https://www.tradingview.com/pine-script-reference/v6/?aff_id=112991&source=pine2-16-tradingview
The Evolution of Institutional Cryptocurrency Custody
The cryptocurrency industry has witnessed a dramatic transformation in custody solutions as institutional investors increasingly demand enterprise-grade security measures that match or exceed traditional financial infrastructure standards. Exchange custody solutions have evolved from simple cold storage implementations to sophisticated multi-layered security architectures that incorporate advanced cryptographic techniques, regulatory compliance frameworks, and institutional-grade operational procedures designed to protect billions of dollars in digital assets.
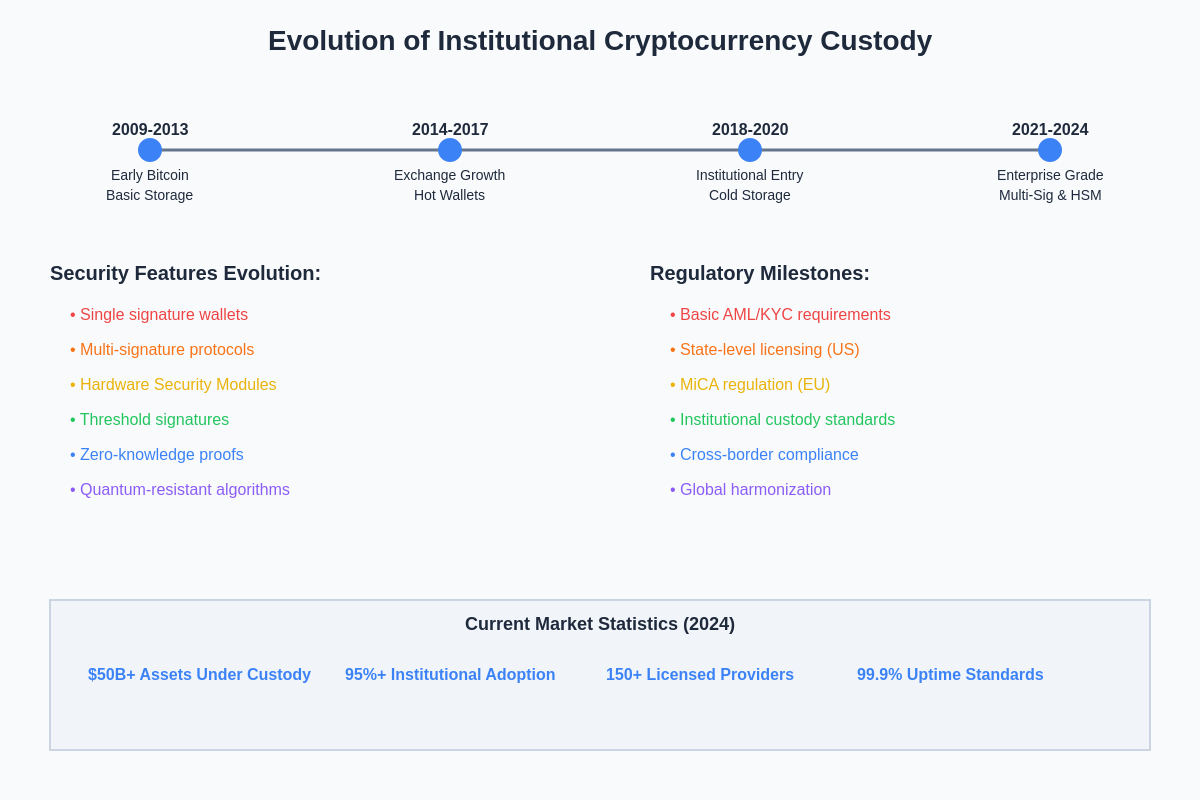
The emergence of institutional-grade custody solutions represents a critical milestone in cryptocurrency market maturation, enabling pension funds, endowments, hedge funds, and corporate treasuries to safely participate in digital asset markets while meeting their fiduciary responsibilities and regulatory requirements. These solutions address the unique challenges of cryptocurrency custody, including key management complexity, regulatory uncertainty, operational security requirements, and the need for transparent audit trails that satisfy institutional risk management standards.
Modern exchange custody solutions have incorporated lessons learned from decades of traditional financial services while adapting to the unique characteristics of blockchain-based assets. The development of these solutions has been driven by increasing institutional adoption, regulatory clarity in major jurisdictions, and technological advances that enable more sophisticated security architectures without compromising operational efficiency.
