The Foundation of Institutional Cryptocurrency Security
Multi-signature wallets have emerged as the cornerstone of security infrastructure for large-scale cryptocurrency lending operations, providing institutional-grade protection for digital assets that often exceed hundreds of millions of dollars in value. These sophisticated cryptographic systems require multiple authorized signatures before any transaction can be executed, creating robust safeguards against both external attacks and internal threats that could compromise massive lending portfolios.
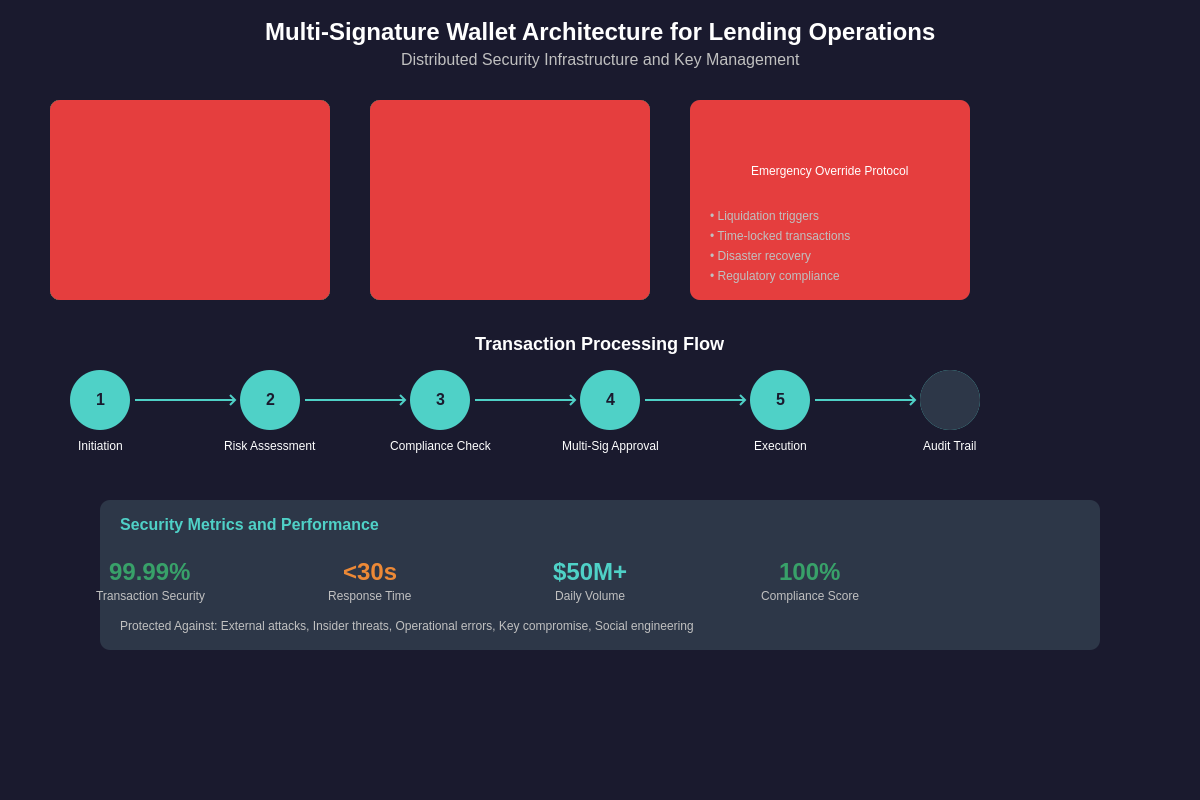
The complexity and scale of modern cryptocurrency lending operations, which involve billions of dollars in digital assets flowing between borrowers, lenders, and collateral pools, demand security measures that far exceed those required for individual or small-scale transactions. Multi-signature wallets address these requirements by distributing control among multiple stakeholders while maintaining the operational efficiency necessary for high-volume lending activities that process thousands of transactions daily.
Leading cryptocurrency lending platforms have implemented sophisticated multi-signature architectures that balance security requirements with operational needs, incorporating advanced features such as time-locked transactions, hierarchical key management, and automated compliance monitoring. These systems must operate seamlessly across multiple blockchain networks while maintaining the highest levels of security for assets that represent significant portions of the global cryptocurrency lending market.
