The advent of quantum computing represents one of the most significant technological developments in human history, with the potential to revolutionize countless industries while simultaneously posing unprecedented challenges to existing security infrastructure. For the cryptocurrency ecosystem, quantum computing presents a dual-edged sword that could fundamentally reshape the landscape of digital asset security, potentially rendering current cryptographic protections obsolete while opening new frontiers for quantum-resistant blockchain technologies. TradingView’s comprehensive charts help traders visualize these emerging technological trends and their potential market impacts.
The Current State of Cryptocurrency Cryptography
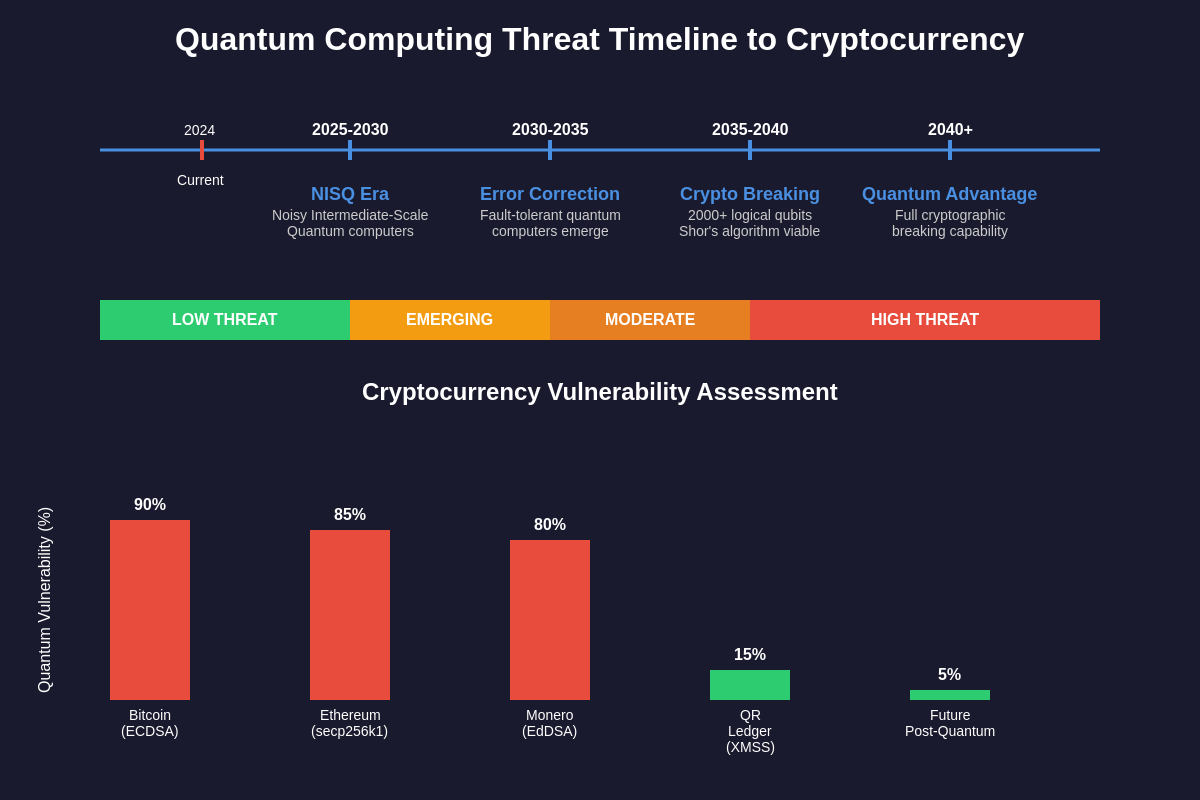
Modern cryptocurrency systems rely fundamentally on asymmetric cryptography, specifically elliptic curve cryptography and hash functions, to secure transactions, protect private keys, and maintain the integrity of blockchain networks. Bitcoin’s ECDSA signatures, Ethereum’s secp256k1 curve implementations, and the SHA-256 hashing algorithm that secures most proof-of-work networks represent the cryptographic backbone upon which the entire $2 trillion cryptocurrency market is built. These cryptographic systems derive their security from the computational intractability of certain mathematical problems, including the discrete logarithm problem and integer factorization, which would require classical computers millions of years to solve using current algorithms.
The security assumptions underlying these cryptographic systems were developed in an era when quantum computing remained largely theoretical, with early researchers like Peter Shor and Lov Grover developing quantum algorithms that demonstrated the potential for quantum computers to solve these supposedly intractable problems in polynomial time. Shor’s algorithm, first proposed in 1994, provides an exponential speedup for factoring large integers and computing discrete logarithms, directly threatening the security of RSA and elliptic curve cryptography. Grover’s algorithm offers a quadratic speedup for searching unsorted databases, effectively halving the security level of symmetric cryptographic systems and hash functions.
The implications of these quantum algorithms for cryptocurrency security cannot be overstated, as they represent a fundamental challenge to the mathematical foundations upon which digital asset security is built. Current estimates suggest that a quantum computer with approximately 2,000 to 4,000 logical qubits could break Bitcoin’s elliptic curve cryptography, potentially allowing an attacker to derive private keys from public keys and effectively steal any Bitcoin whose public key has been revealed through transactions.
Hash function security, while more resilient to quantum attacks than asymmetric cryptography, still faces significant degradation under quantum assault. Grover’s algorithm effectively halves the security level of hash functions, meaning that SHA-256’s 256-bit security would be reduced to approximately 128 bits against a quantum attacker. While this reduction does not immediately break hash-based systems, it represents a substantial weakening of security margins that could become problematic as quantum computing technology advances.