Regulatory Framework and Compliance Requirements
The regulatory landscape governing cryptocurrency custody has become increasingly complex as jurisdictions around the world develop comprehensive frameworks for digital asset service providers. In the United States, state-level banking regulators, the Office of the Comptroller of the Currency, and federal securities regulators have established detailed requirements for cryptocurrency custody operations, including capital requirements, cybersecurity standards, and operational controls that mirror traditional banking and securities custody regulations.
European markets have implemented the Markets in Crypto-Assets regulation, which establishes comprehensive requirements for crypto-asset service providers including custody and administration services. These regulations mandate specific technical standards, operational procedures, and risk management frameworks that custody providers must implement to operate legally within the European Union, creating harmonized standards that facilitate cross-border institutional participation in cryptocurrency markets.
The regulatory framework extends beyond basic licensing requirements to encompass detailed operational standards including segregation of client assets, comprehensive insurance coverage, regular third-party audits, and specific reporting requirements that enable regulatory oversight of custody operations. Compliance with these frameworks requires significant investment in legal, technical, and operational infrastructure that many traditional exchanges struggle to implement without specialized expertise and substantial capital investment.
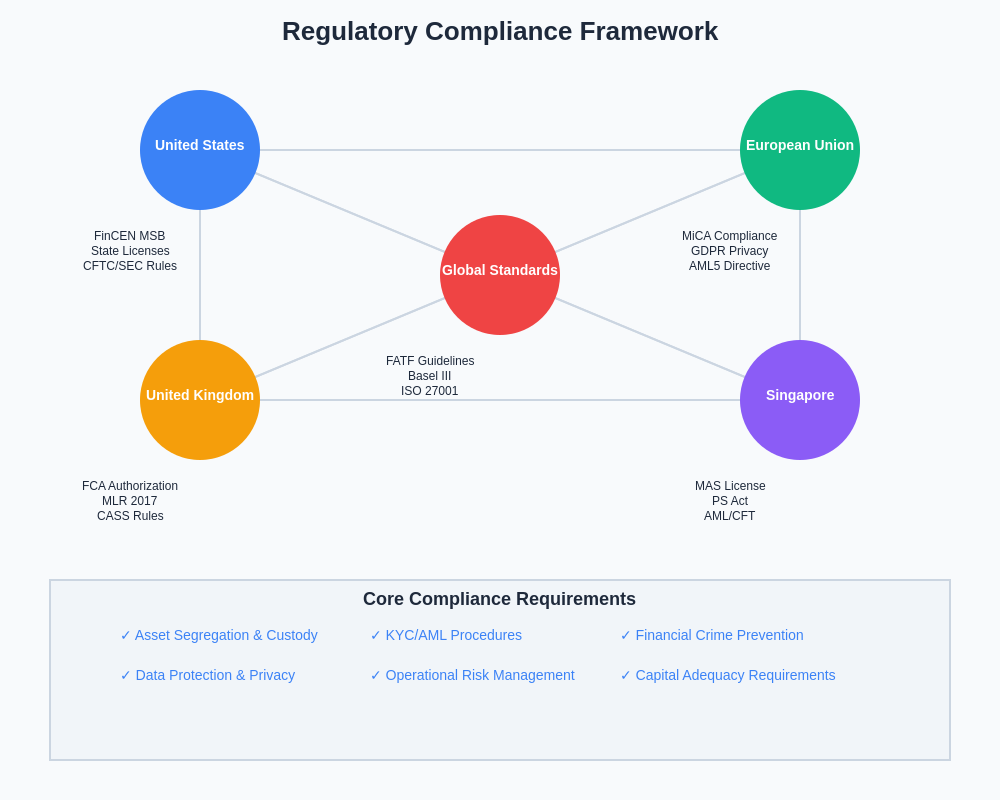
Anti-money laundering and know-your-customer requirements for institutional custody solutions often exceed those applied to retail trading services, reflecting the larger transaction volumes and higher risk profiles associated with institutional clients. These enhanced due diligence requirements include ongoing monitoring of transaction patterns, verification of beneficial ownership for complex institutional structures, and reporting of suspicious activities that may indicate market manipulation or other illicit activities.
Multi-Signature and Hardware Security Architecture
Multi-signature technology forms the foundation of most institutional-grade custody solutions, providing mathematically verifiable security that distributes signing authority across multiple parties or devices to prevent single points of failure. Advanced multi-signature implementations utilize threshold signature schemes that can require approval from any subset of authorized signers, enabling flexible governance structures that balance security with operational efficiency for different types of institutional clients.