The implementation of multi-signature wallets in lending operations requires careful consideration of factors including key distribution strategies, signature threshold optimization, operational workflow integration, and regulatory compliance requirements. Each decision in the design and deployment process can have significant implications for both security and operational efficiency, making proper planning and implementation critical for successful large-scale lending operations.
Technical Architecture and Key Management Strategies
The technical architecture underlying multi-signature wallets for large lending operations involves sophisticated cryptographic protocols that must balance security, scalability, and operational requirements across diverse blockchain networks and lending scenarios. Modern multi-signature implementations utilize advanced cryptographic schemes including threshold signatures, hierarchical deterministic key generation, and hardware security module integration to create robust security frameworks capable of protecting billions of dollars in digital assets.
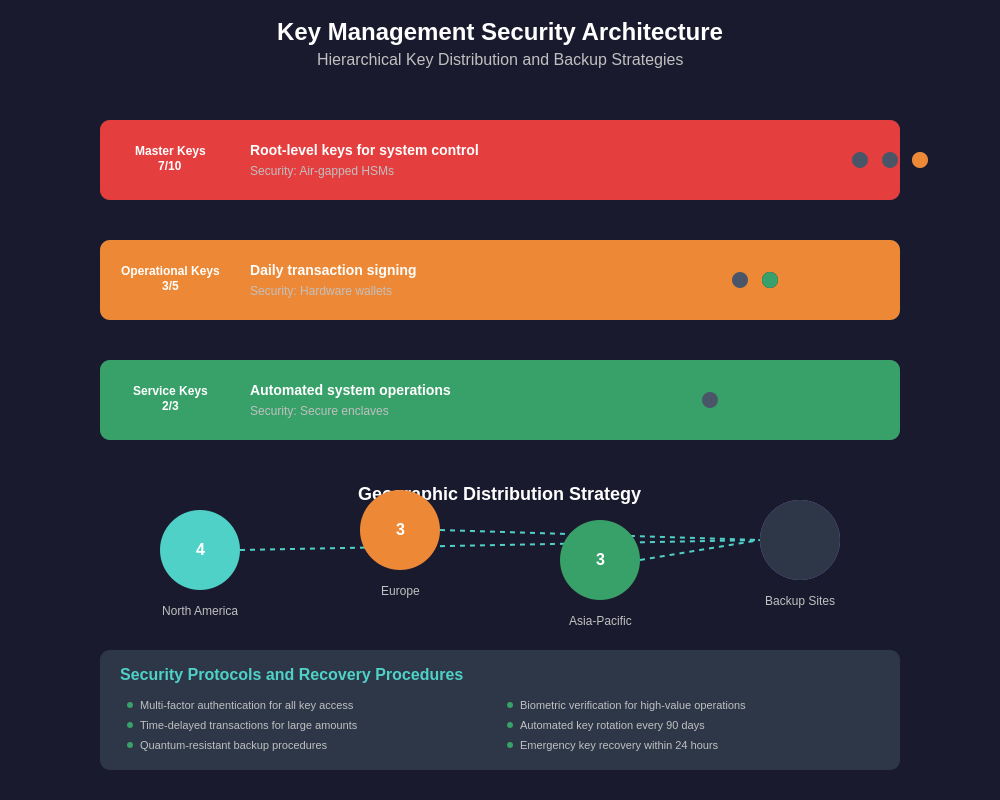
Key management strategies for large lending operations typically employ hierarchical structures that separate operational keys from master keys, enabling different levels of access and control based on transaction types, amounts, and risk assessments. Master keys are often stored in air-gapped hardware security modules or specialized custody solutions, while operational keys may be distributed across multiple geographic locations and stored in hardware wallets or secure enclaves to prevent single points of failure.
The signature threshold configuration represents one of the most critical decisions in multi-signature wallet design, with lending operations typically implementing different thresholds for different transaction types and amounts. Small operational transactions might require a simple 2-of-3 signature scheme, while large fund movements or configuration changes might require 5-of-7 or even higher thresholds to ensure adequate oversight and security for high-value operations.
Detailed analysis of multi-signature wallet security architectures reveals the importance of proper key rotation procedures, backup strategies, and disaster recovery planning in maintaining long-term security for lending operations. These systems must be designed to handle various failure scenarios including key compromise, hardware failure, and personnel changes while maintaining continuous operation of critical lending functions.
