Advanced trading tools and analytics are essential for understanding DeFi protocol performance metrics before making investment decisions based on audit findings.
Understanding the Critical Role of Security Audits in DeFi
The decentralized finance ecosystem has revolutionized traditional financial services by eliminating intermediaries and enabling permissionless access to financial products, yet this innovation comes with significant security risks that require thorough evaluation through comprehensive audit reports. Smart contract audits serve as the primary mechanism for identifying vulnerabilities, assessing protocol safety, and providing users with critical information needed to make informed decisions about participating in DeFi protocols.
Security audits in the DeFi space represent far more than simple code reviews, encompassing comprehensive evaluations of smart contract logic, economic models, governance structures, and potential attack vectors that could compromise user funds or protocol integrity. Professional audit firms employ sophisticated methodologies combining automated analysis tools, manual code review, formal verification techniques, and economic modeling to identify both technical vulnerabilities and design flaws that could be exploited by malicious actors.
The complexity of modern DeFi protocols, which often integrate multiple smart contracts, external oracle feeds, cross-chain bridges, and complex tokenomics mechanisms, makes comprehensive security evaluation increasingly challenging and essential for protocol safety. Users who understand how to properly evaluate audit reports gain significant advantages in risk assessment, enabling them to distinguish between genuinely secure protocols and those with hidden vulnerabilities that could result in significant financial losses.
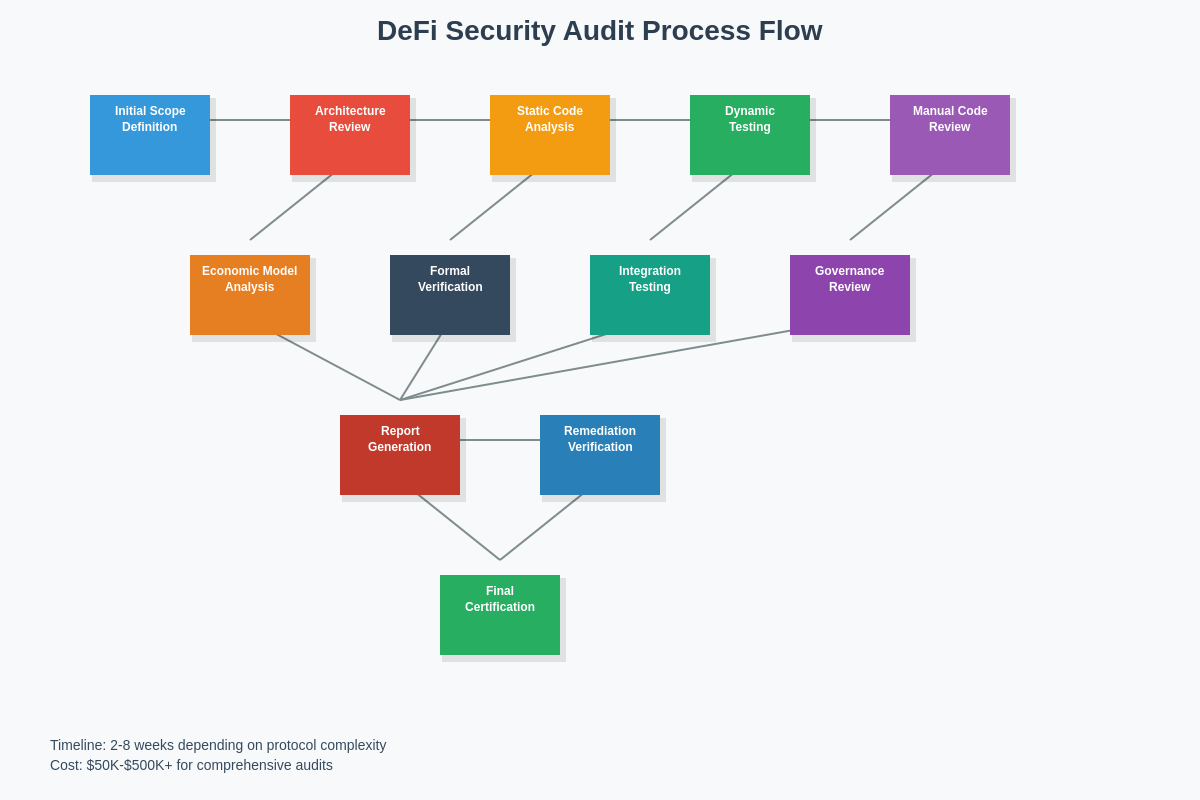
Fundamental Components of Professional DeFi Audits
Professional DeFi security audits typically encompass multiple distinct phases designed to comprehensively evaluate different aspects of protocol security, with each phase employing specialized methodologies and tools to identify specific categories of vulnerabilities and risks. The initial reconnaissance phase involves thorough documentation review, architectural analysis, and understanding of the protocol’s intended functionality, economic incentives, and potential attack surfaces.
