Get advanced technical analysis tools and Pine Script resources at TradingView’s comprehensive platform for secure cryptocurrency trading strategies.
The Critical Foundation of Cryptocurrency Security
Seed phrases represent the most fundamental security component in cryptocurrency ownership, serving as the master key that controls access to digital assets across virtually all blockchain networks. These twelve to twenty-four word sequences, formally known as mnemonic phrases or recovery phrases, provide the cryptographic foundation that allows users to recover and control their cryptocurrency wallets regardless of device failure, loss, or theft. Understanding the critical importance of proper seed phrase security practices has become essential for anyone participating in the cryptocurrency ecosystem, as a single compromised seed phrase can result in the permanent loss of all associated digital assets.
The mathematical elegance of seed phrases lies in their ability to generate virtually unlimited wallet addresses and private keys through hierarchical deterministic algorithms, making them simultaneously powerful and vulnerable. Unlike traditional banking where account recovery involves identity verification and institutional support, cryptocurrency seed phrases operate on a trustless system where possession of the correct word sequence provides absolute control over associated funds. This fundamental difference means that seed phrase security cannot rely on third-party recovery mechanisms, placing the entire burden of protection on individual users who must implement comprehensive security strategies to safeguard their digital wealth.
Understanding the Technical Foundation of Seed Phrases
The technical architecture underlying seed phrases emerges from the BIP39 standard, which defines how random entropy is converted into human-readable word sequences that can reliably recreate wallet private keys and addresses. This standardization ensures that seed phrases generated by one wallet application can be imported into another compatible wallet, providing users with flexibility and protection against vendor lock-in while maintaining security through cryptographic randomness.
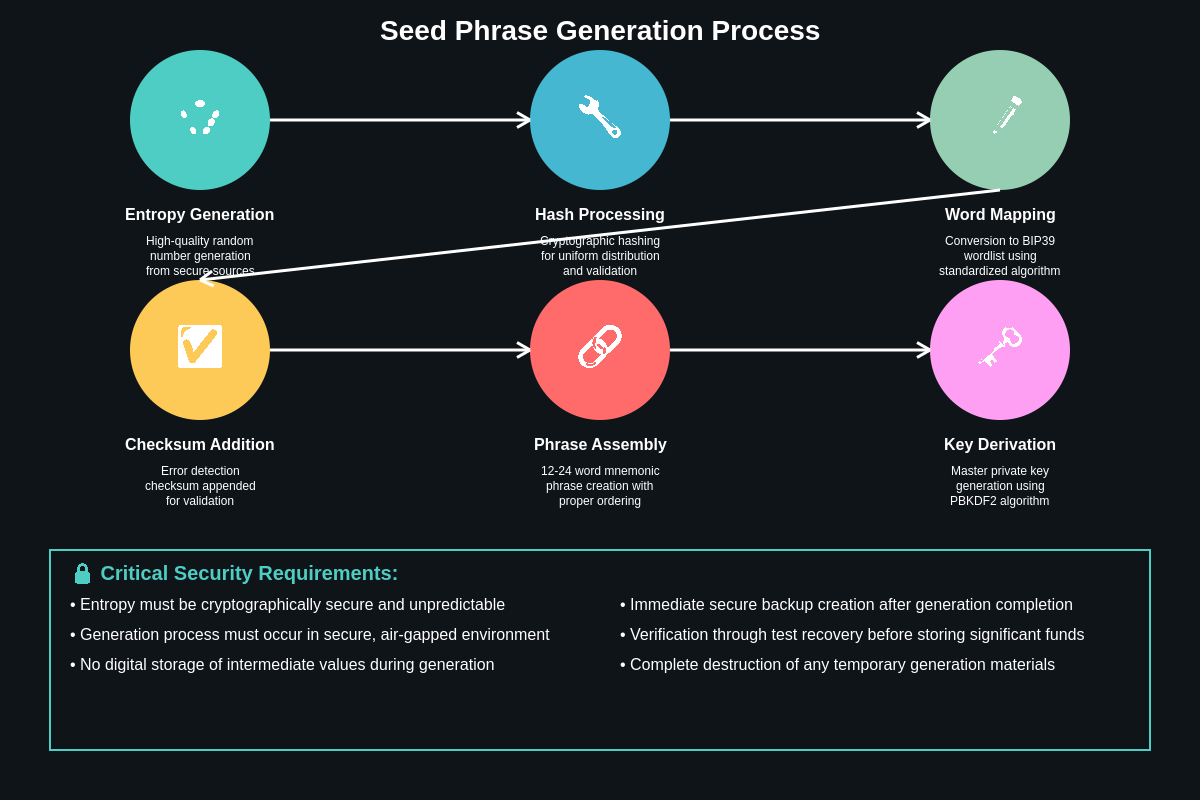
Modern seed phrase generation begins with high-quality entropy sources that produce truly random data, typically derived from operating system random number generators that collect unpredictable environmental factors such as mouse movements, keyboard timings, and hardware interrupts. This entropy is then processed through cryptographic hash functions to ensure uniform distribution before being mapped to word lists containing exactly 2048 carefully selected words, chosen for their distinctiveness and resistance to confusion during transcription or verbal communication.
The hierarchical deterministic wallet structure enabled by seed phrases allows for the generation of billions of unique addresses from a single seed, creating a tree-like structure where each branch can contain multiple accounts and each account can generate countless receiving addresses. This architecture provides both privacy benefits through address rotation and practical advantages through simplified backup requirements, as users need only secure their seed phrase to maintain access to all derived addresses and their associated cryptocurrency holdings.
