Explore advanced oracle attack vectors and mitigation strategies on TradingView
The Critical Role of Price Oracles in DeFi Lending
Price oracles serve as the fundamental backbone of decentralized finance lending platforms, providing real-time asset pricing data that determines collateral values, liquidation thresholds, and borrowing capacity across the ecosystem. These external data feeds bridge the gap between on-chain smart contracts and off-chain market information, enabling lending protocols to make critical decisions about loan-to-value ratios, margin requirements, and liquidation triggers that protect both lenders and borrowers from excessive risk exposure.
The sophisticated nature of modern DeFi lending protocols creates complex dependencies on oracle accuracy and reliability, with protocols often handling billions of dollars in total value locked that relies entirely on precise price feeds for operational security. Oracle manipulation attacks exploit these dependencies by artificially influencing price data fed to lending protocols, creating opportunities for attackers to extract value through over-borrowing, avoiding liquidations, or triggering unfair liquidations of other users’ positions.
The decentralized nature of blockchain systems makes oracle security particularly challenging, as smart contracts cannot directly access external data sources and must rely on trusted intermediaries or consensus mechanisms to obtain accurate pricing information. This fundamental limitation creates attack surfaces that sophisticated adversaries can exploit using various techniques including flash loans, arbitrage manipulation, governance attacks, and coordinated market manipulation across multiple venues.
Oracle manipulation attacks have become increasingly sophisticated as the DeFi ecosystem has matured, with attackers developing complex multi-step strategies that combine flash loans with price manipulation to maximize extraction while minimizing detection and response time. These attacks often target specific vulnerabilities in oracle aggregation algorithms, price update mechanisms, or governance structures that control oracle parameters.
Historical Context and Evolution of Oracle Attacks
The evolution of oracle manipulation attacks mirrors the broader development of the DeFi ecosystem, beginning with simple price feed manipulations in early protocols and evolving into sophisticated multi-vector attacks that exploit complex interactions between different protocol components. Early oracle attacks focused primarily on single-source price feeds that could be manipulated through concentrated trading activity on specific exchanges, leading to the development of more robust aggregation mechanisms.
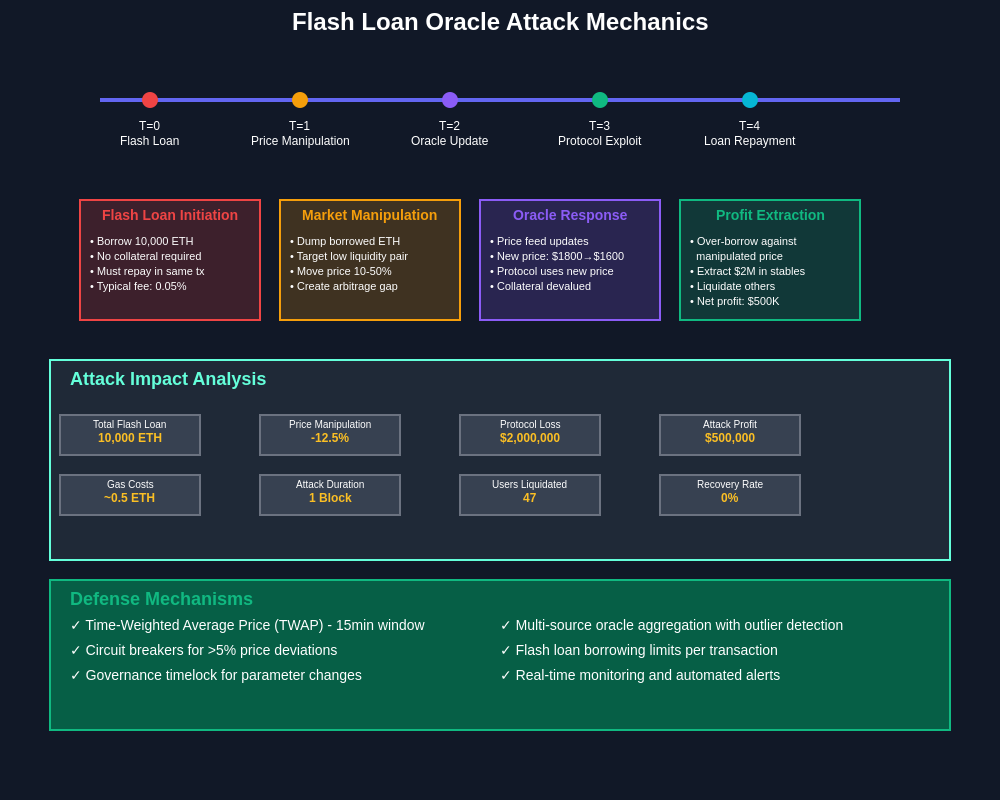
The introduction of flash loans revolutionized oracle manipulation attacks by enabling attackers to borrow large amounts of capital without collateral, execute complex manipulation strategies within a single transaction, and repay the borrowed funds before the transaction completes. This capability dramatically reduced the capital requirements for oracle attacks while increasing their potential profitability and frequency.
