The Ethereum Scaling Challenge
Ethereum has established itself as the backbone of decentralized finance and the broader Web3 ecosystem, hosting thousands of decentralized applications and facilitating billions of dollars in transactions. However, the network’s success has revealed fundamental scalability limitations that threaten its continued growth and adoption. With transaction fees sometimes reaching hundreds of dollars during peak congestion periods and throughput limited to approximately 15 transactions per second, Ethereum’s base layer struggles to meet the demands of a global financial system that requires fast, affordable, and reliable transaction processing.
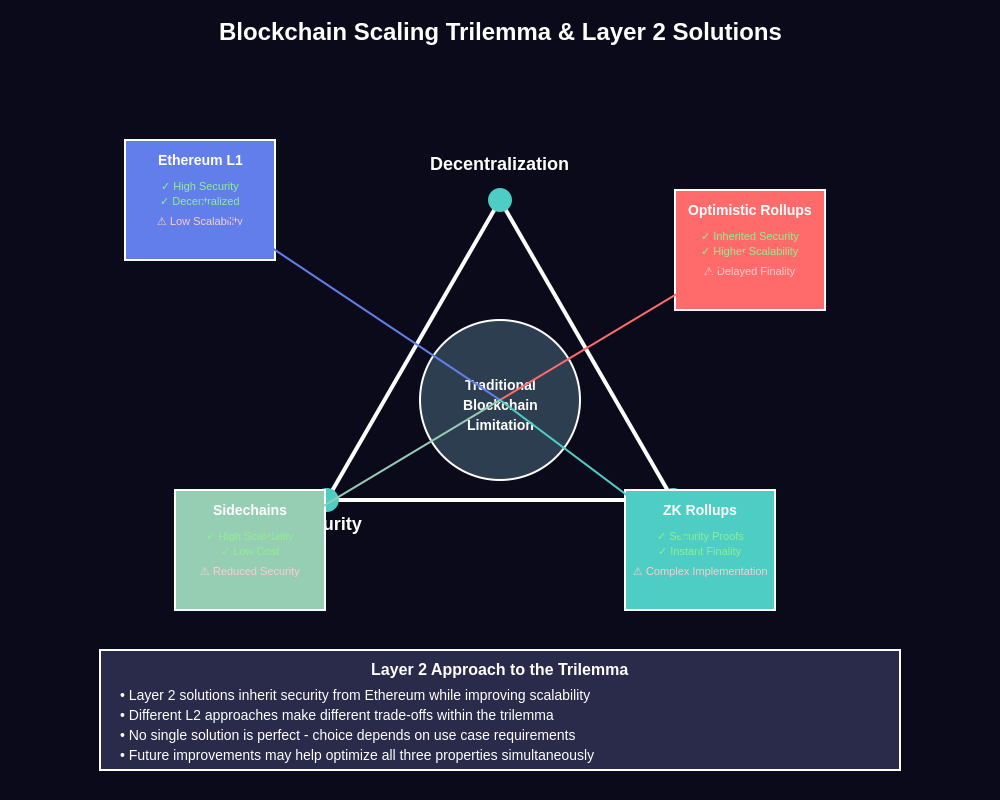
The root of Ethereum’s scalability challenge lies in its design philosophy of prioritizing decentralization and security over raw performance. Every transaction on the Ethereum mainnet must be processed by every node in the network, creating a bottleneck that limits overall throughput. While this approach ensures maximum security and decentralization, it creates significant barriers to mass adoption as users face prohibitively high fees and slow confirmation times during periods of high network activity.
Layer 2 solutions have emerged as the most promising approach to addressing these limitations without compromising Ethereum’s core security guarantees. These scaling solutions operate on top of the Ethereum mainnet, processing transactions off-chain while leveraging the underlying blockchain for final settlement and dispute resolution. By moving the bulk of transaction processing away from the congested mainnet, Layer 2 solutions can dramatically increase throughput while reducing costs, making Ethereum accessible to a broader range of users and use cases.
Understanding Layer 2 Architecture
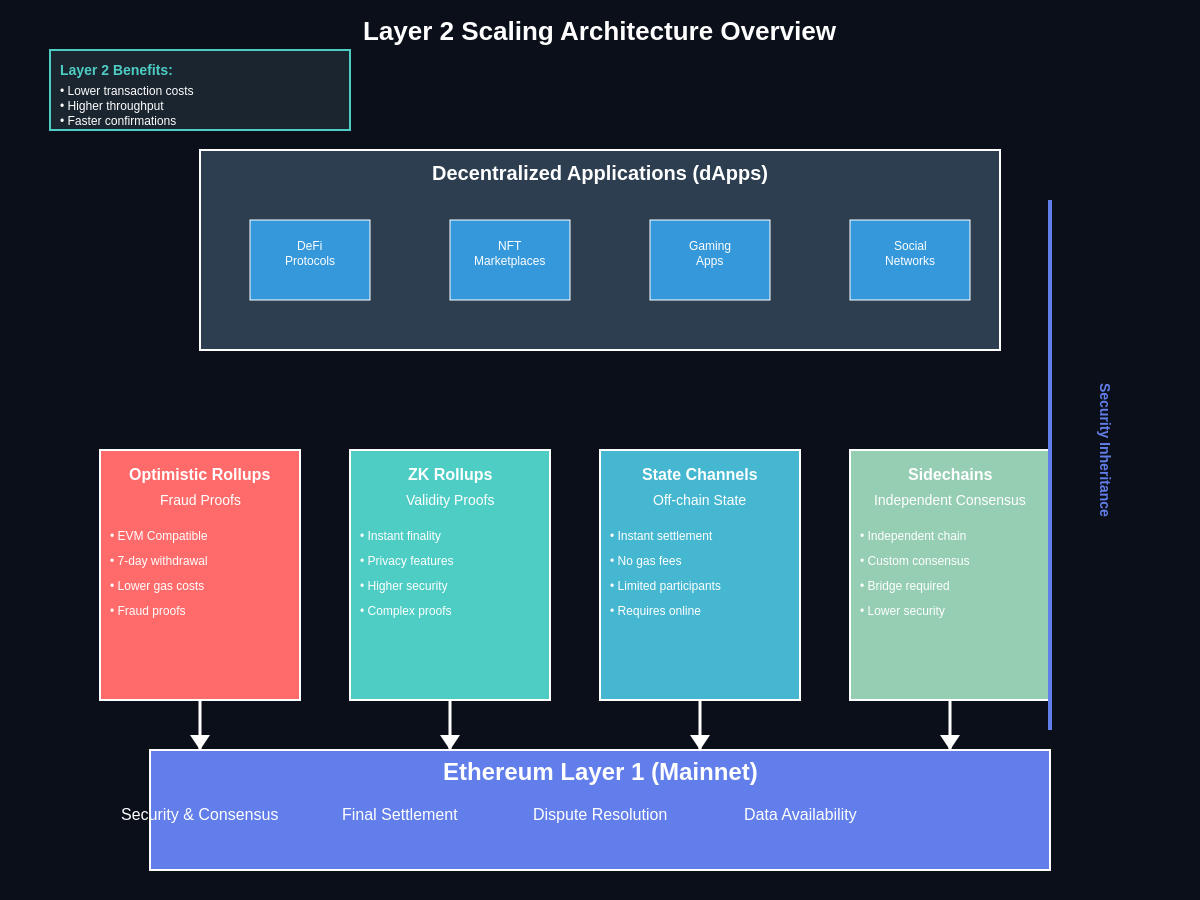
Layer 2 solutions function as secondary frameworks built on top of Ethereum’s base layer, creating a hierarchical structure where different layers serve distinct purposes. The base layer, or Layer 1, maintains the core security and consensus mechanisms that make Ethereum trustless and decentralized. Layer 2 solutions inherit this security while providing enhanced scalability and reduced costs through various technical approaches that optimize transaction processing and data availability.
