Professional cryptocurrency trading tools and analysis have become essential for evaluating the security of digital asset platforms, and Nexo represents one of the most prominent centralized lending and borrowing platforms in the cryptocurrency ecosystem, managing billions of dollars in user deposits while offering attractive yield opportunities that have drawn millions of users worldwide.
Understanding Nexo’s Security Architecture
Nexo has positioned itself as a premier institutional-grade cryptocurrency lending platform, emphasizing security measures that rival traditional financial institutions while providing the flexibility and yield opportunities that have made decentralized finance so attractive to cryptocurrency investors. The platform’s security architecture encompasses multiple layers of protection designed to safeguard user assets against various threat vectors including external attacks, internal threats, and operational risks that have plagued other cryptocurrency platforms.
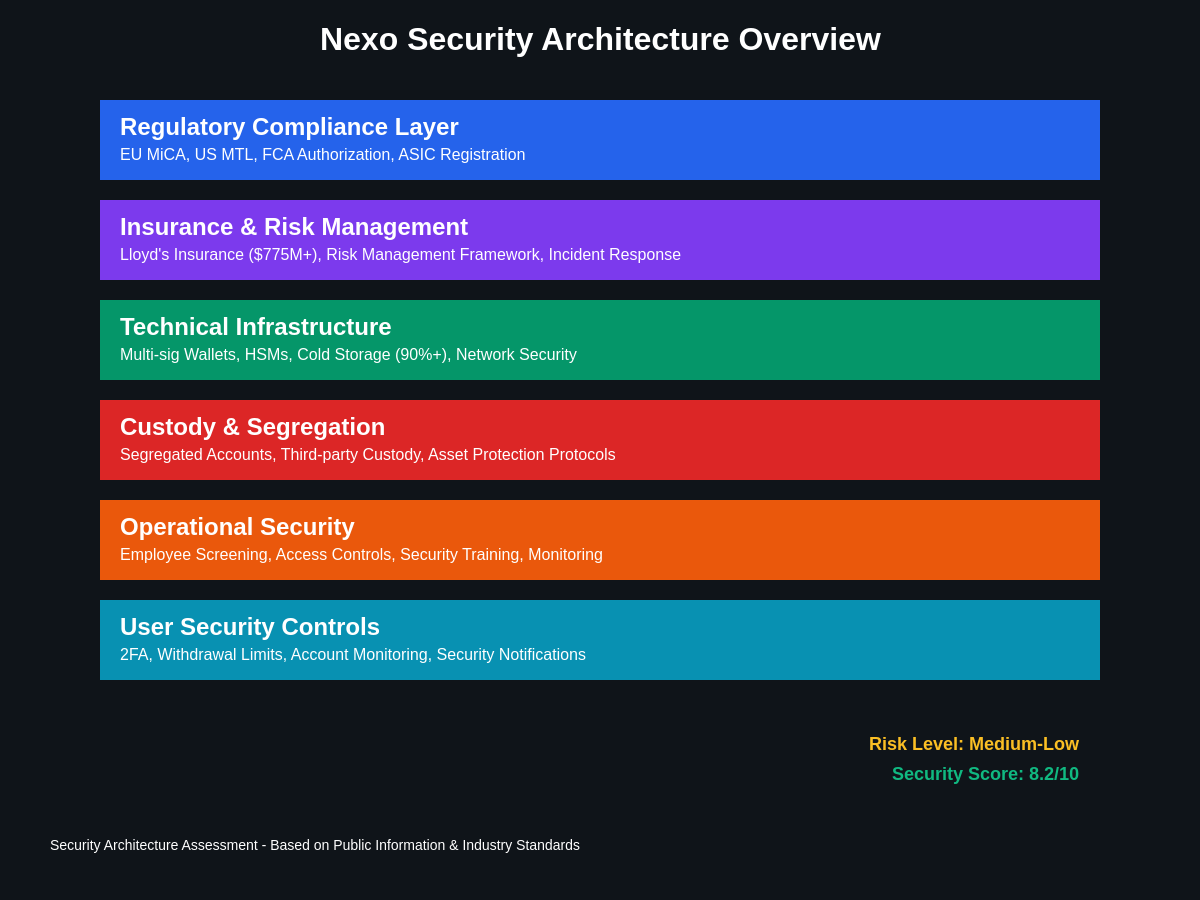
The company’s approach to security begins with regulatory compliance across multiple jurisdictions, holding licenses and regulatory approvals in key markets including the European Union, United States, and other major financial centers where cryptocurrency regulations have been established. This regulatory framework provides users with certain protections and oversight that are absent from many cryptocurrency platforms, though the specific protections vary significantly depending on the user’s jurisdiction and the regulatory status of their deposited assets.