Historical analysis of major oracle attacks reveals common patterns including targeting of low-liquidity assets with limited price sources, exploitation of governance vulnerabilities that control oracle parameters, and coordination of attacks during periods of high market volatility when price movements appear more natural. Notable incidents include attacks on bZx, Harvest Finance, and various other lending protocols that resulted in combined losses exceeding hundreds of millions of dollars.
The development of more sophisticated oracle aggregation methods including time-weighted average prices, multi-source feeds, and cryptographic proof systems represents an ongoing arms race between protocol developers and potential attackers. Each new defensive mechanism introduces additional complexity that can create new attack vectors while attempting to close existing vulnerabilities.
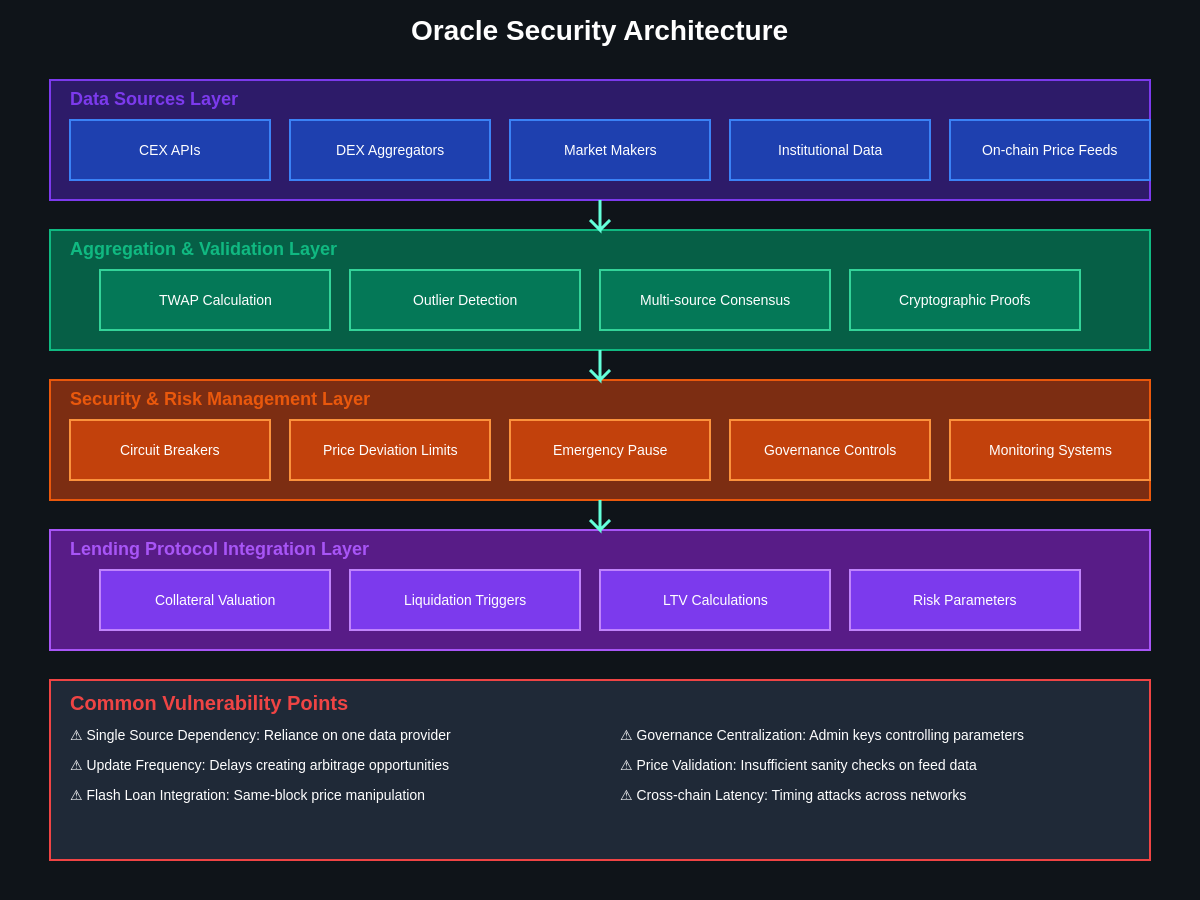
Technical Architecture of Oracle Systems
Oracle systems in DeFi lending protocols typically employ complex architectures designed to balance accuracy, timeliness, and resistance to manipulation through various technical mechanisms. Centralized oracles rely on trusted data providers who aggregate price information from multiple sources and submit updates to on-chain contracts, while decentralized oracles attempt to achieve consensus among multiple independent data providers through various incentive and validation mechanisms.
Price aggregation algorithms represent a critical component of oracle security, with different approaches offering varying levels of protection against manipulation attempts. Simple average calculations can be vulnerable to outlier manipulation, while more sophisticated approaches including median calculations, outlier detection, and weighted averages based on source reliability can provide enhanced resistance to manipulation attempts.