The fundamental principle underlying all Layer 2 solutions is the concept of moving computation off-chain while maintaining the ability to settle disputes and finalize transactions on the mainnet. This approach allows for significant performance improvements because transactions can be processed much faster when they don’t require immediate consensus from the entire Ethereum network. Instead, Layer 2 solutions batch multiple transactions together and submit periodic checkpoints to the mainnet, effectively amortizing the cost and time of mainnet interaction across many transactions.
Security in Layer 2 systems is maintained through various mechanisms that ensure users can always recover their funds and dispute invalid state transitions. Optimistic rollups, for example, assume transactions are valid by default but provide a challenge period during which anyone can submit fraud proofs to dispute incorrect state transitions. Zero-knowledge rollups take a different approach, using cryptographic proofs to demonstrate the validity of state transitions without revealing the underlying transaction data.
The relationship between Layer 1 and Layer 2 creates a symbiotic ecosystem where the base layer provides security and final settlement while Layer 2 solutions handle the heavy lifting of transaction processing. This division of labor allows Ethereum to scale effectively while maintaining its core properties of decentralization and security. Users can benefit from fast, cheap transactions on Layer 2 while still having the assurance that their assets are ultimately secured by Ethereum’s robust consensus mechanism.
Rollup Technology Deep Dive
Rollups represent the most mature and widely adopted category of Layer 2 solutions, offering a compelling combination of scalability, security, and compatibility with existing Ethereum infrastructure. The term “rollup” derives from the process of rolling up or bundling multiple transactions into a single batch that is then submitted to the Ethereum mainnet. This batching approach dramatically reduces the per-transaction cost of interacting with the mainnet while maintaining strong security guarantees through various verification mechanisms.
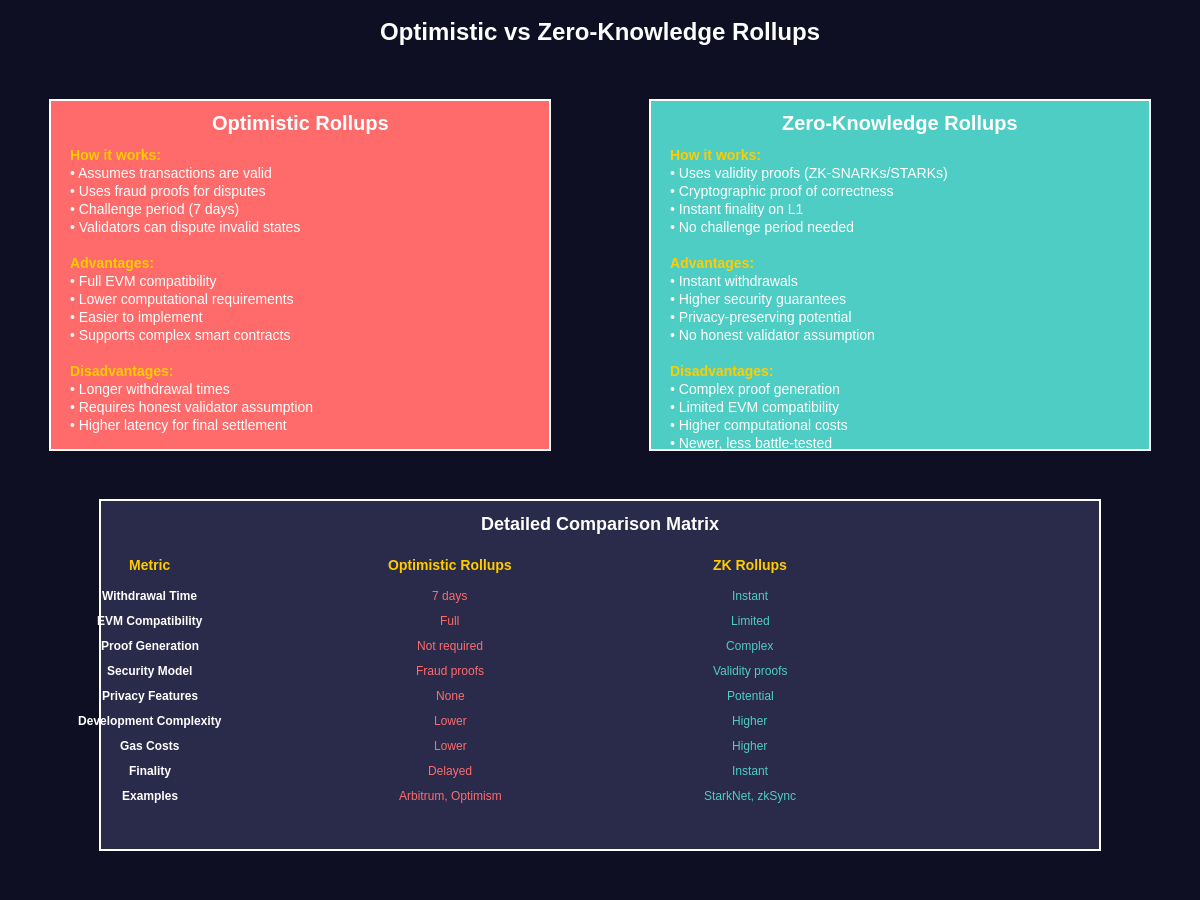
The two primary types of rollups, Optimistic and Zero-Knowledge, take fundamentally different approaches to ensuring transaction validity. Optimistic rollups operate under the assumption that all submitted transactions are valid unless proven otherwise through a challenge mechanism. This approach allows for faster processing and broader compatibility with existing Ethereum smart contracts, as the rollup can execute the same code that would run on the mainnet. When disputes arise, validators can submit fraud proofs that demonstrate the invalidity of a particular state transition, triggering a resolution process on the mainnet.
Zero-Knowledge rollups, in contrast, use advanced cryptographic techniques to generate mathematical proofs that demonstrate the validity of all transactions in a batch without revealing the specific details of those transactions. These validity proofs are submitted alongside the transaction batch to the mainnet, where they can be verified much more quickly than re-executing all the transactions. This approach offers stronger security guarantees and faster finality than Optimistic rollups but requires more complex infrastructure and may have limitations in terms of smart contract compatibility.
Both types of rollups inherit Ethereum’s security properties while offering significant improvements in throughput and cost efficiency. Transactions processed on rollups can achieve costs that are orders of magnitude lower than equivalent mainnet transactions, making previously economically unfeasible use cases viable. The security model ensures that even if rollup operators act maliciously or go offline, users can still recover their funds and continue transacting, albeit with some additional complexity and delay.
