Explore advanced trading strategies and technical analysis tools to enhance your cryptocurrency investment journey as you progress beyond basic wallet management.
Understanding Cryptocurrency Wallets and Their Essential Role
Cryptocurrency wallets serve as the fundamental gateway to the digital asset ecosystem, functioning not as traditional storage containers but as sophisticated software interfaces that manage your private keys and enable interaction with blockchain networks. Understanding the true nature of cryptocurrency wallets represents the first crucial step in your journey toward secure and effective digital asset management, as these tools essentially provide the cryptographic keys that prove ownership of your cryptocurrency holdings on various blockchain networks.
The misconception that cryptocurrency wallets actually store your digital assets stems from traditional banking analogies, but the reality involves a more complex system where your cryptocurrency remains permanently recorded on the blockchain while your wallet manages the private keys that grant access to those funds. These private keys function as cryptographic signatures that authorize transactions, making them the most critical component of your cryptocurrency security infrastructure. The wallet software provides a user-friendly interface for generating, storing, and utilizing these keys while abstracting away the complex cryptographic operations that occur behind the scenes.
Modern cryptocurrency wallets have evolved far beyond simple key management tools to become comprehensive platforms that support multiple blockchain networks, decentralized applications, non-fungible tokens, and advanced features like staking, lending, and decentralized finance protocols. This evolution reflects the broader maturation of the cryptocurrency ecosystem and the increasing sophistication of users who demand more functionality from their wallet software while maintaining the highest standards of security and privacy.
Types of Cryptocurrency Wallets and Their Unique Characteristics
The cryptocurrency wallet landscape encompasses several distinct categories, each offering different advantages and trade-offs between security, convenience, and functionality.
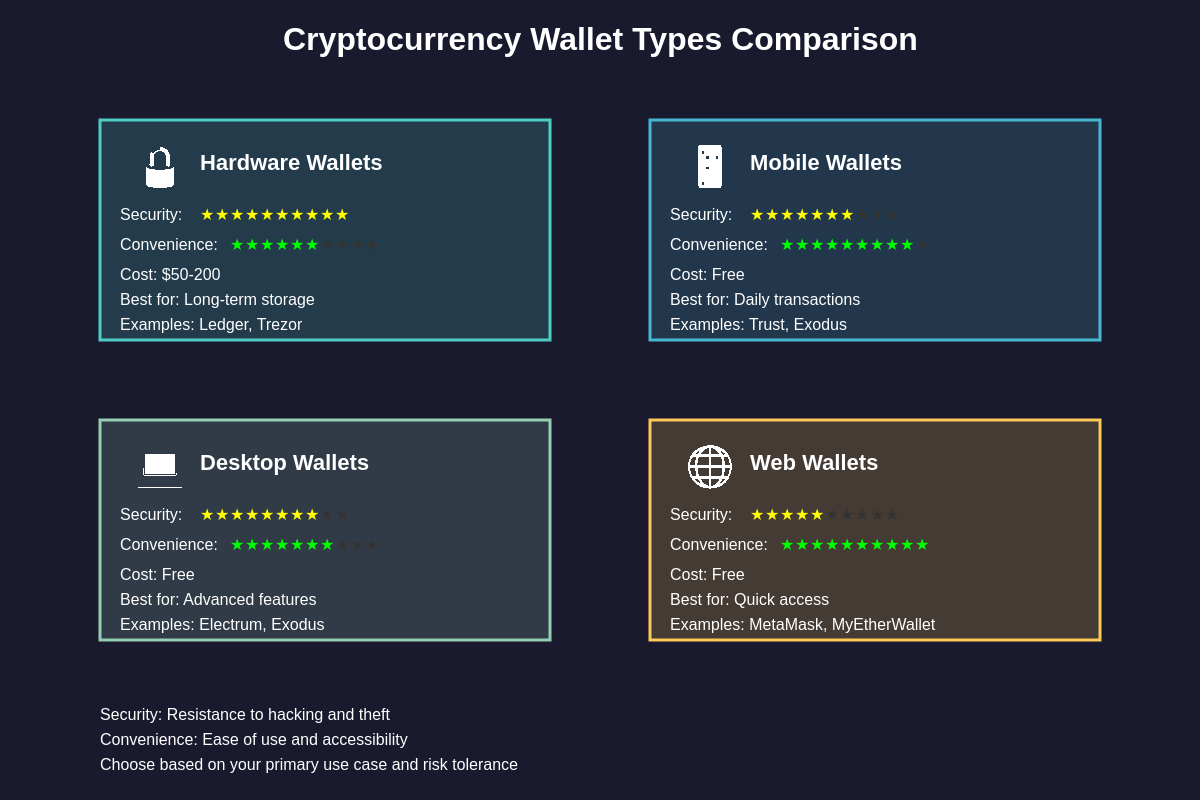
Hot wallets maintain constant internet connectivity, enabling immediate access to your cryptocurrency for trading, spending, and interacting with decentralized applications, but this connectivity also introduces potential security vulnerabilities that users must carefully consider. These wallets excel in situations requiring frequent transactions or active participation in decentralized finance protocols, making them ideal for experienced users who understand the associated risks.