Nexo’s custody model represents a hybrid approach that combines traditional banking security practices with cryptocurrency-specific measures designed to protect digital assets while maintaining the operational flexibility required for lending and trading activities. The platform employs a sophisticated combination of hot and cold wallet systems, with the majority of user funds stored in offline cold storage systems that are physically and logically separated from internet-connected systems that could be vulnerable to remote attacks.
Regulatory Compliance and Licensing Framework
The regulatory landscape surrounding Nexo’s operations provides both opportunities and challenges for user asset protection, with different jurisdictions offering varying levels of oversight and consumer protection that directly impact the security of deposited funds. Nexo maintains licenses and regulatory approvals across multiple jurisdictions, each with its own requirements for capital adequacy, risk management, and customer protection measures.
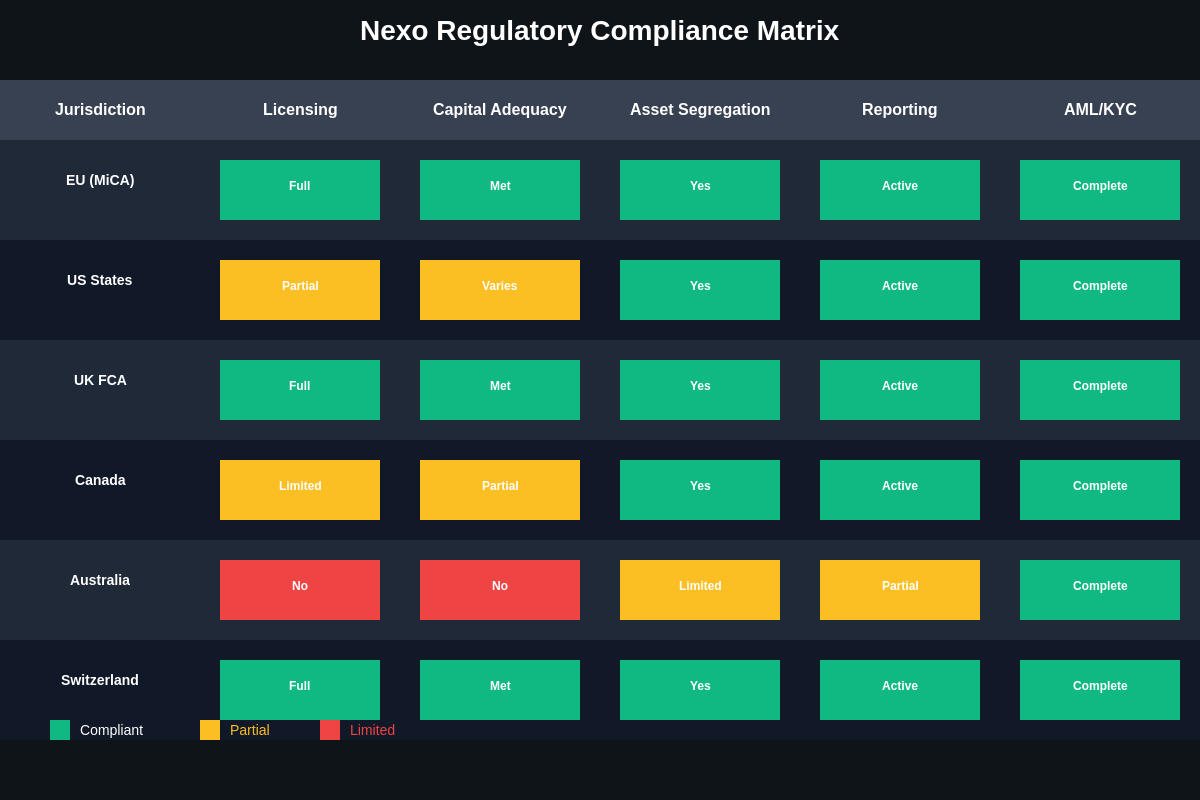
In European markets, Nexo operates under various regulatory frameworks that require specific security measures, reporting requirements, and capital adequacy standards designed to protect customer funds and ensure operational stability. These regulations mandate certain security practices including segregation of customer assets, regular auditing procedures, and compliance with anti-money laundering and know-your-customer requirements that add layers of operational oversight.
