Learn more about crypto security with TradingView’s comprehensive tools
The Critical Choice in Cryptocurrency Security
The fundamental decision between hardware and software wallets represents one of the most important security choices cryptocurrency users will make, directly impacting the safety of their digital assets and their overall experience in managing cryptocurrencies. This comprehensive analysis examines the technical architecture, security implications, usability considerations, and cost-benefit analysis of both wallet types to provide users with the information necessary to make informed decisions about their cryptocurrency storage solutions.
The distinction between hardware and software wallets goes beyond simple categorization, encompassing fundamental differences in how private keys are generated, stored, and accessed during transaction signing processes. Hardware wallets employ dedicated security chips and air-gapped architecture to provide maximum protection against various attack vectors, while software wallets offer enhanced convenience and integration capabilities at the cost of increased exposure to system-level vulnerabilities and online threats.
Understanding Hardware Wallet Architecture
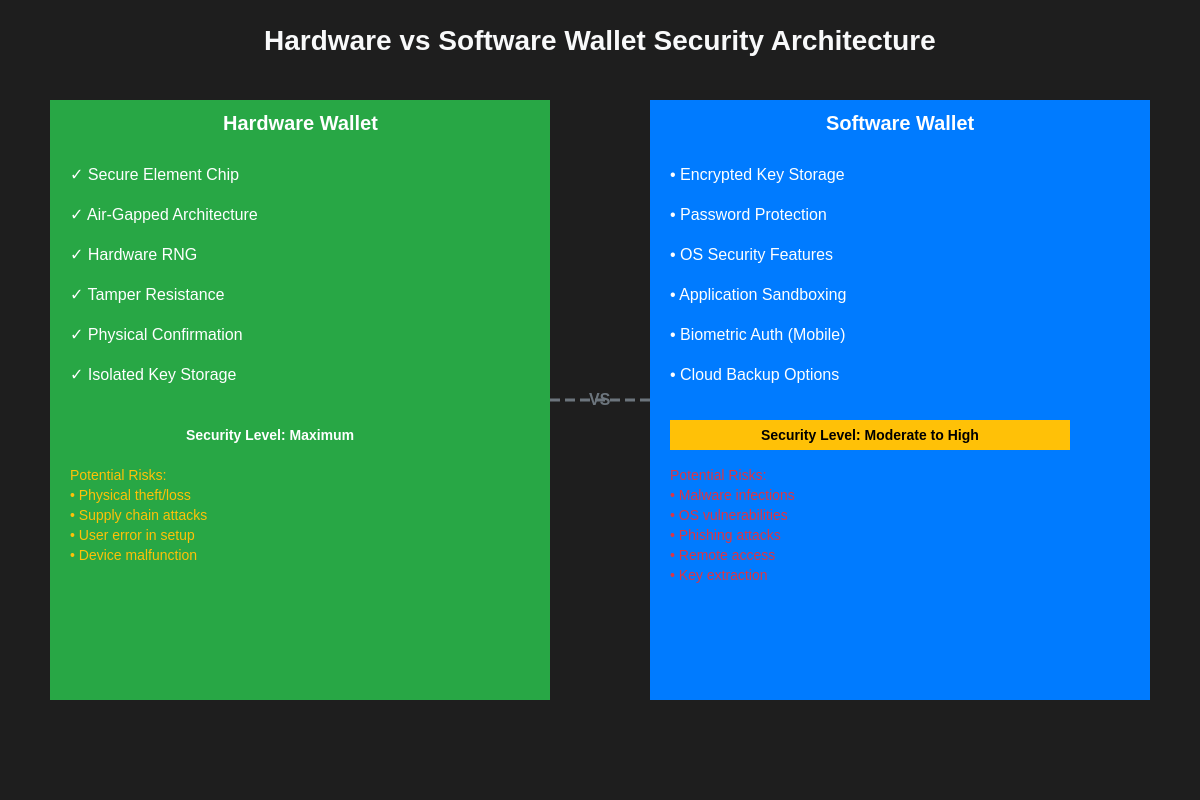
Hardware wallets represent the gold standard in cryptocurrency security through their implementation of dedicated security hardware specifically designed to protect private keys from extraction and unauthorized use. These devices typically employ secure elements or specialized microcontrollers that provide hardware-level isolation between the cryptocurrency management functions and any potentially compromised systems they connect to during transaction operations.