Cold wallets prioritize security above convenience by maintaining complete offline operation, storing your private keys on devices that never connect to the internet and thereby eliminating the possibility of remote attacks or unauthorized access through network vulnerabilities. Hardware wallets represent the most popular category of cold storage solutions, utilizing specialized secure elements and cryptographic processors to protect your private keys while still enabling convenient transaction signing through temporary connections to internet-enabled devices for broadcasting transactions to blockchain networks.
Software wallets span the spectrum from desktop applications that provide full node functionality to mobile applications optimized for everyday use and browser extensions that integrate seamlessly with decentralized applications and cryptocurrency trading platforms. Desktop wallets often provide the most comprehensive feature sets and enhanced security through local key storage, while mobile wallets prioritize convenience and accessibility for users who need cryptocurrency access while traveling or conducting business away from their primary computers.
Paper wallets, though less common in modern cryptocurrency management, still serve specific use cases where users require completely offline key generation and storage without relying on any electronic devices that might be compromised or fail over time. These wallets involve printing private keys and addresses on physical paper, creating a permanent offline backup that remains immune to digital attacks but requires careful physical security measures to prevent theft, damage, or loss.
Selecting the Right Wallet Type for Your Specific Needs
Choosing the appropriate cryptocurrency wallet requires careful consideration of your individual use patterns, security requirements, technical expertise, and long-term cryptocurrency goals. New users often benefit from starting with reputable mobile wallets that provide intuitive interfaces, comprehensive customer support, and built-in educational resources while maintaining reasonable security standards through features like biometric authentication and secure enclave storage on modern smartphones.
Active traders and frequent users typically require hot wallets with robust exchange integrations, advanced portfolio management features, and seamless access to decentralized trading platforms and market analysis tools that enable real-time decision making based on current market conditions. These users often maintain multiple wallets to segregate different types of cryptocurrency activities while balancing security and convenience according to the specific requirements of each use case.
Long-term investors and individuals managing significant cryptocurrency holdings should prioritize security through hardware wallets or multi-signature solutions that distribute control across multiple devices or parties, reducing the risk of single points of failure while ensuring that substantial investments remain protected against both technical attacks and physical threats. These advanced security measures require additional setup complexity and ongoing management but provide invaluable protection for substantial cryptocurrency holdings.
Institutional users and businesses require enterprise-grade solutions that support multiple users, advanced permission systems, compliance reporting, and integration with existing financial infrastructure while maintaining the highest security standards through features like hardware security modules, multi-party computation protocols, and comprehensive audit trails that satisfy regulatory requirements.
Essential Security Considerations for Cryptocurrency Wallet Management
Cryptocurrency wallet security extends far beyond the initial setup process to encompass ongoing practices that protect your digital assets throughout their entire lifecycle. Private key management represents the cornerstone of cryptocurrency security, as these cryptographic credentials provide complete control over your funds and cannot be recovered if lost or stolen. Understanding that cryptocurrency transactions are irreversible emphasizes the critical importance of implementing comprehensive security measures from the moment you begin your cryptocurrency journey.

Strong password creation and management becomes paramount when dealing with cryptocurrency wallets, as weak passwords can provide attackers with direct access to your funds without requiring sophisticated technical attacks. Modern password managers can generate and store complex, unique passwords for each of your cryptocurrency accounts while providing convenient access through biometric authentication or master passwords. The additional layer of two-factor authentication adds significant security by requiring a second form of verification for account access, though users must ensure their backup authentication methods remain secure and accessible.
