TradingView Pine Script Reference
The Critical Foundation of DeFi Security
Smart contract audits have become the cornerstone of security in the decentralized finance ecosystem, representing the difference between a protocol that protects billions of dollars in user funds and one that becomes another cautionary tale in the history of DeFi exploits. As the DeFi space has matured from experimental playground to institutional-grade financial infrastructure, the importance of rigorous security auditing has grown exponentially, with audit reports now serving as essential documentation that investors, users, and institutions rely upon before committing capital to any protocol.
The complexity of modern DeFi protocols, which often involve intricate interactions between multiple smart contracts, cross-chain bridges, yield farming mechanisms, and governance systems, creates numerous attack vectors that require specialized expertise to identify and remediate. Professional audit firms employ teams of security researchers, blockchain developers, and cryptography experts who dedicate weeks or months to thoroughly examining every line of code, testing edge cases, and modeling potential attack scenarios that could compromise protocol security or user funds.
The financial stakes involved in DeFi protocol security cannot be overstated, with total value locked across various protocols exceeding hundreds of billions of dollars at peak market conditions. When vulnerabilities in smart contracts are exploited, the consequences extend far beyond immediate financial losses to include destroyed user confidence, regulatory scrutiny, and long-term damage to the broader DeFi ecosystem’s reputation and adoption prospects.
Understanding the Smart Contract Audit Process
The smart contract audit process represents a comprehensive security assessment that combines automated analysis tools with manual code review, formal verification techniques, and extensive testing methodologies to identify vulnerabilities, inefficiencies, and potential attack vectors within blockchain-based applications. Professional audit firms typically follow structured methodologies that have evolved through years of experience analyzing thousands of smart contracts across various blockchain platforms and use cases.
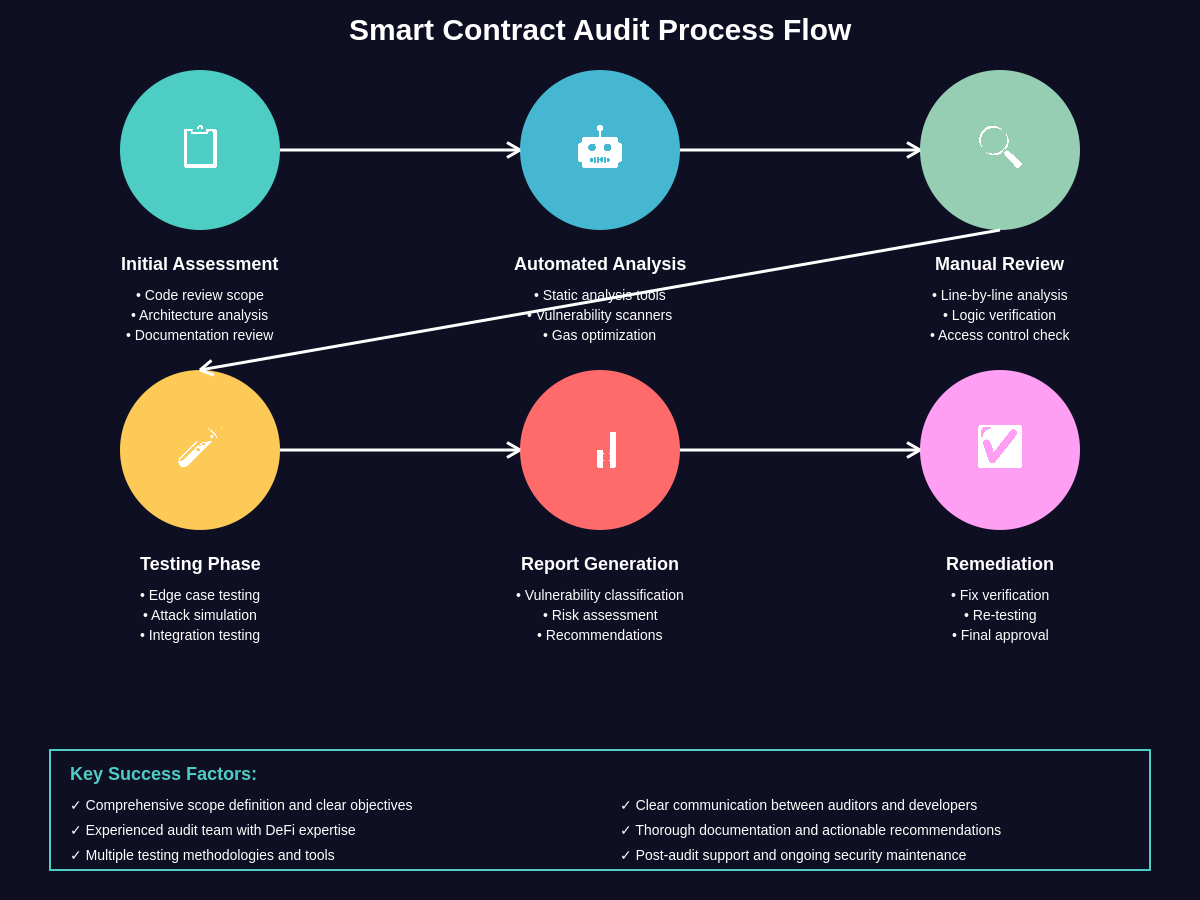