The secure element technology used in premium hardware wallets implements cryptographic operations at the hardware level, ensuring that private keys never leave the device in unencrypted form and that all transaction signing occurs within the protected environment of the security chip. This architecture provides protection against a wide range of attack vectors including malware infections on connected computers, man-in-the-middle attacks, and various forms of side-channel analysis that might compromise software-based security implementations.
Hardware wallets implement deterministic key generation using standardized protocols such as BIP32, BIP39, and BIP44, ensuring that users can recover their entire wallet from a single mnemonic seed phrase while maintaining the security benefits of hierarchical deterministic key derivation. The seed phrase generation process occurs entirely within the secure environment of the device, utilizing true random number generators to ensure cryptographically secure entropy for key material generation.
Track crypto prices and security trends with TradingView’s professional charting tools
The transaction signing process in hardware wallets follows a strict isolation model where transaction details are displayed on the device’s screen for user verification before signing occurs within the secure element. This approach prevents malware on connected computers from modifying transaction details or tricking users into signing unintended transactions, as the final authorization must occur through physical interaction with the hardware device itself.
Software Wallet Security Models
Software wallets encompass a diverse range of applications including desktop clients, mobile applications, and web-based interfaces, each implementing different security models and offering varying levels of protection for private key material. The security of software wallets depends heavily on the security of the underlying operating system and the implementation quality of the wallet software itself, creating potential vulnerabilities that are generally not present in hardware wallet implementations.
Desktop software wallets typically store private keys in encrypted files on the user’s computer, protected by passwords or other authentication mechanisms, but remain vulnerable to various forms of malware that can potentially access key material through memory analysis, keylogging, or other system-level attack techniques. Advanced software wallets implement additional security measures such as encrypted storage, secure memory handling, and integration with system-level security features, but these protections are fundamentally limited by the security capabilities of the host operating system.
Mobile software wallets benefit from the enhanced security features of modern mobile operating systems including application sandboxing, secure storage APIs, and biometric authentication systems, but still face potential vulnerabilities from malicious applications, operating system exploits, and device compromise scenarios. The convenience of mobile wallets for daily transactions must be balanced against their increased exposure to various attack vectors compared to air-gapped hardware solutions.