Advanced seed phrase implementations incorporate additional security features such as passphrase extensions, which function as a twenty-fifth word that users can optionally add to their seed phrase to create entirely separate wallet instances. This feature enables plausible deniability scenarios where users can maintain both a decoy wallet with minimal funds and a hidden wallet containing their primary holdings, accessible only when the correct passphrase is provided alongside the standard seed phrase sequence.
Common Vulnerabilities and Attack Vectors
Seed phrase vulnerabilities typically emerge from inadequate storage practices, with digital storage representing one of the most significant risk factors for cryptocurrency users. Screenshots, text files, cloud storage, email drafts, and password managers all create digital footprints that can be compromised through various attack vectors including malware, data breaches, unauthorized access, and social engineering attacks targeting account credentials. Even supposedly secure digital storage solutions can fail catastrophically, as demonstrated by numerous incidents where users lost access to cloud storage accounts or discovered that their encrypted files had been corrupted or deleted.
Physical storage vulnerabilities present equally serious challenges, particularly when users fail to protect against environmental hazards, theft, or inadvertent destruction. Paper-based storage, while immune to digital attacks, faces risks from fire, flood, physical degradation, and human error during transcription or handling. Metal storage solutions offer improved durability but can still be subject to theft, loss, or damage from extreme conditions, while improper storage locations can expose seed phrases to discovery by family members, service personnel, or criminals conducting targeted attacks.
Social engineering attacks specifically targeting seed phrase disclosure have become increasingly sophisticated, with attackers impersonating customer support representatives, technical experts, or trusted community members to convince users to reveal their recovery phrases. These attacks often incorporate urgency tactics, technical terminology, and fabricated security scenarios to create psychological pressure that overrides users’ natural security instincts. The effectiveness of these attacks demonstrates how human factors can undermine even technically sound security implementations when users lack proper awareness and training.
Digital forensics capabilities enable attackers to recover seed phrases from devices that users believe have been securely wiped, as standard deletion processes often leave recoverable data traces on storage devices. Even hardware wallets can be vulnerable to sophisticated attacks when users fail to follow proper initialization and setup procedures, potentially exposing seed phrases during the generation process or creating attack vectors through side-channel analysis of device behavior during cryptographic operations.
For comprehensive market analysis and secure trading setups, explore TradingView’s advanced charting tools that professional traders use to protect and grow their cryptocurrency portfolios.