Time-based mechanisms including time-weighted average prices (TWAP) offer protection against short-term price manipulation by averaging prices over extended periods, though these systems can be vulnerable to sustained manipulation campaigns or attacks that exploit the delay between actual price movements and oracle updates. The optimal time window for TWAP calculations requires careful balance between manipulation resistance and responsiveness to legitimate price movements.
Cryptographic proof systems enable oracles to provide verifiable evidence of data accuracy and integrity, though these systems often introduce additional complexity and computational requirements that can affect performance and cost. Zero-knowledge proofs, threshold signatures, and other cryptographic primitives offer various approaches to oracle security with different trade-offs between security, performance, and implementation complexity.
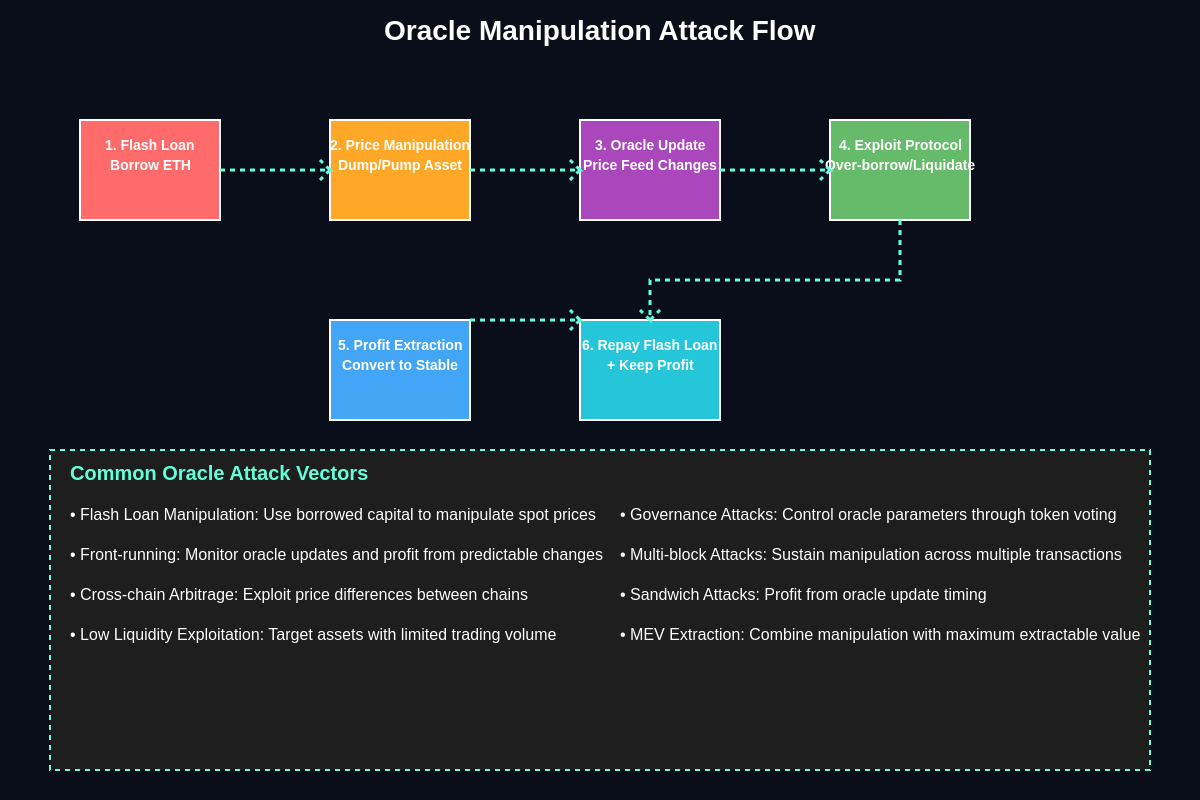
Common Attack Vectors and Methodologies
Flash loan attacks represent the most common and sophisticated form of oracle manipulation, enabling attackers to borrow large amounts of capital, manipulate prices through coordinated trading, exploit the manipulated prices to extract value from lending protocols, and repay the borrowed funds within a single atomic transaction. These attacks are particularly effective because they require no initial capital investment while potentially generating substantial profits.
Price manipulation through concentrated trading involves attackers accumulating large positions in target assets and executing coordinated buy or sell orders designed to move prices in specific directions that benefit their positions in lending protocols. This technique is most effective against assets with limited liquidity or exchanges with shallow order books that can be moved with relatively modest capital investments.