Web-based wallets and browser extensions introduce additional security considerations related to web security, including potential vulnerabilities from malicious websites, browser exploits, and man-in-the-middle attacks that could compromise private key material or transaction integrity. While some web wallets implement client-side encryption and never transmit private keys to servers, users must trust both the wallet provider and the integrity of the web delivery mechanism for the wallet software.
Security Threat Analysis and Attack Vectors
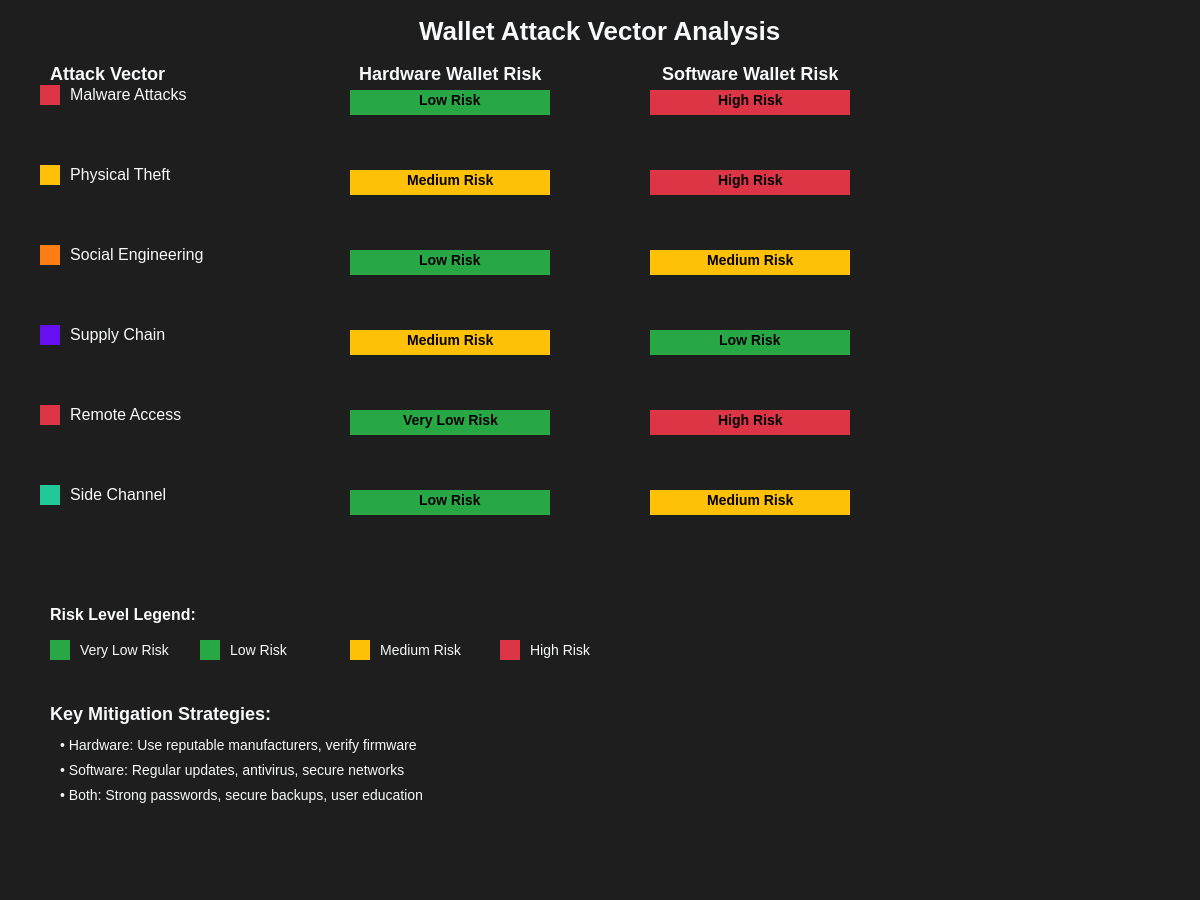
The threat landscape for cryptocurrency wallets encompasses a wide range of potential attack vectors that vary significantly in their applicability to hardware versus software wallet implementations. Understanding these threats and their mitigation strategies is crucial for users making informed decisions about wallet security and for developers implementing robust security measures in wallet software.
Malware represents one of the most significant threats to software wallets, with various forms of malicious software capable of stealing private keys, modifying transactions, or performing unauthorized operations on behalf of attackers. Hardware wallets provide inherent protection against malware-based attacks through their isolation from potentially compromised systems, though users must still verify transaction details on the device to prevent social engineering attacks that manipulate displayed information.
Physical security threats affect both hardware and software wallets but in different ways, with hardware wallets requiring protection against physical theft and tampering while software wallets must be protected against unauthorized access to the devices on which they are installed. Advanced hardware wallets implement tamper-resistant features and secure boot processes to detect and respond to physical tampering attempts, while software wallets rely on device-level security features such as encryption and authentication to protect against unauthorized access.
Social engineering attacks target the human element in cryptocurrency security, attempting to trick users into revealing sensitive information or performing actions that compromise their wallet security. Hardware wallets can provide some protection against social engineering by requiring physical confirmation of transactions, but users must still maintain vigilance against phishing attempts and other forms of deception that might lead to compromise of their recovery phrases or authentication credentials.
Analyze wallet security metrics using TradingView’s advanced analytical tools
Supply chain attacks represent an emerging threat vector that can affect both hardware and software wallets through compromise of development tools, distribution channels, or manufacturing processes. Hardware wallets may be vulnerable to supply chain attacks that introduce malicious firmware or hardware modifications, while software wallets face potential compromise through malicious dependencies, compromised development environments, or malicious updates distributed through official channels.