Operational Workflows and Transaction Processing
The operational workflows required for multi-signature wallets in large lending operations involve complex coordination between multiple stakeholders, automated systems, and manual oversight processes designed to ensure both security and efficiency in high-volume transaction processing environments. These workflows must accommodate the unique requirements of lending operations including collateral management, liquidation procedures, interest payments, and borrower fund disbursements while maintaining strict security controls.
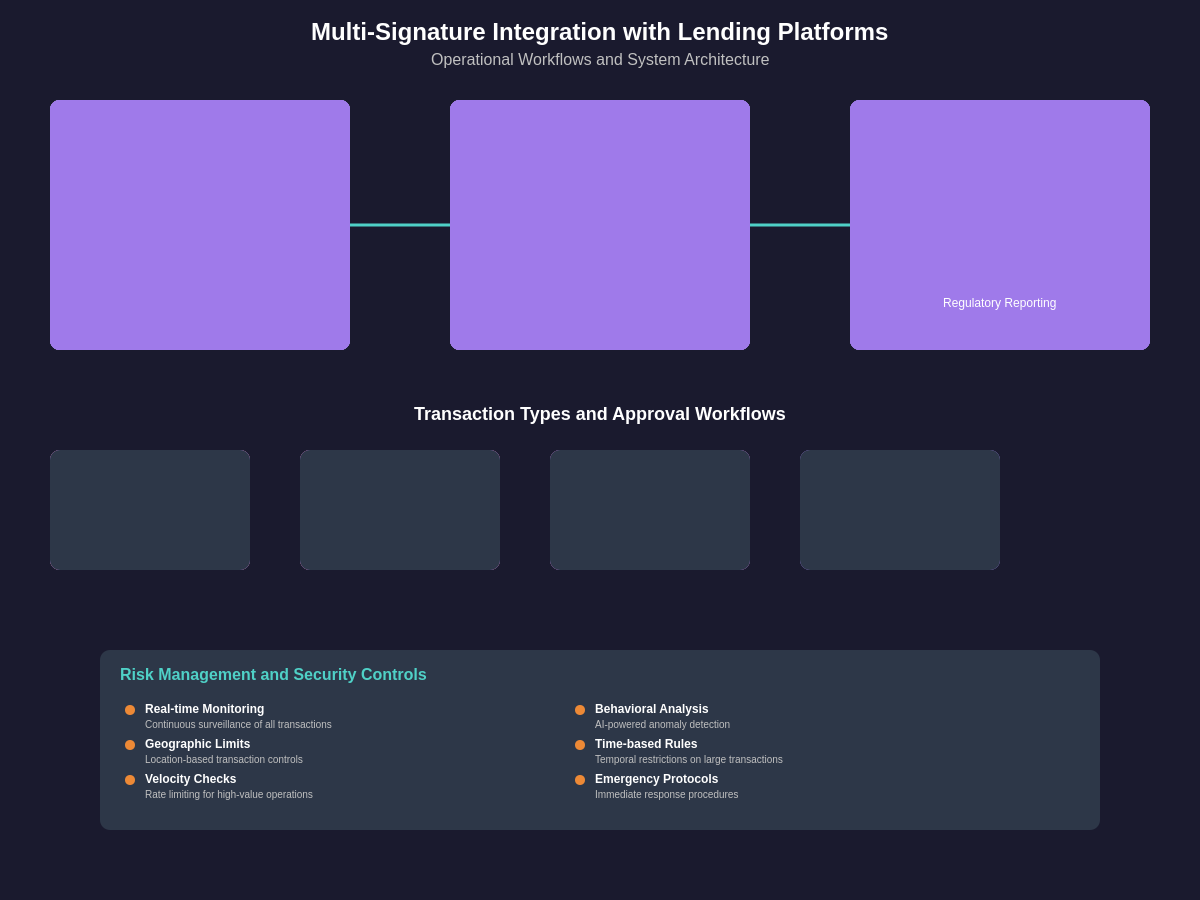
Transaction processing in multi-signature lending systems typically involves multiple stages including transaction initiation, risk assessment, compliance verification, signature collection, and final execution, with each stage incorporating appropriate security measures and audit trails. Automated systems handle routine transactions such as interest payments and collateral adjustments, while larger transactions or those meeting specific risk criteria require manual review and approval from designated signatories.
