The Quantum Revolution and Cryptographic Foundations
The emergence of quantum computing represents one of the most significant technological leaps of our time, promising to revolutionize everything from drug discovery to financial modeling. However, this revolutionary technology also poses an unprecedented threat to the cryptographic foundations that secure our digital assets. As quantum computers become more powerful and accessible, the question isn’t whether they will break current encryption methods, but when. For cryptocurrency holders and blockchain networks, this quantum threat represents an existential challenge that demands immediate attention and preparation.
The fundamental vulnerability lies in the mathematical problems that underpin modern cryptography. Bitcoin, Ethereum, and virtually every other cryptocurrency rely on elliptic curve cryptography and the RSA algorithm, both of which are considered computationally infeasible to break with classical computers. These cryptographic systems depend on the difficulty of factoring large numbers or solving discrete logarithm problems, tasks that would take classical computers thousands of years to complete. However, quantum computers operate on entirely different principles, using quantum bits or qubits that can exist in multiple states simultaneously, enabling them to solve these mathematical problems exponentially faster than their classical counterparts.
Shor’s Algorithm and the Y2Q Timeline
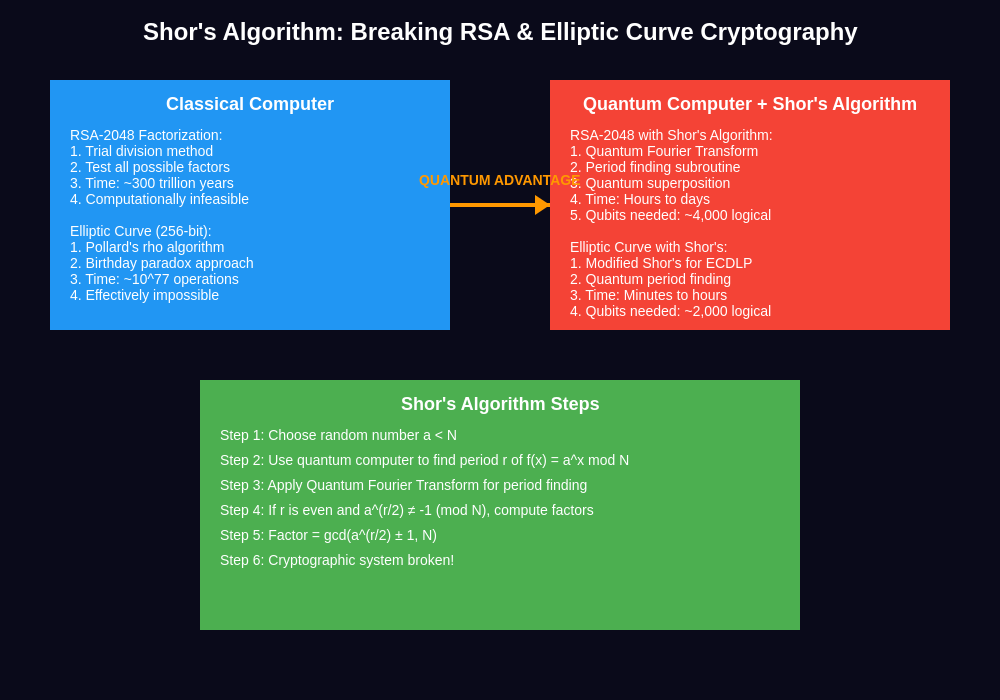
The theoretical framework for this quantum advantage was established by mathematician Peter Shor in 1994, when he developed an algorithm specifically designed to factor large integers efficiently on a quantum computer. Shor’s algorithm demonstrated that a sufficiently powerful quantum computer could break RSA encryption and elliptic curve cryptography in polynomial time, reducing what would take classical computers millennia to accomplish into mere hours or days. This revelation sent shockwaves through the cryptographic community and established the timeline for what experts now call “Y2Q” or “Years to Quantum” – the countdown to when quantum computers will possess enough power to threaten current encryption standards.