Static analysis represents a critical component of modern DeFi audits, utilizing automated tools to scan smart contract code for common vulnerability patterns, coding errors, and deviations from security best practices. Advanced static analysis tools can identify issues such as reentrancy vulnerabilities, integer overflow conditions, improper access controls, and gas optimization opportunities that could impact protocol performance or security.
Dynamic analysis and fuzzing techniques involve executing smart contracts in controlled environments with various input parameters to identify edge cases, unexpected behaviors, and potential exploit scenarios that might not be apparent through static code review alone. These techniques often reveal complex interaction bugs that only manifest under specific conditions or when multiple functions are called in particular sequences.
Manual code review conducted by experienced security auditors remains irreplaceable for identifying logic flaws, design vulnerabilities, and complex attack vectors that automated tools might miss. Expert auditors bring deep understanding of common DeFi attack patterns, economic incentive structures, and emerging threat vectors that enable them to identify sophisticated vulnerabilities requiring human insight and creativity to discover.
Formal verification represents the most rigorous approach to smart contract security analysis, involving mathematical proofs that demonstrate the correctness of critical protocol properties under all possible execution scenarios. While formal verification is computationally intensive and requires specialized expertise, it provides the highest level of assurance for critical smart contract functions, particularly those involving fund custody, mathematical calculations, and access controls.
Evaluating Audit Firm Credibility and Methodology
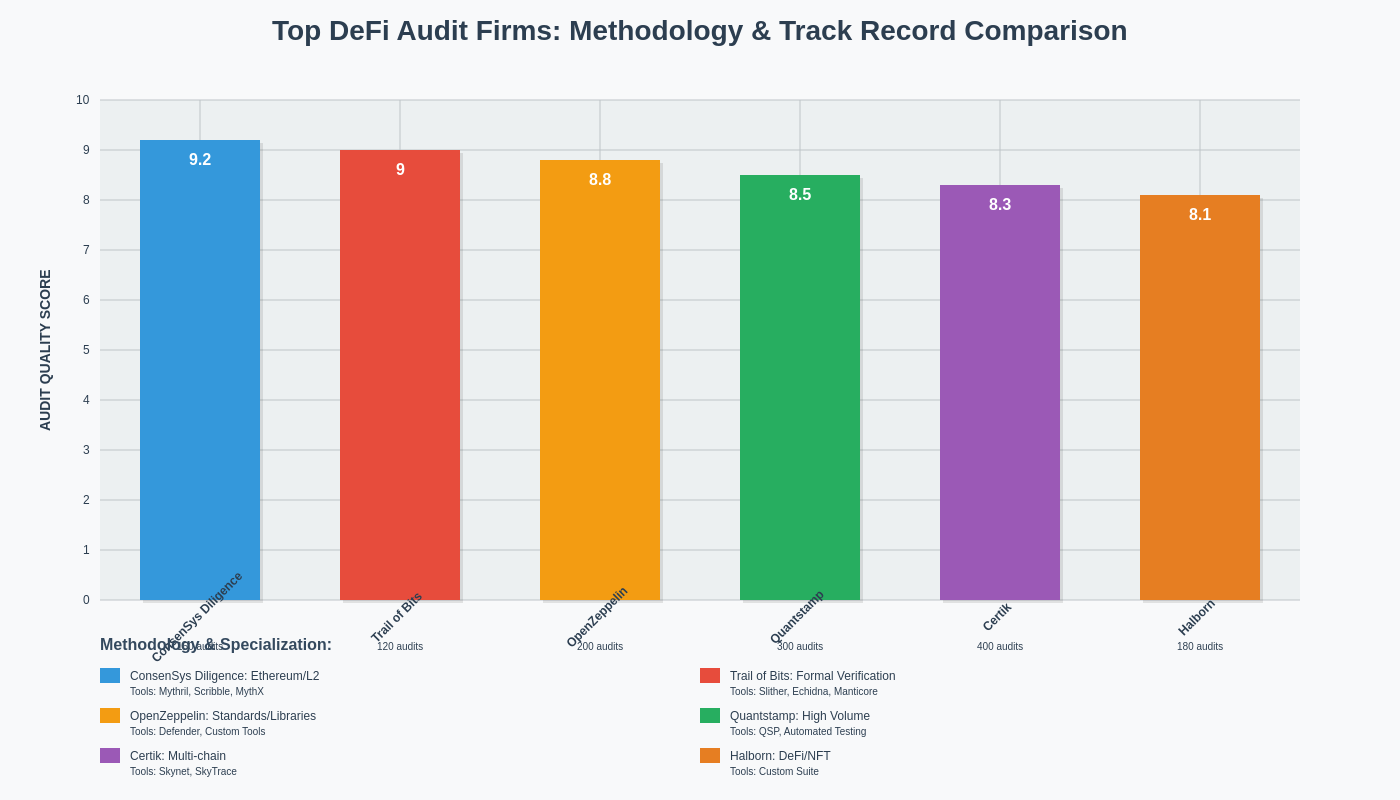
The credibility and methodology of audit firms varies dramatically across the DeFi security landscape, with some firms providing thorough, professional analysis while others offer superficial reviews that may miss critical vulnerabilities. Evaluating audit firm credibility requires examining their track record, methodology transparency, team expertise, and historical performance in identifying vulnerabilities that were subsequently exploited in production environments.