Governance attacks target the decentralized governance mechanisms that control oracle parameters including price sources, update frequencies, aggregation methods, and security thresholds. Attackers can accumulate governance tokens through various means and propose changes that weaken oracle security or create opportunities for future manipulation attacks.
Multi-vector attacks combine multiple manipulation techniques simultaneously to overwhelm oracle security systems and maximize extraction potential. These sophisticated campaigns might involve coordinated price manipulation across multiple exchanges, governance attacks to weaken security parameters, and flash loan execution to capitalize on the created vulnerabilities within compressed timeframes.
Sandwich attacks involve attackers monitoring pending oracle updates and placing transactions immediately before and after the updates to profit from predictable price movements. These attacks exploit the public nature of blockchain transactions and the predictable timing of oracle updates to generate profits at the expense of other protocol users.
Economic Impact and Market Consequences
Oracle manipulation attacks have resulted in hundreds of millions of dollars in direct losses across the DeFi ecosystem, with indirect effects including reduced user confidence, increased insurance costs, and elevated operational expenses for protocol developers implementing enhanced security measures. The economic impact extends beyond immediate financial losses to include broader market effects that can persist long after individual attacks are resolved.
Insurance markets for DeFi protocols have been significantly affected by oracle manipulation risks, with many insurers either refusing coverage for oracle-related losses or charging prohibitively expensive premiums that make insurance economically unfeasible for many protocols. This insurance crisis creates additional risk for users and protocols while concentrating risk among a smaller number of participants willing to accept uninsured exposure.