Data availability represents a critical component of rollup security and efficiency. For rollups to maintain their security guarantees, the data necessary to reconstruct the current state must be available to all network participants. Most rollups currently publish this data to Ethereum as calldata, which is expensive but provides strong availability guarantees. Future improvements, including Ethereum’s planned data sharding upgrade, promise to reduce these costs significantly while maintaining security properties.
Optimistic Rollups: Scaling Through Trust
Optimistic rollups have gained significant traction in the Ethereum ecosystem due to their relative simplicity and excellent compatibility with existing smart contracts and development tools. Networks like Arbitrum and Optimism have successfully deployed Optimistic rollup solutions that support thousands of applications and process millions of transactions while maintaining strong security guarantees through their connection to Ethereum mainnet.
The “optimistic” nature of these rollups stems from their assumption that all submitted state transitions are valid unless challenged. This approach allows for immediate transaction processing without waiting for complex cryptographic proofs to be generated. Validators monitor the rollup for invalid state transitions and can submit fraud proofs during a challenge period, typically lasting one to seven days. This challenge period represents the primary trade-off of Optimistic rollups, as withdrawals to the mainnet must wait for this period to expire to ensure no valid challenges will be raised.
The fraud proof mechanism forms the backbone of Optimistic rollup security. When a validator believes that an invalid state transition has been submitted, they can initiate a challenge by posting a bond and providing evidence of the fraud. The dispute resolution process then occurs on the Ethereum mainnet, where the contested computation is re-executed to determine the correct outcome. If fraud is proven, the dishonest party loses their bond, while successful challengers are rewarded for their vigilance in maintaining network integrity.
Smart contract compatibility represents one of the strongest advantages of Optimistic rollups. Developers can deploy existing Ethereum contracts with minimal modifications, leveraging familiar development tools and frameworks. This compatibility has enabled rapid ecosystem growth, with many major DeFi protocols launching on Optimistic rollups to offer their users lower fees and faster transactions. The Ethereum Virtual Machine compatibility ensures that complex smart contract interactions work as expected, maintaining the rich functionality that makes Ethereum attractive to developers.
Recent developments in Optimistic rollup technology focus on improving the dispute resolution process and reducing withdrawal times. Interactive fraud proofs allow for more efficient challenge resolution by requiring disputants to narrow down their disagreement to a specific computational step. Multi-round fraud proofs further optimize this process by enabling binary search-like approaches to identify the exact point of disagreement. These improvements reduce the computational burden on the mainnet while maintaining robust security guarantees.
Zero-Knowledge Rollups: Cryptographic Scaling
Zero-Knowledge rollups represent the cutting edge of Layer 2 scaling technology, utilizing advanced cryptographic techniques to provide both scalability and enhanced privacy properties. Projects like Polygon’s zkEVM and StarkNet have demonstrated the potential of ZK rollups to process thousands of transactions per second while generating mathematical proofs that validate the correctness of all state transitions without revealing sensitive transaction details.
The core innovation of ZK rollups lies in their use of zero-knowledge proofs, cryptographic constructs that allow one party to prove knowledge of certain information without revealing the information itself. In the context of rollups, this means that a batch of transactions can be proven to be valid without requiring validators to re-execute every transaction. The rollup operator generates a succinct proof, often just a few hundred bytes, that demonstrates the validity of potentially thousands of transactions, dramatically reducing the verification burden on the Ethereum mainnet.
Two primary types of zero-knowledge proofs are used in current rollup implementations: zk-SNARKs and zk-STARKs. zk-SNARKs offer excellent proof sizes and verification times but require a trusted setup ceremony and may be vulnerable to quantum computing advances. zk-STARKs provide quantum resistance and eliminate the need for trusted setup but generate larger proofs that require more computational resources to verify. The choice between these approaches involves trade-offs between security assumptions, performance characteristics, and implementation complexity.
The privacy benefits of ZK rollups extend beyond simple transaction obfuscation. By proving computational correctness without revealing inputs, ZK rollups enable new categories of applications that require privacy-preserving computation. Financial applications can process sensitive data without exposing individual positions or trading strategies, while identity systems can verify credentials without revealing personal information. This privacy enhancement opens up use cases that would be impossible or inadvisable on transparent blockchains.
However, ZK rollups face significant challenges in achieving full Ethereum Virtual Machine compatibility. The complex instruction set and state model of the EVM make it difficult to generate efficient zero-knowledge proofs for arbitrary smart contract execution. Current solutions involve various trade-offs, from supporting only specific operations to developing new virtual machines optimized for zero-knowledge proof generation. The development of zkEVMs represents a major breakthrough in addressing these compatibility challenges while maintaining the benefits of zero-knowledge verification.
State Channels: Instant Finality for Frequent Interactions
State channels provide a fundamentally different approach to Layer 2 scaling, focusing on enabling instant, feeless transactions between specific parties rather than creating general-purpose scaling infrastructure. This approach excels in scenarios involving frequent interactions between a known set of participants, such as micropayments, gaming, or real-time applications that require immediate transaction finality without the delays inherent in blockchain confirmation processes.
The basic concept of state channels involves participants locking funds in a smart contract on the Ethereum mainnet and then conducting an unlimited number of off-chain transactions by exchanging signed state updates. These state updates represent the current distribution of the locked funds among participants and can be executed instantly without waiting for blockchain confirmation. The latest state update can be submitted to the mainnet at any time to close the channel and distribute funds according to the final agreed-upon state.
Security in state channels relies on the ability of participants to challenge invalid state updates during a dispute resolution period. If one party attempts to close the channel with an outdated or invalid state, other participants can submit a more recent state update to the mainnet, proving that the attempted closure was fraudulent. This mechanism ensures that honest participants can always recover their rightful funds, even if other channel participants act maliciously or attempt to cheat.
The Lightning Network for Bitcoin provides the most well-known example of state channel technology, and similar concepts have been adapted for Ethereum through projects like Connext and Raiden. These implementations enable instant payments and complex state transitions while maintaining the security guarantees of the underlying blockchain. State channels can support not just simple payments but also complex smart contract interactions, games, and other stateful applications that benefit from instant finality.
However, state channels face limitations that restrict their applicability to specific use cases. The requirement for participants to be online to receive payments limits their utility for asynchronous interactions. The capital efficiency challenges of locking funds in channels can make them unsuitable for applications with unpredictable transaction patterns. Additionally, the complexity of managing channel states and routing payments through channel networks presents usability challenges that must be addressed through improved tooling and user interfaces.