Initial audit phases involve automated scanning using specialized tools designed to detect common vulnerability patterns, including reentrancy attacks, integer overflow conditions, access control failures, and gas optimization opportunities. These automated tools serve as the first line of defense, quickly identifying obvious security issues while allowing human auditors to focus their expertise on more complex logical vulnerabilities and protocol-specific risks that require deep understanding of the intended functionality.
Manual code review represents the most critical component of the audit process, where experienced security researchers examine every function, modifier, and state variable to understand how the contract behaves under various conditions. This process involves tracing execution paths, analyzing function interactions, reviewing access controls, and identifying scenarios where the contract might behave differently than intended by the developers.
The audit process typically includes comprehensive testing of business logic, where auditors create detailed test cases that explore edge conditions, boundary values, and unexpected input combinations that could potentially be exploited by malicious actors. These tests often reveal logical flaws that might not be apparent during normal operation but could be catastrophic when exploited by sophisticated attackers with deep understanding of the protocol mechanics.
Documentation review forms another essential component, where auditors compare the actual code implementation against the intended functionality described in technical specifications, whitepaper documentation, and developer comments. Discrepancies between intended and actual behavior often reveal serious security vulnerabilities or indicate areas where the development team may have misunderstood their own protocol’s operation.
Types of Vulnerabilities Discovered Through Audits
Smart contract audits regularly uncover a wide range of vulnerability types, from simple coding errors to complex economic exploits that could drain entire protocol treasuries. Reentrancy vulnerabilities represent one of the most dangerous and commonly discovered issues, where external contracts can call back into the original contract before state updates are completed, potentially allowing attackers to drain funds through repeated withdrawals or manipulate internal accounting systems.
