The Shadow Economy of Digital Deception
The explosive growth of memecoin markets has created an unprecedented breeding ground for sophisticated financial fraud, with malicious actors exploiting the speculative enthusiasm and cultural phenomena surrounding meme-based cryptocurrencies to orchestrate elaborate schemes that have collectively stolen billions of dollars from unsuspecting investors worldwide.
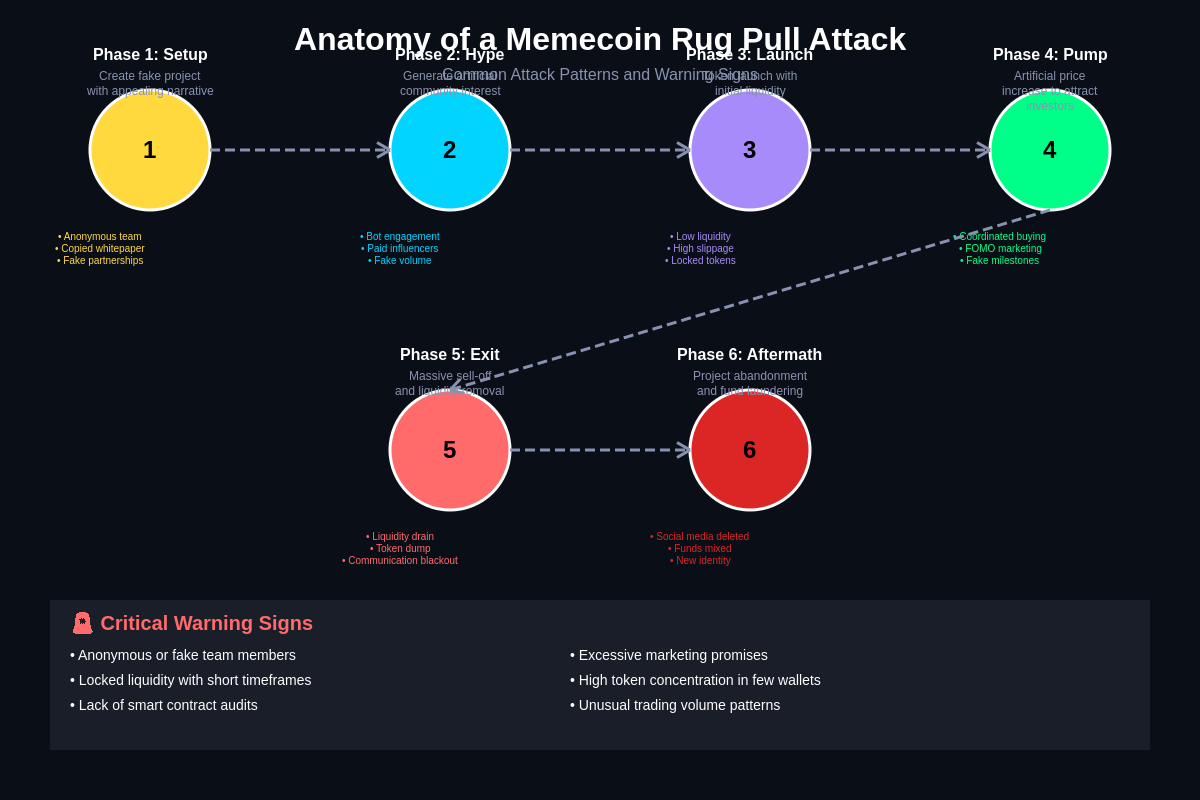
These fraudulent activities, commonly known as rug pulls and exit scams, represent a dark evolution of traditional financial fraud adapted to the decentralized and largely unregulated landscape of cryptocurrency markets, where the promise of astronomical returns often blinds participants to fundamental security risks and red flags that would be immediately apparent in traditional financial contexts.
The anatomy of memecoin fraud reveals a sophisticated understanding of crowd psychology, social media manipulation, and technical vulnerabilities that enable bad actors to create convincing facades of legitimate projects while systematically extracting value from their communities through carefully orchestrated deception campaigns. These schemes often begin with the creation of seemingly authentic memecoin projects that leverage popular cultural references, viral marketing techniques, and community-building strategies to establish credibility and attract initial investment before executing predetermined exit strategies that leave investors with worthless tokens and empty promises.
The decentralized nature of cryptocurrency markets provides numerous advantages for fraudsters seeking to operate with minimal oversight or accountability, including the ability to launch projects anonymously, manipulate token economics through smart contract programming, and execute complex money laundering operations that obscure the trail of stolen funds across multiple blockchain networks and jurisdictions. The proliferation of new tokens visible in real-time market data makes it increasingly difficult for investors to distinguish between legitimate projects and elaborate fraud schemes designed to exploit speculative enthusiasm.