The timeline for quantum computers achieving the capability to break current cryptocurrency cryptography remains a subject of intense debate among researchers, with estimates ranging from 10 to 30 years depending on the rate of technological advancement and breakthrough discoveries in quantum error correction and fault-tolerant quantum computing. However, the mere possibility of this quantum threat has already begun driving significant research and development efforts into quantum-resistant cryptographic systems.
Quantum Computing Fundamentals and Cryptographic Implications
Quantum computing operates on fundamentally different principles than classical computation, leveraging quantum mechanical phenomena such as superposition, entanglement, and interference to perform calculations that would be impossible or impractical for classical computers. Where classical bits exist in definite states of 0 or 1, quantum bits or qubits can exist in superposition states that represent probabilistic combinations of both values simultaneously. This quantum parallelism allows quantum computers to explore multiple solution paths simultaneously, providing exponential speedups for certain classes of problems.
The power of quantum computing for cryptographic applications emerges from its ability to efficiently solve mathematical problems that form the basis of modern cryptographic security. The discrete logarithm problem, which underlies the security of elliptic curve cryptography used in Bitcoin and most other cryptocurrencies, becomes polynomially solvable using Shor’s algorithm on a sufficiently large quantum computer. This represents a fundamental shift from exponential to polynomial complexity, transforming what were previously intractable problems into efficiently solvable ones.
Current quantum computers, while demonstrating quantum supremacy in specific computational tasks, remain far from the scale and stability required to threaten cryptocurrency cryptography. The quantum computers developed by companies like IBM, Google, and IonQ typically contain dozens to hundreds of physical qubits, but suffer from high error rates and limited coherence times that prevent them from running the complex algorithms required for cryptographic attacks. The development of fault-tolerant quantum computers with thousands of logical qubits represents a significant engineering challenge that may require years or decades to overcome.
The concept of logical qubits versus physical qubits represents a crucial distinction in understanding the quantum threat timeline. While physical qubits are the actual quantum systems that perform computations, logical qubits are error-corrected quantum states that can maintain quantum information for extended periods despite the inherent fragility of quantum systems. Current estimates suggest that hundreds or thousands of physical qubits may be required to create a single logical qubit capable of reliable computation, significantly increasing the hardware requirements for cryptographically relevant quantum computers.
Quantum error correction represents perhaps the greatest challenge in developing cryptographically relevant quantum computers, as quantum systems are extremely sensitive to environmental interference that can destroy quantum states and introduce computational errors. The development of efficient quantum error correction codes and fault-tolerant quantum computing architectures represents an active area of research that will ultimately determine the timeline for quantum computers capable of threatening cryptocurrency security.
The implications of quantum computing extend beyond mere computational speedups to include entirely new computational paradigms that could enable novel approaches to cryptographic analysis and blockchain security. Quantum machine learning algorithms could potentially identify patterns in blockchain transactions that are invisible to classical analysis, while quantum optimization algorithms could enable more efficient mining algorithms or consensus mechanisms that fundamentally alter the economics of cryptocurrency networks.
Timeline and Technical Requirements for Cryptographically Relevant Quantum Computers
The development timeline for quantum computers capable of breaking cryptocurrency cryptography depends on numerous technical factors, including advances in quantum hardware, error correction, and algorithmic efficiency. Current expert estimates suggest that cryptographically relevant quantum computers may emerge within 10 to 30 years, though significant uncertainty surrounds these predictions due to the numerous technical challenges that must be overcome.
The hardware requirements for breaking Bitcoin’s elliptic curve cryptography using Shor’s algorithm have been estimated by various research groups, with most studies suggesting that between 2,000 and 4,000 logical qubits would be sufficient to derive private keys from public keys within reasonable timeframes. However, these logical qubits must be implemented using potentially millions of physical qubits due to the overhead requirements of quantum error correction, representing a massive engineering challenge that current quantum computing technology cannot yet meet.
Recent advances in quantum computing hardware have demonstrated significant progress toward these goals, with companies like IBM planning quantum computers with over 100,000 qubits by 2033 and Google achieving quantum supremacy in specific computational tasks. However, the path from current noisy intermediate-scale quantum computers to fault-tolerant systems capable of running Shor’s algorithm remains uncertain and depends on breakthrough developments in quantum error correction and qubit coherence.
The concept of quantum advantage versus quantum supremacy represents an important distinction in understanding the quantum threat timeline. While quantum supremacy refers to quantum computers performing any computational task faster than classical computers, quantum advantage specifically relates to quantum computers providing practical benefits for real-world applications. For cryptocurrency security, quantum advantage would mean quantum computers that can break cryptographic systems faster and more efficiently than classical attacks.
Alternative approaches to quantum computing, including photonic quantum computers, trapped ion systems, and topological quantum computers, offer different trade-offs in terms of scalability, error rates, and operational requirements. These diverse technological approaches may result in different timelines for cryptographically relevant quantum computers, with some approaches potentially achieving breakthrough capabilities sooner than others.
The development of quantum software and algorithms represents another crucial factor in the quantum threat timeline, as efficient implementations of Shor’s algorithm and other quantum cryptographic attacks require sophisticated software stacks and algorithmic optimizations. Current research into quantum software development, including quantum compilers and optimization techniques, will ultimately determine how efficiently future quantum computers can execute cryptographic attacks.
Government and military investment in quantum computing research has accelerated significantly in recent years, with major nations including the United States, China, and European Union committing billions of dollars to quantum research programs. These investments could potentially accelerate the development timeline for cryptographically relevant quantum computers, particularly if breakthrough discoveries emerge from well-funded research programs.