Reputable audit firms maintain detailed public records of their audit methodologies, tool usage, and findings from previous engagements, enabling potential clients and protocol users to assess the thoroughness and effectiveness of their security evaluation processes. Leading firms typically employ teams of experienced security researchers with backgrounds in smart contract development, formal verification, cryptography, and exploit development, providing diverse perspectives essential for comprehensive security analysis.
The methodology employed by audit firms should encompass both automated and manual analysis techniques, with clear documentation of testing procedures, coverage metrics, and limitation acknowledgments. High-quality audit reports explicitly state the scope of analysis, testing methodologies employed, limitations of the review process, and recommendations for ongoing security monitoring and improvement.
Historical performance metrics provide valuable insights into audit firm effectiveness, including their success rate in identifying vulnerabilities later exploited in production, the accuracy of their severity assessments, and the quality of their remediation recommendations. Firms with strong track records typically maintain public databases of their audit findings, allowing the community to verify their effectiveness and learn from identified vulnerabilities.
The independence and conflict of interest policies of audit firms represent critical factors in evaluating the reliability of their findings, as financial relationships between auditors and protocol teams can potentially compromise the objectivity and thoroughness of security evaluations. Reputable firms maintain clear policies regarding conflict of interest disclosure, payment structures that align incentives with thorough analysis rather than favorable outcomes, and mechanisms for ensuring audit independence.
Interpreting Vulnerability Classifications and Severity Levels
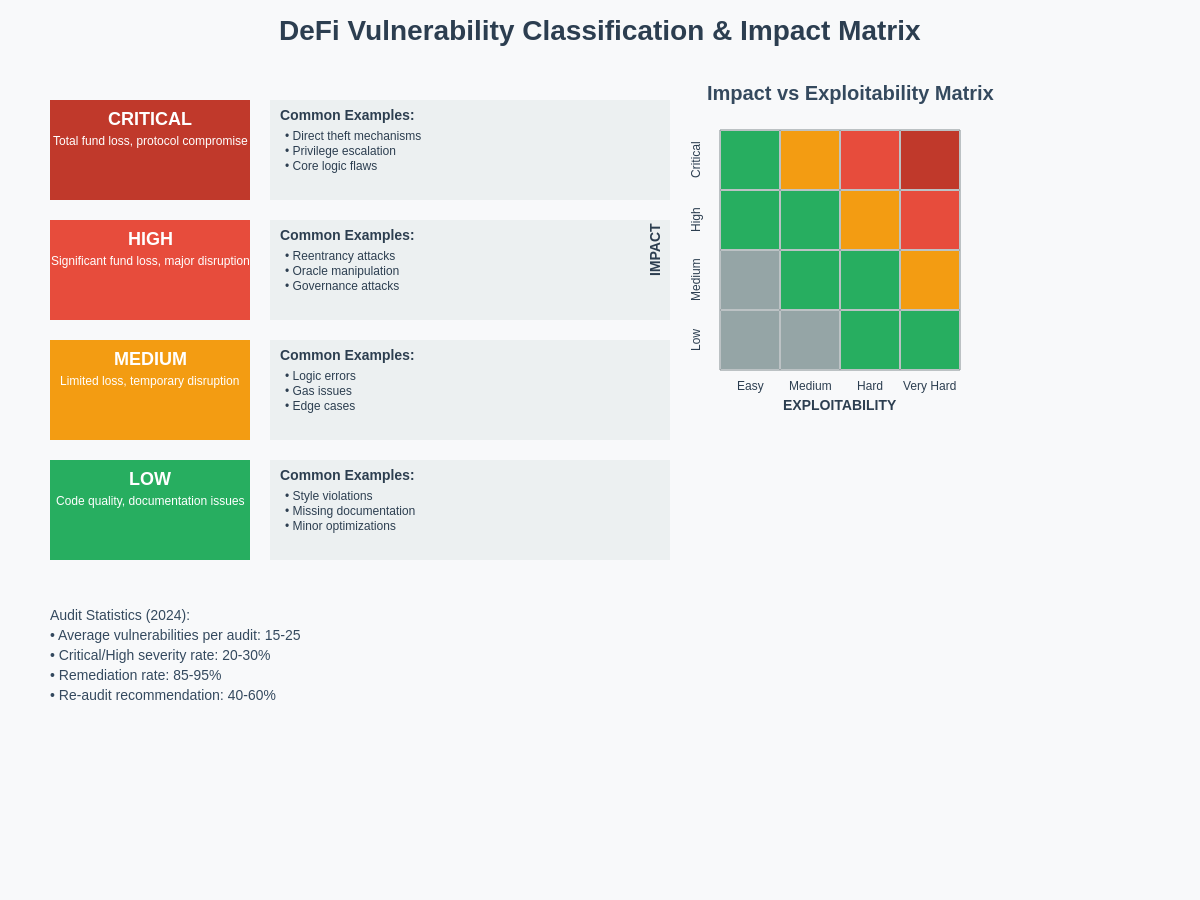
Professional DeFi audit reports categorize identified vulnerabilities according to standardized severity classifications that reflect both the potential impact and exploitability of discovered issues, enabling readers to prioritize remediation efforts and assess overall protocol risk levels. Understanding these classification systems requires familiarity with common vulnerability types, impact assessment methodologies, and the factors that influence severity determinations.