Polygon and the Multi-Chain Approach
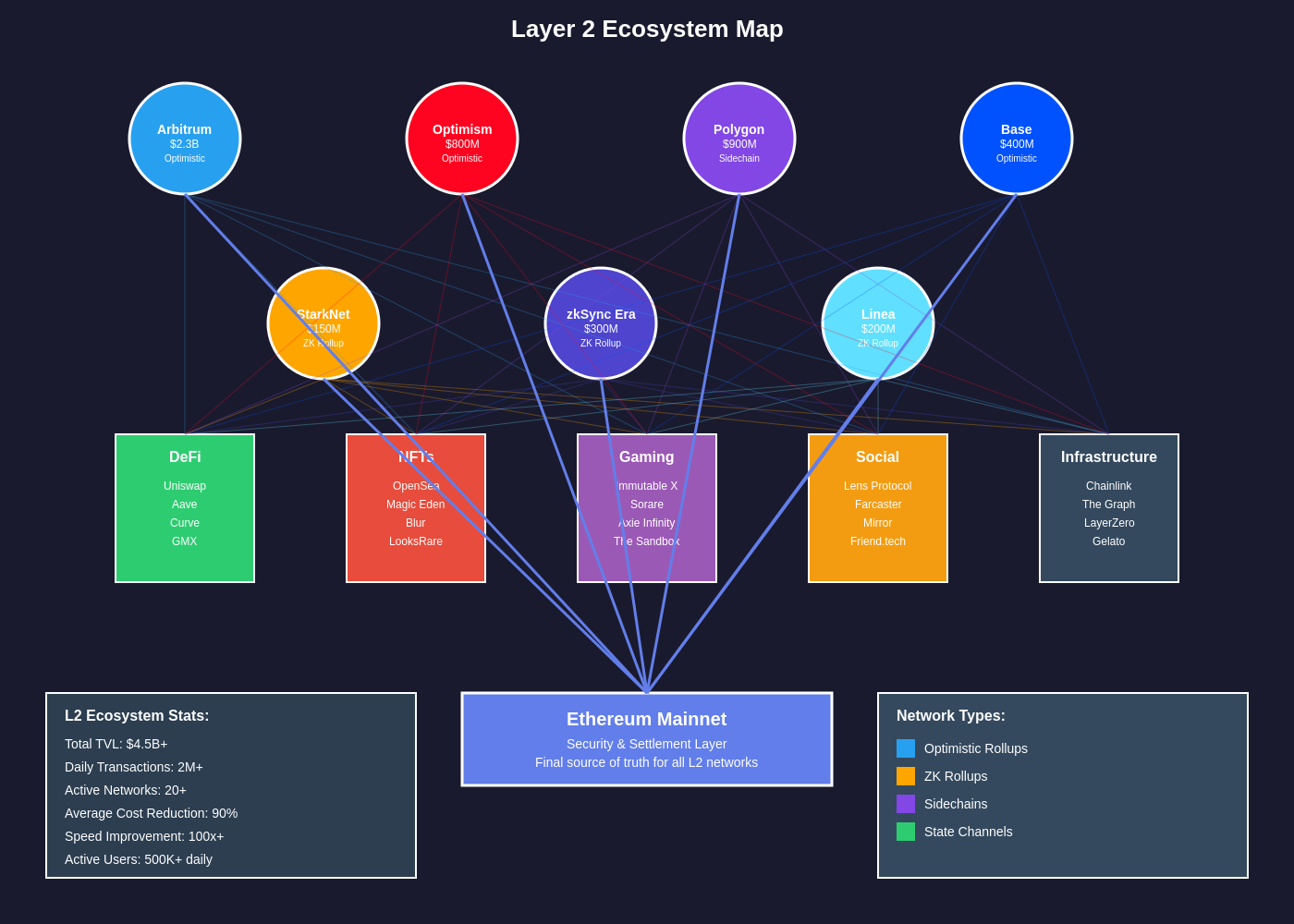
Polygon has established itself as one of the most successful Layer 2 ecosystems by taking a multi-faceted approach that combines various scaling technologies under a unified framework. Rather than committing to a single scaling solution, Polygon provides a platform that supports multiple approaches, including sidechains, Plasma chains, Optimistic rollups, and Zero-Knowledge rollups, allowing developers to choose the solution that best fits their specific requirements.
The Polygon PoS chain represents the ecosystem’s most mature offering, functioning as an Ethereum-compatible sidechain that provides fast and cheap transactions while maintaining periodic checkpointing to the Ethereum mainnet. This approach sacrifices some decentralization in favor of performance, using a smaller set of validators to achieve faster block times and lower transaction costs. The regular checkpointing to Ethereum provides an additional layer of security and enables asset bridging between the networks.
Polygon’s expanding ecosystem includes ambitious projects like Polygon Hermez, a zk-rollup focused on payments and simple smart contract interactions, and Polygon Miden, which aims to provide a more general-purpose zero-knowledge virtual machine. The diversity of approaches allows Polygon to serve different segments of the market while maintaining interoperability and shared infrastructure across its various solutions.
The network effects and ecosystem development surrounding Polygon demonstrate the importance of developer adoption and user experience in Layer 2 success. By providing familiar development tools, comprehensive documentation, and strong incentive programs, Polygon has attracted hundreds of projects and millions of users to its platform. The ecosystem includes major DeFi protocols, NFT marketplaces, gaming applications, and enterprise solutions, showcasing the versatility of Layer 2 infrastructure.
Polygon’s approach to interoperability extends beyond simple asset bridging to include more sophisticated cross-chain communication protocols. The planned Polygon 2.0 upgrade promises to unify the various Polygon chains into a seamless multi-chain ecosystem where assets and data can flow freely between different scaling solutions. This vision of a unified, interoperable Layer 2 ecosystem represents a significant evolution from the current fragmented landscape of isolated scaling solutions.
Arbitrum: Optimistic Rollup Leadership
Arbitrum has emerged as the leading Optimistic rollup solution in terms of total value locked and ecosystem adoption, demonstrating the viability of fraud proof-based scaling for general-purpose smart contract execution. The network’s success stems from its excellent Ethereum compatibility, robust security model, and developer-friendly infrastructure that makes deploying and interacting with smart contracts nearly identical to the mainnet experience.
The technical architecture of Arbitrum incorporates several innovations that improve upon basic Optimistic rollup designs. The AnyTrust technology allows for configurable trust assumptions, enabling applications to choose their preferred balance between decentralization and performance. The interactive dispute resolution system reduces the on-chain computational burden of fraud proofs by requiring disputants to narrow down their disagreement through a binary search process, making challenges more efficient and cost-effective.
Arbitrum’s ecosystem growth has been driven by the migration of major DeFi protocols seeking to offer their users lower transaction costs without sacrificing security or functionality. The network hosts native versions of popular applications like Uniswap, Aave, and Curve, as well as innovative new protocols that leverage the improved economics of Layer 2 transactions. The seamless user experience has made Arbitrum attractive to both experienced DeFi users and newcomers who were previously priced out by mainnet fees.
The launch of Arbitrum Nova represents an evolution toward more specialized Layer 2 solutions within the Arbitrum ecosystem. Nova uses AnyTrust technology to achieve even lower costs and higher throughput by relying on a data availability committee rather than posting all transaction data to Ethereum. This approach is particularly well-suited for gaming and social applications that require high transaction volumes but can tolerate slightly weaker security assumptions.
Future developments in the Arbitrum ecosystem focus on further reducing costs and improving user experience through innovations like local fee markets and improved batching algorithms. The planned transition to a more decentralized governance model through the ARB token will give the community greater control over network parameters and upgrade decisions, reflecting the maturation of the platform from a development project to a community-governed public good.