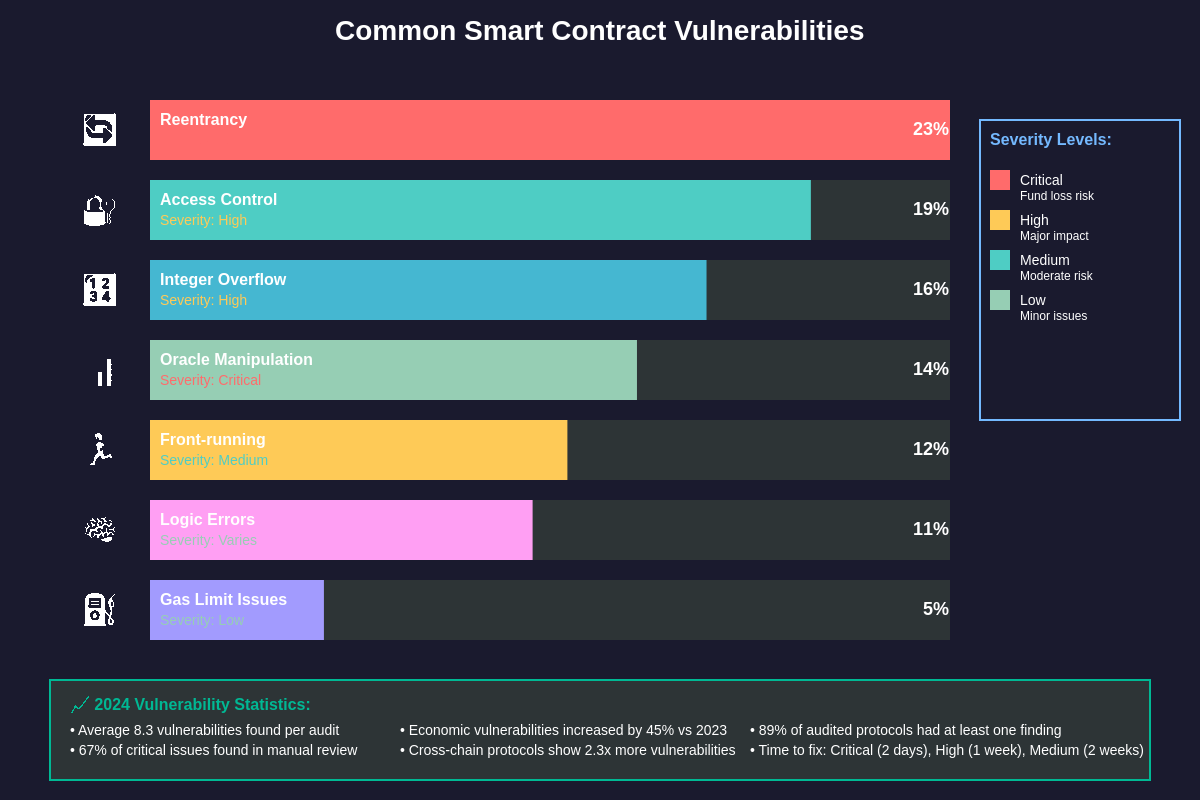
Access control vulnerabilities frequently emerge during audits, particularly in protocols with complex governance mechanisms or multi-role permission systems. These issues can range from functions missing proper access restrictions to subtle privilege escalation bugs where users can gain unauthorized access to administrative functions through carefully crafted transaction sequences.
Integer arithmetic issues, including overflow and underflow conditions, remain prevalent despite improvements in modern programming languages and compiler protections. Smart contract developers often rely on TradingView’s advanced charting capabilities to analyze token price movements and implement mathematical models that can introduce subtle arithmetic vulnerabilities if not properly handled.
Oracle manipulation represents a sophisticated attack vector that audit teams specifically examine, particularly in protocols that rely on external price feeds for critical functionality like liquidations, reward distributions, or collateral valuations. Auditors analyze how protocols handle oracle failures, price deviations, and potential manipulation scenarios where attackers might influence external data sources to their advantage.
Economic vulnerabilities often prove more subtle but equally dangerous, involving flaws in tokenomics, incentive mechanisms, or game theory assumptions that could be exploited to extract value from protocols through legal but unintended means. These might include arbitrage opportunities that consistently drain protocol reserves, governance attacks that allow minority stakeholders to control majority decisions, or reward mechanisms that can be gamed to extract disproportionate value.
Front-running and MEV-related vulnerabilities have become increasingly important as automated trading and maximum extractable value extraction have grown more sophisticated. Auditors examine how protocols handle transaction ordering, whether sensitive operations can be front-run, and if the protocol design inadvertently creates profitable MEV opportunities that could harm regular users.
The Economic Impact of Unaudited Protocols
The financial consequences of deploying unaudited smart contracts in the DeFi ecosystem have been devastating, with billions of dollars lost to exploits that could have been prevented through proper security auditing. High-profile protocol failures serve as stark reminders of the critical importance of thorough security review, demonstrating how single vulnerabilities can instantly destroy projects that took months or years to develop and attracted hundreds of millions in user deposits.
The Poly Network hack of 2021, which resulted in over $600 million in stolen funds, highlighted how cross-chain bridge vulnerabilities can have catastrophic consequences when proper audit procedures are not followed. While the funds were eventually returned due to the attacker’s unexpected cooperation, the incident demonstrated the massive scale of potential losses when complex multi-chain protocols are deployed without adequate security review.