Current Quantum Computing Capabilities
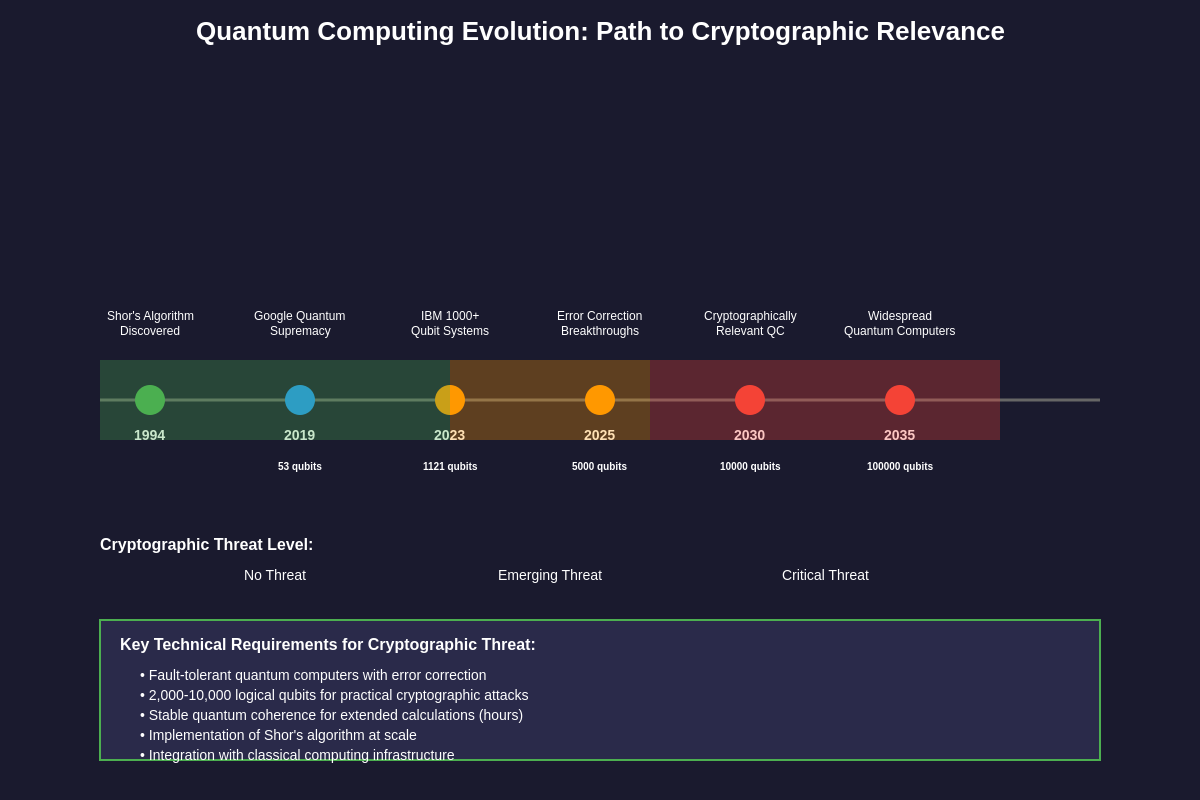
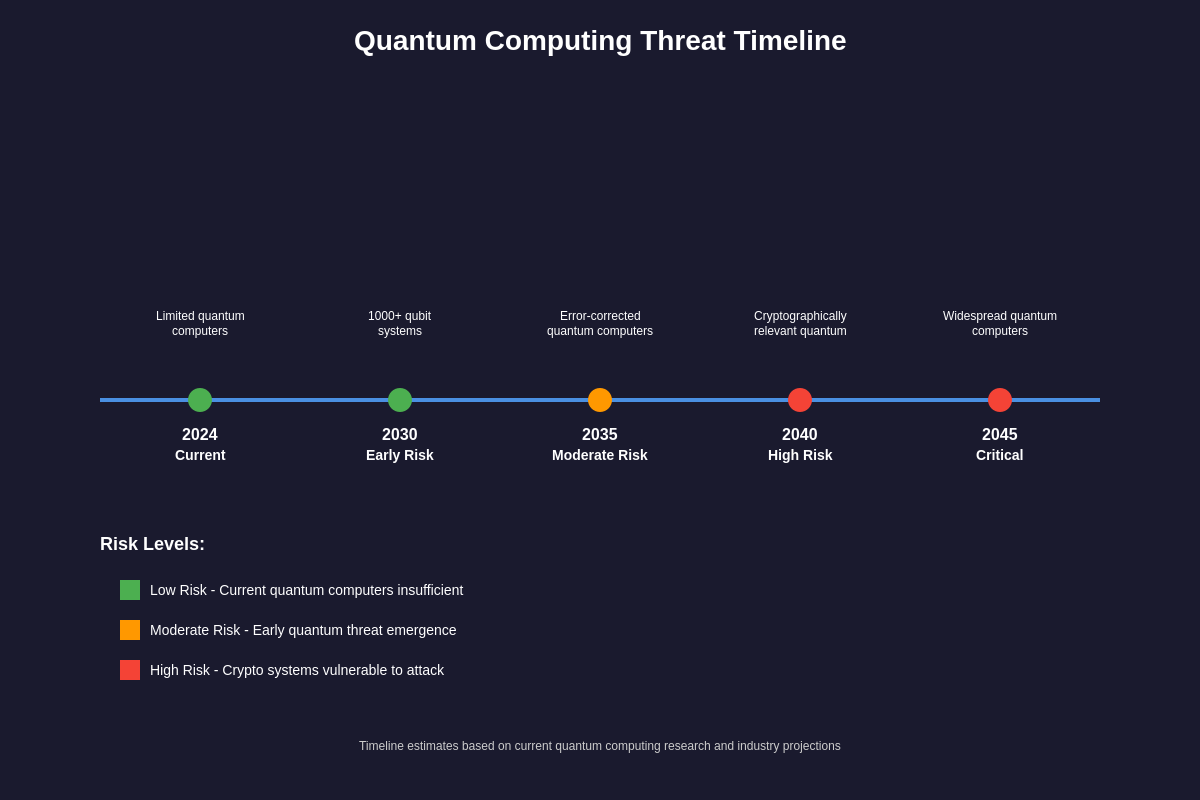
Current quantum computing capabilities remain limited but are advancing rapidly. Companies like IBM, Google, and IonQ have developed quantum computers with hundreds of qubits, but these systems are still far from the thousands of stable, error-corrected qubits needed to break modern encryption. IBM’s recent roadmap suggests they will achieve 100,000 qubits by 2033, while other estimates place the cryptographically relevant quantum computer threshold at around 4,000 to 10,000 logical qubits. The challenge lies not just in scaling the number of qubits but in achieving the quantum error correction necessary to maintain coherence across complex calculations.