Physical Security Implementation Strategies
Implementing robust physical security for seed phrases requires a multi-layered approach that balances accessibility for legitimate recovery scenarios against protection from unauthorized access and environmental hazards. The optimal physical security strategy typically involves creating multiple copies of seed phrases using different storage mediums and distributing them across geographically separated locations to minimize the risk of total loss from localized disasters or targeted attacks.
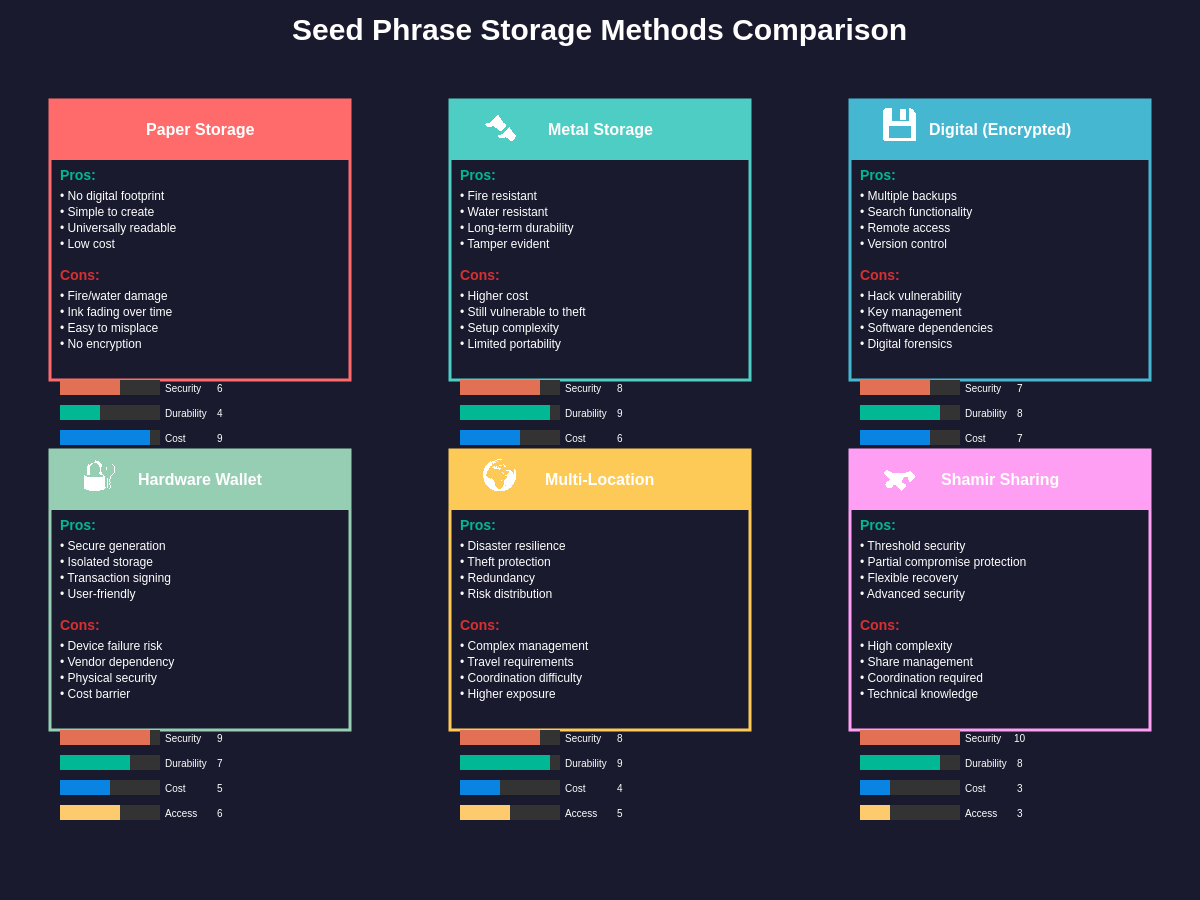
Metal storage solutions have emerged as the gold standard for long-term seed phrase preservation, offering superior resistance to fire, water, and corrosion compared to paper-based alternatives. High-quality stainless steel or titanium storage devices can withstand extreme temperatures, physical impact, and environmental exposure while maintaining legibility for decades. However, users must carefully evaluate different metal storage products, as some designs prove vulnerable to structural failure under stress or use materials that can corrode under specific environmental conditions.