Smaller protocols face even greater risks from security vulnerabilities, as they typically lack the resources for comprehensive incident response, user compensation, or platform recovery that larger projects might manage. A single successful exploit can completely destroy a smaller protocol’s credibility and user base, making audit costs seem minimal compared to the potential consequences of deployment without proper security verification.
Insurance protocols and risk assessment platforms increasingly require comprehensive audit documentation before providing coverage or favorable risk ratings, making audits not just security measures but essential business requirements for protocols seeking institutional adoption or professional risk management services. Market analysis platforms like TradingView help investors evaluate protocol security through various metrics, but audit reports remain the primary source of security assurance.
The cascading effects of major protocol hacks extend beyond immediate financial losses to include reduced confidence in the broader DeFi ecosystem, increased regulatory scrutiny, and heightened investor caution that can negatively impact innovation and adoption across the entire sector. These systemic risks make protocol security a shared responsibility that affects all participants in the DeFi ecosystem.
Leading Audit Firms and Their Methodologies
The smart contract auditing industry has evolved to include numerous specialized firms, each developing unique methodologies and expertise areas that address different aspects of protocol security. Established firms like ConsenSys Diligence, Trail of Bits, and OpenZeppelin have built reputations through years of successful audits and have developed comprehensive frameworks that combine automated tools, manual review processes, and specialized testing techniques.
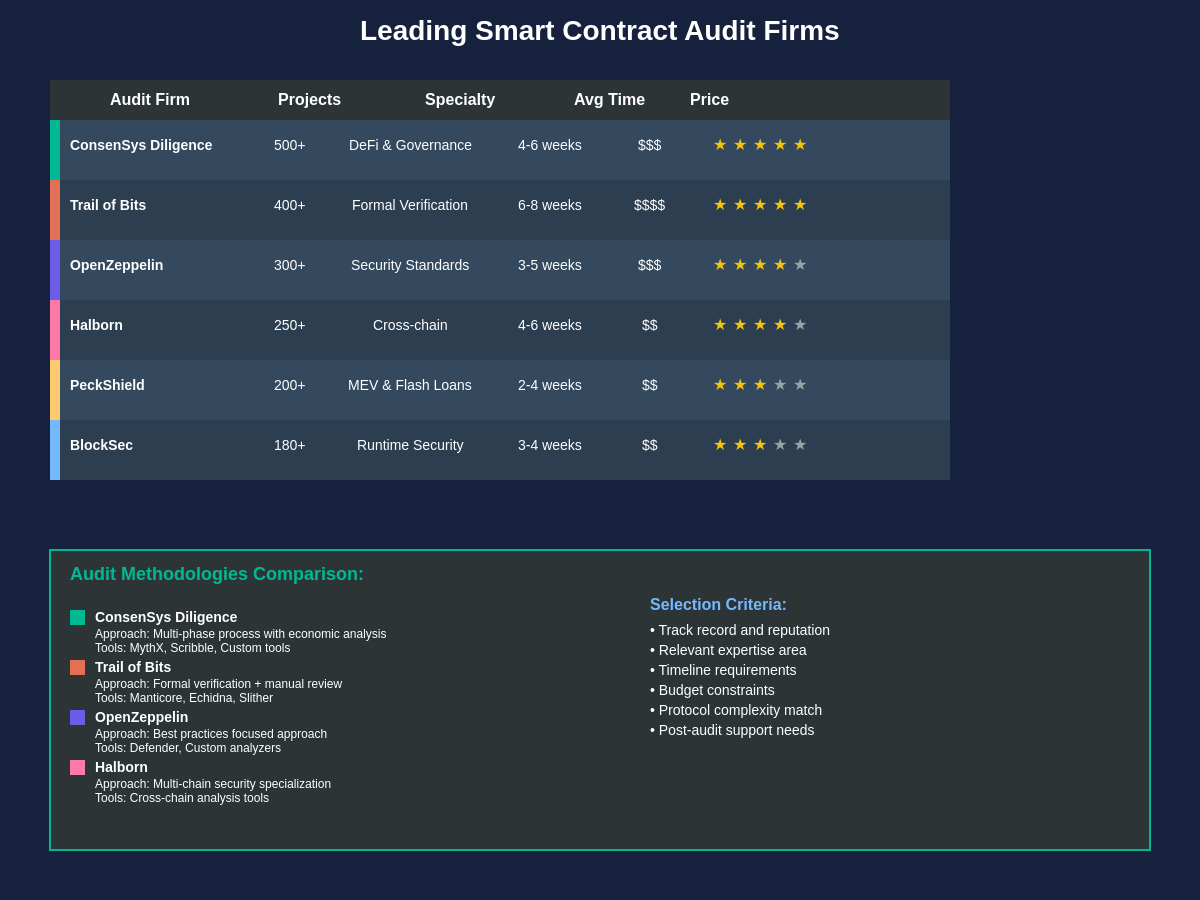
ConsenSys Diligence employs a multi-phase approach that begins with automated vulnerability scanning using proprietary tools before progressing to detailed manual code review and concluding with comprehensive testing of identified issues. Their methodology emphasizes understanding protocol economics and game theory implications alongside traditional security concerns, recognizing that DeFi protocols face unique risks related to economic incentives and user behavior.
Trail of Bits brings a formal verification approach to smart contract auditing, utilizing mathematical proofs and symbolic execution techniques to verify contract properties and identify edge cases that might not be apparent through traditional testing methods. Their approach is particularly valuable for protocols with complex mathematical operations or critical security requirements where formal guarantees of correctness are essential.
OpenZeppelin leverages their extensive experience developing security libraries and standards to provide audits that focus on best practices, code quality, and long-term maintainability alongside immediate security concerns. Their audit process includes detailed recommendations for improving code architecture and implementing established security patterns that can prevent future vulnerabilities.