Optimism and Public Goods Funding
Optimism has distinguished itself in the Layer 2 space not only through its technical achievements but also through its innovative approach to funding public goods and incentivizing ecosystem development. The network’s “Optimistic Vision” extends beyond mere scaling to encompass a sustainable model for funding the digital infrastructure and public goods that benefit the entire blockchain ecosystem.
The technical foundation of Optimism closely mirrors other Optimistic rollup implementations but includes several refinements that improve security and user experience. The modular design separates concerns between different system components, making the platform easier to upgrade and customize. The EVM equivalence ensures that existing Ethereum applications can deploy with minimal changes, maintaining compatibility while benefiting from reduced costs and faster transaction processing.
The Optimism Collective represents a novel governance experiment that allocates a significant portion of network value to funding public goods rather than traditional profit maximization. Through mechanisms like retroactive public goods funding and the Citizens’ House governance structure, Optimism creates sustainable incentives for developers to build infrastructure, tools, and applications that benefit the broader ecosystem rather than extracting maximum value for themselves.
Optimism’s unique tokenomics include innovative distribution mechanisms that reward users for positive-sum behaviors like participating in governance, contributing to public goods, or building applications that benefit the ecosystem. This approach contrasts with traditional token distributions that often concentrate value among early investors and team members, instead seeking to align incentives with long-term ecosystem health and sustainability.
The Superchain vision represents Optimism’s ambitious plan to create a network of interoperable L2 chains that share security, governance, and economic models while maintaining their independence and specialization. This approach acknowledges that different applications and use cases may require different trade-offs in terms of performance, security, and functionality, while still benefiting from shared infrastructure and network effects.
Base and Coinbase’s Layer 2 Strategy
Base represents Coinbase’s strategic entry into the Layer 2 ecosystem, leveraging the exchange’s massive user base and regulatory relationships to bridge the gap between traditional finance and decentralized applications. Built on Optimism’s OP Stack, Base inherits proven rollup technology while benefiting from Coinbase’s expertise in user experience, compliance, and institutional relationships.
The technical architecture of Base emphasizes security and regulatory compliance, incorporating features that make it attractive to institutional users and traditional finance applications. The tight integration with Coinbase’s existing infrastructure allows for seamless onboarding of the exchange’s users to DeFi applications, potentially bringing millions of new users into the broader Web3 ecosystem without the complexity typically associated with blockchain interactions.
Base’s approach to ecosystem development focuses on practical applications that demonstrate the value of blockchain technology to mainstream users. Rather than pursuing the most cutting-edge or experimental applications, Base prioritizes usefulness, reliability, and user experience that can appeal to users who may be encountering blockchain technology for the first time through Coinbase’s platform.
The regulatory positioning of Base reflects Coinbase’s broader strategy of working within existing regulatory frameworks while pushing for clearer guidelines and better understanding of blockchain technology among policymakers. This approach may limit some types of experimental applications but provides a more stable foundation for applications requiring regulatory clarity or institutional adoption.
The long-term vision for Base extends beyond simple transaction processing to encompass a broader platform for financial innovation that bridges traditional and decentralized finance. By leveraging Coinbase’s relationships with traditional financial institutions and regulatory bodies, Base aims to create pathways for greater institutional adoption of blockchain technology while maintaining the openness and innovation that characterizes the broader DeFi ecosystem.
StarkNet and Advanced Zero-Knowledge Technology
StarkNet represents one of the most ambitious implementations of zero-knowledge rollup technology, utilizing advanced STARK proofs to create a general-purpose computing platform that can support complex smart contract execution while maintaining strong security and privacy properties. The platform’s unique approach to virtual machine design and proof generation sets it apart from EVM-compatible solutions, offering new possibilities for application development and optimization.
The Cairo programming language and virtual machine form the foundation of StarkNet’s approach to zero-knowledge computation. Unlike systems that attempt to generate ZK proofs for existing instruction sets, Cairo is designed from the ground up to be “STARK-friendly,” enabling efficient proof generation for complex computations. This approach requires developers to learn new paradigms and tools but offers significant advantages in terms of proof generation speed and verification efficiency.
The technical innovations in StarkNet extend to novel approaches to state management, transaction processing, and cross-layer communication. The account abstraction model allows for more flexible authentication mechanisms and transaction patterns, while the native support for privacy-preserving computation enables applications that would be impossible on transparent blockchains. These features position StarkNet as a platform for next-generation applications that require both scalability and privacy.
The StarkNet ecosystem has attracted projects focused on advanced use cases like algorithmic trading, private voting systems, and zero-knowledge machine learning. The platform’s unique capabilities enable applications that require computational privacy or complex mathematical operations that benefit from the verifiable computation guarantees provided by STARK proofs.
Future developments in StarkNet focus on improving compatibility with existing Ethereum tooling while maintaining the platform’s unique advantages. The development of transpilation tools and compatibility layers aims to make it easier for Ethereum developers to build on StarkNet, while ongoing research into proof optimization and hardware acceleration promises to further improve the platform’s performance characteristics.
Economic Models and Fee Structures
The economic models underlying Layer 2 solutions represent a critical factor in their adoption and long-term sustainability, with different approaches offering various trade-offs between cost efficiency, security, and decentralization. Understanding these economic dynamics is essential for users, developers, and investors seeking to navigate the Layer 2 ecosystem and make informed decisions about platform selection and resource allocation.
Transaction fee structures on Layer 2 solutions typically involve multiple components, including the cost of computation on the Layer 2 network itself, the amortized cost of posting data to Ethereum, and potential network-specific fees for additional services or governance participation. The relative importance of these components varies significantly between different Layer 2 approaches, with some networks prioritizing minimal fees while others focus on sustainable revenue models for network operators and validators.
The mechanism for fee price discovery also varies significantly between Layer 2 solutions, with some implementing EIP-1559 style auctions while others use simpler fixed-price models or dynamic pricing based on network utilization. These different approaches can lead to significantly different user experiences during periods of high demand, with some networks maintaining stable fees while others experience price volatility similar to the Ethereum mainnet.
Revenue sharing and value accrual models represent another important dimension of Layer 2 economics, determining how network value is distributed among stakeholders including users, developers, operators, and token holders. Some networks prioritize minimal extraction and public goods funding, while others implement more traditional business models focused on generating returns for network operators and investors.
The long-term sustainability of different economic models depends on their ability to balance competing incentives while maintaining security and decentralization properties. Networks that rely on external subsidies or venture capital funding may face challenges as these sources of support diminish, while networks with sustainable revenue models may be better positioned for long-term success. The ongoing evolution of Layer 2 tokenomics represents an important area of experimentation and innovation within the broader blockchain ecosystem.
Developer Experience and Tooling
The developer experience on Layer 2 solutions plays a crucial role in determining platform adoption and ecosystem growth, with successful networks investing heavily in documentation, tooling, and developer support infrastructure. The quality of development tools and the ease of deployment can significantly impact the willingness of projects to migrate from Ethereum mainnet or choose one Layer 2 solution over another.