The concentration of oracle attacks in specific market segments has created distortions in capital allocation and risk pricing across the DeFi ecosystem, with some assets and protocols becoming effectively uninvestable due to oracle manipulation risks while others command premium valuations based on superior oracle security. These market effects can persist long after technical vulnerabilities are addressed.
Competitive dynamics within the DeFi lending space have been significantly influenced by oracle security considerations, with protocols investing heavily in oracle infrastructure and security while users increasingly prioritize oracle robustness when selecting platforms. This competition has driven innovation in oracle technology while creating barriers to entry for new protocols that lack resources to implement sophisticated oracle security measures.
Specific Case Studies and Attack Analysis
The bZx attacks of February 2020 represent landmark cases in oracle manipulation history, demonstrating how flash loans could be combined with price manipulation to extract value from lending protocols. The first attack involved borrowing ETH through a flash loan, using a portion to manipulate the price of WBTC on Kyber Network, and exploiting the manipulated price to generate profits from bZx lending positions before repaying the flash loan.
The Harvest Finance attack of October 2020 showcased more sophisticated techniques involving curve pool manipulation and cross-protocol arbitrage to extract approximately $24 million from the platform. The attacker used flash loans to manipulate the price ratios in Curve pools, exploited these price discrepancies through Harvest’s yield farming strategies, and extracted value through a series of complex transactions that took advantage of temporary price imbalances.
The Compound liquidation attack involved manipulation of oracle prices to trigger unfair liquidations of user positions, demonstrating how oracle attacks can affect innocent users beyond direct protocol exploitation. The attacker manipulated the price of DAI through concentrated trading activity, caused legitimate user positions to appear undercollateralized based on the manipulated prices, and profited from the liquidation penalties imposed on affected users.
More recent attacks have demonstrated increasing sophistication including multi-block manipulation campaigns that sustain price distortions over extended periods, cross-chain attacks that exploit price discrepancies between different blockchain networks, and attacks that target specific oracle vulnerabilities in complex multi-asset lending pools with intricate price relationships.
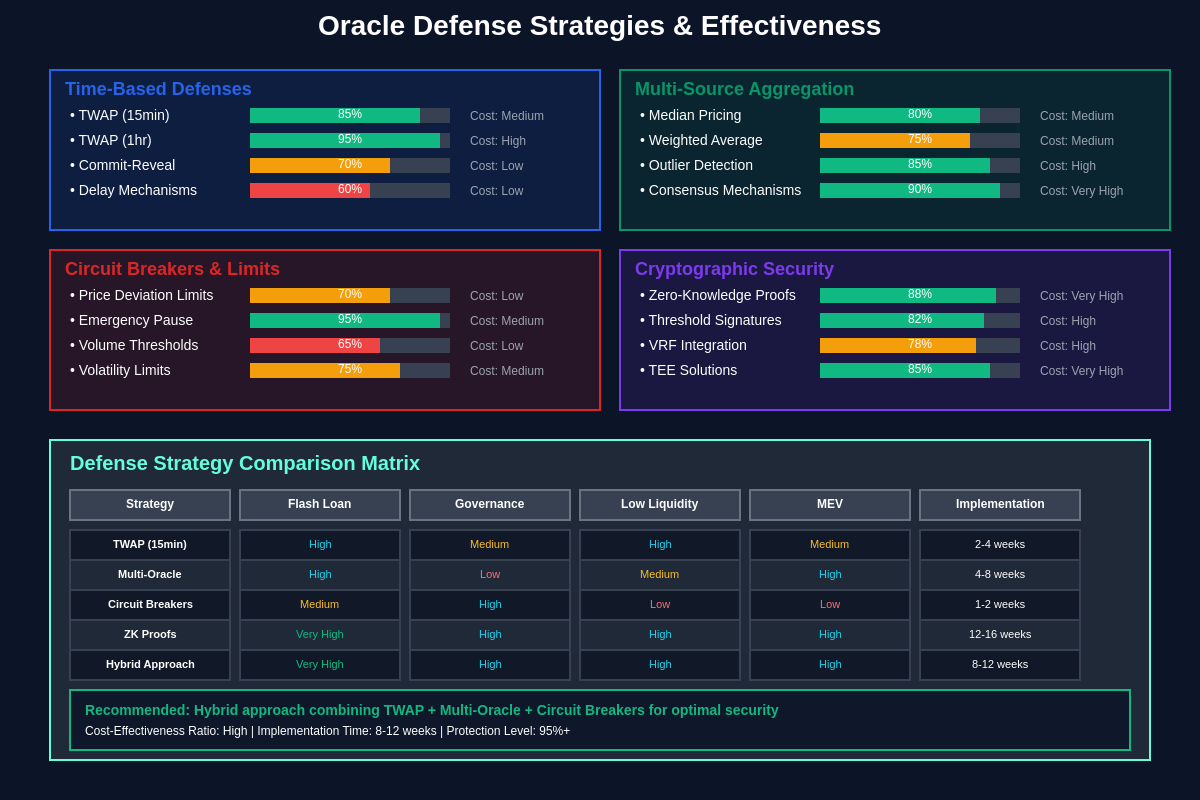
Defense Mechanisms and Security Measures
Time-weighted average price (TWAP) systems represent one of the most effective defenses against short-term oracle manipulation, though they require careful calibration to balance manipulation resistance with responsiveness to legitimate price movements. TWAP implementations typically average prices over periods ranging from minutes to hours, depending on the specific use case and risk tolerance of the protocol.
Multi-source oracle aggregation provides enhanced security by requiring consensus among multiple independent data providers before accepting price updates, though this approach can introduce complexity and potential points of failure if not implemented carefully. Advanced aggregation mechanisms include outlier detection, source reliability weighting, and Byzantine fault tolerance to maintain accuracy even when some data sources are compromised or manipulated.