Newer audit firms like Halborn, BlockSec, and PeckShield have emerged to address the growing demand for audit services, each developing specialized expertise in areas like cross-chain protocols, MEV-related vulnerabilities, or specific blockchain platforms. The competition between audit firms has driven improvements in methodology, turnaround times, and the comprehensiveness of audit reports.
The audit industry has also seen the emergence of automated audit platforms and bug bounty programs that complement traditional audit services by providing continuous security monitoring and incentivizing ongoing vulnerability discovery. These platforms use machine learning and static analysis techniques to identify potential issues while offering rewards for security researchers who discover and responsibly disclose vulnerabilities.
Audit Report Analysis and Interpretation
Understanding how to properly interpret audit reports has become a critical skill for DeFi participants, as these documents contain essential information about protocol security but require technical expertise to fully comprehend. Professional audit reports typically include executive summaries for non-technical stakeholders, detailed technical findings with severity classifications, and recommendations for addressing identified issues.
Severity classifications in audit reports generally follow standardized frameworks that categorize vulnerabilities as critical, high, medium, or low risk based on factors including potential impact, likelihood of exploitation, and difficulty of remediation. Critical and high-severity findings typically indicate vulnerabilities that could result in significant fund loss or protocol compromise and require immediate attention before protocol deployment or continued operation.
The status of audit findings represents crucial information that often gets overlooked by protocol users and investors. Findings marked as “acknowledged” or “fixed” indicate different levels of risk mitigation, with fixed issues having been addressed through code changes that were verified by auditors, while acknowledged issues may remain in the codebase with team acceptance of the associated risks.
Audit report disclaimers and limitations require careful attention, as they define the scope of the audit engagement and clarify what aspects of the protocol were and were not examined. Some audits focus only on specific contract components or exclude certain types of vulnerabilities from their scope, meaning that an audit report does not guarantee comprehensive security coverage of the entire protocol.
The timing of audit reports relative to protocol deployment and updates also affects their relevance, as changes made after audit completion can introduce new vulnerabilities or invalidate previous security assessments. Protocols that undergo frequent updates or implement new features after audit completion may require ongoing security review to maintain their security posture.