Phishing attacks represent one of the most common threats to cryptocurrency users, with sophisticated scammers creating convincing replicas of legitimate wallet interfaces, exchange platforms, and service providers to steal login credentials and private keys. Developing strong habits around URL verification, bookmark usage, and source validation can prevent these attacks while maintaining the convenience of online cryptocurrency services. Users should always access their wallets through official applications or carefully verified websites rather than following links in emails, social media posts, or other potentially compromised communications.
Regular software updates maintain critical security patches and feature improvements that protect against newly discovered vulnerabilities and attack vectors in the constantly evolving cryptocurrency threat landscape. Enabling automatic updates where possible ensures that your wallet software remains current with the latest security enhancements while manual verification of update sources prevents the installation of malicious software disguised as legitimate updates.
Step-by-Step Mobile Wallet Setup Process
Mobile wallet installation begins with identifying reputable wallet applications through official app stores, verified developer websites, or trusted cryptocurrency community recommendations rather than relying on search results or third-party download sites that might distribute malicious software. Popular mobile wallets like Trust Wallet, Exodus, and Coinbase Wallet have established strong security records and provide comprehensive features suitable for most beginner users while maintaining user-friendly interfaces that simplify the initial setup process.
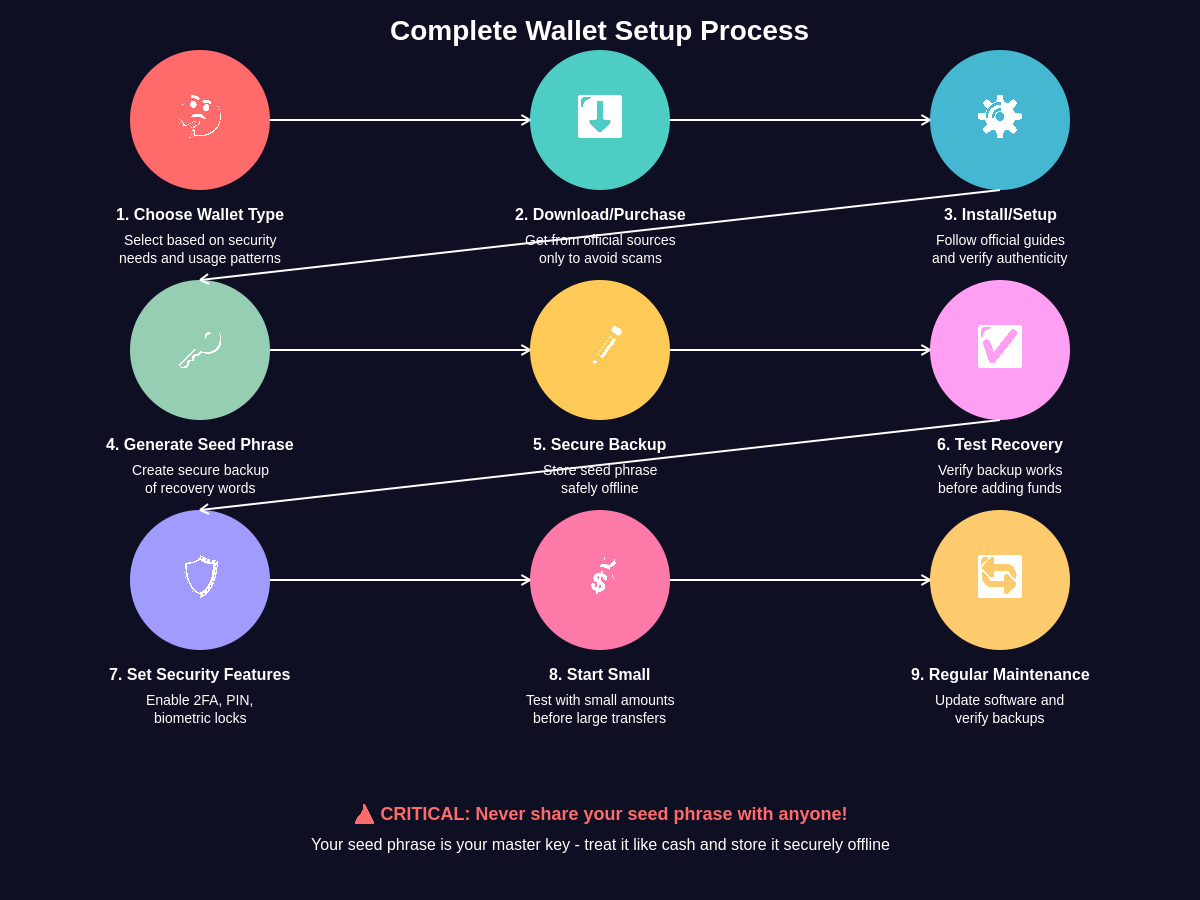
The initial setup process typically involves creating a new wallet or importing an existing one, with new users generally choosing the creation option to generate fresh private keys that have never been exposed to potential security risks. During this process, the wallet application will guide you through accepting terms of service, granting necessary permissions for operation, and configuring basic security settings like PIN codes or biometric authentication that protect access to your wallet on the mobile device.