The coordination of signatures across multiple parties and systems presents significant operational challenges, particularly for time-sensitive transactions such as liquidations that must be executed quickly to prevent losses due to market volatility. Advanced multi-signature systems incorporate features such as offline signing capabilities, mobile signature applications, and emergency override procedures to ensure that critical transactions can be processed even under adverse conditions.
Integration with existing lending platform infrastructure requires sophisticated APIs and middleware systems that can coordinate multi-signature operations with portfolio management systems, risk monitoring tools, and compliance platforms. These integrations must maintain the security benefits of multi-signature wallets while providing the operational efficiency required for high-volume lending operations that may process thousands of transactions daily.
Risk Management and Compliance Frameworks
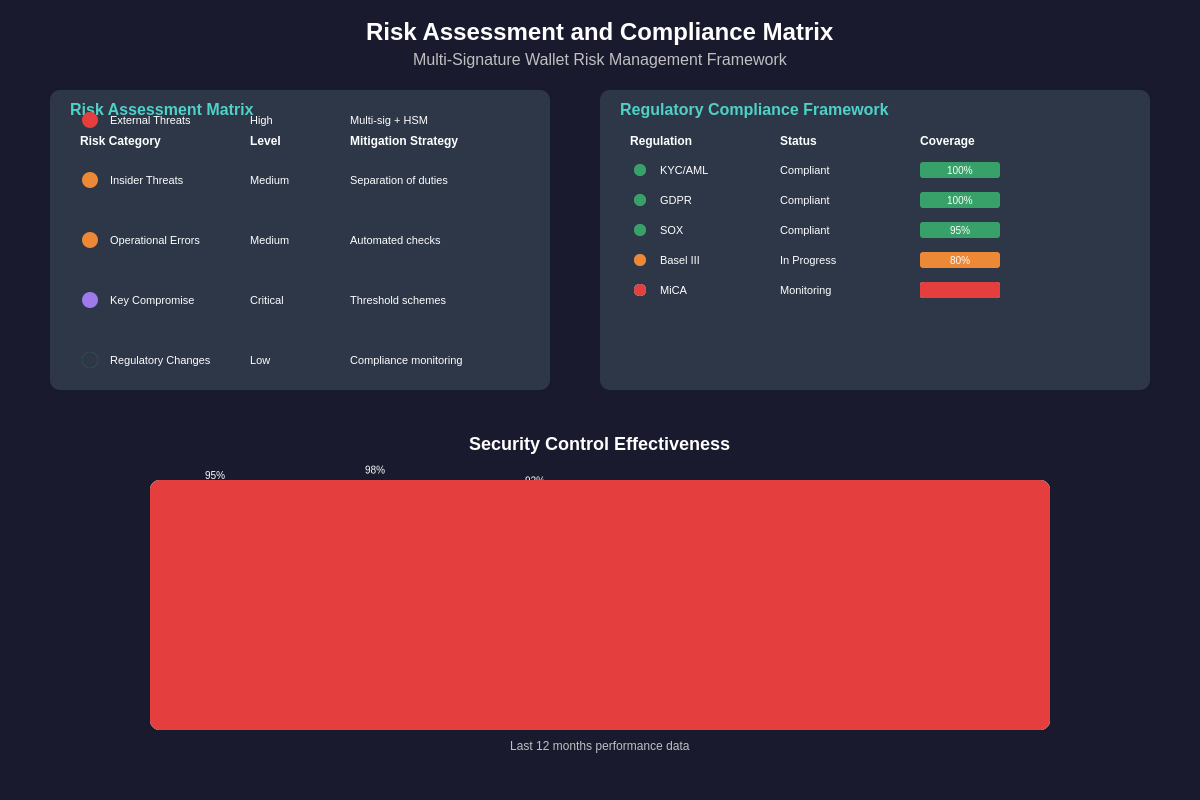
Risk management frameworks for multi-signature wallets in lending operations must address a complex array of threats including external attacks, insider threats, operational errors, and regulatory compliance requirements while maintaining the flexibility needed for dynamic lending markets. These frameworks incorporate multiple layers of protection including transaction monitoring, anomaly detection, compliance verification, and audit trail maintenance to ensure comprehensive protection of lending assets.