EVM compatibility represents the most important factor for many developers, as it allows existing Ethereum projects to deploy with minimal code changes while leveraging familiar development frameworks like Hardhat, Truffle, and Remix. Networks that achieve high levels of EVM compatibility can tap into the existing ecosystem of Ethereum developers and tools, accelerating ecosystem growth and reducing the barriers to entry for new projects.
However, EVM compatibility comes with trade-offs, particularly for networks utilizing zero-knowledge proofs where the complex instruction set of the EVM makes proof generation challenging and expensive. Alternative approaches involve developing new virtual machines optimized for specific Layer 2 technologies, but these require developers to learn new paradigms and tools, potentially slowing adoption in exchange for better performance or functionality.
The availability of infrastructure services like indexing, analytics, oracles, and cross-chain bridges significantly impacts the developer experience on Layer 2 networks. Projects that provide comprehensive infrastructure support or integrate with existing service providers can offer developers a more complete toolkit for building sophisticated applications. The fragmentation of infrastructure across different Layer 2 solutions represents an ongoing challenge that affects both development complexity and user experience.
Debugging and monitoring tools specifically designed for Layer 2 environments are becoming increasingly important as applications grow more complex and handle larger transaction volumes. The unique characteristics of Layer 2 systems, including state synchronization between layers and novel transaction lifecycle patterns, require specialized tools that can help developers understand and optimize their applications’ performance across different network layers.
Interoperability and Cross-Chain Communication
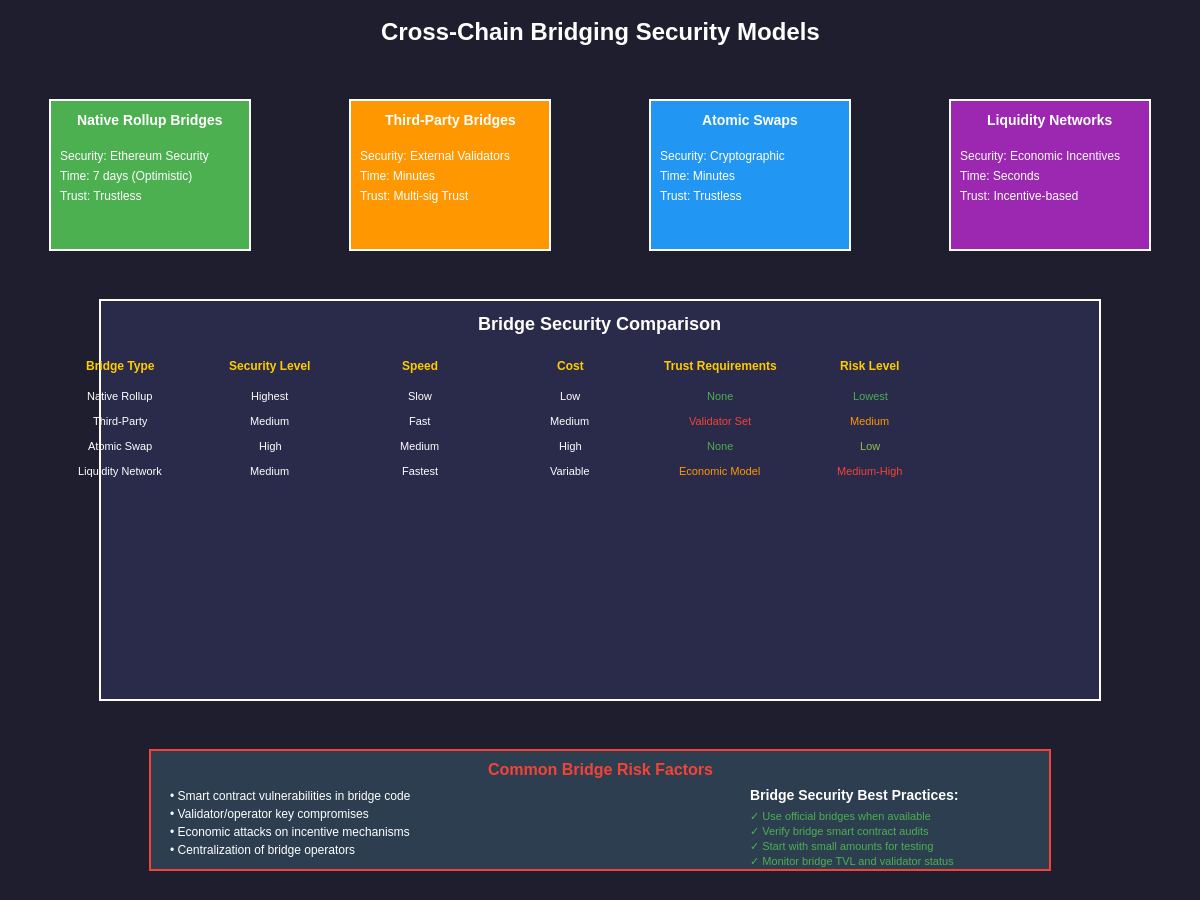
Interoperability between different Layer 2 solutions and the broader multi-chain ecosystem represents one of the most significant challenges and opportunities in the current blockchain landscape. As the number of Layer 2 solutions continues to grow, the ability to move assets and data seamlessly between networks becomes increasingly important for maintaining user experience and preventing ecosystem fragmentation.
Current bridging solutions typically rely on various trust assumptions and security models, ranging from simple multi-signature schemes to more sophisticated systems involving economic incentives and fraud proofs. The choice of bridging mechanism involves trade-offs between security, speed, cost, and complexity, with different approaches suitable for different types of assets and use cases. Understanding these trade-offs is crucial for users and developers working with cross-chain applications.
The development of standardized communication protocols like the Inter-Blockchain Communication protocol and various cross-chain messaging systems promises to improve interoperability while reducing the complexity and security risks associated with current bridging solutions. These protocols enable more sophisticated cross-chain applications that can leverage the unique capabilities of different networks while maintaining unified user experiences.
Native interoperability features built into Layer 2 protocols represent another approach to addressing fragmentation, with some networks designing their architecture to facilitate communication with other chains from the ground up. This approach can provide better security guarantees and user experience than retrofitted bridging solutions but requires coordination and standardization across different network development teams.
The future of Layer 2 interoperability may involve the development of shared security models where multiple networks inherit security from Ethereum while maintaining their independence and specialization. This approach could enable a more unified ecosystem where users and developers can move freely between networks without sacrificing security or dealing with complex bridging procedures.
Security Considerations and Risk Assessment
Security in Layer 2 solutions involves complex trade-offs and novel risk vectors that differ significantly from the security model of Ethereum mainnet. Understanding these risks is crucial for users, developers, and institutions considering Layer 2 adoption, as the consequences of security failures can include loss of funds, data integrity issues, and broader ecosystem disruption.
The security models of different Layer 2 approaches involve varying assumptions about validator behavior, data availability, and cryptographic security. Optimistic rollups rely on economic incentives and fraud proof mechanisms that assume at least one honest validator will challenge invalid state transitions. Zero-knowledge rollups depend on the cryptographic security of proof systems and the correctness of proof generation software. State channels require participants to remain online and monitor for fraudulent state updates.