The psychological exploitation inherent in memecoin fraud often targets investors’ fear of missing out on the next major cryptocurrency success story, leveraging social proof, artificial scarcity, and celebrity endorsements to create compelling investment narratives that override rational risk assessment and due diligence practices. Fraudsters have become increasingly sophisticated in their understanding of behavioral economics and social media dynamics, enabling them to craft highly effective deception campaigns that can attract millions of dollars in investment within hours or days of project launch.
Anatomy of Rug Pull Schemes
Rug pull schemes represent perhaps the most common and devastating form of memecoin fraud, involving the systematic extraction of liquidity from token trading pools by project developers or insiders who retain control over critical project infrastructure and token distribution mechanisms. These operations typically unfold through carefully planned sequences of events designed to maximize the amount of value extracted while minimizing the likelihood of detection or intervention by affected investors or platform operators until the damage has already been done.
The technical execution of rug pulls often involves the manipulation of automated market maker liquidity pools, where fraudsters initially provide substantial liquidity to establish credible trading markets before systematically removing their contributions once sufficient external investment has accumulated in the pools. This process can be executed through various mechanisms including direct liquidity withdrawal, token supply manipulation, smart contract backdoors, or coordinated selling pressure that crashes token prices while insiders execute large trades at favorable prices.
Soft rug pulls represent a more subtle form of fraud where project developers gradually abandon their commitments and responsibilities while slowly extracting value through token sales, reduced development activity, and diminished community engagement rather than executing dramatic exit events that might trigger immediate investor awareness or legal scrutiny. These schemes can persist for months or years, slowly bleeding value from communities while maintaining plausible deniability about malicious intent.
Hard rug pulls involve immediate and dramatic extraction of value through technical exploits, liquidity removal, or other mechanisms that instantly render tokens worthless or untradeable, often leaving investors with no recourse for recovery and clear evidence of fraudulent intent. These operations typically target projects that have achieved significant hype and investment accumulation, maximizing the potential financial impact while leveraging the emotional investment of community members who may be reluctant to acknowledge they have been victims of fraud.
The social engineering components of rug pull schemes often involve the cultivation of trust and credibility through fake team credentials, fabricated partnerships, manipulated social media presence, and artificial community engagement designed to create the appearance of legitimate project development and community support. Price manipulation visible in detailed chart analysis often precedes major rug pull events as fraudsters coordinate final extraction activities.
Advanced rug pull operations may involve multiple phases of extraction spread across different timeframes and mechanisms to avoid triggering automated fraud detection systems or regulatory attention while maximizing the total amount of value that can be extracted from affected communities. These sophisticated schemes often incorporate elements of legitimate project development to maintain credibility while secretly preparing exit strategies that can be executed when optimal conditions arise.
Exit Scam Methodologies and Execution
Exit scams in the memecoin space extend beyond simple rug pulls to encompass comprehensive fraud operations that involve elaborate deception campaigns, fake business development activities, and sophisticated money laundering operations designed to systematically extract investor funds while maintaining the appearance of legitimate business operations until the moment of final extraction. These schemes often involve multiple participants working in coordination to create convincing facades of successful cryptocurrency projects while secretly planning predetermined exit strategies.
The preparation phase of exit scams typically involves extensive groundwork to establish credibility including the creation of professional-looking websites, social media accounts, marketing materials, and community engagement activities that provide social proof and legitimacy to attract initial investor interest. Fraudsters often invest significant resources in creating convincing project narratives, fake team profiles, fabricated partnerships, and artificial community engagement to build trust and credibility that can be leveraged to attract larger investment amounts.
Fundraising phases of exit scams often involve presales, initial coin offerings, or other investment mechanisms that enable fraudsters to collect funds directly from investors before token distribution or exchange listing events that would provide liquidity and enable price discovery. These fundraising activities may be presented as legitimate business development efforts while secretly serving as mechanisms for collecting maximum investment before executing exit strategies.
The execution phase of exit scams typically involves the sudden cessation of all project activities, deletion of social media accounts and websites, and immediate liquidation of any remaining project assets or token holdings that can be converted to more stable cryptocurrencies or fiat currencies. These activities often occur without warning and may be timed to coincide with broader market volatility or other events that might obscure the fraudulent nature of the project’s collapse.
Money laundering operations following exit scams often involve complex chains of cryptocurrency transactions designed to obscure the trail of stolen funds and make recovery efforts more difficult for affected investors or law enforcement agencies. These operations may involve the use of privacy coins, mixing services, decentralized exchanges, and cross-chain bridges to fragment and anonymize stolen funds across multiple blockchain networks and jurisdictions.
The psychological aftermath of exit scams often leaves victims struggling with feelings of betrayal, financial loss, and embarrassment that may discourage them from reporting incidents to authorities or seeking assistance with recovery efforts, enabling fraudsters to operate with reduced risk of accountability or legal consequences. The cultural stigma associated with cryptocurrency investment losses can compound these psychological effects and reduce the likelihood of collective action against fraudsters.
Social Media Manipulation and Influence Operations
The success of memecoin fraud schemes relies heavily on sophisticated social media manipulation campaigns that exploit algorithmic content distribution, artificial engagement generation, and influencer marketing to create viral awareness and investment demand for fraudulent projects.