Critical severity vulnerabilities typically involve issues that could result in total loss of user funds, protocol compromise, or systemic failures affecting the entire DeFi ecosystem. These vulnerabilities often include direct theft mechanisms, privilege escalation attacks, or fundamental flaws in core protocol logic that could be exploited with minimal effort or resources by malicious actors.
High severity issues generally encompass vulnerabilities that could result in significant financial losses, partial fund theft, or serious disruption of protocol functionality, though they may require specific conditions or sophisticated attack techniques to exploit successfully. Examples include reentrancy vulnerabilities in withdrawal functions, oracle manipulation attacks, or governance attacks that could compromise protocol parameters.
Medium severity vulnerabilities typically involve issues that could cause limited financial losses, temporary service disruptions, or degraded protocol performance, but do not pose immediate threats to user funds or overall protocol security. These issues might include gas optimization opportunities, minor logic errors, or edge cases that could cause unexpected behavior under unusual circumstances.
Low severity findings generally encompass code quality issues, documentation problems, or theoretical vulnerabilities that are unlikely to be exploited in practice but represent opportunities for improvement in code maintainability, user experience, or future security posture. While low severity issues may not pose immediate risks, addressing them can prevent future security problems and improve overall protocol quality.
The classification methodology employed by audit firms should consider multiple factors including exploitability, potential impact, attack complexity, and the likelihood of successful exploitation under realistic conditions. Quality audit reports provide detailed justifications for severity classifications, including specific exploit scenarios, impact assessments, and recommendations for remediation prioritization.
Analyzing Smart Contract Architecture and Design Patterns
Evaluating DeFi protocol safety through audit reports requires understanding the underlying smart contract architecture and design patterns employed by the protocol, as these fundamental decisions significantly impact both security posture and potential attack surfaces. Modern DeFi protocols typically employ complex architectures involving multiple interacting contracts, proxy patterns for upgradeability, and integration with external protocols that create additional security considerations.