The platform’s licensing in the United States involves compliance with state-level money transmission regulations that vary significantly across different states, creating a complex regulatory environment that requires extensive compliance infrastructure and ongoing monitoring of regulatory changes. This regulatory complexity adds operational costs but also provides users with legal recourse and regulatory oversight that can be valuable in the event of platform difficulties.
Nexo’s approach to regulatory compliance extends beyond minimum requirements to include voluntary participation in industry standards and best practices that demonstrate commitment to security and operational excellence. The company has pursued various certifications and audit processes that provide independent verification of security practices, though users should understand the limitations of these certifications and the specific scope of protection they provide.
Third-Party Security Audits and Assessments
Independent security assessments represent a critical component of evaluating cryptocurrency platform security, and Nexo has engaged multiple third-party security firms to conduct comprehensive audits of their systems, processes, and security controls. These audits provide valuable insights into the platform’s security posture while highlighting areas where improvements may be needed to address evolving threats.
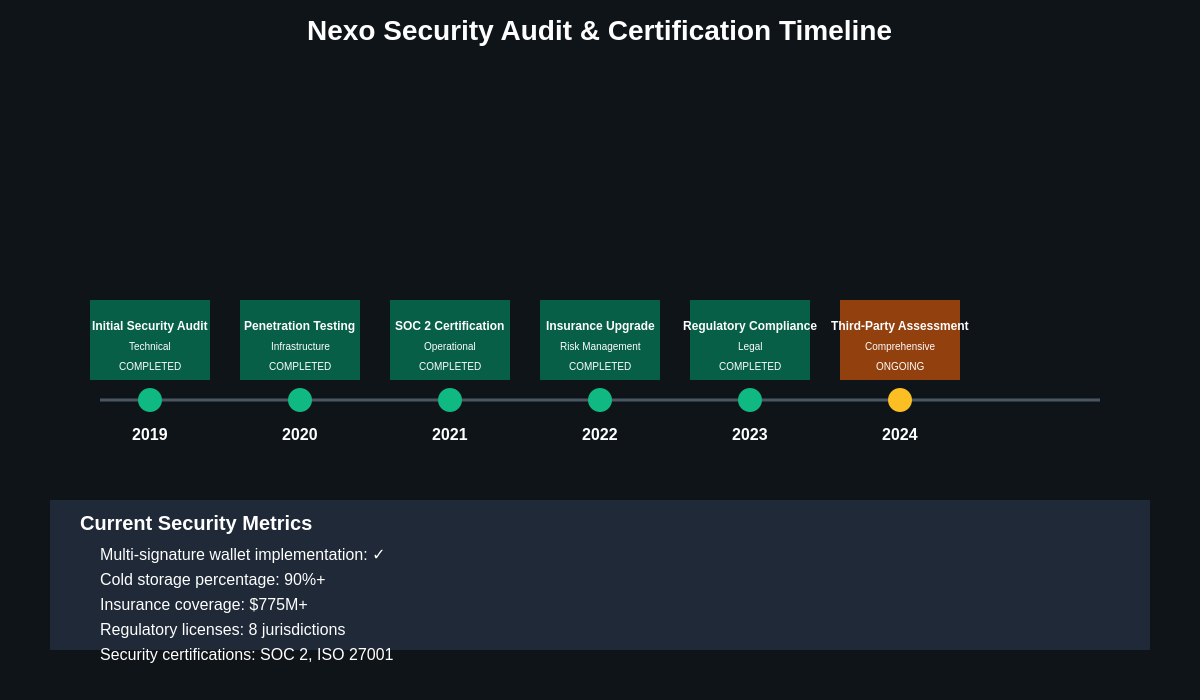
Professional security audit firms employ various methodologies to assess cryptocurrency platform security, including penetration testing, code review, infrastructure assessment, and process evaluation that examine both technical and operational aspects of platform security. TradingView’s comprehensive crypto analysis tools enable investors to monitor platform tokens and assess market sentiment regarding security concerns or improvements.