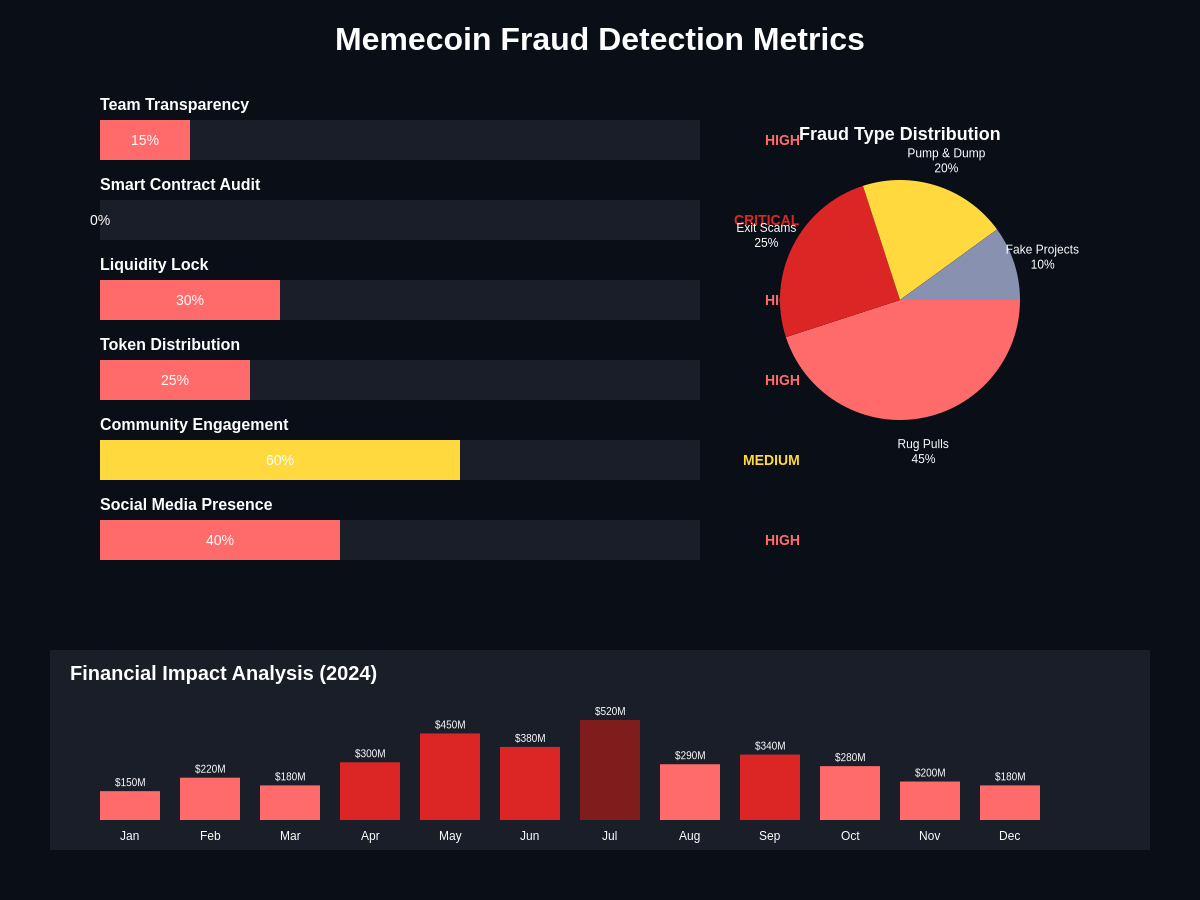
These operations often involve coordinated networks of fake accounts, bot activity, and paid promotion designed to create the appearance of organic community interest and social proof that can convince real investors to participate in fraudulent schemes.
Bot networks play crucial roles in memecoin fraud by generating artificial engagement metrics, manipulating social media trends, and creating the appearance of widespread community support for fraudulent projects through coordinated posting, commenting, and sharing activities across multiple platforms simultaneously. These automated systems have become increasingly sophisticated in their ability to mimic human behavior patterns and avoid detection by platform anti-spam systems while maintaining coordinated messaging that supports fraudulent project narratives.
Influencer manipulation involves the recruitment of social media personalities, cryptocurrency commentators, and other individuals with significant followings to promote fraudulent memecoin projects through sponsored content, endorsements, or other promotional activities that may not clearly disclose the financial relationships or compensation arrangements involved. These promotional campaigns often leverage the trust and credibility that influencers have established with their audiences to drive investment interest in fraudulent projects.
Fake news and media manipulation campaigns involve the creation and distribution of fabricated news articles, press releases, partnership announcements, and other content designed to create the appearance of legitimate business development and mainstream recognition for fraudulent projects. These materials are often distributed through networks of fake news websites, social media accounts, and content syndication services that can make fraudulent information appear more credible and widespread than it actually is.
