The digital age has brought unprecedented connectivity and transparency, but it has also exposed the fragility of personal privacy in our interconnected world. As blockchain technology continues to reshape industries and redefine how we think about trust and verification, one revolutionary concept stands at the forefront of protecting individual privacy while maintaining the integrity that makes distributed systems so powerful. Zero-knowledge proofs represent a paradigm shift in cryptographic thinking, offering a solution to one of the most challenging problems in computer science: how to prove you know something without revealing what you know.
The Mathematical Foundation of Privacy
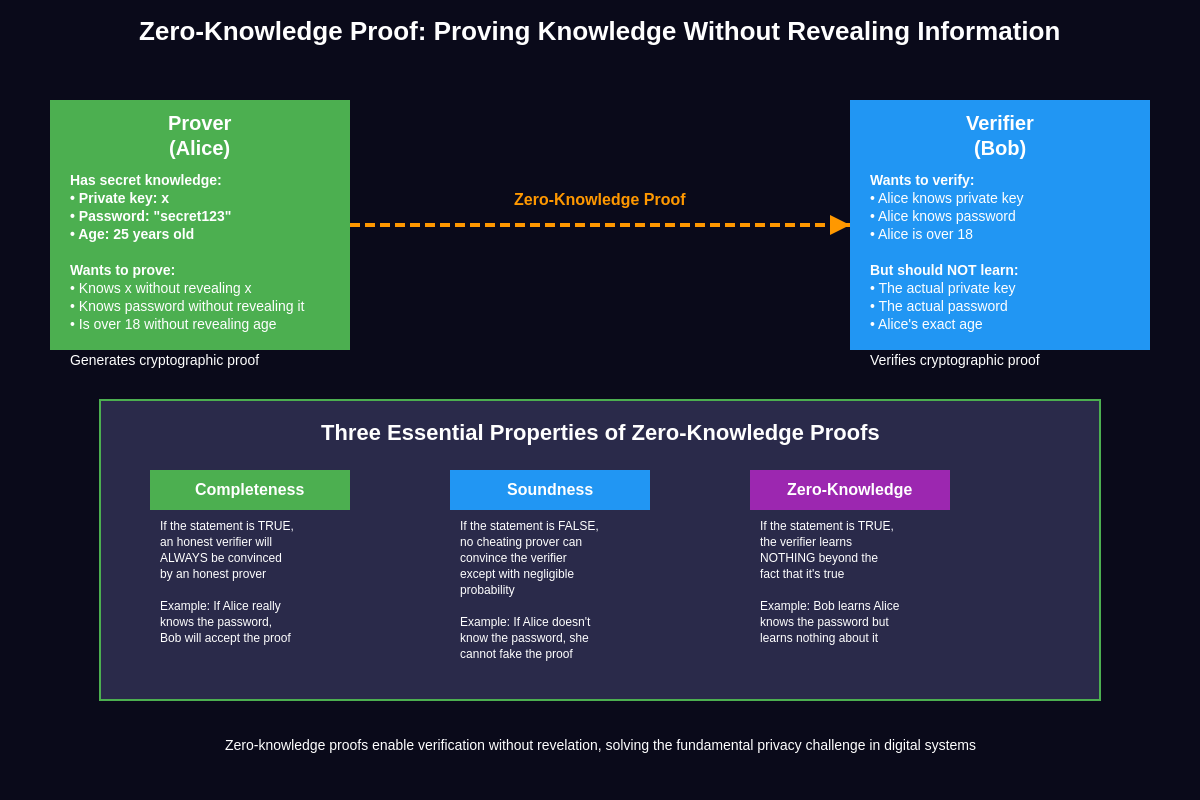
Zero-knowledge proofs emerged from the theoretical computer science research of the 1980s, when Shafi Goldwasser, Silvio Micali, and Charles Rackoff introduced the concept that would fundamentally change how we think about privacy and verification. At its core, a zero-knowledge proof is a cryptographic method that allows one party, known as the prover, to demonstrate to another party, called the verifier, that they possess knowledge of a specific piece of information without revealing the information itself. This mathematical impossibility became reality through sophisticated cryptographic protocols that have evolved into practical implementations powering today’s privacy-focused blockchain applications.