Cryptocurrency Vulnerabilities Exposed
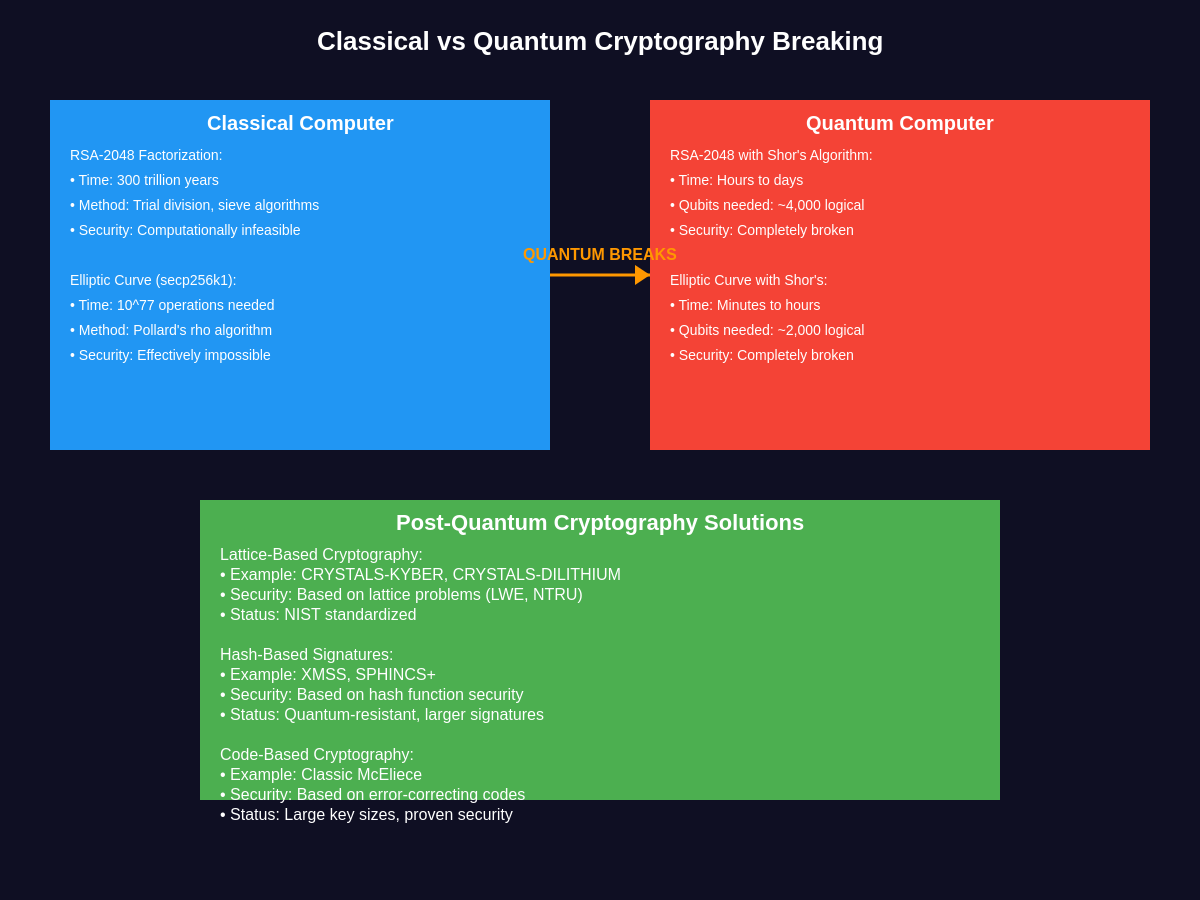
The implications for cryptocurrency security are profound and multifaceted. Bitcoin addresses are generated using elliptic curve cryptography, specifically the secp256k1 curve, which creates a public-private key pair. The security model assumes that deriving a private key from a public key is computationally impossible. However, a quantum computer running Shor’s algorithm could potentially derive private keys from public keys, effectively allowing an attacker to steal funds from any address that has ever made a transaction and thus exposed its public key on the blockchain. Professional traders monitoring Bitcoin’s price movements and technical patterns need to understand these fundamental security risks that could impact long-term value propositions.