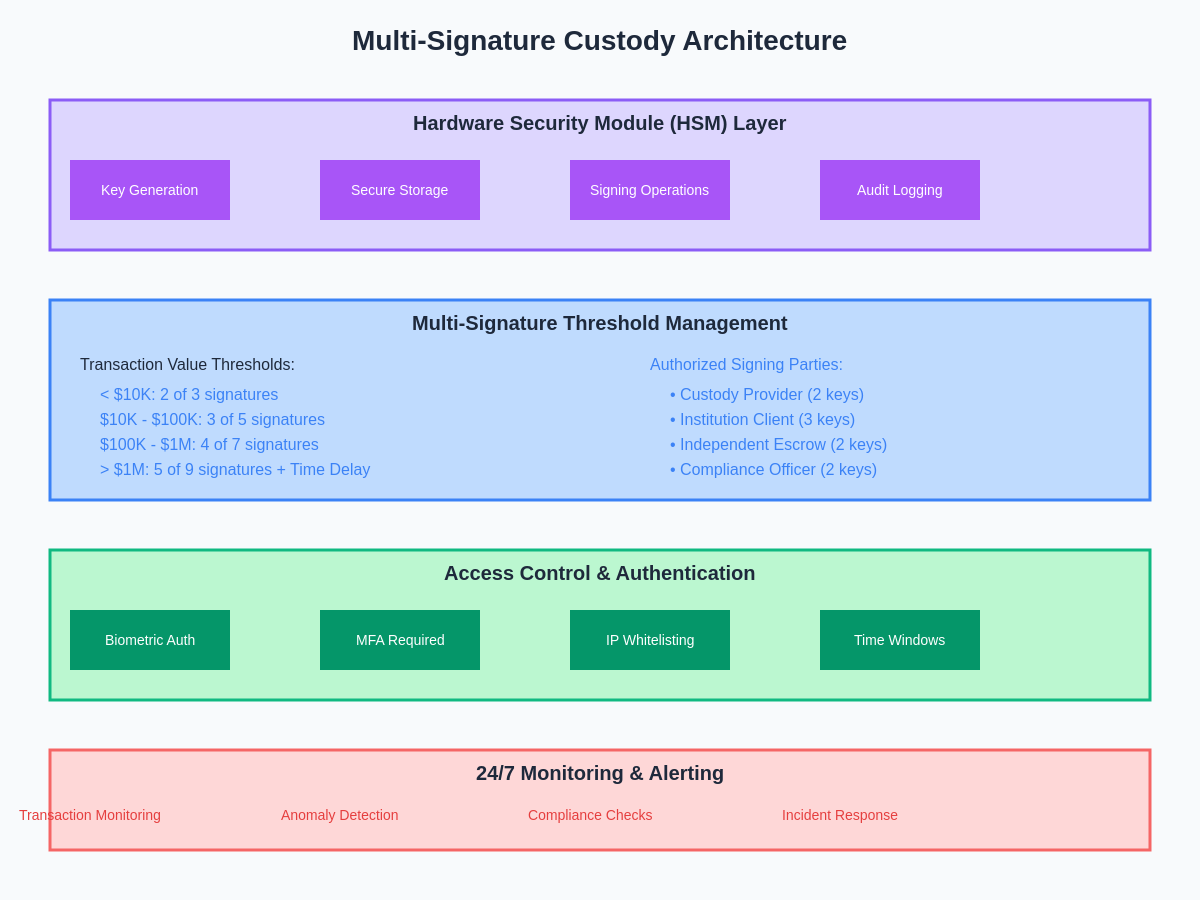
Hardware Security Modules represent another critical component of institutional custody architecture, providing tamper-resistant hardware environments for key generation, storage, and cryptographic operations. These specialized devices undergo rigorous certification processes including FIPS 140-2 Level 3 or higher validation, ensuring they meet strict physical and logical security requirements that institutional clients demand for protecting high-value digital assets.
The integration of multi-signature protocols with HSM technology creates layered security architectures where critical operations require both hardware-based authentication and distributed approval processes. This combination provides protection against a wide range of attack vectors including insider threats, external cyber attacks, and physical compromise of individual security devices, while maintaining the operational flexibility necessary for institutional trading and asset management activities.