Seed phrase generation and backup represents the most critical step in mobile wallet setup, as this sequence of twelve to twenty-four randomly generated words provides the master key for recovering your wallet and accessing your cryptocurrency if your mobile device is lost, stolen, or damaged. The wallet application will display these words in a specific order that must be recorded accurately and stored securely offline, as anyone with access to your seed phrase can recreate your wallet and control your funds from any compatible device or application.
Verification of your seed phrase backup ensures that you have correctly recorded these critical recovery words before proceeding with wallet funding or regular use. Most wallet applications require users to confirm their seed phrase by selecting words in the correct order or typing specific words from the sequence, preventing common backup errors that could result in permanent loss of access to cryptocurrency funds. This verification step should never be skipped, regardless of your confidence in the initial backup process.
Hardware Wallet Setup and Security Implementation
Hardware wallet acquisition requires purchasing devices directly from manufacturers or authorized distributors to ensure authenticity and prevent supply chain attacks that could compromise device security before reaching end users. Popular hardware wallet manufacturers like Ledger, Trezor, and KeepKey provide secure ordering processes and tamper-evident packaging that helps users verify device integrity upon delivery, though additional verification steps may be necessary for high-value applications or users with elevated security requirements.
Initial device setup involves connecting the hardware wallet to a computer or mobile device through USB or Bluetooth connections while following manufacturer-provided setup instructions that guide users through device initialization, PIN code creation, and seed phrase generation. Hardware wallets typically generate seed phrases using true random number generators built into their secure elements, providing superior entropy compared to software-based solutions while ensuring that private keys never leave the secure hardware environment.
Firmware updates and device configuration enable additional security features and support for new cryptocurrencies while maintaining compatibility with evolving blockchain networks and protocols. Most hardware wallets provide companion applications that facilitate firmware updates, account management, and transaction processing while maintaining the security advantages of offline private key storage. Users should always verify firmware authenticity through manufacturer-provided verification tools before installing updates to prevent the installation of malicious firmware that could compromise device security.
Backup and recovery procedures for hardware wallets extend beyond seed phrase storage to include device replacement processes, PIN code recovery options, and procedures for accessing funds when the primary hardware device becomes unavailable. Understanding these recovery mechanisms before they become necessary ensures that users can maintain access to their cryptocurrency even when facing hardware failures, loss, or damage to their primary devices.
Desktop Wallet Installation and Configuration
Desktop wallet selection depends on your operating system, required cryptocurrency support, and desired feature set, with options ranging from lightweight SPV clients that rely on remote servers for blockchain data to full node implementations that download and verify entire blockchain histories. Full node wallets like Bitcoin Core provide maximum security and privacy by eliminating reliance on third-party servers while contributing to network security and decentralization, though they require substantial storage space and bandwidth for initial synchronization and ongoing operation.
Installation procedures vary significantly between different desktop wallet applications, with some requiring simple executable file downloads while others involve complex compilation processes from source code for users requiring maximum security verification. Following official installation guides and verifying download integrity through cryptographic signatures or hash verification helps ensure that you install authentic software rather than modified versions that could contain malicious code designed to steal cryptocurrency or compromise system security.
Initial configuration involves creating wallet files, setting encryption passwords, and configuring network connections according to your security and performance preferences. Many desktop wallets offer advanced configuration options for network proxies, custom blockchain nodes, and fee calculation algorithms that enable experienced users to optimize performance and privacy while beginners can rely on secure default settings that provide appropriate security without requiring extensive technical knowledge.
Backup procedures for desktop wallets encompass both seed phrase storage and wallet file backups that preserve transaction history, address labels, and custom configuration settings that enhance usability and record keeping. Regular automated backups to secure locations help prevent data loss while ensuring that wallet recovery procedures can restore full functionality rather than just basic fund access when restoration becomes necessary.