Geographic distribution of seed phrase backups requires careful consideration of access patterns, security levels, and recovery scenarios to ensure that legitimate users can retrieve their phrases when needed while preventing unauthorized access. Safe deposit boxes, home safes, and trusted family members can all serve as storage locations, but each option presents distinct trade-offs between security, accessibility, and cost. Users must develop comprehensive plans that account for various emergency scenarios, including their own incapacitation, natural disasters, and security breaches at storage locations.
Advanced physical security implementations may incorporate techniques such as secret sharing schemes, where seed phrases are split into multiple parts that must be combined for recovery, providing protection against single points of failure while complicating unauthorized access attempts. These schemes can distribute phrase fragments across multiple trusted parties or storage locations, ensuring that compromise of any single fragment does not expose the complete seed phrase while maintaining recoverability through predetermined threshold requirements.
Digital Security Best Practices and Pitfalls
Digital security for seed phrases demands a comprehensive understanding of modern threat landscapes and the implementation of defense-in-depth strategies that account for both technical vulnerabilities and human factors. The fundamental principle guiding digital seed phrase security involves minimizing digital exposure while maintaining practical usability for legitimate recovery scenarios, requiring users to carefully balance convenience against security risks in their implementation strategies.
Password managers represent a contentious topic in seed phrase security, offering both significant benefits and notable risks depending on implementation quality and user practices. High-quality password managers with proper encryption, secure key derivation, and robust authentication mechanisms can provide reasonable protection for seed phrases when combined with strong master passwords and multi-factor authentication. However, password managers also create centralized targets for attackers and introduce additional complexity that can lead to lockout scenarios where users lose access to both their password manager and their seed phrases simultaneously.
Encryption strategies for digital seed phrase storage must account for key management challenges that can create recursive security problems, where the encryption keys themselves require secure storage and management. Advanced users might implement multi-layer encryption schemes using different algorithms and key sources, but these approaches demand significant technical expertise and can create recovery complications that outweigh their security benefits for typical users. Simpler encryption approaches using established tools and clear recovery procedures often provide better overall security outcomes for most cryptocurrency users.
Cloud storage security for seed phrases requires extreme caution and sophisticated implementation to avoid creating easily accessible targets for attackers. Users who choose to store encrypted seed phrases in cloud services must implement client-side encryption using keys that never leave their control, employ multiple encryption layers with different key sources, and maintain comprehensive offline backup strategies that can function independently of cloud storage access. Even with these precautions, cloud storage introduces attack vectors and dependency risks that make offline storage preferable for most users.
Advanced Security Techniques and Implementations
Multisignature wallet architectures provide sophisticated alternatives to traditional seed phrase security by distributing control across multiple cryptographic keys, reducing the risk associated with any single compromised seed phrase or private key. These systems can require multiple signatures from different keys to authorize transactions, creating security models that can survive the compromise of individual keys while maintaining operational flexibility for legitimate users. Advanced multisignature implementations can incorporate time locks, spending limits, and hierarchical authorization schemes that provide fine-grained control over fund access and movement.
Hardware security modules and dedicated signing devices offer enhanced protection for seed phrases and private keys by providing tamper-resistant environments that isolate cryptographic operations from potentially compromised host systems. These devices can generate seed phrases using high-quality entropy sources, store private keys in secure elements that resist physical and logical attacks, and perform signing operations without exposing sensitive key material to host systems. However, users must carefully evaluate hardware security solutions to ensure they meet their specific security requirements and understand the trade-offs between security and usability inherent in different implementations.