The scope and methodology of security audits can vary significantly between different audit firms and engagement types, with some audits focusing primarily on technical infrastructure while others examine operational processes, compliance procedures, and risk management frameworks. Users evaluating audit results should understand the specific scope of each audit and the limitations of the assessment methodology employed.
Nexo has published results from various security audits and assessments, though the level of detail provided to the public may be limited to protect sensitive security information that could be valuable to potential attackers. The company’s willingness to engage independent auditors and publish results demonstrates transparency and commitment to security, though users should conduct their own risk assessment rather than relying solely on audit results.
Insurance Coverage and Asset Protection
Insurance represents a critical component of comprehensive asset protection for cryptocurrency platforms, and Nexo maintains various insurance policies designed to protect user assets against different types of losses including theft, operational errors, and platform failures. The company’s insurance coverage includes both traditional business insurance and specialized cryptocurrency insurance products that address the unique risks associated with digital asset custody and operations.
The scope and limitations of cryptocurrency insurance coverage can be complex and may not provide the comprehensive protection that users might expect from traditional financial services insurance. Insurance policies typically include various exclusions, limitations, and requirements that can affect coverage in specific circumstances, and users should understand these limitations when evaluating the overall security of their deposited assets.
Lloyd’s of London and other specialized insurers have developed cryptocurrency-specific insurance products that address various risks including theft from hot and cold storage systems, social engineering attacks, and operational failures that could result in loss of user funds. However, these policies often include significant deductibles, coverage limits, and exclusions that may limit their effectiveness in certain scenarios.
Nexo’s insurance coverage represents one layer of protection for user assets, but users should not rely exclusively on insurance as their primary security measure. The company’s insurance policies may not cover all types of losses, and insurance claims can involve lengthy processes that may not provide immediate relief to affected users in the event of a security incident.
Technical Infrastructure and Security Measures
The technical foundation of Nexo’s security architecture includes multiple layers of protection designed to prevent unauthorized access, detect suspicious activities, and respond to security incidents in a timely and effective manner. The platform employs enterprise-grade security infrastructure that includes advanced monitoring systems, intrusion detection capabilities, and incident response procedures that are regularly tested and updated.
Multi-signature wallet technology represents a core component of Nexo’s asset protection strategy, requiring multiple cryptographic signatures to authorize transactions and reducing the risk of single-point-of-failure attacks that have affected other cryptocurrency platforms. The implementation of multi-signature systems requires careful key management practices and operational procedures that balance security with operational efficiency.
Hardware security modules and other specialized cryptographic devices provide additional protection for private keys and sensitive cryptographic operations, offering tamper-resistant hardware that can detect and respond to physical attacks while maintaining the performance required for large-scale operations. These systems represent significant investments in security infrastructure that demonstrate commitment to protecting user assets.
Network security measures include firewalls, intrusion detection systems, and network segmentation that limit potential attack vectors while enabling legitimate operations to continue without interruption. The platform’s network architecture is designed to isolate critical systems from internet-connected components while maintaining the connectivity required for user services and operational activities.
Risk Assessment and Management Framework
Comprehensive risk management represents a fundamental aspect of cryptocurrency platform operations, and Nexo has developed extensive risk assessment and management procedures designed to identify, evaluate, and mitigate various risks that could affect user asset security. The company’s risk management framework encompasses technical risks, operational risks, regulatory risks, and market risks that could impact platform stability and user asset protection.