Modular smart contract architectures offer advantages in terms of code maintainability, testing efficiency, and upgrade flexibility, but they also introduce additional complexity in terms of inter-contract communication, access control management, and potential for composition attacks that exploit interactions between different contract components. Audit reports should thoroughly evaluate the security implications of chosen architectural patterns and identify potential vulnerabilities arising from contract interactions.
Upgradeability mechanisms represent critical security considerations for DeFi protocols, as they enable protocol improvements and bug fixes while potentially introducing centralization risks and attack vectors that could compromise protocol immutability guarantees. Common upgradeability patterns include proxy contracts, diamond patterns, and modular architectures, each with distinct security implications that require careful evaluation in audit reports.
Access control implementations across DeFi protocols vary significantly in sophistication and security, with some protocols employing simple owner-based controls while others implement complex role-based systems with time delays, multi-signature requirements, and governance-based permissions. Audit reports should carefully evaluate access control mechanisms to identify potential privilege escalation vulnerabilities, centralization risks, and governance attack vectors.
External dependencies and oracle integrations represent significant attack surfaces for DeFi protocols, as vulnerabilities or manipulations in external systems can compromise protocol security regardless of the quality of internal smart contract code. Comprehensive audit reports evaluate the security implications of external dependencies, oracle choice and implementation, and potential for manipulation or failure of external data sources.
Gas optimization and efficiency considerations impact both protocol security and user experience, as inefficient implementations can create denial-of-service vulnerabilities, increase transaction costs, and potentially enable economic attacks that exploit gas consumption patterns. Quality audit reports identify gas optimization opportunities while ensuring that efficiency improvements do not compromise security guarantees.
Economic Model Security and Tokenomics Analysis
Beyond technical smart contract security, comprehensive DeFi audit reports must evaluate the economic security of protocol tokenomics, incentive structures, and game-theoretic mechanisms that govern protocol behavior and user interactions. Economic vulnerabilities can be just as damaging as technical exploits, potentially enabling sophisticated attacks that manipulate protocol incentives to extract value or destabilize the system.
Token distribution mechanisms and initial allocation structures significantly impact protocol security by determining the concentration of governance power, potential for market manipulation, and long-term sustainability of protocol incentives. Audit reports should analyze token distribution for potential centralization risks, governance vulnerabilities, and economic attack vectors that could compromise protocol decentralization or stability.
Liquidity mining and yield farming incentive structures require careful economic analysis to identify potential for unsustainable rewards, token inflation risks, and gaming mechanisms that could be exploited by sophisticated actors to extract disproportionate value from protocol rewards. Understanding the mathematical models underlying these incentive systems helps identify potential for economic exploits and long-term sustainability issues.
Governance token mechanics and voting systems represent critical components of DeFi protocol security, as governance vulnerabilities can enable attackers to gain control over protocol parameters, treasury funds, or upgrade mechanisms through vote buying, flash loan governance attacks, or other manipulation strategies. Comprehensive audits evaluate governance security through both technical and economic lenses.
Oracle dependencies and price feed mechanisms require thorough security analysis, as oracle manipulation attacks represent one of the most common and devastating attack vectors in DeFi. Audit reports should evaluate oracle choice, implementation, fallback mechanisms, and potential for price manipulation attacks that could enable arbitrage opportunities or protocol exploitation.
Slippage protection, maximum extractable value considerations, and front-running protection mechanisms impact both user security and protocol sustainability by determining how effectively the protocol protects users against various forms of transaction ordering manipulation and value extraction by sophisticated actors.
Red Flags and Warning Signs in Audit Reports
Experienced DeFi users learn to identify specific warning signs and red flags in audit reports that indicate elevated risk levels or inadequate security evaluation, enabling them to make more informed decisions about protocol participation and risk management. These warning signs often involve limitations in audit scope, inadequate remediation of identified issues, or concerning patterns in vulnerability disclosure and resolution.
Incomplete audit scope represents a significant red flag, particularly when critical protocol components such as governance mechanisms, oracle integrations, or upgrade pathways are excluded from security evaluation. Protocols that undergo limited-scope audits may have substantial unaudited attack surfaces that could be exploited by sophisticated attackers, making comprehensive scope evaluation essential for risk assessment.