Usability and User Experience Considerations
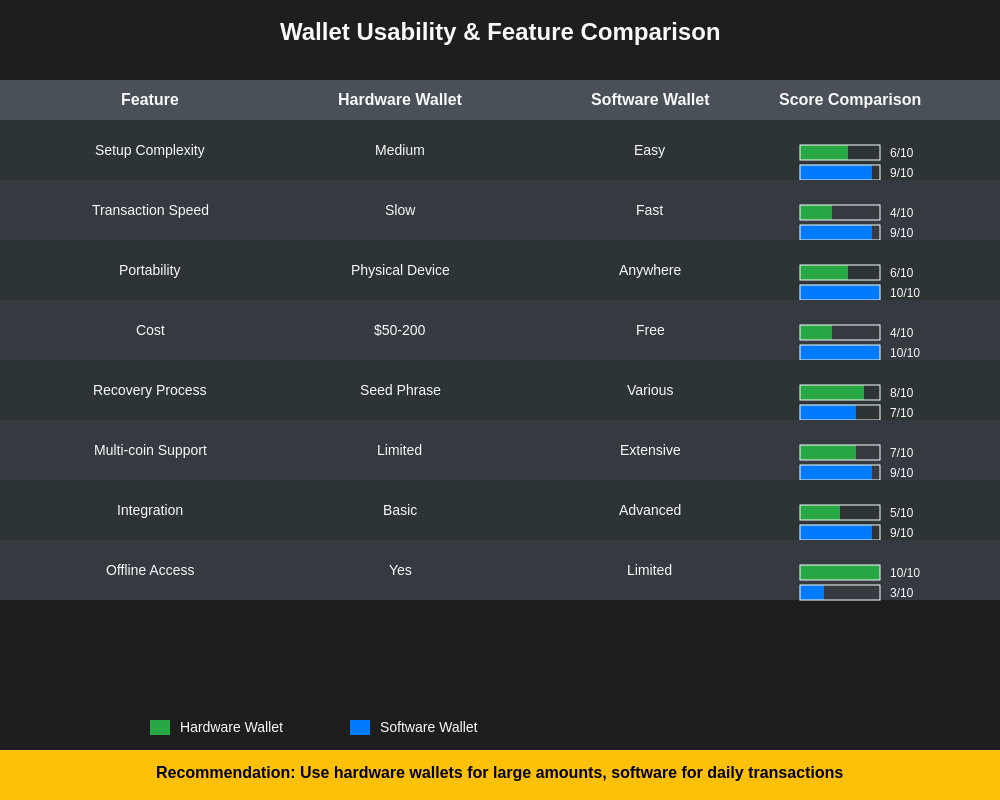
The user experience differences between hardware and software wallets significantly impact their suitability for different use cases and user profiles, with each approach offering distinct advantages and limitations that must be considered in the context of intended usage patterns and user technical expertise levels.
Hardware wallets generally require more complex setup procedures and operational workflows compared to software wallets, as users must manage physical devices, understand backup and recovery procedures, and navigate the interface limitations inherent in small-screen devices with limited input capabilities. However, this complexity often correlates with enhanced security, as the additional steps and verification requirements help prevent user errors and provide multiple opportunities to detect and prevent fraudulent transactions.
Software wallets typically offer more streamlined user experiences with rich interfaces, integrated features such as portfolio tracking and exchange integration, and seamless transaction processes that require minimal user intervention. This enhanced usability comes at the cost of increased security risks, as the convenience features often require increased connectivity and trust in third-party services that may introduce additional attack vectors or privacy compromises.
The backup and recovery processes for hardware and software wallets differ significantly in their implementation and security implications, with hardware wallets typically requiring users to securely store physical recovery phrases while software wallets may offer various backup options including cloud storage integration that trades convenience for potential security compromises. Users must understand the security implications of different backup strategies and implement appropriate protection measures for their recovery materials.
Transaction confirmation workflows vary substantially between hardware and software wallets, with hardware wallets requiring physical interaction and verification on the device screen while software wallets may offer various confirmation mechanisms ranging from simple password entry to biometric authentication. The optimal balance between security and usability depends on the user’s risk tolerance, transaction frequency, and technical expertise level.