Ethereum faces similar vulnerabilities, as it also relies on elliptic curve cryptography for address generation and transaction signing. The Ethereum network’s transition to proof-of-stake through Ethereum 2.0 introduces additional quantum vulnerabilities in its validator system, where quantum attacks could potentially compromise validator keys and disrupt network consensus. The decentralized nature of blockchain networks means that quantum attacks could simultaneously target multiple participants, creating systemic risks that extend beyond individual wallet compromises.
Quantum Threat Timeline and Investment Landscape
The timeline for quantum threats varies significantly depending on technological breakthroughs and investment in quantum research. Conservative estimates suggest that cryptographically relevant quantum computers may emerge within 10 to 20 years, while more optimistic projections place this timeline at 5 to 10 years. National security agencies and governments are investing heavily in quantum research, with programs like the U.S. National Quantum Initiative and China’s massive quantum computing investments potentially accelerating development timelines. The secretive nature of some quantum research means that breakthrough announcements could come suddenly, leaving little time for cryptographic transitions. Investors tracking quantum computing stocks and related technology trends should monitor these developments closely as they will significantly impact the cryptocurrency market landscape.
Industry Response to Quantum Threats
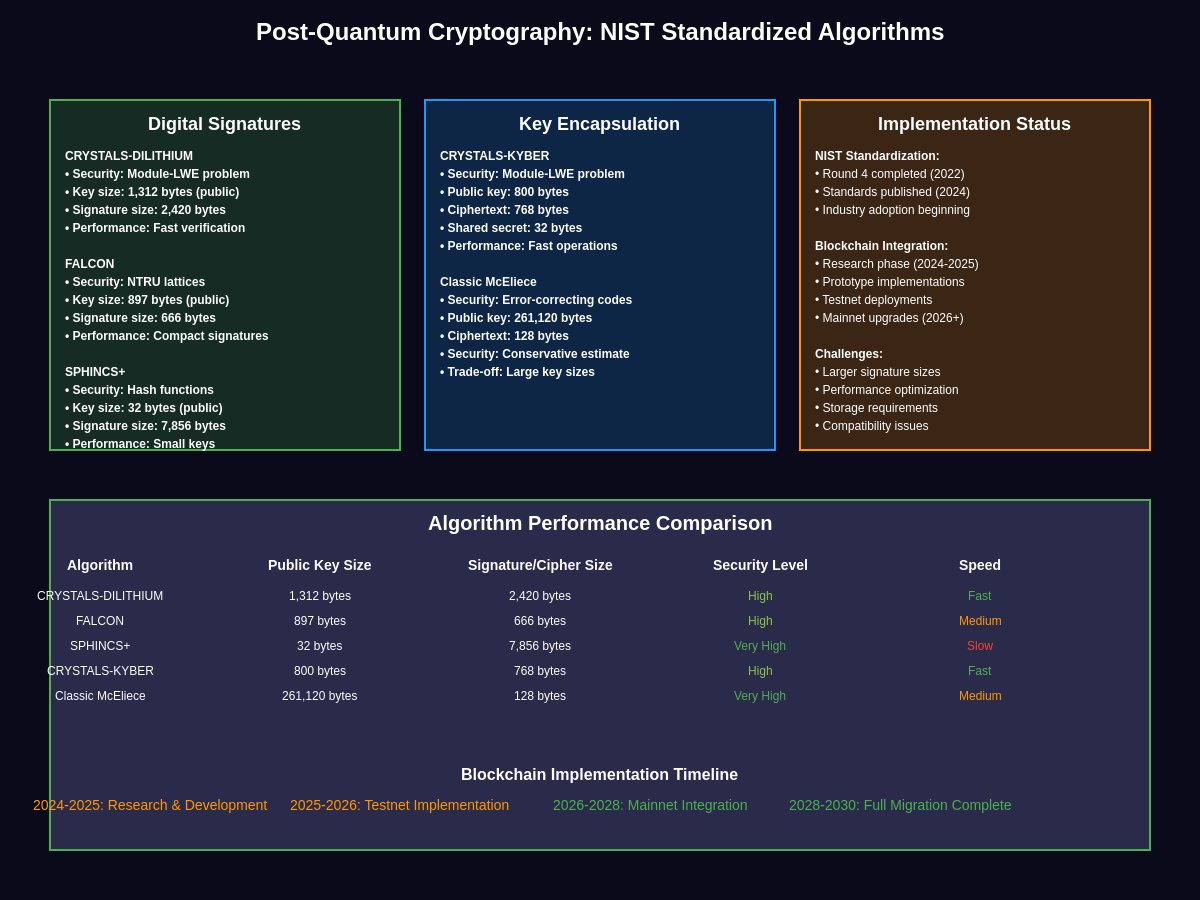
The cryptocurrency industry has begun responding to these quantum threats through various approaches. Post-quantum cryptography research focuses on developing mathematical problems that remain difficult even for quantum computers to solve. These quantum-resistant algorithms typically rely on different mathematical foundations, such as lattice-based cryptography, hash-based signatures, or multivariate cryptography. The National Institute of Standards and Technology has been standardizing post-quantum cryptographic algorithms, with several candidates showing promise for blockchain integration.