Advanced implementations incorporate time-locked transactions, geographic distribution of signing keys, and automated policy enforcement that can prevent unauthorized transactions even when multiple signatures are compromised. These features provide additional security layers that are particularly important for institutional clients managing large portfolios or operating under strict regulatory requirements that mandate specific operational controls.
Institutional Key Management Protocols
Key management represents perhaps the most critical aspect of institutional cryptocurrency custody, requiring sophisticated protocols that balance security, accessibility, and operational efficiency while meeting regulatory requirements for asset protection and audit trail maintenance. Institutional key management systems typically employ hierarchical deterministic key derivation schemes that enable generation of unlimited child keys from master seeds while maintaining mathematical relationships that facilitate backup and recovery procedures.
The physical security of key material requires specialized facilities that meet or exceed traditional financial industry standards, including geographically distributed secure storage locations, biometric access controls, and environmental monitoring systems that detect and respond to unauthorized access attempts. Many institutional custody providers maintain multiple secure facilities across different jurisdictions to provide geographic redundancy while complying with local regulatory requirements.
Key ceremony procedures for institutional clients involve multi-party computation protocols that enable secure key generation and backup without any single party having access to complete key material. These ceremonies typically require participation from the custody provider, the institutional client, and independent third parties who collectively generate and verify cryptographic keys through mathematically provable processes that create complete audit trails.
Recovery procedures for institutional key management systems must balance the need for asset accessibility with security requirements that prevent unauthorized access to client funds. Advanced systems implement threshold recovery schemes that require multiple independent parties to authorize key recovery operations, with different threshold requirements for different types of operations based on transaction values and institutional risk policies.
Cold Storage and Air-Gapped Systems
Cold storage systems for institutional custody solutions utilize air-gapped computing environments that are physically isolated from internet connectivity to prevent remote attacks while maintaining the operational capabilities necessary for periodic transaction signing and portfolio management activities. These systems incorporate specialized hardware configurations that enable secure communication with external systems through cryptographically verified message passing without compromising the isolation of critical key material.
The operational procedures for cold storage systems require sophisticated workflows that balance security requirements with the need for timely transaction processing when institutional clients require asset movement for trading, rebalancing, or distribution activities. Many systems implement time-delayed transaction approval processes that provide additional security against unauthorized access while enabling legitimate operations to proceed within acceptable timeframes.
Geographic distribution of cold storage systems provides protection against natural disasters, political instability, and other location-specific risks that could affect asset accessibility. Institutional custody providers typically maintain cold storage facilities in multiple countries with different legal and regulatory frameworks, ensuring that client assets remain accessible even if individual locations become unavailable due to regulatory changes or other external factors.
The backup and disaster recovery procedures for cold storage systems must ensure complete asset recovery capabilities while maintaining the security properties that make cold storage effective. This requires sophisticated key sharing schemes, secure backup procedures, and regular testing of recovery processes to verify that institutional clients can regain access to their assets even in worst-case scenarios involving multiple simultaneous failures.
https://www.tradingview.com/symbols/BTCUSD/?aff_id=112991&source=pine2-16-tradingview
Insurance and Risk Management
Insurance coverage for institutional cryptocurrency custody has evolved significantly as specialized insurers develop products specifically designed to address the unique risks associated with digital asset custody and the substantial values involved in institutional portfolios. Comprehensive coverage typically includes theft protection for both hot and cold storage systems, coverage for social engineering attacks, protection against insider threats, and business interruption insurance that covers operational disruptions resulting from security incidents.
The risk assessment procedures for institutional custody insurance require detailed evaluation of technical security measures, operational procedures, regulatory compliance status, and the track record of custody providers and their key personnel. Insurers typically require regular third-party security audits, penetration testing results, and detailed documentation of security procedures before providing coverage, with ongoing monitoring requirements that ensure continued compliance with security standards.
Risk management frameworks for institutional custody solutions incorporate quantitative risk modeling that evaluates the probability and potential impact of different types of security incidents across various threat vectors. These models help custody providers optimize their security investments and insurance coverage while providing institutional clients with transparent information about the risks associated with different custody arrangements and operational procedures.
The integration of insurance coverage with custody operations requires sophisticated claims procedures that can rapidly determine the extent of losses while preserving evidence necessary for potential recovery efforts. Many institutional custody providers maintain dedicated incident response teams that work closely with insurers, law enforcement, and blockchain analysis firms to maximize the chances of asset recovery while minimizing disruption to ongoing operations.