Multiple audit approaches, where protocols engage several independent audit firms, have become increasingly common for high-value projects seeking maximum security assurance. Comparing findings across multiple audit reports can reveal inconsistencies in auditor approaches or identify vulnerabilities that some teams might have missed during their review process.
The Role of Formal Verification in Smart Contract Security
Formal verification represents the most rigorous approach to smart contract security, utilizing mathematical proofs to verify that contracts behave according to their specifications under all possible conditions. This approach goes beyond traditional testing and code review by providing mathematical guarantees about contract behavior, making it particularly valuable for protocols handling large amounts of value or implementing critical financial infrastructure.
The formal verification process involves creating mathematical models of smart contract behavior and proving properties about these models using automated theorem provers and proof assistants. This approach can definitively prove the absence of certain types of vulnerabilities rather than simply testing for their presence, providing a higher level of security assurance than traditional audit methods.
Specification development represents a critical challenge in formal verification, as the mathematical properties being verified must accurately capture the intended behavior of the smart contract. Incomplete or incorrect specifications can lead to verified contracts that still contain serious vulnerabilities, making the specification development process as important as the verification itself.
Tool limitations in formal verification mean that this approach is most effective when combined with traditional audit methods rather than used as a complete replacement. Current formal verification tools excel at proving certain types of properties, particularly those related to arithmetic operations and state transitions, but may struggle with complex interactions or protocol-level behaviors that span multiple contracts.
Cost and time considerations make formal verification most practical for critical protocol components rather than comprehensive verification of entire DeFi systems. Many protocols adopt hybrid approaches where core security-critical functions undergo formal verification while broader protocol functionality receives traditional audit coverage.
The integration of formal verification with traditional development workflows remains an active area of research and development, with new tools and methodologies emerging to make formal methods more accessible to smart contract developers and audit teams.
Economic Models and Audit Pricing
The economics of smart contract auditing reflect the high value of security expertise and the significant liability that audit firms assume when providing security assessments for protocols handling millions or billions of dollars in user funds. Audit pricing typically depends on factors including code complexity, protocol value, timeline requirements, and the reputation and expertise of the audit firm.
Code complexity metrics influence audit pricing significantly, with more complex protocols requiring additional time for auditors to understand functionality, trace execution paths, and identify potential vulnerabilities. Protocols implementing novel mechanisms, cross-chain functionality, or complex governance systems typically command higher audit fees due to the specialized expertise required for their assessment.
Timeline considerations affect audit costs, with expedited audits commanding premium pricing due to the need to allocate additional resources and potentially prioritize one engagement over others. However, rushed audits may compromise quality, creating a tension between time-to-market pressures and security thoroughness that protocol teams must carefully balance.
Audit firm reputation and track record influence pricing structures, with established firms typically charging premium rates based on their proven expertise and the insurance value their reputations provide to protocol teams. The audit firm’s name on a security report can significantly influence investor and user confidence, making the reputation premium a worthwhile investment for many protocols.
Multiple audit strategies have become common for high-value protocols, with teams engaging several independent audit firms to maximize security coverage and demonstrate commitment to security best practices. While this approach significantly increases costs, it can provide better security outcomes and stronger user confidence that justify the additional investment.
Ongoing security relationships between protocols and audit firms have emerged as an alternative to traditional one-time audit engagements, with firms providing continuous security monitoring, rapid response for critical updates, and ongoing consultation throughout protocol evolution. These relationships can provide better security outcomes while potentially reducing long-term costs through improved efficiency and deeper protocol understanding.
Post-Audit Security Maintenance
The completion of a smart contract audit represents the beginning rather than the end of a protocol’s security journey, as maintaining security requires ongoing attention to code updates, emerging threat vectors, and evolving best practices. Post-audit security maintenance involves implementing processes for managing code changes, monitoring for new vulnerabilities, and responding to security incidents that may arise despite thorough initial auditing.