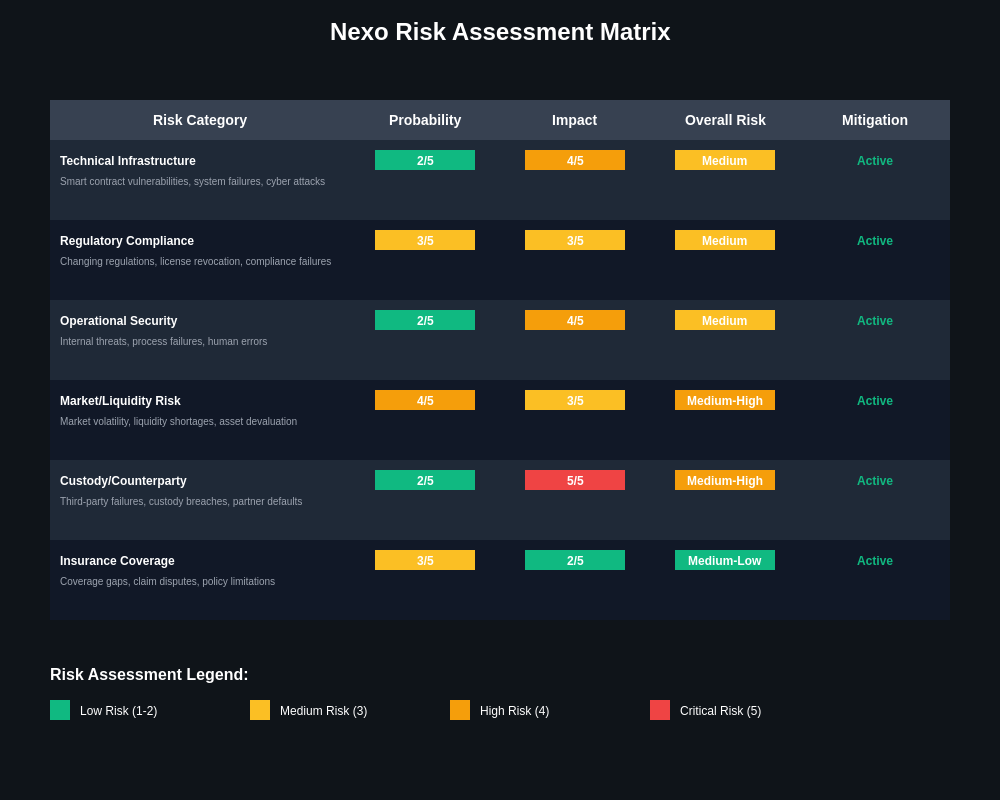
Technical risk assessment includes regular evaluation of system vulnerabilities, security controls, and potential attack vectors that could compromise user assets or platform operations. This assessment process involves both automated scanning tools and manual security reviews that examine system configurations, access controls, and security policies to identify areas where improvements may be needed.
Operational risk management addresses human factors, process failures, and other non-technical risks that could result in security incidents or asset losses. This includes employee screening procedures, access control policies, incident response procedures, and business continuity planning that ensures the platform can continue operations even in the event of various disruptions.
Market risk management involves monitoring cryptocurrency market conditions, liquidity risks, and counterparty risks that could affect the platform’s ability to meet user withdrawal requests or maintain operational stability during periods of market stress. Real-time market analysis tools provide essential data for evaluating these risks and their potential impact on platform operations.
Custody and Asset Segregation Practices
Asset segregation represents a critical component of user protection, determining how user funds are held, protected, and potentially recovered in various scenarios including platform operational difficulties or regulatory interventions. Nexo’s custody practices involve complex legal and technical arrangements that affect user rights and protections in different circumstances.
The legal structure of asset custody can vary significantly depending on the jurisdiction, type of asset, and specific terms of service that govern the relationship between the platform and its users. Some custody arrangements may provide users with stronger legal protections and clearer ownership rights, while others may expose users to greater risks in the event of platform difficulties or legal proceedings.