Community infiltration strategies involve the placement of fraudster-controlled accounts within legitimate cryptocurrency communities, forums, and social media groups where they can promote fraudulent projects while appearing to be genuine community members providing authentic recommendations based on personal research and experience. These infiltration efforts often involve extensive preparation to establish account histories and credibility before being activated to promote specific fraudulent schemes.
Psychological manipulation techniques used in social media campaigns often exploit cognitive biases, emotional triggers, and social dynamics that can override rational decision-making processes and encourage impulsive investment behavior despite obvious red flags or warning signs. Market sentiment analysis tools used by professional traders can sometimes help identify artificial manipulation patterns, though sophisticated fraudsters continue to develop more subtle approaches.
Technical Vulnerabilities and Smart Contract Exploits
The technical infrastructure underlying memecoin projects often contains deliberate vulnerabilities and backdoors that enable fraudsters to manipulate token economics, extract liquidity, or disable trading functionality according to predetermined exit strategies while maintaining plausible deniability about malicious intent during the project’s operational phase. These technical vulnerabilities are often disguised as legitimate features or hidden within complex smart contract code that may not be thoroughly audited or understood by investors before they commit funds to fraudulent projects.
Smart contract backdoors represent one of the most common technical mechanisms used in memecoin fraud, involving the inclusion of hidden functions or administrative privileges that enable project controllers to manipulate token supply, transfer ownership, pause trading, or execute other actions that can be used to extract value or disable project functionality when desired. These backdoors are often disguised as emergency functions or administrative features that appear legitimate but can be abused for fraudulent purposes.
Liquidity lock mechanisms that appear to provide security for investors may actually contain hidden provisions or escape clauses that enable fraudsters to extract liquidity under specific conditions or through alternative pathways that are not immediately apparent to casual observers reviewing project documentation or smart contract code. These deceptive security measures can provide false confidence to investors while preserving fraudster access to critical project infrastructure.
Token distribution mechanisms may be designed to create unfair advantages for project insiders through hidden allocations, preferential pricing, or other arrangements that enable fraudsters to accumulate large token positions at minimal cost while public investors pay market prices for their holdings. These distribution inequities can enable massive profit extraction when fraudsters liquidate their holdings into markets supported by public investor demand.
Proxy contracts and upgradeable smart contract architectures may be used to disguise the true functionality of memecoin projects while preserving the ability to modify critical project parameters or functionality after launch when investor attention has decreased and community vigilance has been relaxed. These technical architectures can enable fraudsters to maintain legitimate appearances while retaining the ability to implement fraudulent modifications when conditions are favorable for extraction.
Multi-signature wallet configurations that appear to provide decentralized control over project funds may actually be controlled by coordinated groups of fraudsters or may contain hidden mechanisms that enable single parties to override collective decision-making processes when executing exit strategies. The complexity of multi-signature arrangements can obscure true control relationships while providing false assurance about decentralized governance and security.
Psychological Manipulation and Victim Targeting
The psychological dimensions of memecoin fraud involve sophisticated manipulation techniques that exploit cognitive biases, emotional vulnerabilities, and social dynamics to override rational decision-making processes and encourage investment behavior that serves fraudster interests rather than victim welfare.
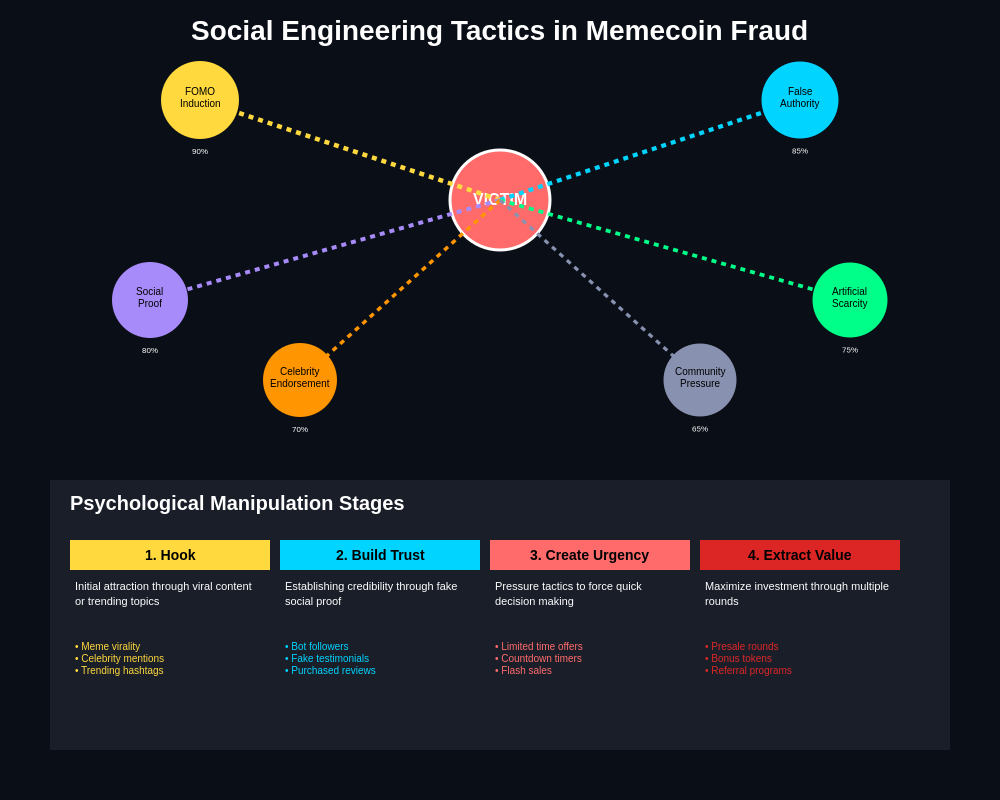
These manipulation strategies often target specific psychological profiles and demographic groups that may be particularly susceptible to certain types of persuasion or social influence while being less likely to conduct thorough due diligence or recognize warning signs of fraudulent activity.