Inadequate remediation of identified vulnerabilities, particularly those classified as high or critical severity, indicates potential ongoing security risks that could be exploited in production environments. Quality protocols demonstrate commitment to security by promptly addressing all identified issues and providing detailed documentation of remediation efforts and verification procedures.
Time pressure and rushed audit timelines often result in reduced audit quality and increased likelihood of missing critical vulnerabilities, making timeline evaluation an important factor in assessing audit reliability. Protocols that allow insufficient time for thorough security evaluation may be prioritizing speed to market over user safety, creating elevated risk levels for early adopters.
Conflicts of interest between audit firms and protocol teams can compromise audit objectivity and thoroughness, particularly when payment structures incentivize favorable findings over comprehensive security evaluation. Transparent disclosure of business relationships, payment structures, and potential conflicts of interest helps users assess the independence and reliability of audit findings.
Multiple unresolved findings across different audit firms or security researchers may indicate systematic security issues or inadequate development practices that extend beyond individual vulnerabilities. Patterns of similar findings across multiple audits suggest potential for additional undiscovered vulnerabilities and elevated overall risk levels.
Lack of transparency in audit methodology, testing procedures, or limitation acknowledgment makes it difficult for users to assess the thoroughness and reliability of security evaluations. Reputable audit firms provide detailed methodology documentation that enables users to understand the scope and limitations of security analysis.
Post-Audit Monitoring and Ongoing Security Assessment
Security evaluation does not end with initial audit completion, as DeFi protocols undergo continuous development, parameter updates, and integration changes that can introduce new vulnerabilities or attack vectors requiring ongoing monitoring and assessment. Understanding how to evaluate ongoing security practices and monitoring mechanisms provides critical insights into long-term protocol safety and risk management.
Bug bounty programs and responsible disclosure policies indicate protocol commitment to ongoing security improvement and community-driven vulnerability discovery, providing additional layers of security evaluation beyond formal audits. Comprehensive market analysis tools help traders monitor protocol token performance and potential security-related price movements that might indicate emerging vulnerabilities or exploits.
Incident response procedures and security monitoring capabilities demonstrate protocol preparedness for handling potential security breaches, oracle failures, or other emergency situations that could threaten user funds or protocol stability. Quality protocols maintain detailed incident response plans, emergency pause mechanisms, and monitoring systems that enable rapid detection and response to potential threats.
Regular security updates and patch management processes indicate ongoing commitment to maintaining security posture as new vulnerabilities are discovered and attack techniques evolve. Protocols that maintain active security improvement programs demonstrate greater long-term safety compared to those that treat security as a one-time consideration.
Community security engagement and transparent communication about security issues, updates, and improvements provide valuable insights into protocol security culture and commitment to user protection. Active engagement with security researchers, timely disclosure of issues, and educational content about protocol security indicate mature security practices.
Integration security considerations become increasingly important as DeFi protocols compose with each other to create complex financial products, requiring ongoing evaluation of integration risks, external dependencies, and potential for composition attacks that exploit interactions between different protocols.
Practical Framework for User Security Evaluation
Developing a systematic approach to evaluating DeFi protocol safety through audit reports enables users to make more informed decisions about risk levels, fund allocation, and participation strategies across different protocols and investment opportunities. This framework should incorporate both technical and economic security considerations while acknowledging the limitations and uncertainties inherent in security evaluation.
Risk assessment matrices help users categorize protocols based on audit quality, vulnerability remediation, track record, and other security indicators, enabling comparative analysis and portfolio diversification strategies that balance potential returns against security risks. Understanding how to weight different risk factors based on personal risk tolerance and investment objectives helps optimize DeFi participation strategies.
Due diligence checklists ensure comprehensive evaluation of all relevant security factors, including audit firm credibility, scope completeness, vulnerability remediation, ongoing security practices, and community feedback. Systematic evaluation processes reduce the likelihood of overlooking critical security considerations that could impact investment outcomes.
Portfolio diversification strategies should consider correlation between protocol security risks, shared dependencies, and potential for systemic failures that could impact multiple protocols simultaneously. Understanding these correlations helps construct more resilient DeFi portfolios that can withstand individual protocol failures or broader ecosystem attacks.
Monitoring and alerting systems enable users to track ongoing security developments, new vulnerability disclosures, and changes in protocol risk profiles that might necessitate portfolio adjustments or risk management actions. Active monitoring helps users respond promptly to emerging threats and opportunities in the rapidly evolving DeFi landscape.