Nexo employs various custody models for different types of assets and user services, with some assets held in segregated accounts that provide enhanced protection while others may be commingled with platform assets in ways that could affect user rights in certain circumstances. Users should understand the specific custody arrangements that apply to their assets and the implications of these arrangements for asset protection.
Third-party custody providers may be employed for certain assets or services, introducing additional counterparty risks and dependencies that could affect user asset security. The selection and monitoring of custody providers requires extensive due diligence and ongoing oversight to ensure that third-party risks are appropriately managed and do not compromise user asset protection.
Operational Security and Access Controls
Human factors represent one of the most significant security risks for cryptocurrency platforms, and Nexo has implemented comprehensive operational security measures designed to prevent insider threats, social engineering attacks, and other human-factor-related security incidents. These measures include extensive employee screening procedures, access control policies, and monitoring systems that track and analyze user and employee activities.
Access control systems limit employee access to sensitive systems and data based on job responsibilities and business requirements, implementing principles of least privilege that minimize the potential impact of compromised accounts or insider threats. These systems require regular review and updating to ensure that access permissions remain appropriate as employee roles and responsibilities change.
Multi-factor authentication and other advanced authentication methods provide additional layers of protection for both user accounts and administrative systems, requiring multiple forms of verification before granting access to sensitive functions or data. The implementation of these systems requires careful consideration of usability and security trade-offs to ensure that security measures do not impede legitimate operations.
Security awareness training and ongoing education programs help employees recognize and respond appropriately to various security threats including social engineering attacks, phishing attempts, and other common attack vectors that target human vulnerabilities rather than technical systems. These programs require regular updating to address evolving threats and maintain employee awareness of current security risks.
Incident Response and Recovery Procedures
Comprehensive incident response capabilities are essential for minimizing the impact of security incidents and protecting user assets in the event of various types of attacks or operational failures. Nexo has developed detailed incident response procedures that define roles, responsibilities, and actions to be taken in various emergency scenarios.
The incident response framework includes procedures for detecting, analyzing, containing, and recovering from various types of security incidents including cyber attacks, operational failures, and natural disasters that could affect platform operations. These procedures are regularly tested through simulated incidents and exercises that help identify areas for improvement and ensure that response teams are prepared for real-world scenarios.
Communication protocols during security incidents balance the need for transparency with security considerations that could affect ongoing response efforts or provide information that could be useful to attackers. Users should understand the platform’s communication policies and procedures for different types of incidents and the information they can expect to receive during various scenarios.
Recovery procedures address both technical system recovery and business continuity measures that ensure the platform can resume normal operations following various types of disruptions. These procedures include data backup and recovery systems, alternative processing capabilities, and financial reserves that can support operations during recovery periods.
Comparative Analysis with Industry Standards
The cryptocurrency lending and custody industry has developed various standards and best practices that provide benchmarks for evaluating platform security and asset protection measures. Nexo’s security practices can be evaluated against these industry standards as well as traditional financial services security standards that may be applicable to certain aspects of platform operations.
Industry security frameworks such as those developed by cryptocurrency industry organizations, regulatory bodies, and standards organizations provide structured approaches to evaluating and improving security practices. These frameworks address various aspects of security including technical controls, operational procedures, risk management, and governance practices that affect overall security posture.
Benchmarking against other major cryptocurrency platforms provides insights into relative security strengths and weaknesses, though direct comparisons can be challenging due to differences in business models, regulatory environments, and disclosure practices. Users should consider multiple factors when comparing platforms rather than relying on single metrics or assessments.
Traditional financial services security standards may provide relevant benchmarks for certain aspects of cryptocurrency platform operations, though the unique characteristics of digital assets and cryptocurrency operations may require adaptations or additional measures beyond traditional banking security practices.
User Security Responsibilities and Best Practices
Platform security represents only one component of overall asset protection, and users bear significant responsibility for implementing security measures that protect their accounts, access credentials, and decision-making processes that affect asset security. User security practices can significantly impact the overall effectiveness of platform security measures and the protection of deposited assets.