Circuit breakers and price deviation limits can prevent oracle manipulation attacks by automatically halting protocol operations when prices move beyond predetermined thresholds that indicate potential manipulation. These systems must be carefully calibrated to avoid false positives during legitimate market volatility while providing effective protection against artificial price movements.
Cryptographic commitment schemes enable oracles to commit to price data before revealing it, preventing front-running and manipulation attempts that rely on observing pending oracle updates. These systems can include features such as commit-reveal schemes, verifiable delay functions, and threshold cryptography to enhance security while maintaining operational efficiency.
Governance security measures including time delays for parameter changes, multi-signature requirements for sensitive updates, and community oversight mechanisms help protect against governance attacks that attempt to weaken oracle security. These measures must balance security with the need for responsive governance that can address emerging threats and adapt to changing market conditions.
Regulatory Perspectives and Compliance Challenges
Regulatory approaches to oracle manipulation vary significantly across jurisdictions, with some treating these attacks as market manipulation similar to traditional financial crimes while others struggle to apply existing frameworks to novel DeFi attack vectors. The global and decentralized nature of DeFi protocols creates additional challenges for regulators attempting to establish jurisdiction and enforce compliance requirements.
Anti-manipulation regulations in traditional finance provide some guidance for addressing oracle attacks, though the technical sophistication and decentralized nature of these attacks require new approaches that account for the unique characteristics of blockchain-based systems. Regulators are increasingly focusing on the responsibilities of oracle providers and protocol developers to implement adequate security measures.
Compliance requirements for oracle providers are evolving rapidly as regulators develop new frameworks specifically designed for cryptocurrency and DeFi applications. These requirements often include obligations for data accuracy, security measures, incident reporting, and user protection that can significantly affect the design and operation of oracle systems.
International coordination efforts aim to develop consistent approaches to oracle security and manipulation prevention across different jurisdictions, though the technical complexity and rapid evolution of DeFi technology create ongoing challenges for regulatory development. Industry self-regulation initiatives complement formal regulatory efforts by establishing best practices and standards for oracle security.
Technical Implementation and Code Security
Smart contract security considerations for oracle integration include proper validation of oracle data, implementation of circuit breakers and emergency stops, and careful handling of price data edge cases that could be exploited by attackers. Code auditing processes specifically focused on oracle integration have become standard practice for serious DeFi protocols.