Data availability represents a critical security consideration for all Layer 2 solutions, as the ability to reconstruct state and challenge invalid transitions depends on having access to the necessary transaction data. Different solutions make different trade-offs regarding data availability, with some posting all data to Ethereum for maximum security while others use data availability committees or alternative storage solutions to reduce costs at the expense of some security guarantees.
Smart contract security in Layer 2 environments involves additional complexity due to the interaction between Layer 1 and Layer 2 systems, cross-chain communication mechanisms, and novel token bridge architectures. The immutability and upgrade mechanisms of Layer 2 systems also differ from Ethereum mainnet, requiring careful consideration of governance and emergency response procedures.
The centralization risks in many current Layer 2 implementations represent another important security consideration, as many networks rely on single operators or small sets of validators to function correctly. While these systems typically include mechanisms for users to exit if operators act maliciously, the practical implementation and usability of these mechanisms vary significantly between different solutions.
Performance Metrics and Benchmarking
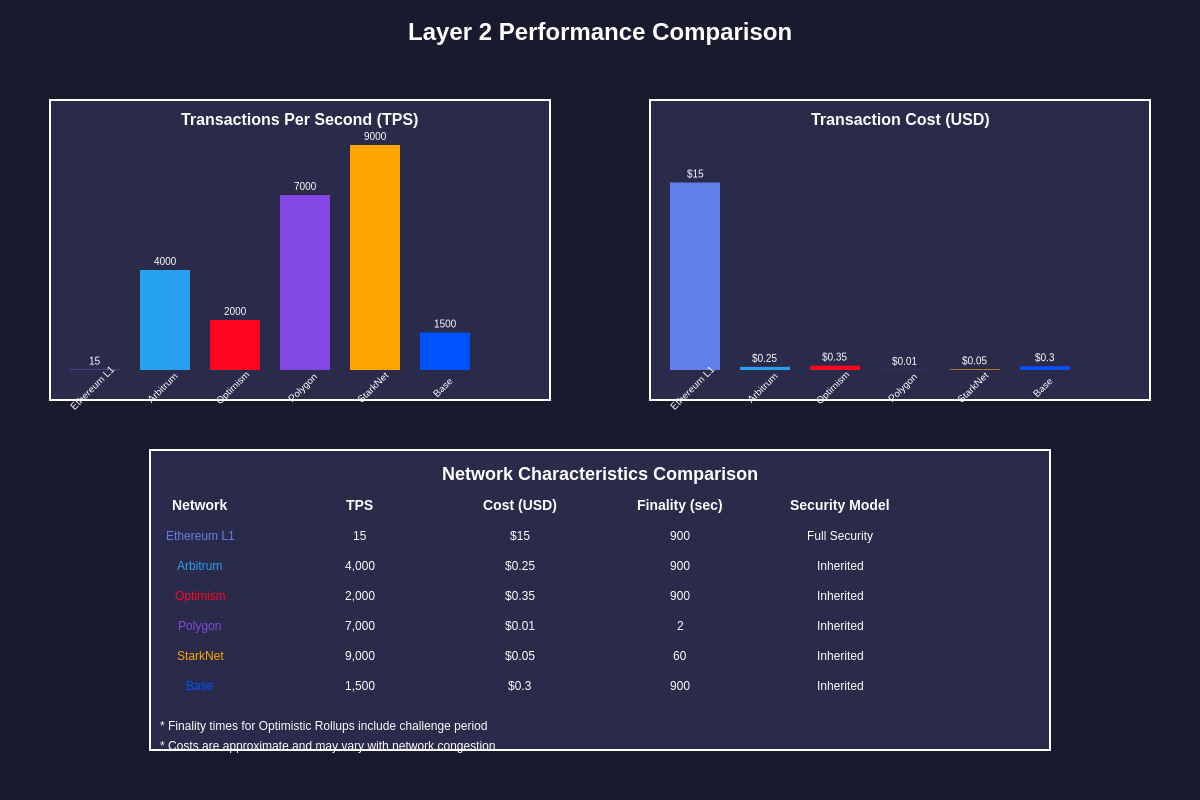
Evaluating the performance of Layer 2 solutions requires consideration of multiple metrics beyond simple transaction throughput, including latency, cost efficiency, finality times, and resource requirements. Professional traders and developers utilize comprehensive analytical tools to assess these performance characteristics and make informed decisions about platform selection for their specific use cases.
Transaction throughput measurements must account for the different types of transactions and complexity of operations being performed, as simple transfers can be processed much more efficiently than complex smart contract interactions involving multiple state changes and external calls. Peak throughput capabilities may differ significantly from sustained performance under realistic network conditions, making real-world performance testing crucial for accurate assessment.
Cost analysis involves understanding the different components of transaction fees and how they scale with network utilization and Ethereum mainnet costs. The predictability of costs during periods of high demand represents an important factor for applications requiring stable operational expenses, while the absolute cost levels determine the economic viability of different types of transactions and business models.
Finality characteristics vary significantly between Layer 2 solutions, with some providing instant soft finality while others require waiting periods for challenges or proof submission. The security level of different finality states affects how applications should handle transaction confirmation and user experience, particularly for high-value transactions or time-sensitive operations.
Decentralization metrics including validator set size, geographic distribution, and stake distribution provide insight into the censorship resistance and long-term sustainability of different Layer 2 networks. These factors become increasingly important as networks mature and handle larger transaction volumes and higher value operations.