Secure enclaves and trusted execution environments available on modern processors can provide additional layers of protection for cryptocurrency operations by creating isolated computational environments that resist attack from privileged software and operating system compromises. These technologies enable the development of wallet applications that can protect seed phrases and private keys even when running on compromised systems, though they require careful implementation and ongoing security updates to maintain their protective properties against evolving attack techniques.
Threshold cryptography and secret sharing schemes enable advanced users to implement distributed seed phrase security where no single party or location contains sufficient information to compromise the complete seed phrase. These systems can split seed phrases using mathematical techniques that require a predetermined threshold of shares to reconstruct the original phrase, providing resilience against partial compromises while maintaining recoverability through legitimate channels. Implementation of threshold schemes requires careful attention to share distribution, recovery procedures, and participant coordination to ensure effective security without creating operational complications.
Learn advanced security strategies for cryptocurrency trading with TradingView’s professional analysis tools that help traders implement comprehensive risk management approaches.
Recovery Planning and Emergency Procedures
Comprehensive recovery planning for seed phrase security requires users to develop detailed procedures that account for various failure scenarios, from simple device loss to complex emergency situations involving incapacitation, natural disasters, or security breaches. Effective recovery plans must balance thoroughness with simplicity, ensuring that authorized users can successfully recover their cryptocurrency holdings while preventing unauthorized access through social engineering or document compromise.
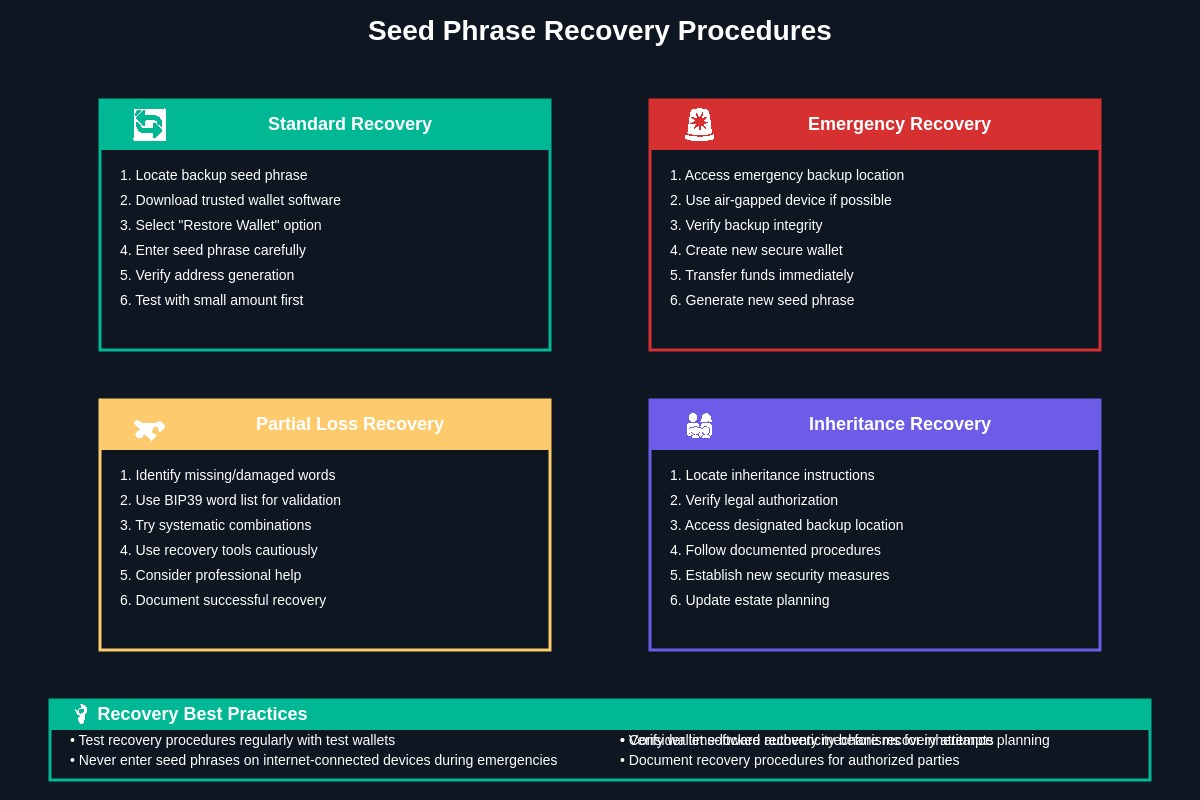
Estate planning considerations for cryptocurrency holdings demand special attention to seed phrase inheritance and succession, as traditional estate planning mechanisms may prove inadequate for managing digital assets secured by cryptographic keys. Users must develop strategies that enable trusted beneficiaries to access cryptocurrency holdings after their death while protecting against premature disclosure or unauthorized access during their lifetime. These strategies might involve trusted third parties, time-locked mechanisms, or legal structures specifically designed to handle cryptocurrency inheritance challenges.