Position sizing and risk management strategies should reflect individual security assessments and risk tolerance levels, with higher-risk protocols receiving smaller allocations and stronger security protocols supporting larger positions. Dynamic position management based on evolving security assessments helps optimize risk-adjusted returns across diverse DeFi opportunities.
Emerging Trends in DeFi Security and Audit Evolution
The DeFi security landscape continues evolving rapidly as new attack vectors emerge, audit methodologies improve, and technological advances enable more sophisticated security analysis techniques. Understanding these trends helps users anticipate future developments in protocol security and audit practices that will impact investment and participation strategies.
Automated security monitoring and real-time threat detection systems are becoming increasingly sophisticated, enabling continuous monitoring of protocol behavior, transaction patterns, and potential attack indicators that could signal emerging threats. These systems complement traditional audits by providing ongoing security assessment and early warning capabilities for various attack scenarios.
Formal verification techniques are becoming more accessible and widely adopted, providing mathematical guarantees about critical protocol properties and helping identify subtle vulnerabilities that might escape traditional audit methodologies. As formal verification tools mature, they will likely become standard components of comprehensive security evaluation processes.
Cross-chain security considerations are becoming increasingly important as DeFi protocols expand across multiple blockchain networks, creating additional complexity in terms of bridge security, consensus mechanism differences, and potential for cross-chain attacks that exploit differences between network security models.
Regulatory compliance and audit requirements are evolving rapidly as governments develop frameworks for DeFi regulation, potentially mandating specific audit standards, ongoing monitoring requirements, and compliance certifications that will impact how protocols approach security evaluation and reporting.
Artificial intelligence and machine learning applications in security analysis are showing promise for identifying complex vulnerability patterns, predicting potential attack vectors, and automating certain aspects of security evaluation that could improve audit efficiency and effectiveness.
Building Personal Security Assessment Capabilities
Developing independent security assessment capabilities enables DeFi users to supplement professional audit reports with their own analysis, providing additional confidence in security evaluations and helping identify potential issues that might have been overlooked in formal audits. While comprehensive security evaluation requires specialized expertise, users can develop practical skills for basic vulnerability identification and risk assessment.
Code reading skills for smart contract analysis help users understand protocol logic, identify obvious vulnerabilities, and verify that implemented functionality matches documented behavior. While most users cannot conduct comprehensive security audits, basic code literacy enables more informed evaluation of protocol claims and audit findings.
Economic analysis capabilities for evaluating tokenomics, incentive structures, and game-theoretic mechanisms provide insights into potential economic vulnerabilities and long-term protocol sustainability that complement technical security assessments. Understanding economic security helps identify protocols with sustainable business models and robust incentive alignment.
Community engagement and information gathering from multiple sources helps users develop comprehensive understanding of protocol reputation, developer track record, and community sentiment that may not be reflected in formal audit reports. Active participation in protocol communities provides early access to information about potential issues and developments.
Professional charting and analysis tools enable users to monitor protocol token performance and identify patterns that might indicate security concerns or market sentiment changes related to protocol safety and reliability.
Risk management discipline and systematic decision-making processes help users maintain consistent security standards and avoid emotional decisions that could compromise portfolio safety. Developing and following systematic evaluation criteria helps maintain investment discipline across changing market conditions and opportunities.