Specific Vulnerabilities in Major Cryptocurrency Protocols
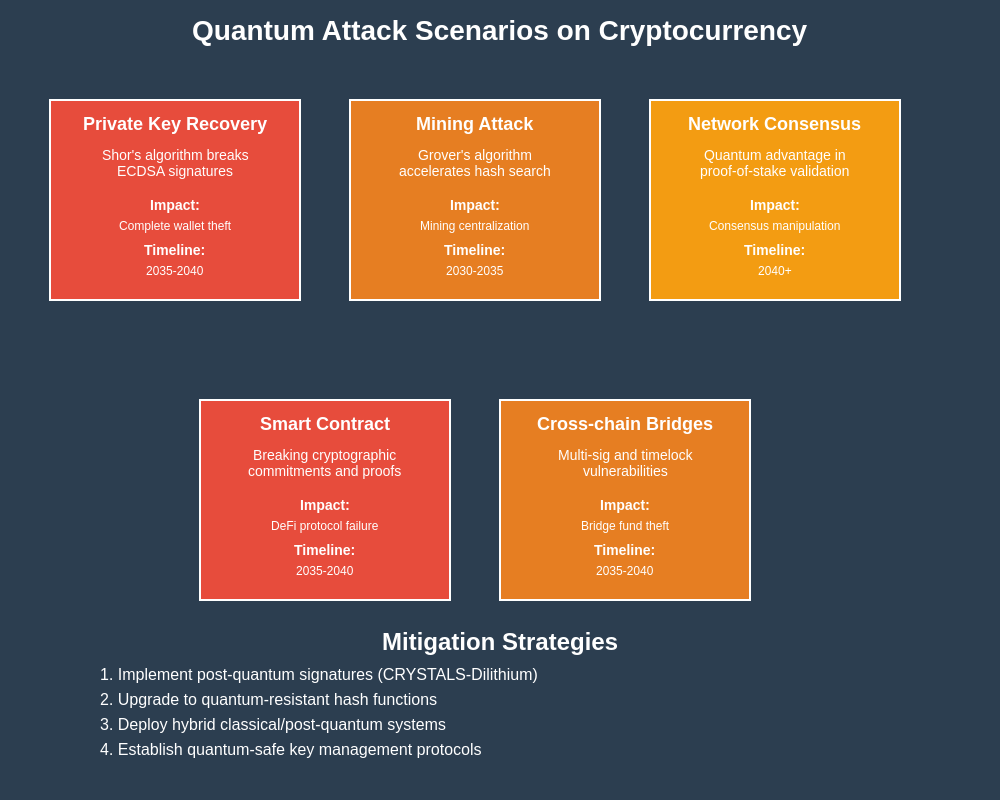
Bitcoin’s security model faces several specific vulnerabilities to quantum computing attacks, primarily centered around the elliptic curve digital signature algorithm used to secure transactions and the SHA-256 hash function used in proof-of-work mining. The secp256k1 elliptic curve used in Bitcoin signatures becomes vulnerable to Shor’s algorithm, potentially allowing quantum attackers to derive private keys from any public key revealed through Bitcoin transactions. This vulnerability affects not only active Bitcoin addresses but also addresses that have sent transactions in the past, as their public keys become known through the transaction history stored on the blockchain.
The Bitcoin protocol’s use of public key hashes in addresses provides some protection against quantum attacks, as attackers would need to break both the elliptic curve cryptography and the hash functions to derive private keys from unused addresses. However, this protection disappears once addresses are used to send transactions, as the public keys become visible on the blockchain and vulnerable to quantum attacks. Historical Bitcoin price data on TradingView shows how security concerns have historically affected market valuation.
Ethereum faces similar elliptic curve vulnerabilities but also confronts additional quantum threats through its smart contract functionality and more complex cryptographic operations. The Ethereum Virtual Machine’s support for various cryptographic operations, including different elliptic curves and hash functions, creates a broader attack surface for quantum adversaries. Additionally, Ethereum’s transition to proof-of-stake introduces new cryptographic components, including BLS signatures and various cryptographic commitments used in the consensus mechanism, each of which may have different levels of quantum resistance.
The upcoming Ethereum 2.0 protocol incorporates several cryptographic primitives that may be vulnerable to quantum attacks, including the BLS signature scheme used for validator consensus and various polynomial commitment schemes used in sharding protocols. While some of these cryptographic systems may offer better quantum resistance than traditional elliptic curve cryptography, they have not been specifically designed to withstand quantum attacks and may require replacement as quantum computing technology advances.
Alternative cryptocurrency protocols face varying levels of quantum vulnerability depending on their specific cryptographic implementations. Privacy-focused cryptocurrencies like Monero and Zcash rely heavily on advanced cryptographic techniques including ring signatures, zero-knowledge proofs, and various commitment schemes that may be particularly vulnerable to quantum attacks. The complex cryptographic constructions used in these privacy protocols often combine multiple cryptographic assumptions, potentially creating additional attack vectors for quantum adversaries.
Proof-of-stake networks generally face different quantum threat profiles compared to proof-of-work systems, as they rely more heavily on digital signatures for consensus and less on hash function security. However, the complex cryptographic protocols used in modern proof-of-stake systems, including various forms of cryptographic sortition and verifiable random functions, may introduce new quantum vulnerabilities that are not present in simpler proof-of-work protocols.
Layer-2 scaling solutions and cross-chain protocols introduce additional quantum vulnerabilities through their use of complex cryptographic constructions including hash time-locked contracts, multi-signature schemes, and various forms of cryptographic commitments. These systems often rely on the security of multiple underlying cryptographic primitives, potentially creating cascading failures if quantum computers compromise any component of the security model.