Emergency access procedures should account for various scenarios where normal recovery methods might be unavailable or compromised, including situations where users become incapacitated, primary storage locations become inaccessible, or security breaches require immediate protective actions. Effective emergency procedures require advance preparation, clear documentation, and regular testing to ensure they function correctly when needed while maintaining security against potential abuse by malicious actors.
Documentation and instruction creation for seed phrase recovery requires careful balance between providing sufficient detail for successful recovery and avoiding the creation of documents that could facilitate unauthorized access. Recovery instructions should be clear enough for intended users to follow successfully but should avoid including actual seed phrase content or specific storage location details that could compromise security if the instructions are discovered by unauthorized parties.
Common Mistakes and How to Avoid Them
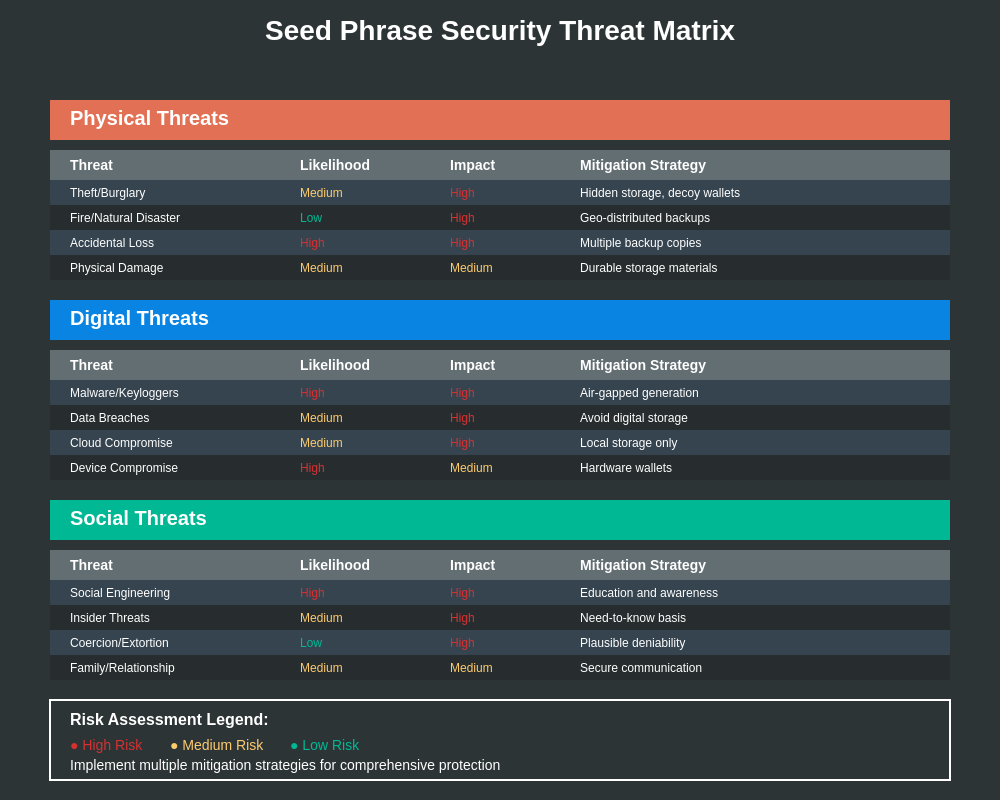
The most prevalent seed phrase security mistake involves inadequate backup strategies, where users either fail to create sufficient backup copies or store all backups in similar environments that can fail simultaneously. Many users create only a single backup copy, often stored in the same location as their primary wallet device, creating scenarios where hardware failure, theft, or disasters can eliminate both primary and backup access to their cryptocurrency holdings. Comprehensive backup strategies require multiple copies using different storage mediums and geographic distribution to ensure resilience against various failure modes.