Bitcoin’s Quantum Defense Strategy
Bitcoin’s response to quantum threats involves multiple potential solutions. The network could implement quantum-resistant signature schemes through soft forks, maintaining backward compatibility while adding new address types that use post-quantum cryptography. BIP-340, which introduced Schnorr signatures, provides a foundation for implementing quantum-resistant schemes through future upgrades. The Bitcoin community has also discussed quantum-resistant address formats that could coexist with current addresses, allowing users to migrate their funds proactively rather than reactively. Traders analyzing Bitcoin’s technical indicators and market sentiment should factor in these upcoming protocol changes when evaluating long-term investment strategies.
Ethereum’s Quantum Resistance Roadmap
Ethereum’s roadmap includes quantum resistance as a long-term consideration, with research into quantum-resistant signature schemes and consensus mechanisms. The network’s ability to implement complex smart contracts provides additional flexibility in deploying quantum-resistant solutions, potentially allowing for gradual migration strategies that protect user funds while maintaining network functionality. Ethereum Improvement Proposals have been submitted addressing quantum resistance, though implementation timelines remain undefined. Market participants monitoring Ethereum’s price action and network developments should track these quantum resistance updates as they will influence the platform’s competitive positioning.
Hardware Wallets and Cold Storage Security
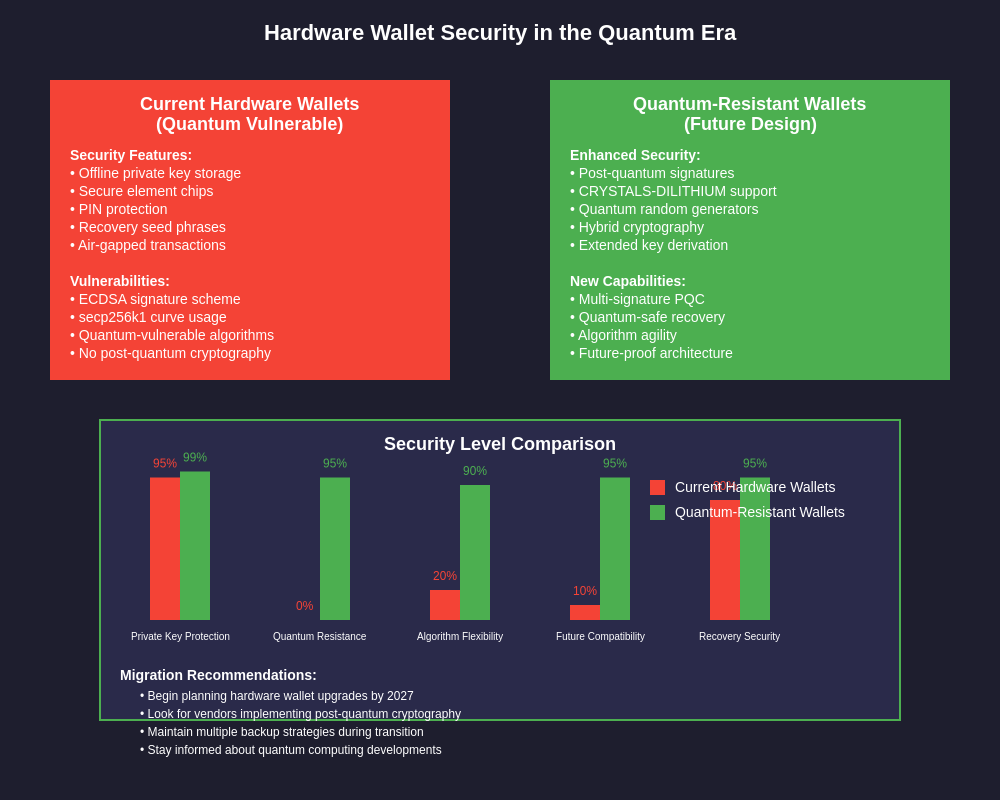
Hardware wallets and cold storage solutions face unique quantum challenges. Current hardware wallets like Ledger and Trezor use the same elliptic curve cryptography as hot wallets, making them equally vulnerable to quantum attacks. However, hardware wallets that never expose private keys online may provide additional security against remote quantum attacks. Future hardware wallet designs are already incorporating quantum-resistant elements, with some companies exploring quantum random number generators and post-quantum signature schemes in their development roadmaps.