Fear of missing out (FOMO) exploitation represents one of the most effective psychological manipulation techniques used in memecoin fraud, involving the creation of artificial scarcity, time pressure, and social proof that can trigger impulsive investment decisions without adequate consideration of risks or alternative opportunities. Fraudsters often leverage viral marketing techniques, celebrity endorsements, and community testimonials to create compelling narratives about limited-time opportunities that require immediate action to avoid permanent exclusion from extraordinary profit potential.
Social proof manipulation involves the fabrication of community engagement, investor testimonials, and success stories that can convince potential victims that fraudulent projects have genuine support and credibility within relevant communities. These social proof elements are often created through coordinated networks of fake accounts, paid promotional campaigns, and bot activity that can generate convincing appearances of authentic community interest and successful investment outcomes.
Authority figure exploitation involves the recruitment or impersonation of respected individuals within cryptocurrency communities, including developers, analysts, influencers, and other personalities whose endorsements or apparent participation in fraudulent projects can provide credibility and legitimacy that encourages investment from their followers or admirers. These authority relationships may involve compensation, coercion, impersonation, or other arrangements that enable fraudsters to leverage established trust relationships for malicious purposes.
Reciprocity manipulation techniques involve the provision of apparent value, exclusive access, or special treatment to potential victims that creates psychological obligations and emotional bonds that can be leveraged to encourage investment behavior or discourage skeptical inquiry about project legitimacy. These reciprocity relationships often involve exclusive community access, personalized attention from project teams, or early access to information or opportunities that make victims feel special and valued.
Confirmation bias exploitation involves the strategic presentation of information that supports existing beliefs or desires about cryptocurrency investment opportunities while suppressing or discouraging investigation of contradictory evidence or alternative perspectives that might reveal fraudulent intent. Fraudsters often create echo chambers and information silos that reinforce positive narratives while discouraging critical thinking or independent research that might reveal warning signs.
Economic Impact and Market Consequences
The economic devastation caused by memecoin fraud extends far beyond immediate financial losses to individual investors, creating systemic risks and market distortions that undermine confidence in legitimate cryptocurrency projects while contributing to regulatory backlash and institutional skepticism about digital asset markets more broadly. The cumulative impact of widespread fraud has created an environment where legitimate projects struggle to attract investment and community support due to investor wariness and regulatory uncertainty surrounding meme-based cryptocurrencies.
Direct financial losses from memecoin fraud schemes have reached billions of dollars across thousands of individual incidents, with individual victims often losing life savings, retirement funds, or other critical financial resources that may take years or decades to replace through traditional income and investment activities. The concentration of losses among retail investors with limited financial resources and sophisticated investment knowledge compounds the human impact of these crimes while reducing the likelihood of successful recovery efforts.
Market manipulation effects of coordinated fraud schemes can distort price discovery mechanisms and create artificial volatility patterns that affect legitimate trading activities and investment strategies across broader cryptocurrency markets. The presence of numerous fraudulent projects can make it increasingly difficult for investors to distinguish between legitimate opportunities and elaborate scams, reducing overall market efficiency and increasing transaction costs for all participants.
Regulatory responses to widespread memecoin fraud have included increased scrutiny of cryptocurrency markets, enhanced enforcement activities, and proposals for new regulatory frameworks that may impose significant compliance costs and operational restrictions on legitimate projects while potentially limiting innovation and competition within the digital asset space. The regulatory uncertainty created by ongoing fraud problems can discourage institutional investment and mainstream adoption of cryptocurrency technologies.
Insurance and risk management implications of memecoin fraud include increased premiums, reduced coverage availability, and enhanced due diligence requirements for cryptocurrency-related investments and business activities. The difficulty of quantifying and managing fraud risks in decentralized markets creates challenges for traditional risk management approaches while limiting the availability of protective mechanisms for potential victims.
Long-term market development consequences may include reduced innovation, limited access to capital for legitimate projects, and increased concentration of market activity among established players with sufficient resources to navigate complex regulatory and security requirements. Comprehensive market analysis tools become essential for identifying legitimate projects amid widespread fraudulent activity.