Quantum-Resistant Cryptographic Solutions
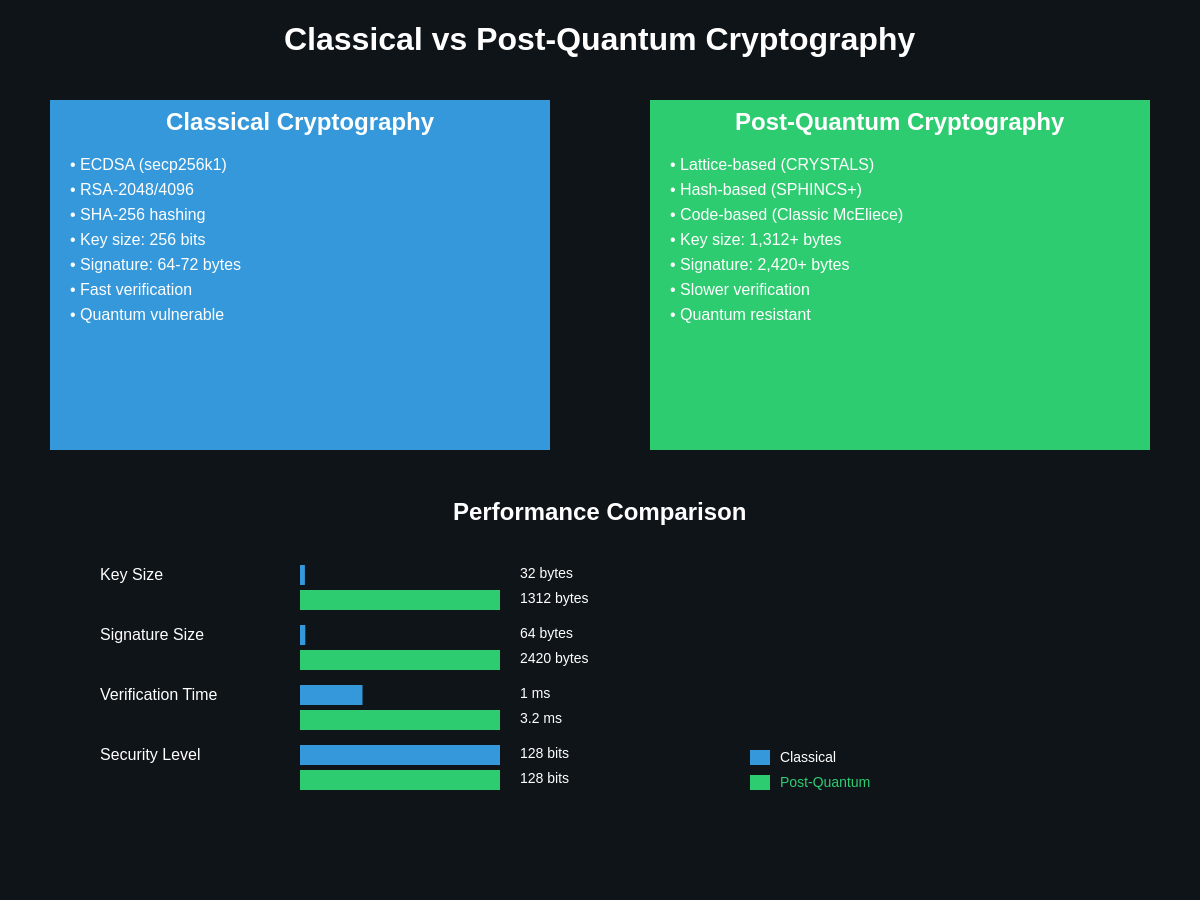
The development of quantum-resistant or post-quantum cryptographic systems represents the primary defense against the quantum threat to cryptocurrency security. These cryptographic systems are designed to remain secure even against attackers with access to large-scale quantum computers, typically by relying on mathematical problems that are believed to be intractable even for quantum computers. The National Institute of Standards and Technology has been conducting a multi-year process to standardize post-quantum cryptographic algorithms, recently selecting several candidates for standardization including lattice-based, code-based, and hash-based cryptographic systems.
Lattice-based cryptography represents one of the most promising approaches to quantum-resistant cryptography, offering efficient implementations and strong security guarantees based on problems like the Learning With Errors problem and the Shortest Vector Problem. These mathematical problems are believed to be intractable for both classical and quantum computers, providing a foundation for quantum-resistant digital signatures, encryption, and key exchange protocols. Several lattice-based cryptographic schemes have been proposed for integration into cryptocurrency systems, though they typically require larger key sizes and signature sizes compared to current elliptic curve systems.
Hash-based signature schemes offer another approach to quantum-resistant cryptography, deriving their security from the one-way property of cryptographic hash functions. While Grover’s algorithm provides a quadratic speedup for attacking hash functions, this reduction in security can be compensated by using larger hash functions or more complex hash-based constructions. Hash-based signatures like XMSS and SPHINCS+ provide strong quantum resistance but suffer from limitations including large signature sizes and restrictions on the number of signatures that can be generated from a single key pair.
Code-based cryptography relies on the difficulty of decoding random linear codes, a problem that appears to be resistant to both classical and quantum attacks. However, code-based cryptographic systems typically require very large key sizes, making them less practical for cryptocurrency applications where storage and bandwidth efficiency are important considerations. Recent research into more efficient code-based systems may eventually make this approach more viable for cryptocurrency implementations.