Oracle data validation mechanisms must account for various attack scenarios including price manipulation, data source compromise, and network-level attacks that could affect oracle operations. Robust validation includes sanity checks, historical comparison, and cross-reference with multiple independent sources to ensure data accuracy and detect potential manipulation attempts.
Emergency response procedures for oracle attacks require careful planning and implementation to enable rapid response to detected manipulation attempts while minimizing disruption to legitimate protocol operations. These procedures often include automated circuit breakers, manual intervention capabilities, and communication protocols to coordinate response efforts across multiple stakeholders.
Gas optimization considerations for oracle systems become critical in high-frequency update scenarios where gas costs can significantly affect the economic viability of oracle operations. Advanced optimization techniques include batched updates, state caching, and efficient data structures that minimize on-chain storage and computation requirements while maintaining security and accuracy.
Emerging Technologies and Future Directions
Layer 2 scaling solutions offer new opportunities for oracle security by enabling higher-frequency updates and more sophisticated aggregation mechanisms that may be economically unfeasible on base layer blockchains. These solutions can provide enhanced security through increased data availability while reducing the cost barriers that limit oracle update frequency and sophistication.
Cross-chain oracle protocols are developing new approaches to maintaining consistent price feeds across multiple blockchain networks while preventing arbitrage-based manipulation that exploits price discrepancies between different chains. These systems must address the unique challenges of cross-chain communication including varying block times, finality requirements, and consensus mechanisms.
Machine learning applications in oracle security include anomaly detection systems that can identify potential manipulation attempts in real-time, predictive models that anticipate attack patterns, and automated response systems that can adapt to new attack vectors without manual intervention. These technologies offer promising approaches to staying ahead of evolving attack methodologies.
Zero-knowledge proof systems enable new approaches to oracle security including privacy-preserving price feeds, verifiable computation of complex aggregation algorithms, and cryptographic proof of data integrity that can enhance user confidence while maintaining operational efficiency. The development of more efficient zero-knowledge proof systems continues to expand the practical applications of these technologies in oracle security.
Integration with Traditional Financial Systems
Bridge protocols connecting DeFi oracle systems with traditional financial data sources face unique challenges in maintaining security and compliance across different regulatory environments while providing the data accuracy and timeliness required for sophisticated lending operations. These integrations must address the different operational characteristics and security models of traditional and decentralized financial systems.
Institutional adoption of DeFi lending protocols requires enhanced oracle security standards that meet the risk management requirements of professional financial institutions while maintaining the decentralized characteristics that provide the fundamental value propositions of DeFi systems. These requirements often include enhanced audit trails, regulatory compliance features, and institutional-grade security measures.
Hybrid oracle models combine centralized and decentralized components to provide enhanced security and compliance capabilities while maintaining resistance to single points of failure. These systems can leverage the reliability and regulatory compliance of traditional data providers while incorporating the manipulation resistance and transparency of decentralized oracle networks.
Risk Management and Insurance Solutions
Parametric insurance products specifically designed for oracle manipulation losses provide automated claims processing based on objective on-chain criteria rather than traditional loss adjustment processes. These products can provide rapid compensation for verified oracle manipulation events while reducing the administrative costs and delays associated with traditional insurance claims.
Risk modeling for oracle manipulation requires sophisticated understanding of attack vectors, market dynamics, and protocol mechanics to accurately price insurance products and assess exposure limits. Advanced risk models incorporate factors including asset liquidity, oracle architecture, governance security, and historical attack patterns to provide comprehensive risk assessment.
Portfolio diversification strategies for DeFi lending include exposure limits across different oracle providers, asset categories, and protocol architectures to reduce concentration risk from oracle manipulation attacks. These strategies must balance diversification benefits with the operational complexity and potential reduction in yields associated with spreading exposure across multiple platforms.
Professional risk management services for DeFi protocols include oracle security auditing, continuous monitoring, incident response planning, and recovery assistance that can help protocols maintain security while managing the operational burden of comprehensive risk management programs.