The elegance of zero-knowledge proofs lies in their ability to satisfy three critical properties simultaneously. Completeness ensures that if the statement being proved is true, an honest verifier will be convinced by an honest prover. Soundness guarantees that if the statement is false, no cheating prover can convince the honest verifier except with negligible probability. Most importantly, the zero-knowledge property ensures that if the statement is true, the verifier learns nothing beyond the fact that the statement is indeed true. These properties create a cryptographic framework that enables verification without revelation, opening possibilities that seemed impossible just decades ago.
The mathematical foundations underlying zero-knowledge proofs draw from various areas of advanced mathematics and computer science, including number theory, algebraic geometry, and computational complexity theory. Interactive proof systems form the backbone of many zero-knowledge constructions, where the prover and verifier engage in a protocol of challenges and responses that gradually build confidence in the truth of a statement without exposing the underlying secrets. The development of non-interactive zero-knowledge proofs, which eliminate the need for back-and-forth communication, has been particularly crucial for blockchain applications where efficiency and scalability are paramount concerns.
Modern zero-knowledge proof systems leverage sophisticated mathematical constructs such as elliptic curves, polynomial commitments, and cryptographic hash functions to create protocols that are both secure and practical. The evolution from theoretical possibility to real-world implementation required breakthroughs in algorithmic efficiency, proof generation speed, and verification costs. Today’s zkSNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge) and zkSTARKs (Zero-Knowledge Scalable Transparent Arguments of Knowledge) represent the culmination of decades of research, offering different trade-offs between setup requirements, proof sizes, and computational overhead.
Privacy Challenges in Traditional Blockchain Systems
Traditional blockchain architectures, exemplified by Bitcoin and early Ethereum implementations, operate on a foundation of radical transparency that serves the dual purpose of enabling trustless verification and maintaining network security. Every transaction, every balance, and every interaction is recorded immutably on a public ledger that anyone can inspect, analyze, and trace. While this transparency solved the fundamental problem of achieving consensus in a decentralized environment without trusted authorities, it created entirely new challenges related to financial privacy, commercial confidentiality, and personal security that have become increasingly problematic as blockchain adoption has grown.
The transparency inherent in public blockchains means that sophisticated blockchain analysis techniques can reveal patterns, connections, and behaviors that users never intended to make public. Professional traders tracking cryptocurrency market movements and privacy coin adoption understand that transaction graph analysis can link addresses to real-world identities, expose business relationships, reveal trading strategies, and compromise competitive advantages that companies have spent years developing. Financial institutions, corporations, and individuals all face similar privacy challenges when operating in transparent blockchain environments.
The pseudonymous nature of most blockchain systems provides only a thin veneer of privacy that sophisticated adversaries can easily penetrate. Address clustering algorithms can group multiple addresses belonging to the same entity, temporal analysis can reveal activity patterns, and correlation attacks can link blockchain transactions to off-chain activities. The immutable nature of blockchain records means that privacy breaches have permanent consequences, creating risks that compound over time as analysis techniques become more sophisticated and datasets become more comprehensive.
Commercial applications of blockchain technology face particularly acute privacy challenges. Supply chain tracking, cross-border payments, and enterprise resource planning all require some level of confidentiality to protect competitive advantages, comply with regulations, and maintain customer trust. The all-or-nothing transparency of traditional blockchains forces organizations to choose between the benefits of decentralized systems and the privacy requirements of their business models. This fundamental tension has limited blockchain adoption in many sectors where privacy is not just preferred but legally required.
Regulatory frameworks around the world increasingly recognize privacy as a fundamental right, with legislation such as the General Data Protection Regulation in Europe and similar privacy laws in other jurisdictions creating legal requirements that traditional transparent blockchains cannot satisfy. The right to be forgotten, data minimization principles, and consent-based data processing all conflict with the permanent, transparent nature of traditional blockchain systems. These regulatory challenges have created a pressing need for privacy-preserving blockchain technologies that can deliver the benefits of decentralization while meeting evolving legal and social expectations around data protection.
Fundamental Types of Zero-Knowledge Proof Systems
The landscape of zero-knowledge proof systems encompasses several distinct approaches, each offering different trade-offs between efficiency, security assumptions, and practical applicability. Interactive zero-knowledge proofs represent the original formulation of the concept, requiring real-time communication between prover and verifier through multiple rounds of challenges and responses. While theoretically elegant and offering strong security guarantees under minimal assumptions, interactive proofs present practical challenges in blockchain environments where asynchronous operation and permanent verification are essential requirements.