Detection and Prevention Strategies
The development of effective detection and prevention strategies for memecoin fraud requires sophisticated analytical capabilities that combine technical analysis, social media monitoring, behavioral pattern recognition, and community intelligence gathering to identify warning signs and red flags before fraud schemes can achieve significant scale or impact. These detection systems must be capable of operating in real-time environments while processing large volumes of data from multiple sources to identify subtle patterns and anomalies that may indicate fraudulent activity in development or execution phases.
Technical analysis approaches to fraud detection involve the examination of smart contract code, tokenomics structures, liquidity arrangements, and trading patterns to identify potential vulnerabilities or suspicious characteristics that may indicate fraudulent intent or technical mechanisms that could enable future extraction activities. These analysis techniques require specialized expertise and sophisticated tools that can parse complex smart contract code and identify hidden functions or backdoors that may not be immediately apparent to casual observers.
Social media monitoring systems can track engagement patterns, account relationships, and content distribution networks to identify artificial manipulation campaigns, coordinated inauthentic behavior, and other indicators of social media fraud that may be supporting memecoin scams. These monitoring capabilities must be capable of distinguishing between organic community enthusiasm and manufactured engagement while tracking sophisticated bot networks and influence operations across multiple platforms simultaneously.
Community intelligence gathering involves the cultivation of information networks within cryptocurrency communities that can provide early warning about emerging fraud schemes, share intelligence about known bad actors, and coordinate collective defense mechanisms that can reduce the effectiveness of fraudulent projects. These community-based approaches leverage distributed knowledge and experience to identify threats that may not be detectable through automated systems alone.
Due diligence frameworks for memecoin evaluation should incorporate technical auditing, team verification, tokenomics analysis, community assessment, and risk factor evaluation to provide comprehensive assessment of project legitimacy and potential fraud risks. These frameworks must be accessible to retail investors while providing sufficient depth and rigor to identify sophisticated fraud schemes that may appear legitimate on superficial examination.
Educational initiatives and awareness campaigns play crucial roles in fraud prevention by improving investor knowledge about common fraud patterns, red flag indicators, and protective measures that can reduce susceptibility to social engineering and psychological manipulation. These educational efforts must be tailored to different audience segments while providing practical guidance that can be applied in fast-moving and emotionally charged investment environments where rational decision-making may be compromised.
Legal Frameworks and Enforcement Challenges
The legal landscape surrounding memecoin fraud enforcement faces significant challenges due to the decentralized, international, and technologically complex nature of cryptocurrency crimes that often span multiple jurisdictions while involving novel technical mechanisms that may not be adequately addressed by existing criminal law frameworks. Law enforcement agencies worldwide have struggled to develop effective investigation and prosecution strategies for cryptocurrency fraud while building specialized expertise and technical capabilities necessary to track, analyze, and pursue cases involving sophisticated blockchain-based crimes.
Jurisdictional complexity in memecoin fraud cases often involves victims, perpetrators, and infrastructure distributed across multiple countries with different legal systems, regulatory frameworks, and enforcement capabilities, creating coordination challenges and legal gaps that fraudsters can exploit to avoid accountability. The anonymity features of cryptocurrency systems can make it difficult to identify perpetrators or establish legal jurisdiction over crimes that may involve numerous participants operating from different locations around the world.
Evidence gathering and preservation in cryptocurrency fraud cases requires specialized technical capabilities and legal procedures that can maintain the integrity of blockchain-based evidence while ensuring compliance with local laws and procedures for criminal investigations. The pseudonymous nature of many cryptocurrency transactions can complicate efforts to establish clear connections between criminal activities and specific individuals while requiring sophisticated analysis techniques to trace fund flows and identify control relationships.
Asset recovery efforts in memecoin fraud cases face significant technical and legal obstacles including the irreversible nature of many cryptocurrency transactions, the difficulty of seizing decentralized assets, and the complex international cooperation required to freeze or recover stolen funds that may be distributed across multiple jurisdictions and platforms. The technical sophistication of money laundering operations used by cryptocurrency fraudsters can make asset recovery extremely difficult or impossible even when perpetrators are successfully identified and prosecuted.
Regulatory compliance requirements for exchanges, wallet providers, and other cryptocurrency service providers create opportunities for law enforcement cooperation and investigation support while potentially improving the likelihood of successful asset recovery and perpetrator identification. However, the decentralized nature of many cryptocurrency systems can limit the effectiveness of traditional regulatory approaches while creating opportunities for fraudsters to operate outside established compliance frameworks.
International cooperation mechanisms for cryptocurrency crime enforcement remain underdeveloped in many regions, creating opportunities for fraudsters to exploit legal and procedural gaps while operating across borders with reduced risk of coordinated law enforcement response. The development of enhanced international cooperation frameworks and standardized procedures for cryptocurrency crime investigation represents a critical need for improving enforcement effectiveness against memecoin fraud and other blockchain-based crimes.