Multivariate cryptography and isogeny-based cryptography represent additional approaches to quantum-resistant cryptography, though both have faced significant challenges in recent years. Multivariate systems have suffered from various cryptographic attacks that have broken many proposed schemes, while isogeny-based cryptography faced a major setback when recent research broke the SIKE cryptosystem that was previously considered a leading candidate for post-quantum standardization.
The integration of post-quantum cryptographic systems into existing cryptocurrency protocols presents significant challenges including backward compatibility, performance considerations, and the need for careful security analysis. The larger key and signature sizes typical of post-quantum systems could significantly impact blockchain storage requirements and transaction throughput, potentially requiring fundamental changes to cryptocurrency protocol design.
Hybrid cryptographic approaches that combine current elliptic curve cryptography with post-quantum systems offer a potential migration path that maintains security against both classical and quantum attackers during the transition period. These hybrid systems provide security against quantum attacks while maintaining the efficiency and compatibility of current cryptographic systems, though they require careful design to avoid introducing new vulnerabilities.
Economic and Market Implications
The potential impact of quantum computing on cryptocurrency markets represents one of the most significant long-term risks facing the digital asset ecosystem, with implications that extend far beyond technical security considerations to encompass fundamental questions about the value proposition and viability of current cryptocurrency systems. Market participants have begun incorporating quantum risk into their investment strategies and valuation models, though the uncertainty surrounding quantum computing timelines makes precise risk assessment extremely challenging.
The immediate market impact of demonstrated quantum capabilities sufficient to break cryptocurrency cryptography would likely be catastrophic, potentially causing massive sell-offs as investors flee from quantum-vulnerable assets toward perceived safety in traditional financial systems or quantum-resistant alternatives. Historical market responses to security threats in the cryptocurrency space suggest that even the perception of quantum vulnerability could trigger significant market volatility long before actual quantum attacks become feasible.
Insurance markets for cryptocurrency assets and exchanges are beginning to incorporate quantum risk into their underwriting models, with some insurers already excluding quantum attacks from coverage or requiring additional premiums for quantum-related risks. The development of quantum risk assessment methodologies and actuarial models represents a growing area of focus for the cryptocurrency insurance industry, though the uncertainty surrounding quantum timelines makes accurate risk pricing extremely difficult.
The competitive dynamics within the cryptocurrency ecosystem could shift dramatically as quantum computing capabilities advance, with quantum-resistant protocols potentially gaining significant market advantages over quantum-vulnerable alternatives. Early movers in implementing robust post-quantum cryptographic systems may capture market share from protocols that fail to adequately address quantum threats, creating powerful incentives for proactive quantum resistance development.
Institutional adoption of cryptocurrency assets could be significantly impacted by quantum concerns, as large financial institutions and corporate treasuries typically require high levels of security assurance before committing significant capital to digital assets. The perception of quantum vulnerability could slow institutional adoption even if practical quantum attacks remain years in the future, highlighting the importance of addressing quantum concerns proactively rather than reactively.
Regulatory responses to quantum threats in cryptocurrency markets remain largely undeveloped, though some regulators have begun considering the implications of quantum computing for financial system stability. Future regulatory frameworks may require cryptocurrency protocols to demonstrate quantum resistance or implement specific quantum risk management measures, potentially creating compliance costs and barriers to entry for new cryptocurrency projects.
The development costs associated with implementing quantum-resistant cryptographic systems represent a significant economic consideration for cryptocurrency projects, as post-quantum systems typically require more computational resources, larger storage requirements, and more complex implementations than current cryptographic systems. These increased costs must be weighed against the potential risks of quantum attacks and the competitive advantages of quantum resistance.
Market analysis tools on TradingView help investors track how quantum computing developments might affect cryptocurrency valuations and trading patterns across different protocols and market segments.
Industry Response and Mitigation Strategies
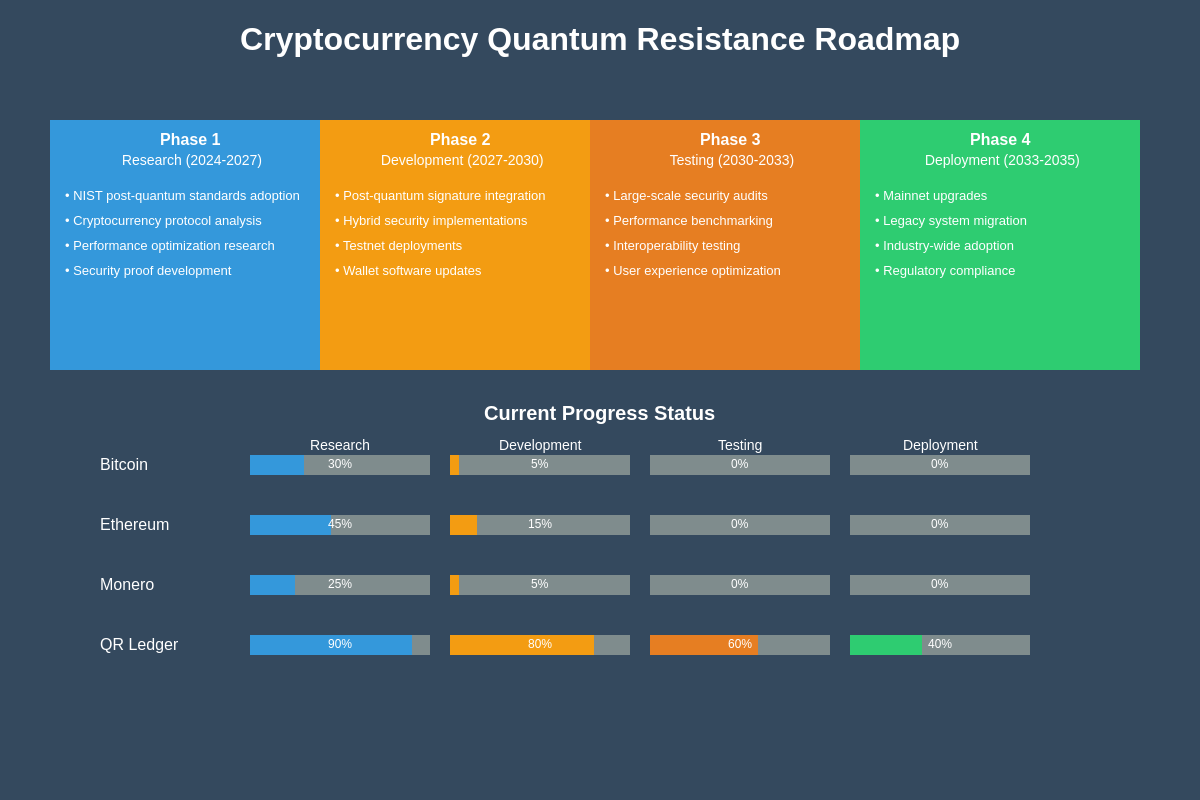
The cryptocurrency industry has begun responding to the quantum threat through various research initiatives, protocol development projects, and collaborative efforts aimed at developing quantum-resistant alternatives to current cryptographic systems. Major cryptocurrency projects including Bitcoin, Ethereum, and others have established research groups or funded external research into post-quantum cryptographic solutions, though the timeline and specific approaches for implementation remain largely undetermined.