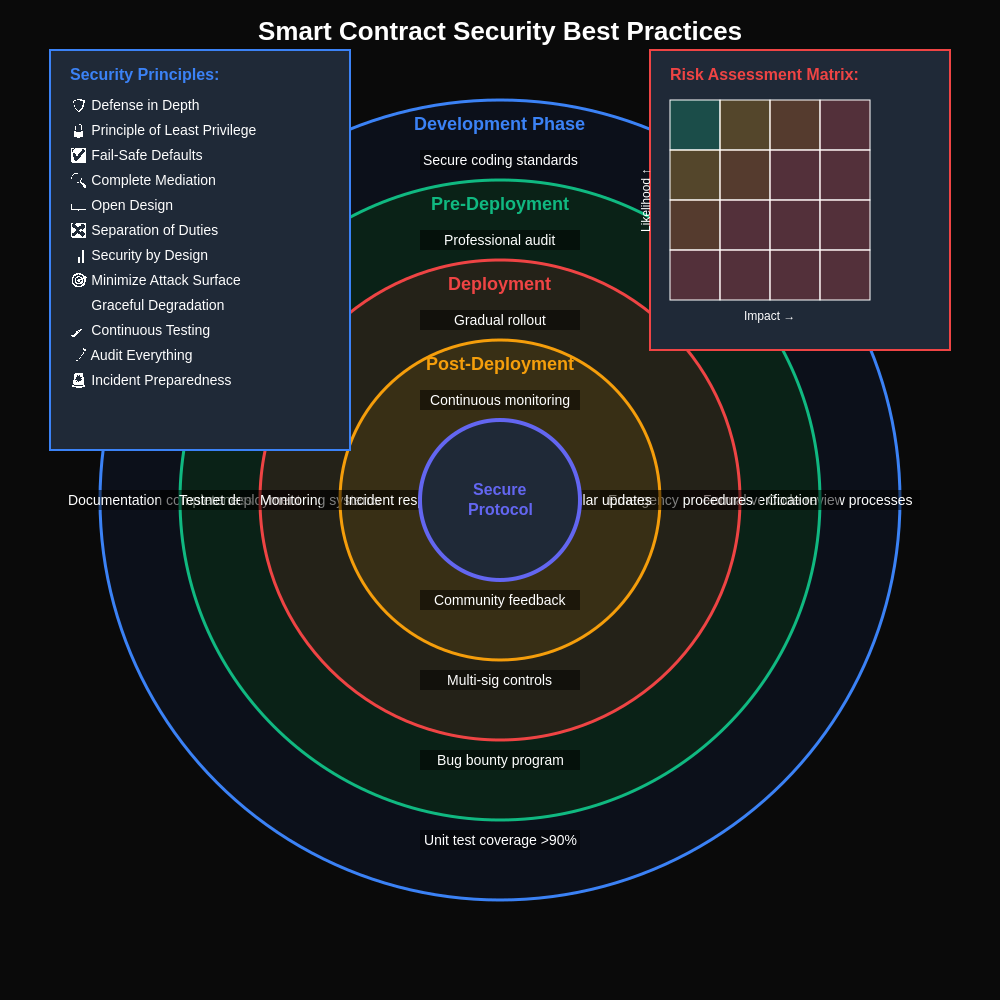
Code change management becomes critical after audit completion, as any modifications to audited smart contracts can potentially introduce new vulnerabilities or invalidate previous security assessments. Effective post-audit processes include security review requirements for all code changes, automated testing frameworks that verify security properties, and clear procedures for determining when additional audit work is required.
Monitoring and incident response capabilities enable protocol teams to detect and respond to security threats that may emerge after deployment, including zero-day vulnerabilities, economic attacks, or exploitation attempts that might not have been anticipated during initial auditing. These capabilities often involve real-time monitoring of contract interactions, automated alerting systems, and predefined response procedures for various threat scenarios.
Bug bounty programs represent an important component of ongoing security maintenance, providing continuous incentives for security researchers to identify and responsibly disclose vulnerabilities that may have been missed during initial auditing or introduced through subsequent updates. Effective bug bounty programs require clear scope definitions, appropriate reward structures, and efficient processes for evaluating and addressing reported vulnerabilities.
Security update procedures must balance the need for rapid response to critical vulnerabilities with the importance of maintaining protocol stability and user confidence. Protocols typically implement governance mechanisms or emergency response procedures that enable rapid deployment of security fixes while maintaining appropriate oversight and transparency about changes being made.