Quantum Supremacy in Cryptography
The concept of quantum supremacy in cryptography differs from the quantum supremacy demonstrations we’ve seen in specialized computing tasks. Breaking cryptographically relevant problems requires not just raw quantum computing power but also the ability to maintain quantum coherence across extended calculations and implement complex error correction protocols. Current quantum computers suffer from high error rates and short coherence times, limiting their practical cryptographic applications. However, advances in quantum error correction and fault-tolerant quantum computing are steadily addressing these limitations.
Quantum Key Distribution and Enhanced Security
Quantum key distribution represents another approach to quantum-safe communications, using the principles of quantum mechanics to detect eavesdropping attempts and establish provably secure communication channels. While QKD requires specialized infrastructure and is primarily suited for point-to-point communications, it demonstrates how quantum mechanics can enhance rather than threaten cryptographic security. Some researchers propose hybrid approaches that combine QKD with blockchain networks for ultra-secure transaction channels.
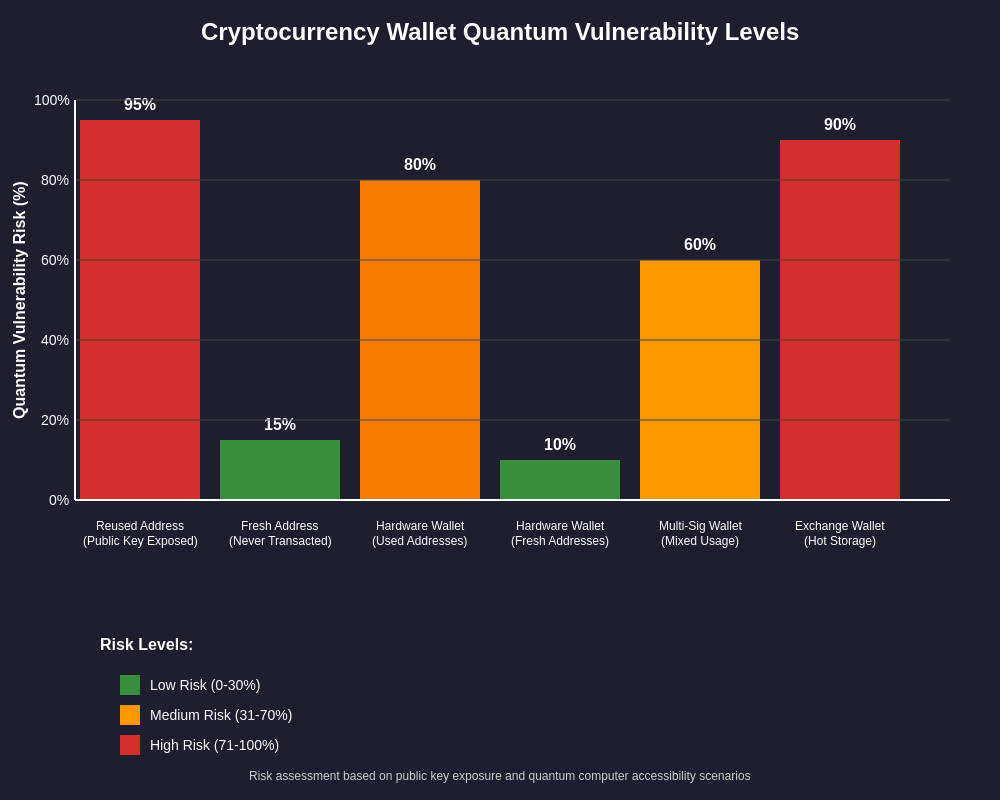
Economic Impact and Market Implications
The economic implications of quantum threats extend beyond individual wallet security to encompass entire cryptocurrency ecosystems. A successful quantum attack on a major cryptocurrency could trigger massive sell-offs, potentially destabilizing the entire crypto market. The anticipation of quantum threats might also influence institutional adoption, with risk-averse institutions potentially delaying cryptocurrency investments until quantum-resistant solutions are implemented. Conversely, early adoption of quantum-resistant technologies could become a significant competitive advantage for forward-thinking blockchain projects. Savvy investors utilize comprehensive crypto market analysis tools to evaluate these technological risks alongside traditional market indicators when building their portfolios.