Transcription errors represent another significant category of seed phrase mistakes, often resulting from unclear handwriting, similar-looking words, or failure to verify backup accuracy through test recovery procedures. Users frequently discover transcription errors only when attempting to recover their wallets during emergency situations, creating high-stress scenarios where correcting mistakes becomes extremely difficult or impossible. Proper transcription procedures involve double-checking all written seed phrases, using clear and consistent handwriting, and performing test recoveries to verify backup accuracy before relying on them for security.
Digital storage mistakes encompass a wide range of poor security practices, from storing seed phrases in plain text files to uploading them to cloud services without adequate encryption protection. Many users fail to understand the persistent nature of digital storage, believing that deleted files are truly gone when they often remain recoverable through forensic techniques for extended periods. Even users who attempt to implement encryption often make implementation mistakes that compromise security, such as using weak passwords, storing encryption keys alongside encrypted data, or failing to properly delete unencrypted temporary files.
Social engineering susceptibility remains a critical vulnerability for many cryptocurrency users, who may disclose seed phrases in response to sophisticated phishing attacks, fake customer support interactions, or social pressure from family members or associates. These attacks often exploit users’ lack of understanding about legitimate recovery procedures, creating scenarios where requests for seed phrase disclosure seem reasonable or necessary. Effective protection against social engineering requires users to understand that legitimate services never require seed phrase disclosure and to develop policies for handling unexpected requests for sensitive information.
Industry Standards and Regulatory Considerations
The BIP39 standard has established the foundational framework for seed phrase implementation across the cryptocurrency industry, providing specifications for entropy generation, word list selection, and mnemonic phrase creation that ensure compatibility between different wallet implementations. This standardization enables users to migrate between different wallet software and hardware devices while maintaining access to their cryptocurrency holdings, though it also creates industry-wide vulnerabilities when implementation flaws or cryptographic weaknesses are discovered in the underlying specifications.
Regulatory frameworks addressing cryptocurrency security and seed phrase management continue to evolve, with different jurisdictions taking varying approaches to user protection, institutional custody requirements, and liability allocation for cryptocurrency losses. Some regulatory environments impose specific security requirements on cryptocurrency service providers, including standards for key management, backup procedures, and customer education, while others focus on disclosure requirements and risk warnings rather than prescriptive technical standards.
Insurance considerations for seed phrase security involve complex evaluation of coverage terms, exclusions, and claim procedures that may not adequately address the unique risks associated with self-custody cryptocurrency holdings. Traditional insurance products often exclude losses resulting from user error, theft of information, or failure to follow prescribed security procedures, creating gaps in coverage that leave cryptocurrency users exposed to financial losses even when they maintain insurance policies. Specialized cryptocurrency insurance products are emerging to address these gaps, but they often come with significant limitations and high costs that may not be practical for typical users.