Community security engagement involves educating users about security best practices, maintaining transparency about protocol security status, and building relationships with security researchers and other protocols that can provide early warning about emerging threats or vulnerabilities that might affect multiple projects in the ecosystem.
Advanced market analysis tools on TradingView help security teams monitor unusual trading patterns or market movements that might indicate exploitation attempts or other security incidents requiring immediate response.
Future Trends in Smart Contract Auditing
The smart contract auditing industry continues to evolve rapidly, driven by advances in automated analysis tools, formal verification techniques, and the growing sophistication of both protocols and attack methods. Machine learning and artificial intelligence are beginning to play larger roles in vulnerability detection, with researchers developing models that can identify subtle patterns indicative of security vulnerabilities that might be missed by traditional analysis methods.
Automated audit tools are becoming more sophisticated and comprehensive, potentially reducing the time and cost required for security assessments while improving the consistency and thoroughness of vulnerability detection. However, these tools remain complementary to human expertise rather than replacements, as complex protocol logic and economic considerations require human understanding and judgment.
Cross-chain and multi-chain protocol security presents new challenges for audit firms, requiring expertise in multiple blockchain platforms, bridge security, and the complex interactions that can arise when protocols operate across different ecosystems. The growing importance of cross-chain functionality is driving the development of specialized audit methodologies and tools designed specifically for these complex environments.
Real-time security monitoring and continuous auditing approaches are emerging as alternatives or supplements to traditional point-in-time audit engagements, providing ongoing security assessment that can adapt to protocol changes and emerging threats. These approaches leverage automated analysis tools and machine learning to provide continuous security insights while reducing the latency between code changes and security assessment.
Regulatory developments are likely to influence audit practices and requirements, particularly as traditional financial regulators develop frameworks for DeFi protocols and institutional adoption increases. Regulatory requirements for security assessments could standardize audit practices while potentially increasing costs and complexity for protocol teams.
The integration of audit findings with protocol governance systems represents an emerging trend that could automate certain aspects of vulnerability response and security maintenance, enabling protocols to automatically implement security fixes or parameter changes based on audit recommendations and community governance decisions.
Conclusion
Smart contract audits have evolved from optional security measures to essential requirements for any serious DeFi protocol seeking to protect user funds and maintain long-term viability in an increasingly competitive and sophisticated ecosystem. The comprehensive security assessment provided by professional audit firms represents the current gold standard for identifying vulnerabilities, validating protocol security assumptions, and providing the documentation necessary for institutional adoption and user confidence.
The economic impact of proper security auditing extends far beyond the immediate costs of engaging audit firms, encompassing the protection of user funds, maintenance of protocol reputation, and contribution to the overall health and maturity of the DeFi ecosystem. As the industry continues to evolve toward greater institutional adoption and regulatory clarity, the importance of thorough security auditing will only continue to grow.
The future of smart contract auditing will likely involve greater automation, more sophisticated analysis techniques, and deeper integration with protocol development and governance processes. However, the fundamental importance of expert human review and the critical role that audit firms play in maintaining DeFi security will remain central to the ecosystem’s continued growth and success.
Protocol teams, investors, and users who understand the importance of comprehensive security auditing and know how to interpret audit results will be better positioned to navigate the complex DeFi landscape while avoiding the devastating consequences that can result from inadequate security practices. The investment in proper security auditing represents not just a cost of doing business but a fundamental requirement for building sustainable and trustworthy decentralized financial infrastructure.
Professional traders and analysts use TradingView’s comprehensive platform to monitor protocol security events and their market impact, understanding that audit announcements and security incidents can significantly influence token prices and protocol adoption rates.
Disclaimer: This article is for educational purposes only and does not constitute financial advice. Smart contract audits, while important, do not guarantee protocol security or eliminate all risks associated with DeFi participation. Always conduct thorough research and consider consulting with financial professionals before making investment decisions in the cryptocurrency space. Past performance does not indicate future results, and all cryptocurrency investments carry significant risk of loss.