Migration Strategies for Cryptocurrency Holdings
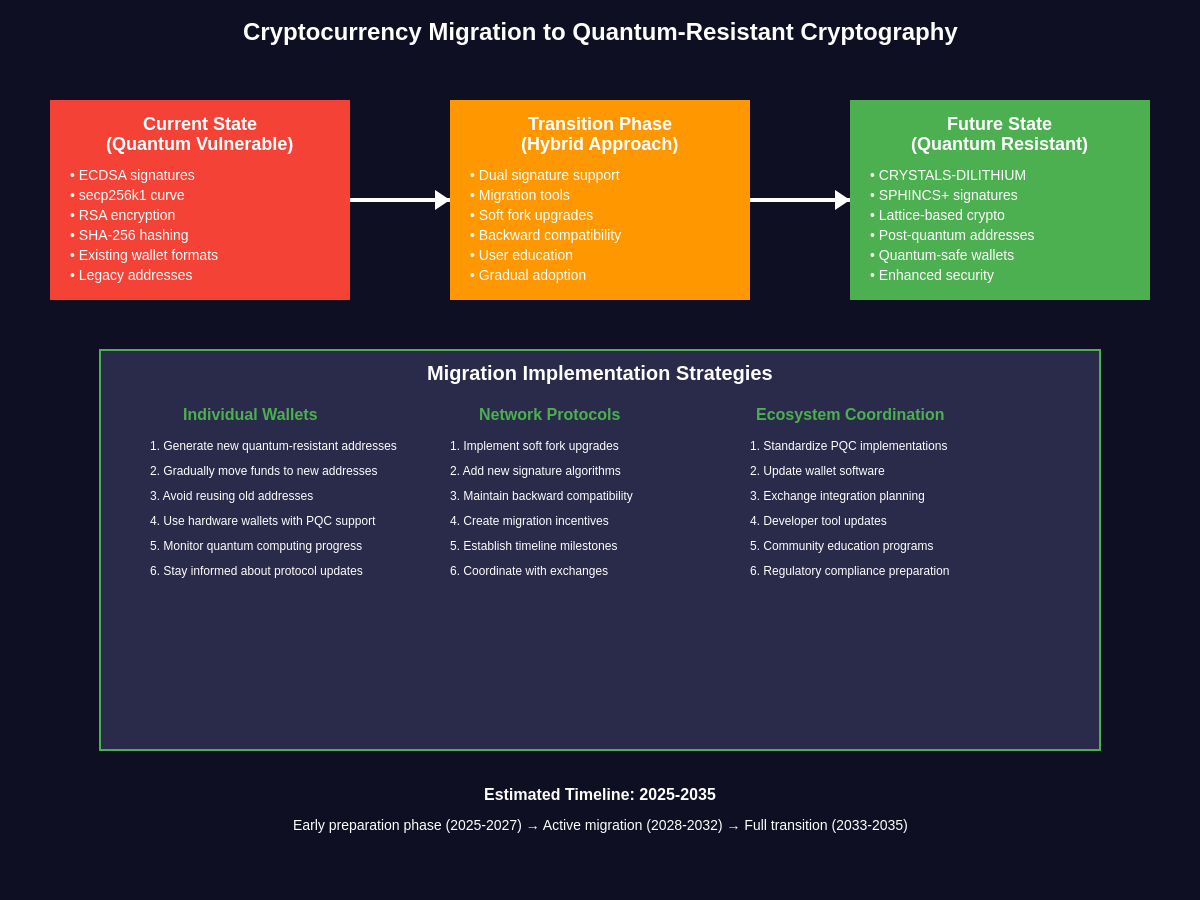
Migration strategies for existing cryptocurrency holdings require careful consideration of timing and implementation approaches. Users holding cryptocurrencies in addresses that have never made outgoing transactions benefit from additional security, as their public keys remain unknown to potential attackers. However, any transaction that spends from an address exposes its public key on the blockchain, creating potential quantum vulnerabilities. Migration strategies might involve moving funds to quantum-resistant addresses before quantum computers become cryptographically relevant, but such migrations must be carefully timed to avoid unnecessary costs and complications.
Government Regulation and International Coordination
The role of governments and regulatory bodies in addressing quantum threats is becoming increasingly important. National security concerns about quantum computing’s impact on financial systems have led to increased funding for post-quantum cryptography research and potential regulatory requirements for quantum-resistant systems. The interconnected nature of global financial systems means that quantum threats to cryptocurrencies could have broader implications for economic stability, potentially driving coordinated international responses to quantum risks.
Research Collaboration and Quantum-Resistant Innovations
Research institutions and cryptocurrency projects are collaborating on quantum-resistant solutions through various initiatives. The Quantum Resistant Ledger project has implemented post-quantum signatures from its inception, providing a testing ground for quantum-resistant blockchain technologies. Academic research into quantum-resistant consensus mechanisms, zero-knowledge proofs, and privacy-preserving technologies continues to advance, with many findings applicable to existing cryptocurrency networks through future upgrades.