Segregation and Omnibus Account Models
Asset segregation represents a fundamental requirement for institutional custody solutions, ensuring that client assets are legally and operationally isolated from the custody provider’s own assets and from other clients’ holdings. Legal segregation requires careful structuring of custody arrangements, often involving special purpose vehicles or trust structures that provide clear legal ownership rights and bankruptcy-remote protections that ensure client assets are not subject to claims against the custody provider.
Operational segregation requires sophisticated account management systems that maintain complete isolation of client assets at the blockchain level while enabling efficient management and reporting across large institutional portfolios. Many custody providers implement per-client address generation schemes that ensure each institutional client’s assets are held in addresses that are cryptographically isolated from other clients, providing transparent on-chain verification of asset segregation.
Omnibus account models offer alternative approaches that can provide operational efficiencies for certain types of institutional clients while maintaining appropriate protections through legal and operational controls rather than blockchain-level segregation. These models require sophisticated internal accounting systems and enhanced legal protections but can enable more efficient portfolio management and trading operations for institutional clients with compatible risk profiles.
The choice between segregated and omnibus models depends on various factors including regulatory requirements in the client’s jurisdiction, the client’s internal risk management policies, operational efficiency requirements, and the specific types of digital assets being held. Many institutional custody providers offer multiple models to accommodate different client preferences and regulatory environments.
Audit and Compliance Reporting
Institutional custody solutions require comprehensive audit capabilities that provide transparency into asset holdings, operational procedures, and security controls while meeting the reporting requirements of institutional clients and their regulators. Real-time proof-of-reserves capabilities enable continuous verification of asset holdings through cryptographic proofs that demonstrate the custody provider maintains sufficient assets to meet all client obligations without revealing sensitive information about individual client holdings.
Third-party audit procedures for institutional custody operations typically follow established frameworks such as SOC 2 Type II examinations that evaluate the design and operating effectiveness of internal controls over extended periods. These audits examine technical security measures, operational procedures, access controls, and change management processes to provide independent verification that custody operations meet institutional security and operational standards.
Regulatory reporting requirements for institutional custody solutions often include detailed transaction reporting, asset holding reports, and operational incident disclosures that must be submitted to relevant regulatory authorities on specified schedules. These reporting requirements necessitate sophisticated data management systems that can generate accurate reports while maintaining client confidentiality and protecting sensitive operational information.
Compliance monitoring systems for institutional custody operations must continuously evaluate operations against applicable regulatory requirements, internal policies, and client-specific requirements to identify potential compliance issues before they result in regulatory violations or client concerns. These systems typically incorporate automated monitoring capabilities alongside manual review processes that ensure comprehensive coverage of all relevant compliance requirements.
Integration with Trading and Portfolio Management
The integration of custody solutions with institutional trading and portfolio management systems requires sophisticated API architectures that enable secure and efficient asset movement while maintaining the security properties of custody operations. These integrations must support various trading strategies including algorithmic trading, portfolio rebalancing, and risk management activities while providing comprehensive audit trails and transaction approval workflows.
Settlement and clearing procedures for institutional cryptocurrency trading often require coordination between custody providers, trading venues, and clearinghouses to ensure efficient transaction processing while maintaining custody security standards. Many institutional custody providers have developed specialized settlement systems that can process large volumes of transactions efficiently while maintaining multi-signature security requirements and providing real-time settlement confirmation.
Portfolio management integration enables institutional clients to maintain unified views of their digital asset holdings across multiple custody providers, trading venues, and blockchain networks while ensuring that portfolio management decisions can be efficiently implemented through automated trading and rebalancing systems. These integrations require sophisticated data management and reconciliation procedures that ensure accurate portfolio reporting despite the complexity of multi-provider custody arrangements.
Risk management integration enables institutional portfolio managers to implement sophisticated risk controls that consider both market risks and operational risks associated with custody arrangements. These systems can automatically implement position limits, concentration limits, and other risk controls while providing real-time monitoring of portfolio exposures across all custody providers and trading venues.
https://www.tradingview.com/symbols/ETHUSD/?aff_id=112991&source=pine2-16-tradingview
Emerging Technologies and Future Developments
Zero-knowledge proof systems are increasingly being integrated into institutional custody solutions to enable privacy-preserving verification of asset holdings and transaction authorization while maintaining the transparency requirements of institutional clients and regulators. These systems can provide mathematical proofs of asset holdings without revealing specific transaction details or portfolio compositions, enabling enhanced privacy protection for institutional clients while maintaining audit capabilities.