Cost-Benefit Analysis and Economic Considerations
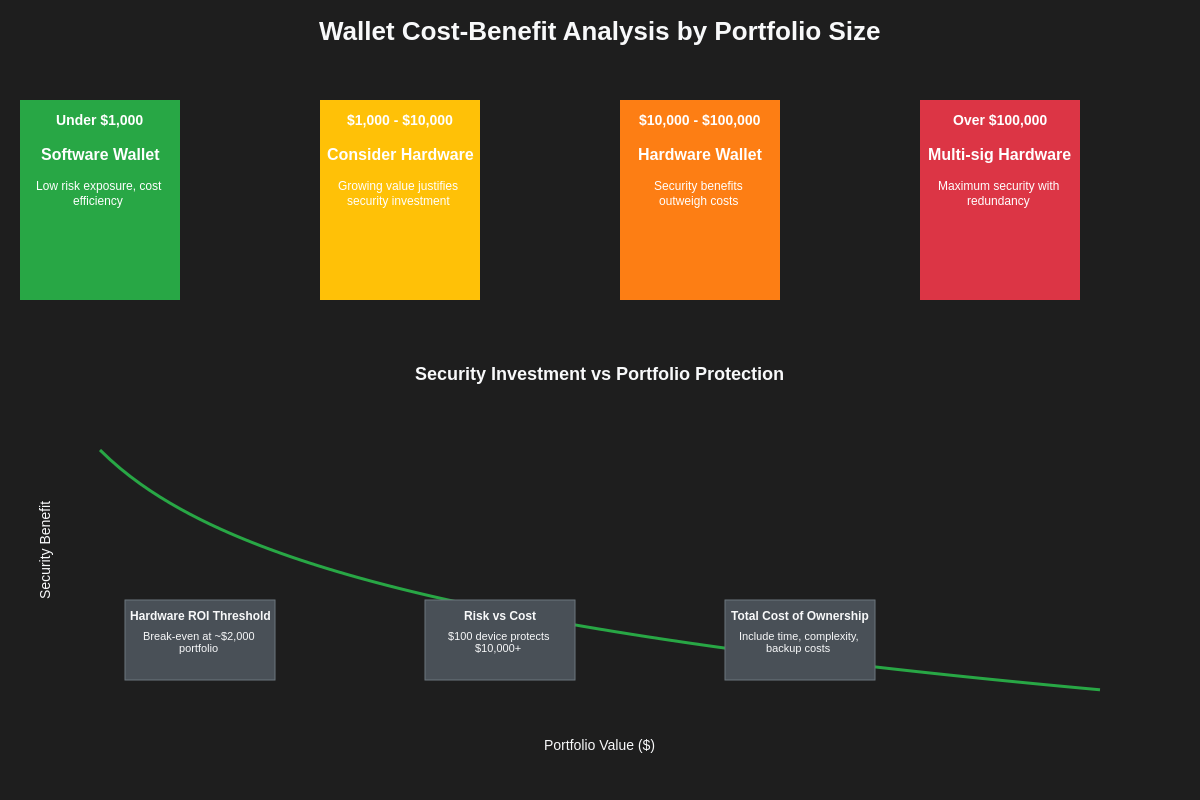
The economic factors influencing the choice between hardware and software wallets extend beyond simple purchase price considerations to encompass total cost of ownership, potential loss scenarios, and the value proposition of enhanced security relative to the assets being protected.
Hardware wallets require upfront investment in physical devices that typically cost between fifty and several hundred dollars depending on features and security capabilities, but this initial cost must be evaluated against the potential value of protected assets and the probability of loss scenarios that could be prevented through enhanced security. For users with significant cryptocurrency holdings, the cost of hardware wallets represents a small fraction of portfolio value and provides substantial risk reduction benefits.
Software wallets generally have lower direct costs, with many high-quality options available at no charge, but users must consider indirect costs including potential losses from security compromises, time and effort required for security maintenance, and opportunity costs associated with enhanced security procedures. The total cost of ownership for software wallets may include expenses for additional security measures such as dedicated devices, enhanced authentication systems, or professional security services.
Insurance and loss recovery considerations differ between hardware and software wallets, with some insurance providers offering different coverage terms or premiums based on the security measures implemented by policyholders. Hardware wallets may qualify for enhanced insurance coverage or reduced premiums due to their superior security characteristics, though users must verify specific policy terms and ensure proper implementation of security best practices to maintain coverage eligibility.
The scalability of security solutions must be considered for users managing multiple cryptocurrency portfolios or providing custody services for others, as hardware wallets may require multiple devices or complex key management procedures while software wallets might offer more flexible multi-account and multi-signature capabilities that scale more efficiently with increasing complexity requirements.
Multi-Signature and Advanced Security Features
Advanced security features available in both hardware and software wallets provide enhanced protection through implementation of multi-signature requirements, time-locked transactions, and other sophisticated security mechanisms that can address specific risk scenarios and provide additional layers of protection against various attack vectors.