Mining and Quantum Computing Convergence
The intersection of quantum computing and cryptocurrency mining presents additional considerations. Quantum computers could potentially provide advantages in solving proof-of-work puzzles, though the specialized nature of mining hardware and the specific requirements of hash-based proof-of-work algorithms may limit quantum advantages in this area. However, quantum computers could excel at optimizing mining strategies and identifying profitable mining opportunities, potentially centralizing mining power among quantum-enabled participants.
Privacy Cryptocurrencies and Quantum Vulnerabilities
Privacy-focused cryptocurrencies face unique quantum challenges due to their reliance on advanced cryptographic techniques. Zero-knowledge proofs, ring signatures, and other privacy-preserving technologies used by coins like Monero and Zcash may be vulnerable to quantum attacks, potentially compromising the privacy guarantees that define these projects. Research into quantum-resistant privacy technologies is ongoing, with some projects already implementing post-quantum privacy features in their development roadmaps. Traders interested in privacy coin price movements and market dynamics should closely monitor quantum resistance development progress as it directly impacts the fundamental value proposition of these cryptocurrencies.
Development Timeline for Quantum-Resistant Solutions
The development timeline for quantum-resistant cryptocurrency solutions involves multiple phases, from research and standardization to implementation and adoption. Early phases focus on identifying suitable post-quantum algorithms and adapting them for blockchain use cases. Standardization efforts ensure interoperability and security across different implementations. Implementation phases involve integrating quantum-resistant features into existing networks through upgrades or creating new quantum-resistant cryptocurrencies from scratch. Adoption phases require user education, wallet support, and ecosystem coordination to ensure smooth transitions to quantum-resistant systems.
Testing and Validation of Post-Quantum Systems
Testing and validation of quantum-resistant cryptographic systems require extensive analysis and peer review. Unlike classical cryptography, which has been tested against decades of attack attempts, post-quantum cryptography is relatively new and may contain undiscovered vulnerabilities. Standardization bodies like NIST conduct rigorous evaluation processes, but the complexity of post-quantum algorithms means that ongoing analysis and validation will be necessary even after standardization. The cryptocurrency community’s open-source nature provides additional opportunities for peer review and security analysis of quantum-resistant implementations.
Education and Awareness Initiatives
Educational initiatives around quantum threats and cryptocurrency security are essential for preparing users and developers for the quantum transition. Understanding the timeline and implications of quantum threats allows cryptocurrency users to make informed decisions about wallet security and migration strategies. Developer education ensures that new cryptocurrency projects consider quantum resistance from their initial design phases rather than attempting to retrofit quantum resistance into existing systems.
Global Coordination and Network Upgrades
The global nature of cryptocurrency networks means that quantum-resistant transitions must consider diverse regulatory environments, technical capabilities, and user populations. Coordination mechanisms for network-wide upgrades become critical when implementing quantum-resistant features, particularly for decentralized networks without central authorities to mandate upgrades. Economic incentives may be necessary to encourage adoption of quantum-resistant technologies, potentially through reduced transaction fees or enhanced security features for quantum-resistant transactions. Advanced charting and analysis platforms enable sophisticated modeling of these network upgrade scenarios and their potential market impacts.
Preparing for the Quantum Future
As we stand at the threshold of the quantum era, the cryptocurrency industry faces both unprecedented challenges and remarkable opportunities. The quantum threat is real and approaching, but it is not insurmountable. Through proactive research, careful planning, and coordinated implementation of quantum-resistant technologies, the cryptocurrency ecosystem can not only survive the quantum transition but emerge stronger and more secure than ever before. The key lies in acting now, before quantum computers achieve cryptographic relevance, to ensure that the digital assets that represent the future of finance remain secure in a quantum world.
The Path Forward for Quantum-Resistant Cryptocurrencies
The journey toward quantum-resistant cryptocurrency systems will require unprecedented cooperation between researchers, developers, users, and regulators. Success depends not only on technological innovation but also on education, coordination, and timely implementation of quantum-resistant solutions. As quantum computing continues to advance, the cryptocurrency community must remain vigilant, adaptive, and committed to maintaining the security and integrity that form the foundation of digital asset systems.
Professional traders and institutional investors require sophisticated technical analysis tools and real-time market data to navigate the evolving landscape of quantum-resistant cryptocurrencies and assess the long-term implications of these technological developments on their investment strategies.
Disclaimer: This article is for educational and informational purposes only and should not be construed as financial advice. Cryptocurrency investments carry significant risks, including the potential for total loss of capital. The quantum computing threats discussed are based on current research and projections, which may change as technology develops. Always conduct your own research and consult with qualified financial advisors before making investment decisions. The author and publisher are not responsible for any financial losses that may occur from acting on the information provided in this article.