Non-interactive zero-knowledge proofs eliminate the need for back-and-forth communication by allowing provers to generate self-contained proofs that verifiers can check independently at any time. This transformation from interactive to non-interactive systems required significant theoretical advances, particularly the development of the common reference string model and the Fiat-Shamir heuristic, which enables the conversion of interactive protocols into non-interactive ones through cryptographic hash functions. Non-interactive proofs are particularly well-suited to blockchain applications where proofs must be included in transactions and verified by multiple network participants without coordination.
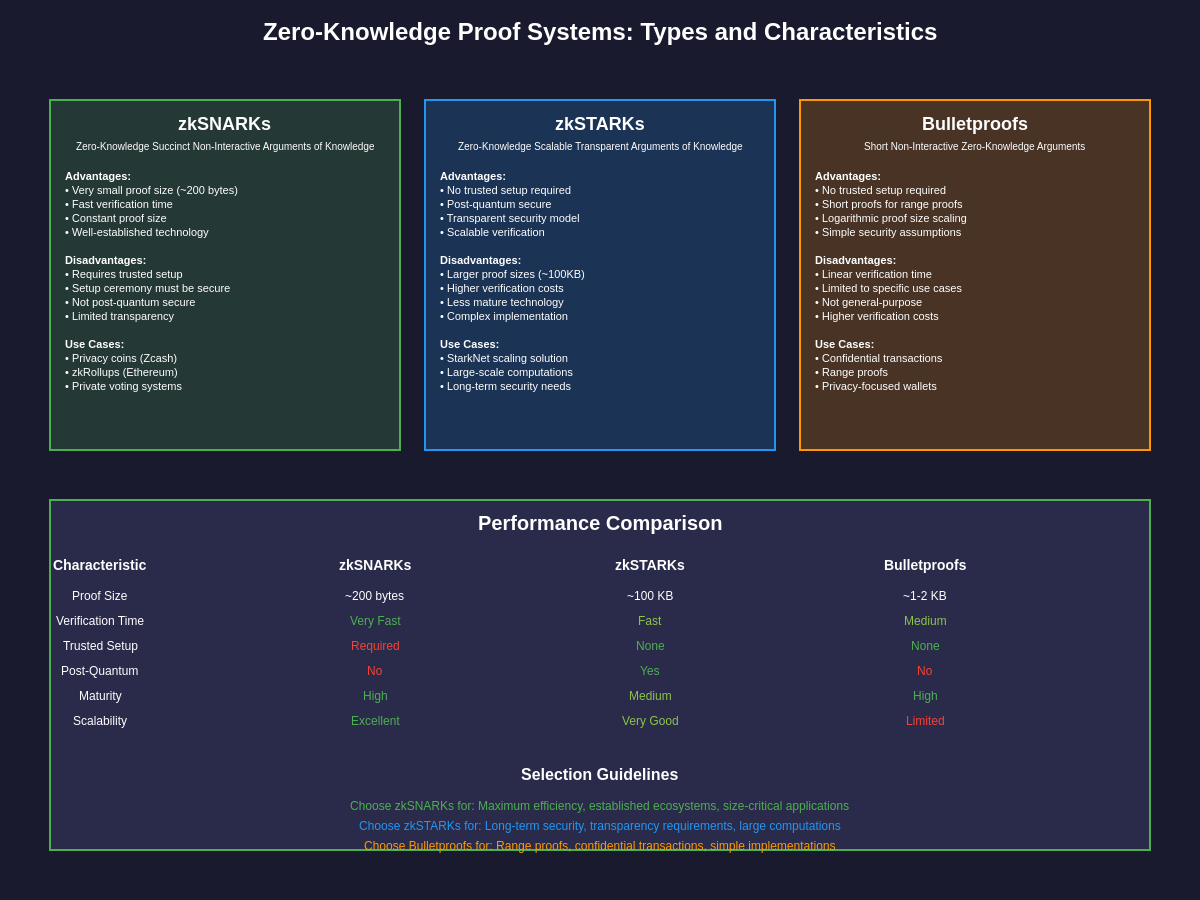
zkSNARKs have emerged as one of the most practically important categories of zero-knowledge proof systems, offering succinct proofs that remain constant in size regardless of the complexity of the statement being proved. The “succinct” property is crucial for blockchain applications where proof sizes directly impact transaction costs and network scalability. However, zkSNARKs typically require a trusted setup ceremony to generate proving and verification keys, creating potential security vulnerabilities if the setup process is compromised. Different zkSNARK constructions, including Groth16, PLONK, and Marlin, offer various improvements in efficiency, universal setup requirements, and proof composition capabilities.