The assessment and mitigation of insider threats represents a particularly critical aspect of multi-signature wallet security for lending operations, as authorized signatories have access to systems controlling billions of dollars in digital assets. Advanced risk management systems implement behavioral monitoring, access controls, background verification procedures, and separation of duties to minimize the risk of internal fraud or misconduct while maintaining operational efficiency.
Compliance frameworks for multi-signature wallets must accommodate diverse regulatory requirements across multiple jurisdictions while supporting the global nature of cryptocurrency lending operations. These frameworks incorporate automated compliance monitoring, transaction screening, reporting capabilities, and audit trail maintenance to ensure adherence to anti-money laundering regulations, know-your-customer requirements, and financial services regulations that apply to lending operations.
Real-time monitoring and alerting systems provide continuous oversight of multi-signature wallet operations, detecting suspicious activities, unauthorized access attempts, and operational anomalies that could indicate security breaches or system failures. These systems must balance sensitivity with practicality to avoid generating excessive false alarms while ensuring that genuine threats are detected and responded to promptly.
Hardware Security Integration and Infrastructure Requirements
The integration of hardware security modules and specialized custody infrastructure represents a critical component of multi-signature wallet implementations for large lending operations, providing additional layers of protection for the cryptographic keys that control access to billions of dollars in digital assets. These hardware solutions offer tamper-resistant key storage, secure key generation, and isolated signature processing capabilities that significantly enhance the security posture of multi-signature systems.
Enterprise-grade hardware security modules designed for cryptocurrency applications provide features including secure key backup and recovery, audit logging, role-based access controls, and integration capabilities with existing IT infrastructure. The selection and configuration of appropriate hardware security solutions requires careful consideration of factors including performance requirements, scalability needs, regulatory compliance, and integration complexity.
The physical security and geographic distribution of hardware security infrastructure presents additional challenges for large lending operations, with many organizations implementing multi-site configurations to prevent single points of failure while maintaining operational continuity. These distributed architectures must balance security benefits with operational complexity and cost considerations while ensuring that signature collection processes can operate efficiently across multiple locations.
Network security and communication protocols for multi-signature wallet infrastructure require sophisticated protection against various attack vectors including man-in-the-middle attacks, network surveillance, and communication interception. Advanced implementations utilize encrypted communication channels, secure authentication protocols, and network segmentation to protect sensitive signature processes and key management operations from external threats.
Regulatory Landscape and Legal Considerations
The regulatory landscape governing multi-signature wallets in cryptocurrency lending operations continues to evolve rapidly across different jurisdictions, with regulators increasingly focusing on custody requirements, operational security standards, and consumer protection measures that directly impact multi-signature wallet implementations. Large lending operations must navigate complex regulatory frameworks while maintaining the security and operational benefits that multi-signature wallets provide.
Custody regulations in major financial centers including the United States, European Union, and Asia-Pacific regions impose specific requirements on how cryptocurrency lending platforms must protect customer assets, with many jurisdictions requiring segregation of customer funds, insurance coverage, and specific security measures that influence multi-signature wallet design and implementation strategies.
The legal framework surrounding multi-signature wallets involves complex questions about liability, asset ownership, and recovery procedures in cases of key loss or compromise, with different jurisdictions providing varying levels of legal clarity and protection for both lending platforms and their customers. These legal considerations must be carefully evaluated during the design and implementation of multi-signature systems to ensure appropriate protection for all stakeholders.
Cross-border regulatory compliance presents particular challenges for global cryptocurrency lending operations, as multi-signature wallet systems must accommodate diverse regulatory requirements while maintaining operational efficiency and security standards. The harmonization of regulatory standards and the development of international cooperation frameworks remain ongoing challenges that affect the design and operation of multi-signature wallet systems.
Economic Impact and Market Dynamics
The economic impact of multi-signature wallet adoption in cryptocurrency lending markets extends beyond security benefits to include effects on market confidence, lending rates, insurance costs, and overall market stability that influence the broader cryptocurrency ecosystem. Large lending operations utilizing robust multi-signature security measures often benefit from lower borrowing costs, improved access to institutional capital, and enhanced market credibility that translates to competitive advantages.
The relationship between multi-signature wallet security and lending rates reflects the risk premium that borrowers and lenders place on security measures, with platforms demonstrating superior security practices often able to offer more competitive rates due to reduced operational risks and lower insurance costs. Analysis of lending market dynamics reveals the growing importance of security infrastructure in determining market positioning and competitive advantage.