Multi-signature functionality allows multiple parties or devices to control access to cryptocurrency funds through requirements that multiple private keys must authorize transactions before they can be executed. Hardware wallets can participate in multi-signature schemes while maintaining their security advantages, though users must carefully coordinate key management and backup procedures across multiple devices to ensure continued access to funds while maintaining security benefits.
Time-locked transactions and other advanced scripting capabilities provide additional security options that can prevent immediate access to funds during specified time periods or under certain conditions, helping protect against impulsive decisions, social engineering attacks, or compromise scenarios where attackers gain temporary access to wallet systems. The implementation of these features varies between hardware and software wallets, with some platforms offering more sophisticated scripting capabilities than others.
Integration with institutional security practices including compliance monitoring, audit trails, and regulatory reporting requirements may favor certain wallet types depending on specific organizational needs and regulatory obligations. Hardware wallets may provide enhanced audit capabilities through their transaction logging and verification requirements, while software wallets might offer better integration with existing compliance and monitoring systems.
Monitor advanced security patterns with TradingView’s institutional-grade platform
Privacy and Anonymity Implications
The privacy characteristics of hardware and software wallets differ significantly in their data collection practices, communication patterns, and potential for transaction correlation, with important implications for users concerned about financial privacy and protection against various forms of surveillance or analysis.
Hardware wallets generally provide enhanced privacy protection through their limited connectivity and reduced data collection requirements, as they typically do not require user registration, account creation, or ongoing communication with vendor services beyond firmware updates. However, the purchase and shipping of hardware wallets creates potential privacy leaks through financial records and delivery information that could be correlated with subsequent blockchain activity.
Software wallets vary widely in their privacy practices, with some implementations providing strong privacy protection through local operation and minimal data collection while others may collect extensive user data, transaction information, and behavioral analytics that could compromise user privacy. Users must carefully evaluate privacy policies and technical implementations to understand the privacy implications of different software wallet choices.
Blockchain analysis and transaction correlation represent ongoing privacy challenges for all cryptocurrency users regardless of wallet type, as the public nature of most blockchain networks enables sophisticated analysis techniques that can potentially de-anonymize users through transaction pattern analysis, address clustering, and correlation with known entities. Advanced privacy features such as coin mixing, transaction batching, and privacy-focused cryptocurrencies can help mitigate these risks but require careful implementation to be effective.
Network-level privacy considerations include the use of VPNs, Tor networks, and other anonymity tools that can help protect user privacy during wallet operation and transaction broadcasting, though users must understand the limitations and potential vulnerabilities of these privacy enhancement techniques to implement them effectively.
Regulatory Compliance and Legal Considerations
The regulatory landscape for cryptocurrency wallets continues to evolve with varying requirements across different jurisdictions, creating important considerations for users regarding compliance obligations, reporting requirements, and the legal implications of different wallet choices and security practices.
Know Your Customer (KYC) and Anti-Money Laundering (AML) requirements may apply differently to various wallet types and usage patterns, with some jurisdictions requiring enhanced due diligence or reporting for certain transaction types or amounts regardless of the wallet technology used. Users must understand their local regulatory obligations and ensure their wallet choices and usage patterns comply with applicable laws and regulations.
Cross-border transaction reporting and tax compliance obligations create additional considerations for wallet users, as different jurisdictions may have varying requirements for cryptocurrency transaction reporting, capital gains calculations, and record-keeping obligations. Hardware wallets may provide enhanced audit trails and transaction verification capabilities that facilitate compliance with reporting requirements, while software wallets might offer better integration with tax reporting and compliance software.
Asset seizure and recovery procedures differ significantly between hardware and software wallets in various legal contexts, with law enforcement agencies potentially having different capabilities and procedures for accessing funds stored in different wallet types. Users must understand the legal implications of their wallet choices and implement appropriate legal and technical protections consistent with their risk tolerance and legal obligations.
Emerging Technologies and Future Developments
The continuous evolution of wallet technology and security practices creates ongoing opportunities for enhanced security, improved usability, and new features that may influence future wallet selection decisions and security strategies for cryptocurrency users.