Threshold signature schemes represent an evolution beyond traditional multi-signature approaches, enabling more flexible signing policies and enhanced security properties through advanced cryptographic techniques. These systems can provide enhanced protection against quantum computing threats while enabling more sophisticated governance models for institutional asset management that can adapt to complex organizational structures and approval requirements.
Smart contract integration for custody operations enables programmable asset management capabilities that can automatically implement complex investment strategies, rebalancing procedures, and risk management policies while maintaining custody security standards. These systems require careful security analysis to ensure that smart contract vulnerabilities do not compromise custody security, but offer significant potential for enhancing operational efficiency and reducing operational risks.
Interoperability solutions for cross-chain asset management are becoming increasingly important as institutional portfolios include assets across multiple blockchain networks. Custody providers are developing sophisticated bridge technologies and cross-chain communication protocols that enable secure asset movement between different blockchain networks while maintaining unified custody security standards across all supported assets.
Cost Structure and Economic Considerations
The cost structure for institutional cryptocurrency custody reflects the substantial infrastructure investments required to meet institutional security and regulatory requirements, with fees typically structured as a combination of asset-based charges, transaction fees, and setup costs that reflect the complexity of institutional custody operations. Asset-based fees often range from 10 to 100 basis points annually depending on the asset types, custody model, and level of service required.
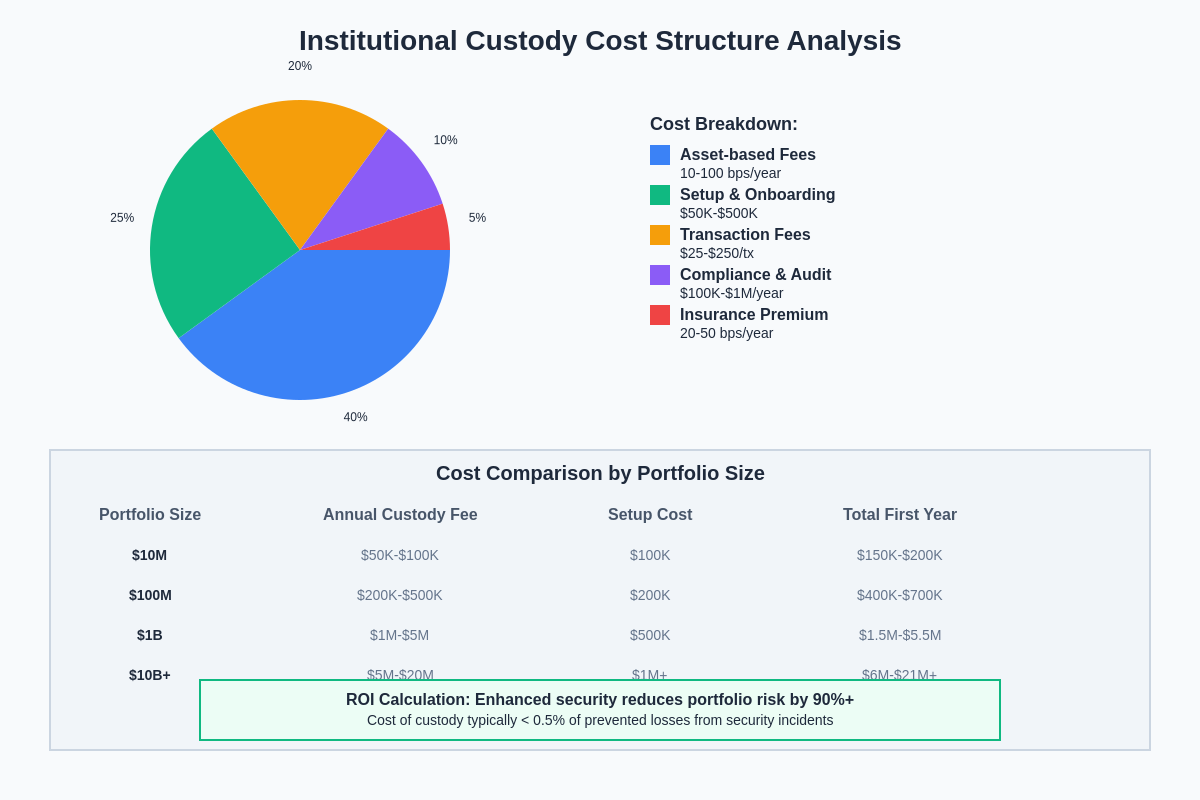
Setup and onboarding costs for institutional custody can be substantial, reflecting the need for comprehensive due diligence, custom integration development, and specialized legal documentation that addresses the specific requirements of institutional clients. These costs can range from tens of thousands to millions of dollars depending on the complexity of the custody arrangement and the level of customization required.