The Bitcoin development community has engaged in ongoing discussions about quantum resistance, with various Bitcoin Improvement Proposals addressing different aspects of post-quantum security. However, the conservative nature of Bitcoin development and the challenges associated with implementing backward-incompatible changes to the protocol mean that quantum resistance upgrades will likely require extensive planning and community consensus-building processes that could take years to complete.
Ethereum’s roadmap includes considerations for quantum resistance, particularly in the context of the ongoing protocol upgrades and the transition to proof-of-stake consensus. The Ethereum Foundation has funded research into post-quantum cryptographic systems and their potential integration into the Ethereum protocol, though specific implementation timelines remain uncertain. The more flexible nature of Ethereum’s development process may enable faster quantum resistance implementation compared to Bitcoin, though the complexity of the Ethereum ecosystem also creates additional challenges.
Several new cryptocurrency projects have been designed from the ground up with quantum resistance as a primary consideration, incorporating post-quantum cryptographic systems into their core protocol design. Projects like QRL (Quantum Resistant Ledger) and others represent early attempts to build quantum-resistant blockchain systems, though these projects face challenges in achieving the network effects and adoption necessary for long-term viability.
Academic and industry research collaborations have emerged to address various aspects of the quantum threat to cryptocurrency systems, including research into efficient post-quantum cryptographic implementations, analysis of quantum attack scenarios, and development of quantum risk assessment methodologies. These collaborative efforts bring together expertise from cryptography, quantum computing, and blockchain development to address the complex challenges posed by the quantum threat.
Standards development organizations including NIST, ISO, and others are working to establish standards for post-quantum cryptographic systems that could be adopted by cryptocurrency protocols. The NIST post-quantum cryptography standardization process has identified several candidate algorithms that may be suitable for cryptocurrency applications, though additional research is needed to optimize these systems for blockchain-specific requirements.
Hardware security module vendors and cryptocurrency custody providers are beginning to develop quantum-resistant solutions for key management and transaction signing, recognizing that quantum threats extend beyond protocol-level cryptography to include the entire cryptocurrency security infrastructure. These solutions may provide near-term protection against quantum attacks even before protocol-level quantum resistance is implemented.
The development of quantum key distribution and other quantum cryptographic technologies offers potential long-term solutions for cryptocurrency security that could provide information-theoretic security guarantees against quantum attacks. However, the practical challenges associated with implementing quantum cryptographic systems at the scale required for global cryptocurrency networks remain significant.
Future Technological Developments
The intersection of quantum computing and cryptocurrency technology extends beyond the immediate security threats to encompass potential opportunities for quantum-enhanced blockchain systems that could leverage quantum computing advantages for improved performance, security, or functionality. Quantum consensus algorithms, quantum-enhanced mining systems, and quantum cryptographic protocols represent emerging areas of research that could fundamentally transform cryptocurrency technology.
Quantum consensus mechanisms represent a particularly intriguing area of research, as quantum computing’s ability to process superposition states and perform parallel computations could potentially enable more efficient or secure consensus protocols. Theoretical work on quantum Byzantine agreement and quantum distributed computing suggests that quantum consensus systems could offer advantages over classical alternatives, though practical implementations remain largely experimental.
The potential for quantum machine learning to enhance cryptocurrency security and functionality represents another emerging area of research, as quantum algorithms could potentially identify patterns in blockchain data or transaction flows that are invisible to classical analysis. These capabilities could enable more sophisticated fraud detection, improved privacy protection, or enhanced smart contract functionality, though the practical requirements for implementing quantum machine learning in cryptocurrency systems remain uncertain.
Quantum random number generation represents a more near-term application of quantum technology to cryptocurrency systems, as true quantum randomness could enhance the security of cryptographic key generation, nonce selection, and other randomness-dependent operations. Several cryptocurrency projects have already begun exploring the integration of quantum random number generators into their security infrastructure.
The development of quantum communication networks and quantum internet infrastructure could eventually enable new types of cryptocurrency systems that leverage quantum entanglement and quantum teleportation for secure value transfer. While these technologies remain largely experimental, they represent potential long-term directions for cryptocurrency evolution that could fundamentally change how digital assets are secured and transferred.