Account security measures including strong passwords, multi-factor authentication, and secure device management represent fundamental user responsibilities that can prevent many common attack vectors including credential theft, account takeover, and unauthorized access. Users should understand and implement comprehensive account security measures regardless of the security measures implemented by the platform.
Phishing and social engineering attacks represent significant threats to cryptocurrency users, with attackers employing increasingly sophisticated techniques to trick users into revealing credentials, approving unauthorized transactions, or taking other actions that compromise account security. User education and awareness represent critical components of defense against these attacks.
Due diligence and ongoing monitoring of platform security, financial health, and regulatory status represent important user responsibilities that can help identify potential risks before they result in asset losses. Users should maintain awareness of platform developments, security incidents, and regulatory changes that could affect asset protection and consider these factors in their ongoing risk assessment.
Financial Health and Operational Transparency
The financial stability and operational transparency of cryptocurrency platforms directly impact user asset security, as financial difficulties or operational problems can affect the platform’s ability to meet user withdrawal requests and maintain security measures. Nexo’s financial health and transparency practices provide important insights into the overall security of deposited assets.
Financial reporting and transparency measures vary significantly among cryptocurrency platforms, with some providing detailed financial information while others maintain limited disclosure that can make it difficult for users to assess platform financial health. The level of financial transparency can affect user ability to make informed decisions about asset deposit and risk management.
Professional financial analysis tools enable users to monitor platform token performance and market sentiment that may reflect concerns about platform financial health or operational issues. However, token performance may not always accurately reflect underlying platform security or financial stability.
Operational metrics including user growth, asset under management, and platform utilization provide insights into business performance and sustainability that can affect long-term security and user asset protection. Users should consider these metrics alongside security measures when evaluating overall platform risk.
Regulatory Developments and Future Outlook
The evolving regulatory landscape for cryptocurrency platforms continues to develop new requirements and standards that will affect platform security measures, user protections, and asset custody practices. Nexo’s response to regulatory developments and proactive compliance efforts provide insights into the platform’s commitment to maintaining appropriate security standards.
Emerging regulations in major markets including the European Union, United States, and other jurisdictions are establishing new requirements for cryptocurrency platform operations, security measures, and user protections that will affect how platforms like Nexo operate and protect user assets. These developments may provide enhanced protections for users while also increasing operational costs and complexity for platforms.
The integration of traditional financial services regulations with cryptocurrency-specific requirements represents a complex regulatory challenge that requires platforms to balance compliance with multiple regulatory frameworks while maintaining operational efficiency and competitive positioning. This regulatory complexity affects both security practices and user protections.
Future security developments including advances in cryptographic techniques, quantum-resistant security measures, and new attack vectors will require ongoing adaptation and investment in security infrastructure. Platform ability to adapt to these developments will affect long-term security and user asset protection capabilities.
Risk Mitigation Strategies for Users
Despite comprehensive platform security measures, users should implement independent risk mitigation strategies that provide additional layers of protection for their cryptocurrency investments and reduce exposure to platform-specific risks. These strategies include diversification, position sizing, and independent security measures that complement platform protections.
Diversification across multiple platforms, asset types, and custody models can reduce exposure to single-platform risks while maintaining access to yield opportunities and other platform benefits. Users should consider their overall cryptocurrency portfolio allocation and avoid concentrating excessive assets on any single platform regardless of security measures.
Position sizing and risk management techniques from traditional investing apply to cryptocurrency platform usage, with users maintaining asset allocations that reflect their risk tolerance and investment objectives rather than maximizing potential returns without considering associated risks. Regular portfolio rebalancing can help maintain appropriate risk levels as market conditions and platform risks evolve.
Independent security measures including hardware wallets, multi-signature setups, and other self-custody solutions provide alternatives to platform custody that can complement centralized platform services while reducing exposure to platform-specific risks. Users should understand the trade-offs between convenience and security when choosing custody solutions.
This article is for informational purposes only and does not constitute financial, investment, or legal advice. Cryptocurrency investments carry significant risks including total loss of capital. Users should conduct their own research and consult with qualified professionals before making investment decisions. Past performance does not guarantee future results, and security measures may not prevent all types of losses or attacks.