Insurance markets for cryptocurrency lending operations have developed specific products and pricing models that account for multi-signature wallet implementations, with insurers offering more favorable terms and higher coverage limits for operations demonstrating appropriate security measures. The availability and cost of insurance coverage can significantly impact the economics of large lending operations and influence adoption of specific multi-signature architectures.
The systemic risks associated with large lending operations and the role of multi-signature wallets in mitigating these risks have become increasingly important considerations for regulators and market participants as the cryptocurrency lending market continues to grow and mature. The failure of major lending platforms can have significant market-wide effects, making robust security infrastructure a matter of systemic importance.
Emerging Technologies and Future Developments
The evolution of multi-signature wallet technology continues to advance with the development of new cryptographic protocols, blockchain platforms, and security innovations that promise to enhance the capabilities and efficiency of multi-signature systems for large lending operations. Emerging technologies including threshold signature schemes, zero-knowledge proofs, and quantum-resistant cryptography represent significant opportunities for improving multi-signature wallet security and functionality.
Threshold signature schemes offer the potential to reduce the operational complexity of multi-signature wallets while maintaining or enhancing security levels, enabling more efficient signature collection processes and reducing the risks associated with key management and coordination. These advanced cryptographic protocols can significantly simplify the operational workflows required for large lending operations while providing enhanced security guarantees.
The integration of artificial intelligence and machine learning technologies into multi-signature wallet systems promises to enhance risk assessment, fraud detection, and operational optimization capabilities that can improve both security and efficiency for large lending operations. These technologies can provide advanced behavioral analysis, anomaly detection, and predictive capabilities that supplement traditional security measures.
Cross-chain interoperability solutions and layer-two scaling technologies are developing capabilities that could significantly enhance the functionality and efficiency of multi-signature wallets for lending operations that span multiple blockchain networks. These developments could reduce transaction costs, improve processing speeds, and enable new types of lending products while maintaining the security benefits of multi-signature architectures.
Implementation Best Practices and Case Studies
The implementation of multi-signature wallets for large lending operations requires careful attention to best practices that have been developed through years of experience in high-stakes cryptocurrency environments, with successful implementations demonstrating common patterns and approaches that maximize both security and operational efficiency. These best practices encompass technical architecture decisions, operational procedures, risk management strategies, and organizational considerations.
The selection of appropriate signature thresholds and key distribution strategies represents one of the most critical implementation decisions, with successful lending operations typically employing tiered approaches that match security requirements to transaction types and amounts. Small operational transactions might utilize 2-of-3 signatures for efficiency, while large fund movements or system configuration changes require higher thresholds such as 5-of-7 or 7-of-10 to ensure adequate oversight.
Key management best practices for large lending operations emphasize the importance of secure key generation, proper backup procedures, regular key rotation schedules, and comprehensive disaster recovery planning that can handle various failure scenarios including key compromise, hardware failure, and personnel changes. The physical and logical separation of master keys from operational keys provides additional protection against both external attacks and insider threats.
Operational security procedures must balance the need for efficiency in high-volume lending operations with the security requirements of multi-signature systems, incorporating features such as automated transaction processing for routine operations, emergency override procedures for time-sensitive situations, and comprehensive audit trails for regulatory compliance and security monitoring purposes.
Technology Integration and Platform Compatibility
The integration of multi-signature wallets with existing lending platform infrastructure requires sophisticated technical solutions that can bridge the gap between traditional financial systems and advanced cryptographic security measures while maintaining the performance and reliability required for large-scale operations. Modern lending platforms must support multiple blockchain networks, diverse cryptocurrency assets, and complex lending products while maintaining the security benefits of multi-signature protection.
API design and middleware development for multi-signature integration involves creating secure communication protocols that can coordinate signature collection processes with portfolio management systems, risk monitoring tools, and compliance platforms without compromising security or operational efficiency. These integrations must handle high transaction volumes while maintaining low latency for time-sensitive operations such as liquidations and margin calls.
Database design and audit trail requirements for multi-signature lending systems must accommodate the complex data structures and relationships involved in multi-party signature processes while maintaining comprehensive records for regulatory compliance and security monitoring. The immutable nature of blockchain transactions combined with traditional database systems creates unique challenges for data management and reconciliation.