Operational costs for institutional custody providers include substantial investments in security infrastructure, regulatory compliance, insurance coverage, and specialized personnel that must be amortized across the custody provider’s client base. The economics of institutional custody therefore favor providers with substantial scale and institutional client bases that can support the high fixed costs of comprehensive custody infrastructure.
The total cost of ownership for institutional cryptocurrency custody must consider not only direct custody fees but also integration costs, operational overhead, and the potential costs of security incidents or operational failures. Many institutional clients find that higher-cost custody solutions provide better long-term value through enhanced security, regulatory compliance, and operational reliability that reduces overall portfolio risks.
Market Leaders and Service Providers
The institutional cryptocurrency custody market has consolidated around a relatively small number of specialized providers that have made the substantial investments necessary to meet institutional requirements for security, regulatory compliance, and operational reliability. These providers include both cryptocurrency-native companies that have evolved to serve institutional markets and traditional financial institutions that have developed cryptocurrency custody capabilities.
Cryptocurrency-native custody providers such as Coinbase Custody, BitGo, and Anchorage Digital have leveraged their deep technical expertise and early market presence to build comprehensive institutional custody platforms that serve many of the largest institutional cryptocurrency investors. These providers typically offer the most advanced technical capabilities and deepest cryptocurrency expertise while continuously evolving their services to meet changing institutional requirements.
Traditional financial institutions including State Street, BNY Mellon, and Northern Trust have developed cryptocurrency custody capabilities that leverage their existing institutional relationships and regulatory expertise while partnering with technology providers to deliver comprehensive digital asset custody solutions. These providers often appeal to institutional clients that prefer working with established financial institutions with long track records in traditional asset custody.
The competitive landscape continues to evolve as new providers enter the market and existing providers expand their capabilities, with increasing focus on specialized services such as DeFi protocol interaction, NFT custody, and support for emerging blockchain networks that institutional clients are beginning to explore. This competition drives continuous innovation in security capabilities, operational efficiency, and service offerings that benefit institutional clients.
Future Outlook and Industry Evolution
The institutional cryptocurrency custody industry is expected to continue evolving rapidly as digital asset adoption accelerates among institutional investors and regulatory frameworks become more established and harmonized across major jurisdictions. The increasing sophistication of institutional crypto investment strategies will drive demand for more advanced custody capabilities including DeFi integration, cross-chain asset management, and programmable custody solutions that can automatically implement complex investment policies.
Regulatory evolution will likely result in more standardized requirements for institutional custody operations, potentially reducing the barriers to entry for new providers while establishing minimum standards that all providers must meet. This standardization could lead to increased competition and operational efficiency while maintaining the high security standards that institutional clients require for protecting large digital asset portfolios.
Technological advances including quantum-resistant cryptography, advanced zero-knowledge proof systems, and more sophisticated multi-party computation protocols will enable new custody architectures that provide enhanced security and privacy protection while maintaining the operational capabilities necessary for institutional asset management. These advances will be particularly important as quantum computing capabilities continue to develop and potentially threaten current cryptographic security assumptions.
The integration of traditional finance and cryptocurrency custody is expected to accelerate as more institutional investors adopt hybrid portfolios that include both traditional and digital assets, driving demand for unified custody solutions that can provide consistent security and operational standards across all asset types. This convergence will likely result in new service models and operational frameworks that bridge the gap between traditional and digital asset custody while meeting the evolving needs of institutional investors.
https://www.tradingview.com/pine-script-reference/v6/?aff_id=112991&source=pine2-16-tradingview
Disclaimer: This article is for informational purposes only and does not constitute financial, investment, legal, or tax advice. Cryptocurrency investments carry significant risks including potential total loss of capital. The regulatory landscape for digital assets continues to evolve and may vary significantly across jurisdictions. Readers should conduct their own research and consult with qualified professionals before making any investment decisions. The information contained herein may not be current and is subject to change without notice. Past performance does not guarantee future results.