Quantum simulation capabilities could enable more sophisticated modeling and analysis of cryptocurrency economic systems, potentially providing insights into market dynamics, protocol behavior, and security properties that are difficult to analyze using classical simulation techniques. These capabilities could inform the design of more robust and efficient cryptocurrency protocols.
The integration of quantum computing with artificial intelligence and machine learning systems could create new opportunities for automated cryptocurrency trading, portfolio management, and risk assessment that leverage quantum advantages in optimization and pattern recognition. These applications could significantly impact cryptocurrency markets and trading strategies.
Quantum-enhanced privacy technologies, including quantum zero-knowledge proofs and quantum homomorphic encryption, could enable new types of privacy-preserving cryptocurrency systems that provide stronger security guarantees than current privacy protocols. These technologies could address growing concerns about transaction privacy and regulatory compliance in cryptocurrency systems.
Regulatory and Policy Considerations
The regulatory landscape surrounding quantum computing and cryptocurrency security remains largely undeveloped, though government agencies and international organizations have begun considering the policy implications of quantum threats to financial systems and critical infrastructure. The intersection of quantum computing policy and cryptocurrency regulation represents a complex area that will likely require new regulatory frameworks and international coordination mechanisms.
National security considerations related to quantum computing development have led several countries to implement export controls and research restrictions that could impact the development and deployment of quantum-resistant cryptocurrency systems. These restrictions may create challenges for international collaboration on cryptocurrency quantum resistance while potentially creating competitive advantages for countries with advanced quantum research capabilities.
The timeline uncertainty surrounding quantum computing development creates significant challenges for regulatory planning, as regulators must balance the need for proactive quantum risk management against the costs and complexity of premature regulatory intervention. Different regulatory approaches may emerge across jurisdictions, potentially creating compliance challenges for global cryptocurrency systems.
Financial stability considerations related to quantum threats have begun appearing in central bank research and policy discussions, as the potential for quantum attacks to disrupt major cryptocurrency markets could have spillover effects on traditional financial systems. Regulatory frameworks may eventually require cryptocurrency systems to demonstrate quantum resistance or implement specific quantum risk management measures.
International cooperation on quantum computing policy and cryptocurrency regulation will likely be necessary to address the global nature of both quantum threats and cryptocurrency systems. Organizations like the Financial Stability Board and International Organization of Securities Commissions may play important roles in coordinating international responses to quantum threats in cryptocurrency markets.
The development of quantum-safe cryptographic standards by organizations like NIST will likely influence regulatory requirements for cryptocurrency quantum resistance, as regulators may require compliance with established standards rather than developing cryptocurrency-specific quantum resistance requirements.
Privacy and surveillance considerations related to quantum computing capabilities may impact cryptocurrency regulatory approaches, as quantum computers could potentially enable more sophisticated monitoring and analysis of cryptocurrency transactions. These capabilities could influence regulatory attitudes toward privacy-focused cryptocurrencies and anonymous transaction systems.
The potential for quantum computing to impact traditional financial system security may create regulatory incentives for cryptocurrency adoption as quantum-resistant alternatives to quantum-vulnerable traditional payment systems. This dynamic could significantly alter regulatory attitudes toward cryptocurrency technology.
Practical Steps for Cryptocurrency Users and Investors
Individual cryptocurrency users and investors can take several practical steps to protect themselves against potential quantum threats while the industry develops and implements quantum-resistant solutions. Understanding the quantum risk timeline and implementing appropriate risk management strategies represents an important component of comprehensive cryptocurrency security planning.
Diversification strategies that include quantum-resistant cryptocurrency protocols can help reduce exposure to quantum threats while maintaining participation in the cryptocurrency ecosystem. As quantum-resistant protocols mature and gain adoption, strategic allocation to these systems may provide protection against quantum attacks on traditional cryptocurrency systems.
Key management practices that minimize quantum exposure include avoiding address reuse and implementing proper operational security measures that limit the exposure of public keys. While these practices cannot fully protect against sophisticated quantum attacks, they can reduce vulnerability windows and provide additional security margins.
Regular monitoring of quantum computing developments and cryptocurrency quantum resistance progress can help users make informed decisions about their cryptocurrency holdings and security practices. Staying informed about quantum research breakthroughs and cryptocurrency protocol developments enables proactive risk management rather than reactive responses to quantum threats.
Hardware security practices that incorporate quantum-resistant elements, including quantum random number generators and quantum-resistant key management systems, can provide additional protection against quantum attacks. While these solutions may not be immediately available or practical for all users, they represent important components of comprehensive quantum risk management strategies.
Insurance and risk management products that address quantum threats in cryptocurrency holdings may become available as the industry matures and quantum risks become better understood. Users should consider these products as part of comprehensive cryptocurrency risk management strategies.
Portfolio allocation strategies that account for quantum risk may include reducing exposure to quantum-vulnerable assets as quantum computing capabilities advance while increasing allocation to quantum-resistant alternatives. These strategies should be balanced against other investment considerations and risk factors.
Portfolio tracking tools on TradingView can help investors monitor their quantum risk exposure across different cryptocurrency holdings and adjust their strategies as quantum computing technology advances.
Long-term Outlook and Scenarios
The long-term outlook for cryptocurrency security in the quantum computing era depends on numerous factors including the pace of quantum computing development, the effectiveness of quantum-resistant cryptographic solutions, and the ability of cryptocurrency protocols to successfully implement quantum resistance upgrades. Several scenarios could emerge depending on how these factors develop over the coming decades.