Recovery and Victim Support Systems
The development of comprehensive victim support systems for memecoin fraud cases requires specialized services that address both the financial and psychological impacts of cryptocurrency fraud while providing practical assistance with legal proceedings, asset recovery efforts, and financial rehabilitation.
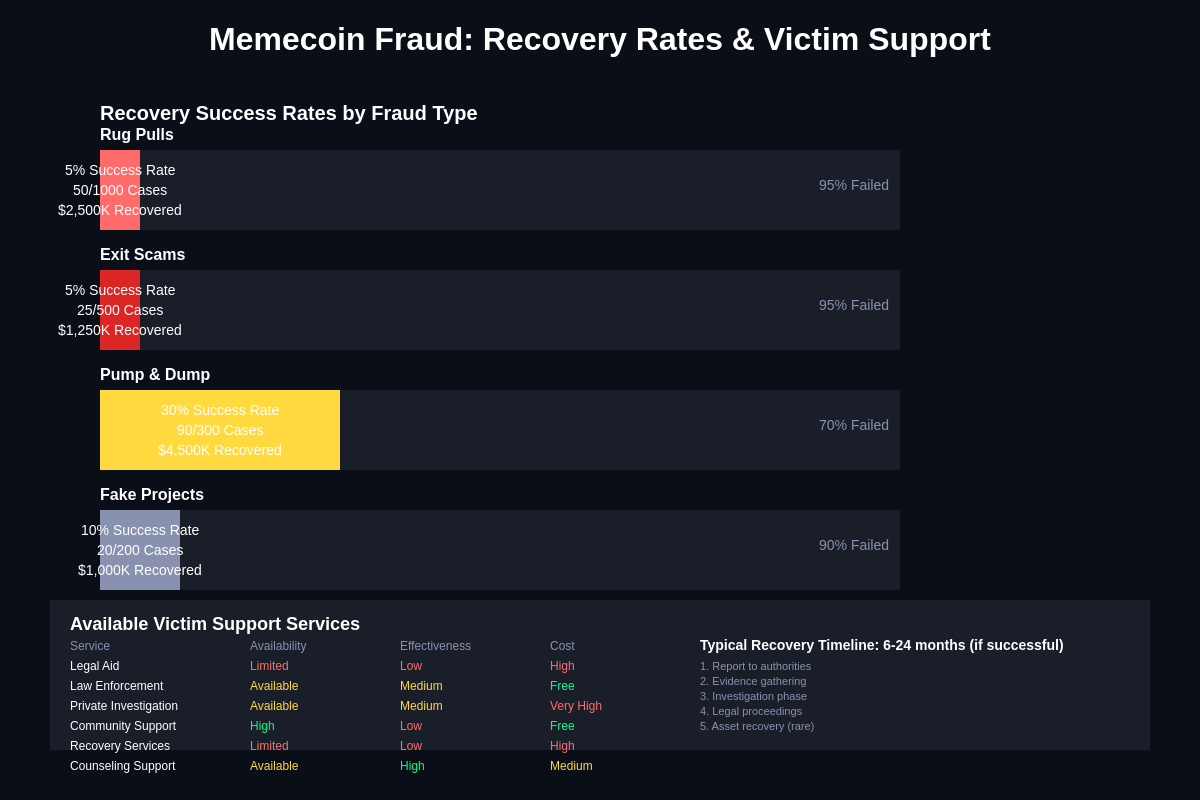
These support systems must be capable of serving diverse victim populations with varying levels of technical sophistication and financial resources while navigating complex legal and technical challenges associated with cryptocurrency fraud recovery.
Financial recovery assistance programs may include legal aid services, asset tracing support, and coordination with law enforcement agencies to maximize the likelihood of successful fund recovery while minimizing additional costs and burdens for fraud victims. These programs must be capable of handling cases involving complex technical issues and international jurisdictions while providing accessible services to victims who may lack the resources to pursue recovery efforts independently.
Psychological support services for fraud victims should address the unique emotional and psychological impacts of cryptocurrency fraud including feelings of betrayal, embarrassment, financial anxiety, and loss of trust in digital technologies and investment opportunities. These services must be culturally sensitive and technically informed while providing practical coping strategies and emotional support throughout recovery processes that may extend over months or years.
Community support networks can provide peer-to-peer assistance, shared experiences, and collective advocacy that can help fraud victims navigate recovery processes while reducing isolation and stigma associated with cryptocurrency fraud victimization. These networks can also serve important roles in intelligence gathering and fraud prevention by sharing information about emerging threats and coordinating collective response efforts.
Legal advocacy and representation services specifically designed for cryptocurrency fraud cases can provide specialized expertise and resources that may not be available through traditional legal aid programs while helping victims navigate complex technical and jurisdictional issues associated with blockchain-based crimes. These services must be capable of handling cases involving novel legal issues and technical evidence while providing accessible representation to victims with limited financial resources.
