current cryptographic systems once sufficiently powerful quantum computers become available. While this threat remains theoretical at present, exchanges and security vendors are beginning to investigate post-quantum cryptographic solutions that could provide protection against future quantum attacks.
The expansion of cryptocurrency adoption and the development of new financial products and services create an expanding attack surface that provides additional opportunities for cybercriminals. Central bank digital currencies, decentralized finance protocols, and cross-chain interoperability solutions all introduce new potential vulnerabilities that attackers may seek to exploit.
Industry Standards and Best Practices
The development of industry-wide security standards and best practices has accelerated in response to the increasing threat landscape, with various organizations working to establish frameworks that can improve security practices across the cryptocurrency exchange industry. These standards address multiple aspects of exchange security including technical infrastructure, operational procedures, personnel management, and incident response capabilities.
The Cryptocurrency Security Standard represents one of the most comprehensive attempts to establish industry-wide security requirements, providing detailed specifications for areas including key management, transaction processing, user authentication, and security monitoring. However, adoption of these standards remains voluntary in many jurisdictions, creating inconsistencies in implementation across different exchanges.
Professional certification programs for cryptocurrency security practitioners have emerged to address the need for specialized knowledge and skills in this rapidly evolving field. These programs provide standardized training and assessment procedures that can help ensure that security personnel have the necessary expertise to protect exchange operations effectively.
Regular security assessments and penetration testing have become standard practices for reputable cryptocurrency exchanges, with many platforms undergoing multiple assessments per year to identify and address potential vulnerabilities. However, the effectiveness of these assessments depends heavily on the expertise of the testing organizations and their familiarity with cryptocurrency-specific attack vectors and defensive measures.
Regulatory Evolution and Compliance Requirements
The regulatory landscape for cryptocurrency exchanges continues to evolve rapidly in response to security incidents and other developments in the digital asset ecosystem, with new requirements being implemented in multiple jurisdictions that affect exchange operations, security practices, and user protections.
Capital adequacy requirements for cryptocurrency exchanges have been implemented in several jurisdictions, requiring platforms to maintain minimum levels of capital reserves that can be used to compensate users in the event of security breaches or other operational failures. These requirements create significant operational challenges for exchanges while providing additional protection for users.
Cybersecurity insurance requirements and incident reporting obligations have become increasingly common regulatory requirements for cryptocurrency exchanges, creating standardized frameworks for risk management and information sharing that can benefit the entire industry. However, the cost and complexity of compliance with these requirements can create barriers to entry for smaller exchanges.
The development of international regulatory coordination mechanisms for cryptocurrency exchanges represents an important evolution in the global regulatory response to digital assets, with various forums working to establish common standards and information sharing procedures that can improve security and reduce regulatory arbitrage opportunities.
Conclusion and Path Forward
The cryptocurrency exchange hacks of 2024 represent a critical inflection point for the digital asset industry, demonstrating both the severity of current security challenges and the urgent need for comprehensive improvements in exchange security practices, regulatory frameworks, and industry coordination. The $2 billion in losses recorded this year serves as a stark reminder of the risks associated with centralized cryptocurrency infrastructure and the importance of implementing robust security measures.
The path forward requires sustained collaboration between exchanges, security vendors, regulatory bodies, and law enforcement agencies to develop and implement effective solutions that address both current threats and emerging risks. This collaboration must be supported by adequate funding for security research and development, appropriate regulatory frameworks that balance innovation with protection, and continued investment in user education and awareness programs.
The evolution of cryptocurrency exchange security will likely involve a combination of technological innovation, regulatory development, and industry standardization that collectively improves the security posture of the entire ecosystem. However, success in this endeavor will require sustained commitment from all stakeholders and recognition that security is an ongoing process rather than a one-time achievement.
Professional traders and institutional investors continue to monitor cryptocurrency market security developments and their impact on asset prices as they evaluate the long-term viability and adoption potential of digital assets. The industry’s ability to address current security challenges will likely determine the pace and extent of future cryptocurrency adoption across both retail and institutional markets.
The lessons learned from 2024’s exchange hacks must be applied systematically across the industry to prevent similar incidents in the future. This includes not only implementing better technical security measures but also addressing the human factors, organizational issues, and systemic risks that enable successful attacks against cryptocurrency infrastructure. Only through comprehensive and sustained efforts can the industry hope to build the secure and trustworthy infrastructure necessary for widespread cryptocurrency adoption.
Disclaimer: This article is for educational and informational purposes only and should not be construed as financial advice. Cryptocurrency trading and storage carry significant risks, including the potential for total loss of capital due to exchange hacks, technical failures, and other security incidents. The security incidents and attack methods discussed are for educational purposes to help readers understand and protect against these risks. Always conduct your own research, use reputable exchanges with strong security practices, and consider using personal wallets for long-term storage rather than keeping large amounts on exchanges. Consult with qualified financial and security advisors before making investment decisions or implementing security measures. The author and publisher are not responsible for any financial losses that may occur from acting on the information provided in this article.