The optimistic scenario involves successful development and deployment of quantum-resistant cryptocurrency systems before quantum computers become capable of breaking current cryptographic systems. In this scenario, the cryptocurrency industry successfully transitions to quantum-resistant protocols with minimal disruption to markets or user adoption, potentially even strengthening the value proposition of cryptocurrency systems by demonstrating their adaptability and resilience.
A more challenging scenario involves quantum computers achieving cryptographic capabilities before adequate quantum-resistant solutions are widely deployed, potentially causing significant market disruption and forcing rapid emergency upgrades to cryptocurrency protocols. This scenario could result in temporary market instability but ultimately lead to stronger and more secure cryptocurrency systems.
The worst-case scenario involves quantum computers breaking cryptocurrency cryptography before effective countermeasures are implemented, potentially causing catastrophic losses for cryptocurrency holders and undermining confidence in digital asset systems. While this scenario appears unlikely given current research progress, it highlights the importance of proactive quantum resistance development.
Intermediate scenarios involve gradual quantum computing development that provides sufficient warning time for cryptocurrency systems to implement quantum resistance while creating ongoing market uncertainty and volatility as quantum capabilities advance. These scenarios may result in extended transition periods with hybrid security systems and evolving threat landscapes.
The competitive dynamics between different cryptocurrency protocols during the quantum transition could significantly impact long-term market structure, with early adopters of effective quantum resistance potentially gaining substantial market advantages. This dynamic could accelerate innovation and development in quantum-resistant cryptographic systems.
The broader implications of quantum computing for financial systems and digital security could create opportunities for cryptocurrency systems to demonstrate superior quantum resistance compared to traditional financial infrastructure, potentially accelerating cryptocurrency adoption as quantum threats to traditional systems become apparent.
International cooperation and competition in quantum computing development could influence the timeline and nature of quantum threats to cryptocurrency systems, with different geopolitical scenarios potentially affecting the availability and effectiveness of quantum countermeasures.
The eventual maturation of both quantum computing and quantum-resistant cryptographic technologies could lead to a new equilibrium in which quantum threats are effectively managed and cryptocurrency systems provide enhanced security and functionality compared to current systems.
Conclusion
The intersection of quantum computing and cryptocurrency security represents one of the most significant long-term challenges and opportunities facing the digital asset ecosystem, requiring proactive planning, innovative technical solutions, and coordinated industry responses to ensure the continued security and viability of cryptocurrency systems. While quantum computers capable of breaking current cryptocurrency cryptography may not emerge for years or decades, the potential impact of these technologies is so significant that early preparation and risk management are essential for the long-term success of the cryptocurrency industry.
The technical challenges associated with implementing quantum-resistant cryptographic systems in cryptocurrency protocols are substantial but not insurmountable, requiring careful engineering, extensive testing, and coordinated deployment strategies that balance security requirements with performance considerations and backward compatibility needs. The cryptocurrency industry’s track record of successfully implementing complex technical upgrades provides reason for optimism about its ability to address quantum threats, though the scale and complexity of quantum resistance implementation will test the industry’s technical capabilities and governance mechanisms.
Market implications of quantum threats extend far beyond technical security considerations to encompass fundamental questions about cryptocurrency valuation, adoption patterns, and competitive dynamics that will likely play out over extended timeframes as quantum computing capabilities advance. Understanding and preparing for these market implications represents an important component of comprehensive cryptocurrency investment and development strategies.
The regulatory and policy landscape surrounding quantum threats to cryptocurrency systems remains largely undeveloped but will likely become increasingly important as quantum computing capabilities advance and government agencies develop more sophisticated understanding of quantum risks to financial systems and critical infrastructure. Proactive engagement with regulatory development processes may help ensure that quantum resistance requirements are technically feasible and economically reasonable.
The ultimate impact of quantum computing on cryptocurrency security will depend on the complex interplay between technological development timelines, industry responses, regulatory frameworks, and market dynamics that are difficult to predict with precision. However, the potential magnitude of quantum impacts on cryptocurrency systems makes this one of the most important long-term considerations for anyone involved in the cryptocurrency ecosystem, whether as users, investors, developers, or regulators.
Success in navigating the quantum transition will require sustained commitment to research and development, international cooperation on standards and best practices, and continued innovation in both quantum-resistant cryptographic systems and quantum computing technologies themselves. The cryptocurrency industry’s demonstrated ability to adapt to changing technological and regulatory environments provides a foundation for optimism about its ability to successfully address quantum challenges while potentially emerging stronger and more secure than current systems.
The quantum threat to cryptocurrency security represents not just a challenge to be overcome but also an opportunity to develop more robust, secure, and innovative digital asset systems that could provide advantages over both current cryptocurrency implementations and traditional financial infrastructure. Realizing these opportunities will require the best efforts of researchers, developers, and industry participants working together to build a quantum-safe future for digital assets.
Disclaimer: This article is for informational and educational purposes only and does not constitute financial, investment, legal, or trading advice. Cryptocurrency investments carry significant risks, including the potential for total loss of capital. The quantum computing threat to cryptocurrency security involves significant uncertainties and long-term technical developments that are difficult to predict with precision. Past performance of cryptocurrency assets does not guarantee future results. The regulatory landscape for cryptocurrency is rapidly evolving and may impact the viability and legality of cryptocurrency investments. Readers should conduct their own research and consult with qualified financial, legal, and technical advisors before making any cryptocurrency-related decisions. The views expressed in this article are those of the author and do not necessarily reflect the views of any affiliated organizations or partners. Quantum computing development timelines and capabilities remain highly uncertain, and actual developments may differ significantly from current predictions and assessments.