Multi-Signature Wallet Setup for Enhanced Security
Multi-signature wallets require multiple private key signatures to authorize transactions, distributing control across multiple devices, locations, or parties to eliminate single points of failure while providing enhanced security for substantial cryptocurrency holdings. These advanced wallet configurations typically involve two-of-three or three-of-five signature schemes where a subset of the total keys can authorize transactions while preventing any single compromised key from enabling unauthorized fund transfers.
Setup complexity for multi-signature wallets exceeds that of standard single-signature solutions, requiring coordination between multiple devices or parties while ensuring that each participant understands their responsibilities and maintains appropriate security practices for their portion of the multi-signature scheme. Popular multi-signature solutions like Electrum, Casa, and Unchained Capital provide user-friendly interfaces that simplify the setup process while maintaining the security advantages of distributed key management.
Key distribution strategies must balance security with accessibility, ensuring that authorized signers can access their keys when needed while preventing unauthorized access through physical security measures, geographic distribution, or institutional custody solutions. Professional multi-signature services can provide institutional-grade key management for users who require maximum security but lack the technical expertise or infrastructure to manage complex multi-signature configurations independently.
Recovery planning for multi-signature wallets requires comprehensive documentation of all key locations, backup procedures, and authorization processes that enable fund recovery even when some keys become unavailable due to hardware failure, loss, or other circumstances. Understanding the minimum signature requirements and recovery procedures before they become necessary prevents potential loss of access to cryptocurrency funds during emergency situations.
Wallet Backup and Recovery Procedures
Comprehensive backup strategies for cryptocurrency wallets extend beyond simple seed phrase storage to encompass multiple backup methods, geographic distribution, and regular verification procedures that ensure recovery capability throughout the entire lifecycle of your cryptocurrency holdings. Seed phrase backups should be created on durable materials like metal backup plates or high-quality paper stored in fireproof and waterproof containers distributed across multiple secure locations to prevent loss due to natural disasters, theft, or accidental destruction.
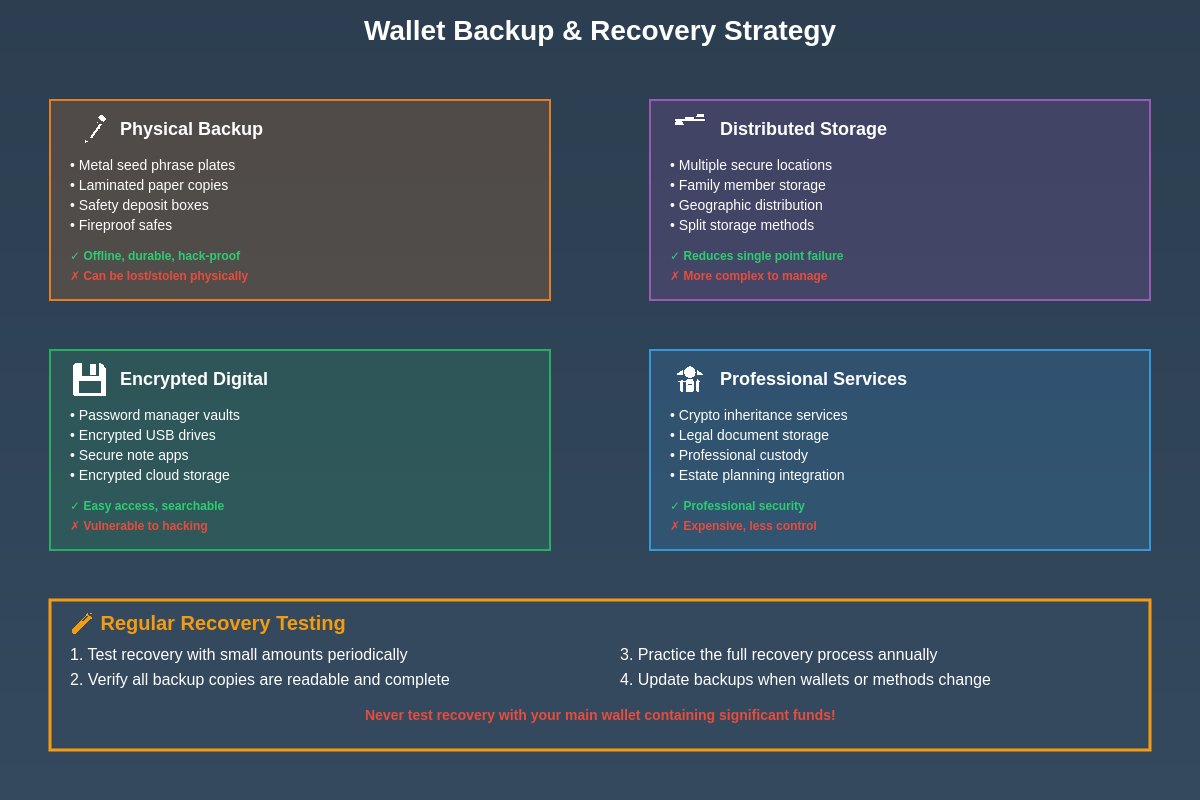
Recovery testing involves periodically verifying that your backup procedures can successfully restore wallet access using test wallets or small amounts of cryptocurrency to validate the backup process without risking substantial funds during testing procedures. This verification process should encompass all backup methods and storage locations while documenting any issues or complications that arise during recovery testing to improve backup procedures and ensure reliable fund recovery when needed.