Professional custody services and institutional solutions have developed sophisticated approaches to seed phrase security that incorporate advanced cryptographic techniques, multi-party authorization schemes, and comprehensive audit procedures. These solutions often involve hardware security modules, secure enclaves, and distributed key management systems that provide enhanced security for large cryptocurrency holdings while maintaining operational flexibility for institutional requirements. However, these professional solutions typically involve significant costs and complexity that make them impractical for individual users.
Future Developments and Emerging Technologies
Quantum computing resistance represents a critical consideration for long-term seed phrase security, as sufficiently powerful quantum computers could potentially compromise the cryptographic algorithms underlying current seed phrase implementations. Research into post-quantum cryptographic algorithms continues to advance, with various candidate algorithms showing promise for providing security against both classical and quantum attacks. However, the transition to quantum-resistant cryptography will require coordination across the entire cryptocurrency ecosystem and may necessitate seed phrase migration procedures that could create temporary vulnerabilities during the transition period.
Biometric integration technologies are exploring ways to enhance seed phrase security through biological authentication factors that cannot be easily replicated or stolen. These approaches might incorporate fingerprint data, retinal patterns, or other biometric factors into seed phrase generation or recovery procedures, providing additional authentication layers that could improve security against certain attack vectors. However, biometric integration also introduces new vulnerabilities related to biometric data storage, spoofing attacks, and the permanent nature of biological authentication factors that cannot be changed if compromised.
Secure hardware developments continue to advance with new processor features, dedicated cryptocurrency chips, and improved tamper resistance that could enhance seed phrase protection in future wallet implementations. These hardware advances might enable new security models that distribute trust across multiple hardware components, provide enhanced protection against physical attacks, or offer improved usability for complex security procedures. However, hardware security advances also face challenges from evolving attack techniques and the economic constraints of consumer device manufacturing.
Social recovery mechanisms are being developed to provide alternatives to traditional seed phrase backup strategies, allowing users to designate trusted parties who can assist with wallet recovery through cryptographic protocols that protect privacy while enabling assistance. These mechanisms might enable recovery procedures that do not require complete seed phrase disclosure while providing protection against loss scenarios that traditional backup strategies cannot address. However, social recovery also introduces new trust assumptions and attack vectors that must be carefully considered in implementation and adoption decisions.
Explore cutting-edge cryptocurrency analysis and secure trading strategies with TradingView’s comprehensive market data and professional-grade security features.
Conclusion and Actionable Recommendations
Seed phrase security represents the cornerstone of cryptocurrency self-custody, requiring users to implement comprehensive security strategies that address both technical vulnerabilities and human factors. The irreversible nature of cryptocurrency transactions and the lack of centralized recovery mechanisms place the entire burden of security on individual users, making proper seed phrase management essential for long-term cryptocurrency ownership success.
Effective seed phrase security implementation requires a balanced approach that combines multiple storage mediums, geographic distribution, and robust recovery procedures while avoiding common pitfalls such as digital storage vulnerabilities and social engineering susceptibility. Users must develop comprehensive understanding of the trade-offs between different security approaches and implement strategies appropriate to their specific risk profiles and technical capabilities.
The evolving landscape of cryptocurrency security continues to present new challenges and opportunities, from quantum computing threats to advanced hardware security solutions. Users who maintain awareness of emerging developments and adapt their security practices accordingly will be better positioned to protect their cryptocurrency holdings against evolving threat landscapes while taking advantage of improved security technologies as they become available.
Success in seed phrase security ultimately depends on consistent implementation of proven security practices, regular review and testing of recovery procedures, and ongoing education about emerging threats and protective technologies. Users who approach seed phrase security with appropriate seriousness and attention to detail will find that proper implementation provides robust protection for their cryptocurrency holdings while maintaining practical accessibility for legitimate recovery scenarios.
Disclaimer: This article is for educational purposes only and does not constitute financial advice. Cryptocurrency investments carry inherent risks, and users should conduct thorough research and consider their risk tolerance before making investment decisions. The security practices discussed require careful implementation and may not be suitable for all users or situations. Always consult with qualified professionals before implementing complex security procedures or making significant cryptocurrency investments.