Educational and prevention services for fraud victims can help prevent re-victimization while building knowledge and skills that can support more effective participation in cryptocurrency markets going forward. These services should address both technical security measures and psychological factors that may increase vulnerability to future fraud attempts while providing practical guidance for safer cryptocurrency investment and participation strategies.
Technological Solutions and Industry Response
The cryptocurrency industry has responded to the growing threat of memecoin fraud through the development of various technological solutions, security standards, and best practices designed to reduce fraud risks while improving transparency and accountability in token launches and project development. These industry-led initiatives represent attempts to address fraud problems through technical innovation and self-regulation rather than relying solely on government intervention or law enforcement responses that may be slow to develop or implement.
Smart contract auditing services have become increasingly sophisticated in their ability to identify potential vulnerabilities, backdoors, and other technical risks in memecoin projects while providing independent verification of code security and functionality. These auditing services must continuously evolve to address new fraud techniques and technical vulnerabilities while providing accessible and affordable services to legitimate projects with limited budgets for security assessments.
Decentralized identity and reputation systems aim to improve accountability and reduce anonymity advantages that enable memecoin fraud by creating persistent identity records and reputation scores that can help investors evaluate project team credibility and track record. These systems must balance privacy protection with accountability enhancement while creating incentives for honest behavior and consequences for fraudulent activities.
Automated fraud detection and monitoring systems leverage machine learning, pattern recognition, and real-time data analysis to identify suspicious activities, unusual trading patterns, and other indicators of potential fraud in memecoin markets. These systems must be capable of processing large volumes of data while minimizing false positive alerts that could harm legitimate projects while maintaining effectiveness against sophisticated fraud schemes that may attempt to evade detection.
Platform security standards and best practices for cryptocurrency exchanges, wallet providers, and other service providers can reduce fraud risks by implementing enhanced due diligence procedures, monitoring systems, and user protection measures that make it more difficult for fraudulent projects to gain access to mainstream cryptocurrency infrastructure and services. These standards must be continuously updated to address emerging threats while balancing security enhancement with innovation and competition objectives.
Community-driven verification and rating systems enable distributed evaluation of memecoin projects through crowdsourced analysis, peer review, and collective intelligence gathering that can supplement formal auditing and regulatory oversight. Advanced analytical tools and platforms have become essential components of these community verification efforts, providing sophisticated capabilities for technical and market analysis.
Future Trends and Emerging Threats
The evolution of memecoin fraud continues to accelerate as bad actors develop increasingly sophisticated techniques for exploiting technological vulnerabilities, regulatory gaps, and psychological factors that enable large-scale financial crimes in cryptocurrency markets. Understanding emerging trends and potential future developments in fraud methodologies becomes crucial for developing effective prevention and response strategies while anticipating new challenges that may emerge as cryptocurrency markets continue to grow and evolve.
Artificial intelligence and machine learning technologies are being increasingly incorporated into fraud schemes to automate social media manipulation, generate convincing fake content, and optimize psychological targeting strategies that can improve the effectiveness of deception campaigns while reducing the manual effort required to execute large-scale fraud operations. These technological developments may enable smaller groups of fraudsters to execute more sophisticated and damaging fraud schemes while making detection and attribution more difficult for security systems and law enforcement agencies.
Cross-chain and multi-platform fraud schemes are becoming more common as fraudsters leverage interoperability technologies and decentralized finance protocols to create complex fraud operations that span multiple blockchain networks and platforms while making investigation and asset recovery more challenging. These schemes may involve sophisticated technical architectures that exploit vulnerabilities in bridge protocols, cross-chain communication systems, and decentralized exchange mechanisms.
Regulatory arbitrage strategies involve the exploitation of jurisdictional differences and regulatory gaps to structure fraud schemes in ways that minimize legal risks while maximizing extraction potential through careful selection of operational locations, legal structures, and technical architectures that may be difficult for regulators to address through traditional enforcement mechanisms. These strategies may become more sophisticated as fraudsters develop better understanding of international legal frameworks and regulatory coordination mechanisms.
Deepfake and synthetic media technologies pose emerging threats for memecoin fraud through the creation of convincing fake video content, audio recordings, and other media that can be used to impersonate legitimate personalities, create false endorsements, or fabricate evidence of project legitimacy and community support. These technologies may enable more convincing deception campaigns while making verification and authentication more challenging for potential victims and investigators.
Institutional and professional fraud operations may emerge as cryptocurrency markets mature and the potential profits from large-scale fraud increase, involving organized criminal groups, professional fraudsters, and sophisticated technical capabilities that may be more difficult to detect and prosecute than current amateur and small-scale fraud operations. These developments could represent significant escalations in the scale and sophistication of threats facing cryptocurrency markets and investors.
Disclaimer: This article is for informational purposes only and does not constitute financial advice. Cryptocurrency investments are highly volatile and risky. Past performance does not guarantee future results. Always conduct your own research and consult with qualified financial advisors before making investment decisions. Be extremely cautious when investing in memecoins and always verify project legitimacy through multiple independent sources.