Digital backup methods can supplement physical backups through encrypted storage solutions, secure cloud services, or distributed storage networks that provide additional redundancy while maintaining appropriate security measures. However, digital backups should never replace physical backups entirely, as digital storage systems remain vulnerable to hacking, service interruptions, or data corruption that could compromise backup integrity when recovery becomes necessary.
Inheritance planning for cryptocurrency requires careful consideration of how authorized parties can access your cryptocurrency holdings in the event of incapacitation or death while maintaining security during your lifetime. Professional estate planning services increasingly provide cryptocurrency-specific guidance that addresses the unique challenges of digital asset inheritance while ensuring compliance with applicable legal requirements and tax obligations.
Common Setup Mistakes and How to Avoid Them
Inadequate seed phrase storage represents the most critical mistake new cryptocurrency users make during wallet setup, often storing these critical recovery words in easily accessible digital formats, unsecured physical locations, or sharing them with unauthorized parties who could use this information to steal cryptocurrency holdings. Proper seed phrase storage requires treating these words as equivalent to cash, implementing physical security measures and access controls that prevent unauthorized access while ensuring authorized users can retrieve them when necessary.
Insufficient backup verification leads to false confidence in recovery procedures that may fail when actually needed, with users often assuming their backup procedures work correctly without performing comprehensive testing that validates the entire recovery process. Regular recovery testing using small amounts of cryptocurrency or dedicated test wallets can identify backup problems before they result in permanent loss of access to substantial cryptocurrency holdings.
Weak password and PIN selection compromises wallet security even when other security measures are properly implemented, with attackers often targeting user authentication credentials rather than attempting to break cryptographic protections built into wallet software. Strong password generation tools and two-factor authentication can significantly enhance security while password managers eliminate the convenience trade-offs associated with complex password requirements.
Software authenticity verification failures expose users to malicious software designed to steal cryptocurrency or compromise system security, with fake wallet applications and compromised downloads representing significant threats in the cryptocurrency ecosystem. Always downloading wallet software from official sources, verifying cryptographic signatures, and using trusted app stores helps ensure software authenticity while avoiding modified versions that could contain malicious code.
Integration with Cryptocurrency Exchanges and Services
Exchange integration strategies balance convenience with security considerations, as direct connections between wallets and exchange accounts can simplify trading and portfolio management while potentially exposing wallet contents to additional attack vectors through compromised exchange accounts or API keys. Many users maintain separate wallets for long-term storage and active trading to limit exposure while benefiting from integration features that enhance usability and portfolio management capabilities.
API key management for exchange integrations requires careful configuration of permissions and security settings that enable necessary functionality while limiting potential damage from compromised credentials or unauthorized access. Read-only API keys can provide portfolio visibility and market data access without enabling unauthorized trades or withdrawals, while carefully configured trading permissions can automate specific strategies while preventing broader account compromise.
Advanced portfolio tracking and analysis tools can integrate with multiple wallets and exchange accounts to provide comprehensive visibility into cryptocurrency holdings, performance metrics, and tax reporting information that simplifies portfolio management for users with complex cryptocurrency activities across multiple platforms and services.