Performance optimization for multi-signature systems in high-volume lending environments requires careful consideration of factors including signature collection latency, blockchain confirmation times, and system scalability to ensure that security measures do not become operational bottlenecks that impact lending platform competitiveness or user experience.
Cost-Benefit Analysis and ROI Considerations
The cost-benefit analysis for implementing multi-signature wallets in large lending operations must consider both direct costs including hardware, software, and personnel expenses, as well as indirect benefits including reduced insurance premiums, improved customer confidence, and competitive advantages in the lending market. The scale of assets under management in large lending operations often justifies significant investments in security infrastructure.
Direct implementation costs for enterprise-grade multi-signature systems include hardware security modules, specialized software licenses, integration development, staff training, and ongoing operational expenses that can represent significant initial investments. However, these costs must be evaluated against the potential losses that could result from security breaches, which could exceed hundreds of millions of dollars for large lending operations.
The insurance cost reductions available to lending operations with robust multi-signature security measures can provide significant ongoing savings that help justify the initial implementation costs, with some insurers offering premium reductions of 20-50% for operations demonstrating appropriate security measures. The availability of insurance coverage itself may depend on the implementation of adequate security measures including multi-signature wallets.
Customer acquisition and retention benefits associated with superior security measures can provide substantial indirect benefits for lending operations, as institutional clients increasingly prioritize security when selecting lending platforms. The competitive advantages gained through superior security infrastructure can translate to market share growth and improved lending terms that provide ongoing economic benefits.
Global Adoption Trends and Market Analysis
The global adoption of multi-signature wallets in cryptocurrency lending operations reflects broader trends toward institutional cryptocurrency adoption, regulatory clarity, and security standardization that are reshaping the digital asset lending landscape. Leading lending platforms across major markets including North America, Europe, and Asia have implemented sophisticated multi-signature systems as standard practice for large-scale operations.
Regional variations in regulatory requirements and security standards have influenced the development of different multi-signature wallet implementations, with some jurisdictions requiring specific security measures or certification processes that affect system design and operational procedures. The harmonization of international standards remains an ongoing challenge that affects cross-border lending operations.
Market analysis of cryptocurrency lending volumes and security incidents reveals the correlation between robust security measures and market growth, with platforms demonstrating superior security practices often experiencing faster growth and better customer retention rates than those with weaker security infrastructure.
The institutional adoption of cryptocurrency lending continues to drive demand for enterprise-grade security solutions including multi-signature wallets, with traditional financial institutions entering the cryptocurrency lending market requiring security standards that meet or exceed those used for traditional financial assets. This institutional demand is driving continued innovation and improvement in multi-signature wallet technology and implementation practices.
Future Outlook and Industry Evolution
The future evolution of multi-signature wallets for cryptocurrency lending operations will likely be shaped by continued technological advancement, regulatory development, and market maturation that create new opportunities and challenges for large-scale lending platforms. Emerging technologies including quantum computing, advanced cryptographic protocols, and artificial intelligence promise to enhance the capabilities and security of multi-signature systems while potentially disrupting existing approaches.
The development of quantum-resistant cryptographic protocols represents both an opportunity and a challenge for multi-signature wallet systems, with the potential for quantum computing to compromise existing cryptographic schemes requiring proactive development of quantum-resistant alternatives. The timeline for quantum computing threats and the development of appropriate countermeasures remains a subject of ongoing research and development.
Regulatory evolution in major markets continues to shape the requirements and opportunities for multi-signature wallet implementations, with increasing clarity and standardization expected to reduce compliance complexity while potentially introducing new requirements for security measures, audit procedures, and operational standards that affect multi-signature system design.
The maturation of cryptocurrency lending markets and the continued growth of institutional participation will likely drive further standardization and improvement of multi-signature wallet technologies, with increased interoperability, reduced operational complexity, and enhanced security features expected to emerge from continued industry development and competition.
Disclaimer: This article is for educational purposes only and does not constitute financial, legal, or investment advice. Cryptocurrency lending involves significant risks including potential loss of principal. The implementation of multi-signature wallets requires technical expertise and should be undertaken only with appropriate professional guidance. Regulatory requirements vary by jurisdiction and may change over time. Past performance does not guarantee future results. Always conduct thorough due diligence and consult with qualified professionals before implementing cryptocurrency security systems or engaging in cryptocurrency lending activities.