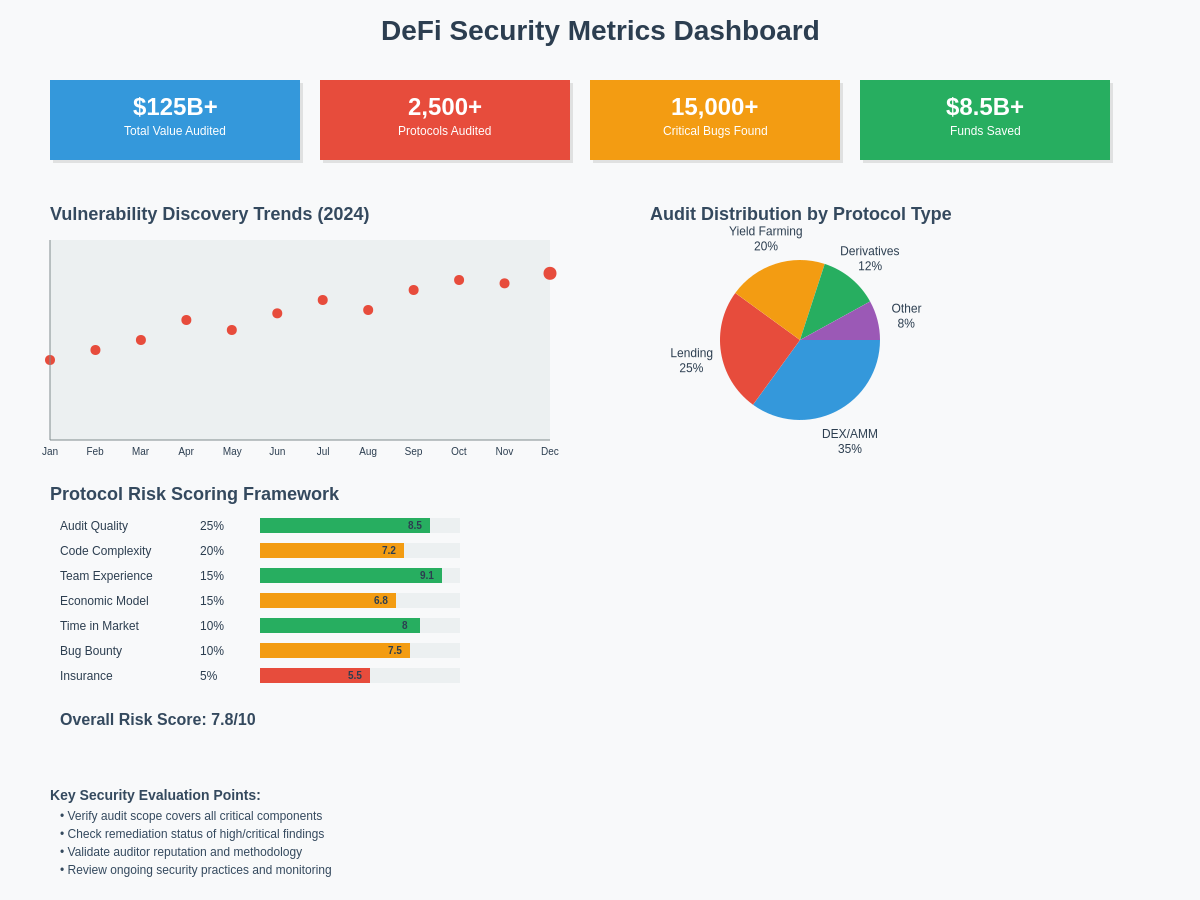
Future of DeFi Security and Audit Standards
The evolution of DeFi security practices and audit standards will significantly impact how users evaluate protocol safety and make participation decisions in the coming years. Understanding likely developments in security technology, regulatory requirements, and industry standards helps users prepare for changes in the DeFi security landscape.
Standardization of audit methodologies and reporting formats will likely improve the comparability and reliability of security evaluations across different protocols and audit firms, making it easier for users to assess relative security levels and make informed decisions about protocol participation.
Integration of insurance and protection mechanisms directly into DeFi protocols may provide additional security layers and risk mitigation options for users, though these mechanisms will require their own security evaluation and understanding of coverage limitations and exclusions.
Decentralized audit networks and community-driven security evaluation may supplement traditional audit firms with distributed security analysis capabilities, potentially improving coverage and reducing costs while requiring new frameworks for evaluating the reliability and credibility of distributed audit results.
Continuous security monitoring and real-time risk assessment capabilities will likely become standard features of mature DeFi protocols, providing users with ongoing visibility into protocol security status and enabling more dynamic risk management strategies based on current threat levels and protocol health metrics.
As the DeFi ecosystem matures, the relationship between security, regulation, and innovation will continue evolving, requiring users to adapt their evaluation frameworks and risk management strategies to changing technological capabilities, regulatory requirements, and market dynamics that will shape the future of decentralized finance.
Disclaimer: This article is for informational purposes only and does not constitute financial, investment, or legal advice. Cryptocurrency and DeFi investments carry significant risks including total loss of capital. Smart contract audits do not guarantee protocol security, and users should conduct their own research and consider their risk tolerance before participating in any DeFi protocol. Past performance does not indicate future results, and all investments should be made with careful consideration of individual financial circumstances and risk management strategies.