Automated backup and synchronization features offered by some wallet providers can simplify wallet management across multiple devices while introducing additional security considerations related to cloud storage and service provider access to sensitive wallet information. Users should carefully evaluate the security trade-offs associated with convenience features while understanding how these services protect sensitive information and maintain user privacy.
Advanced Wallet Features and Customization Options
Staking integration within modern wallets enables users to earn rewards by participating in proof-of-stake consensus mechanisms without requiring separate staking services or complex technical setup procedures. Built-in staking features typically handle validator selection, reward distribution, and network participation while providing user-friendly interfaces that display staking rewards, duration requirements, and associated risks for different proof-of-stake networks.
Decentralized application browser functionality transforms cryptocurrency wallets into comprehensive platforms for interacting with the broader decentralized finance ecosystem, enabling users to access lending protocols, decentralized exchanges, yield farming opportunities, and other DeFi services directly through their wallet interfaces. These integrated browsers maintain security by managing permissions and transaction approvals while providing convenient access to the expanding universe of decentralized applications.
Custom network configuration allows advanced users to connect their wallets to test networks, layer-two scaling solutions, and alternative blockchain networks that may not be supported by default wallet configurations. This functionality enables early access to new networks and protocols while requiring additional technical knowledge to configure network parameters safely and avoid potential compatibility issues or security vulnerabilities.
Advanced fee management features provide users with granular control over transaction costs and confirmation times through custom fee calculation algorithms, transaction batching capabilities, and replace-by-fee mechanisms that optimize blockchain interactions according to specific user requirements and market conditions. Understanding these features can significantly reduce transaction costs for active users while ensuring appropriate confirmation times for time-sensitive transactions.
Troubleshooting Common Wallet Issues
Transaction failures can occur due to insufficient fees, network congestion, incorrect recipient addresses, or insufficient account balances, requiring systematic troubleshooting to identify root causes and implement appropriate solutions. Most wallet applications provide transaction history and status information that can help diagnose problems while blockchain explorers offer additional visibility into transaction processing and network conditions that may affect transaction success.
Synchronization problems with desktop wallets often result from network connectivity issues, corrupted blockchain data, or insufficient storage space for blockchain synchronization files. Resolving these issues may require network configuration changes, blockchain data re-synchronization, or storage management to ensure proper wallet operation and accurate balance information.
Lost password recovery procedures vary significantly between different wallet types and configurations, with some wallets offering account recovery options through service providers while others rely entirely on user-controlled seed phrases for access restoration. Understanding recovery options before problems occur prevents panic decisions and ensures appropriate recovery procedures are followed when access issues arise.
Balance display discrepancies can result from synchronization delays, network forks, unconfirmed transactions, or incorrect network configurations that prevent wallets from accessing accurate blockchain information. Patience and network troubleshooting often resolve these issues while understanding normal blockchain confirmation processes helps users distinguish between technical problems and normal network operations.
Best Practices for Long-Term Wallet Management
Regular security audits of your wallet setup, backup procedures, and security practices help identify potential vulnerabilities or outdated practices that may compromise security as threats and technologies evolve over time. These audits should encompass password strength, software updates, backup verification, and integration security while documenting any necessary improvements to maintain optimal security posture.
Software maintenance involves staying current with wallet updates, security patches, and feature enhancements while carefully evaluating new features and configuration changes that may affect security or functionality. Maintaining current software versions provides access to security improvements and bug fixes while avoiding compatibility issues with evolving blockchain networks and protocols.
Backup maintenance requires periodic verification of seed phrase storage, backup accessibility, and recovery procedures while updating storage methods and locations as circumstances change over time. Physical backup materials should be inspected for degradation while digital backups require verification of encryption integrity and storage provider security practices.
Portfolio rebalancing and wallet organization strategies help maintain optimal security and functionality as cryptocurrency holdings grow and evolve, potentially requiring migration to more secure wallet solutions, implementation of multi-signature configurations, or segregation of different types of cryptocurrency activities across specialized wallet configurations optimized for specific use cases.
Disclaimer: This article is for educational purposes only and does not constitute financial advice. Cryptocurrency investments carry significant risks, including the potential for total loss of invested capital. Always conduct thorough research and consider consulting with qualified financial professionals before making investment decisions. The security of cryptocurrency wallets depends on proper implementation of recommended practices, and users are responsible for maintaining the security of their private keys and backup procedures.