Market Impact and Systemic Risk Considerations
Systemic risk assessment for oracle manipulation includes analysis of potential cascade effects where attacks on major oracle providers or widely-used protocols could affect multiple dependent systems simultaneously. The interconnected nature of DeFi protocols creates complex risk relationships that can amplify the impact of individual oracle attacks across the broader ecosystem.
Liquidity impact analysis examines how oracle manipulation attacks affect market liquidity and price discovery mechanisms both during and after attack events. These effects can include temporary price dislocations, reduced trading activity, and long-term changes in market structure that affect the efficiency of price discovery mechanisms.
Confidence and adoption effects from oracle manipulation attacks can persist long after technical vulnerabilities are addressed, affecting user behavior, institutional adoption, and overall market development in ways that extend far beyond the immediate financial impact of individual attacks. Understanding and addressing these broader market effects requires coordination across multiple stakeholders in the DeFi ecosystem.
Monetary policy implications of oracle manipulation include potential effects on stablecoin mechanisms, algorithmic trading systems, and other protocol mechanisms that rely on accurate price feeds for their economic functions. Central bank digital currency implementations must also consider oracle security as they develop systems that may interact with DeFi protocols.
Best Practices and Recommendations
Protocol development best practices for oracle security include comprehensive security auditing, multi-source price aggregation, implementation of circuit breakers and emergency controls, and regular testing of security mechanisms under various attack scenarios. These practices should be integrated into development processes from the earliest stages of protocol design.
User protection measures include education about oracle manipulation risks, transparent disclosure of oracle architectures and security measures, and implementation of user-friendly tools that enable individuals to assess and manage their exposure to oracle manipulation risks. Clear communication about risk factors helps users make informed decisions about their participation in DeFi lending.
Industry collaboration initiatives including shared security research, coordinated response to emerging threats, and development of common standards for oracle security can help raise the overall security level of the DeFi ecosystem while reducing the burden on individual protocols to develop comprehensive security measures independently.
Continuous monitoring and improvement processes ensure that oracle security measures evolve in response to new attack vectors and changing market conditions. These processes should include regular security assessments, community feedback mechanisms, and systematic analysis of attack patterns to identify areas for improvement.
Monitor real-time DeFi lending rates and oracle price feeds
Conclusion and Future Outlook
Oracle manipulation attacks represent one of the most significant ongoing security challenges in the DeFi ecosystem, requiring continuous innovation and vigilance from protocol developers, security researchers, and users to maintain the integrity of decentralized lending systems. The evolution of attack methodologies demands corresponding evolution in defense mechanisms, creating an ongoing arms race that drives innovation while creating ongoing security challenges.
The development of more robust oracle systems through improved aggregation mechanisms, enhanced cryptographic security, and better integration with traditional financial systems offers promise for reducing oracle manipulation risks while maintaining the core benefits of decentralized finance. However, the fundamental challenge of providing accurate external data to blockchain systems ensures that oracle security will remain a critical area of focus for the foreseeable future.
Future developments in oracle technology including advanced cryptographic approaches, artificial intelligence integration, and cross-chain coordination mechanisms offer potential solutions to current vulnerabilities while potentially introducing new attack vectors that require ongoing research and development efforts. The success of DeFi lending platforms will continue to depend heavily on the security and reliability of their oracle infrastructure.
The broader adoption of DeFi lending protocols by institutional users and integration with traditional financial systems will likely drive additional requirements for oracle security and compliance that could accelerate the development of more robust oracle technologies while creating new challenges for maintaining the decentralized characteristics that provide fundamental value in these systems.
Disclaimer: This article is for educational and informational purposes only and does not constitute financial, investment, or legal advice. Cryptocurrency and DeFi investments carry significant risks including potential loss of principal. Oracle manipulation attacks represent serious security threats that can result in substantial financial losses. Readers should conduct their own research and consult with qualified professionals before making investment decisions. The information presented may not reflect the most current market conditions or regulatory developments. Past performance does not guarantee future results. All examples and case studies are provided for illustrative purposes only and should not be considered as recommendations or endorsements.