Quantum-resistant cryptography represents an emerging consideration for long-term cryptocurrency security, as advances in quantum computing may eventually threaten current cryptographic algorithms used in both hardware and software wallets. Wallet developers are beginning to implement quantum-resistant algorithms and upgrade paths to ensure continued security as quantum computing capabilities advance.
Biometric authentication and advanced user verification technologies are being integrated into both hardware and software wallets to provide enhanced security while maintaining usability, though users must understand the privacy and security implications of biometric data storage and authentication mechanisms. The implementation of biometric features varies significantly between different wallet types and may introduce new attack vectors that must be carefully evaluated.
Integration with decentralized identity systems and self-sovereign identity protocols may provide new opportunities for enhanced privacy and security in wallet implementations, allowing users to maintain control over their identity information while benefiting from enhanced authentication and verification capabilities that could improve security and usability simultaneously.
Artificial intelligence and machine learning technologies are being incorporated into wallet security systems to provide enhanced threat detection, transaction analysis, and security monitoring capabilities, though users must understand the privacy implications and potential limitations of AI-based security features to make informed decisions about their implementation and use.
Best Practices and Implementation Guidelines
Successful implementation of either hardware or software wallet solutions requires adherence to established security best practices and careful attention to operational security procedures that can significantly impact the overall security and usability of cryptocurrency storage and management systems.
Backup and recovery procedures represent critical components of wallet security that must be implemented correctly regardless of wallet type, with users required to securely store recovery materials while ensuring they remain accessible during emergency recovery scenarios. Hardware wallets typically use standardized seed phrase systems that require physical storage of recovery words, while software wallets may offer various backup options that users must evaluate for their security and reliability characteristics.
Regular security updates and maintenance procedures are essential for maintaining wallet security over time, with hardware wallets requiring firmware updates and software wallets requiring application updates and security patches. Users must establish procedures for monitoring and applying security updates while verifying the authenticity and integrity of update packages to prevent compromise through malicious updates.
Operational security practices including secure communication channels, verified software downloads, and protection against social engineering attacks apply to both hardware and software wallet users and require ongoing vigilance and education to implement effectively. Users must understand common attack patterns and develop defensive strategies appropriate to their risk profile and technical capabilities.
Testing and verification procedures should be implemented before committing significant funds to any wallet solution, including verification of backup and recovery processes, transaction signing procedures, and security feature functionality. Users should start with small amounts and gradually increase their holdings as they gain confidence in their security procedures and wallet operation.
Access comprehensive crypto security resources through TradingView’s educational platform
Conclusion and Recommendations
The choice between hardware and software wallets ultimately depends on individual user requirements, risk tolerance, technical expertise, and intended usage patterns, with both approaches offering distinct advantages and limitations that must be carefully evaluated in the context of specific user needs and security objectives.
Hardware wallets provide superior security through their dedicated security hardware and air-gapped architecture, making them the preferred choice for users with significant cryptocurrency holdings, long-term storage requirements, or high security needs who can accept the additional complexity and cost associated with hardware wallet operation. The investment in hardware wallet technology is generally justified for users whose cryptocurrency holdings exceed several thousand dollars or who require the highest levels of security available.
Software wallets offer enhanced convenience and integration capabilities that make them suitable for users requiring frequent transaction capabilities, advanced features, or integration with other cryptocurrency services, though they require careful selection and implementation to minimize security risks. Advanced users may benefit from software wallets that offer sophisticated features while implementing additional security measures to mitigate the inherent risks of software-based key storage.
Hybrid approaches that combine hardware and software wallets can provide optimal security and usability for many users, using hardware wallets for long-term storage and high-value transactions while maintaining software wallets for daily transactions and convenience. This approach requires careful coordination between wallet systems and clear procedures for fund movement between different security tiers.
The rapidly evolving cryptocurrency ecosystem will continue to drive innovation in wallet technology, with new security features, usability improvements, and integration capabilities that may influence future wallet selection decisions. Users should stay informed about emerging technologies and security best practices while maintaining flexibility in their wallet strategies to adapt to changing requirements and threat landscapes.
Disclaimer: This article is for educational purposes only and does not constitute financial advice. Cryptocurrency investments carry significant risk, and users should conduct thorough research and consider consulting with financial advisors before making investment decisions. The security of cryptocurrency assets depends on proper implementation of security practices and careful selection of appropriate storage solutions based on individual risk tolerance and requirements.