Future Developments and Technological Roadmaps
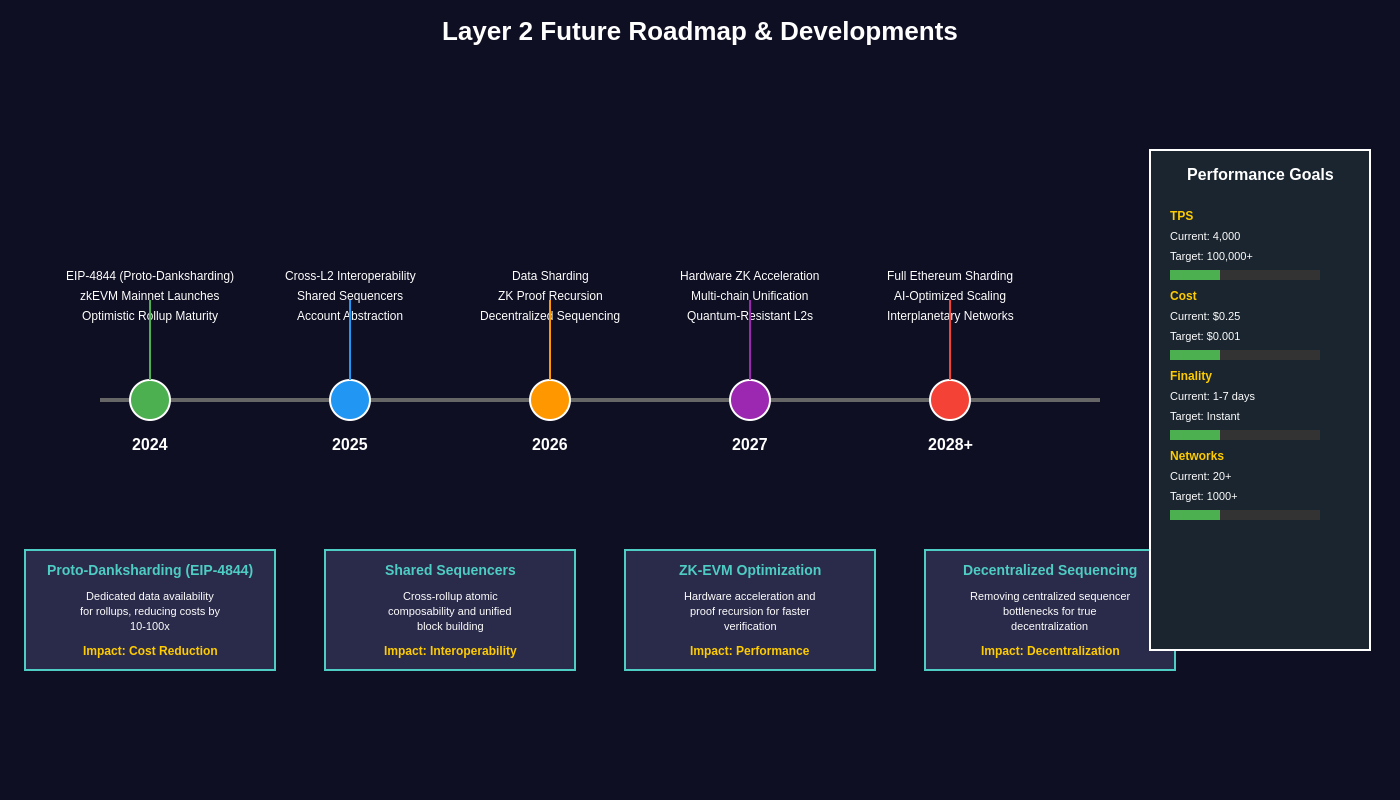
The Layer 2 ecosystem continues to evolve rapidly, with significant technological developments and upgrades planned across different networks and scaling approaches. Understanding these roadmaps is crucial for making informed decisions about platform adoption and long-term strategic planning in the evolving blockchain landscape.
Ethereum’s planned upgrades, including data sharding and statelessness improvements, promise to significantly reduce the costs and complexity of Layer 2 operations while improving the security and decentralization properties of rollup solutions. The Proto-Danksharding upgrade represents the first step toward dedicated data availability for rollups, potentially reducing costs by orders of magnitude while maintaining security guarantees.
Zero-knowledge technology continues to advance rapidly, with improvements in proof generation speed, verification efficiency, and support for more complex computation. The development of hardware acceleration for proof generation and verification promises to make ZK rollups more practical for general-purpose computation, while advances in proof recursion and aggregation could enable new scaling paradigms that were previously impossible.
The convergence of different Layer 2 approaches through technologies like fraud proofs for ZK rollups and validity proofs for optimistic systems may blur the traditional distinctions between different scaling solutions. This hybrid approach could combine the benefits of different systems while mitigating their respective weaknesses, leading to more robust and versatile scaling infrastructure.
Interoperability improvements including standardized cross-chain communication protocols and shared security models promise to reduce fragmentation while maintaining the benefits of specialization and experimentation. The development of intent-based systems and cross-chain automated market makers could further improve user experience by abstracting away the complexity of multi-chain interactions.
Regulatory Landscape and Compliance Considerations
The regulatory environment surrounding Layer 2 solutions continues to evolve as policymakers and regulatory bodies develop their understanding of blockchain scaling technologies and their implications for financial regulation, consumer protection, and systemic risk. The regulatory treatment of Layer 2 networks may differ significantly from mainnet Ethereum due to their different security models, governance structures, and operational characteristics.
The classification of Layer 2 tokens and governance mechanisms represents an area of ongoing regulatory uncertainty, with different jurisdictions potentially taking different approaches to networks that distribute tokens to users, fund public goods, or implement novel governance models. The decentralization level and control structures of different Layer 2 networks may influence their regulatory treatment and compliance requirements.
Cross-border operations and the global nature of Layer 2 networks create additional regulatory complexity, as networks may need to comply with regulations in multiple jurisdictions while maintaining their permissionless and decentralized characteristics. The development of regulatory sandboxes and collaborative frameworks between different regulatory bodies may help address these challenges while fostering innovation.
The treatment of bridging mechanisms and cross-chain transactions presents unique regulatory challenges, as these operations may involve multiple networks with different regulatory status and compliance requirements. The development of compliance tools and regulatory technology specifically designed for Layer 2 environments will be crucial for institutional adoption and mainstream integration.
Future regulatory developments may focus on establishing clear frameworks for Layer 2 networks that balance innovation and experimentation with consumer protection and systemic risk management. The input of the blockchain community in these regulatory processes will be crucial for developing frameworks that support continued innovation while addressing legitimate regulatory concerns.
Institutional Adoption and Enterprise Use Cases
The adoption of Layer 2 solutions by institutional users and enterprise applications represents a significant growth opportunity that requires addressing specific requirements around compliance, performance guarantees, and integration with existing systems. Understanding these requirements and the solutions being developed to address them provides insight into the potential for mainstream adoption of blockchain technology.
Enterprise applications often require service level agreements, uptime guarantees, and predictable performance characteristics that may not align with the experimental nature of many current Layer 2 implementations. The development of enterprise-grade Layer 2 solutions involves additional infrastructure for monitoring, alerting, and support that goes beyond the basic protocol implementation.
Compliance and audit requirements for institutional users create demand for Layer 2 solutions that can provide detailed transaction logs, support for permissioned operations, and integration with existing compliance and risk management systems. The development of privacy-preserving compliance tools using zero-knowledge technology represents an important area of innovation that could enable institutional adoption while maintaining user privacy.
The integration of Layer 2 solutions with traditional financial infrastructure including payment systems, custody solutions, and regulatory reporting systems requires standardized APIs, robust security practices, and comprehensive documentation. The development of institutional-grade tooling and infrastructure represents a significant opportunity for Layer 2 networks to expand beyond the current crypto-native user base.
The potential for central bank digital currencies and government-issued tokens to utilize Layer 2 infrastructure for scalability while maintaining regulatory control represents another important institutional use case. The requirements for these applications may drive the development of new Layer 2 architectures that balance scalability with the control and auditability requirements of government applications.
Professional traders and institutional investors increasingly rely on sophisticated market analysis platforms to evaluate Layer 2 opportunities and track the performance of various scaling solutions as the ecosystem continues to mature and institutional adoption accelerates.
Disclaimer: This article is for educational and informational purposes only and should not be construed as financial advice. Cryptocurrency investments carry significant risks, including the potential for total loss of capital. Layer 2 solutions involve additional technical risks including smart contract vulnerabilities, bridge security issues, and novel cryptographic assumptions that may not be fully understood. Always conduct your own research and consult with qualified financial advisors before making investment decisions. The author and publisher are not responsible for any financial losses that may occur from acting on the information provided in this article.