zkSTARKs represent an alternative approach that eliminates the need for trusted setup ceremonies by relying purely on cryptographic hash functions for their security. While zkSTARK proofs are generally larger than zkSNARK proofs, they offer several advantages including transparency in their security assumptions, post-quantum security, and better scalability characteristics for very large computations. The trade-off between proof size and setup requirements makes zkSTARKs particularly attractive for applications where transparency and long-term security are more important than minimizing proof overhead.
Bulletproofs occupy a unique position in the zero-knowledge proof landscape by offering short proofs without requiring trusted setup ceremonies, though they require more computational effort for verification compared to zkSNARKs. Originally developed for confidential transactions in cryptocurrency systems, Bulletproofs have found applications in range proofs, membership proofs, and other scenarios where moderate proof sizes are acceptable and trusted setup is undesirable. The logarithmic scaling of Bulletproof verification costs makes them particularly suitable for applications involving many small proofs rather than single large computations.
Blockchain Integration and Technical Implementation
The integration of zero-knowledge proofs into blockchain systems requires careful consideration of multiple technical factors including proof generation costs, verification efficiency, storage requirements, and network bandwidth constraints. Successful implementations must balance the privacy benefits of zero-knowledge proofs against the computational and economic costs of generating and verifying proofs within the constraints of decentralized networks where resources are limited and coordination is challenging.
Proof generation represents one of the most significant technical challenges in zero-knowledge blockchain systems. Creating proofs for complex statements can require substantial computational resources and specialized hardware, potentially creating barriers to adoption and introducing centralization pressures if only well-resourced participants can efficiently generate proofs. Modern proof systems have made significant strides in improving generation efficiency through algorithmic optimizations, specialized hardware acceleration, and parallelization techniques, but proof generation remains orders of magnitude more expensive than traditional cryptographic operations.
Verification efficiency is equally critical for blockchain integration since every network participant must be able to verify proofs independently without relying on trusted third parties. The asymmetric nature of zero-knowledge proof systems, where verification is much faster than proof generation, makes them well-suited to blockchain environments where many nodes must verify the same proof. However, even fast verification operations can become bottlenecks when multiplied across thousands of network participants and numerous transactions per block.
Storage and bandwidth considerations play crucial roles in determining the practical viability of zero-knowledge proof systems in blockchain applications. Proof sizes directly impact transaction fees, block space utilization, and network synchronization costs. The most successful blockchain implementations of zero-knowledge proofs have focused heavily on minimizing proof sizes through advanced cryptographic techniques and careful system design. Investors analyzing privacy-focused blockchain projects and their technical implementations recognize that proof size optimization often determines the commercial viability of zero-knowledge systems.
Smart contract integration presents additional complexity layers as zero-knowledge proofs must interoperate with existing blockchain infrastructure and programming models. Different blockchain platforms have taken varying approaches to zero-knowledge integration, from native protocol support to smart contract-based implementations to entirely new blockchain architectures designed around zero-knowledge primitives. The choice of integration approach significantly impacts performance, security, and developer accessibility, influencing the types of applications that can practically leverage zero-knowledge technologies.
Privacy Coins and Anonymous Transactions
Privacy-focused cryptocurrencies represent the most mature and widely deployed applications of zero-knowledge proof technology in blockchain systems. These digital assets demonstrate how cryptographic privacy techniques can be integrated into monetary systems while maintaining the essential properties of decentralization, security, and programmability that make blockchain-based currencies viable alternatives to traditional financial systems.
Zcash pioneered the mainstream adoption of zero-knowledge proofs in cryptocurrency through its implementation of zkSNARKs for transaction privacy. The Zcash protocol enables fully shielded transactions where transaction amounts, sender addresses, and recipient addresses are cryptographically hidden while still allowing network participants to verify that transactions are valid and funds are not being created or destroyed improperly. This breakthrough demonstrated that strong cryptographic privacy could be achieved without sacrificing the security or decentralization properties that make cryptocurrencies valuable.
The technical architecture of Zcash illustrates the complexity and sophistication required to implement zero-knowledge privacy in production cryptocurrency systems. The protocol maintains both transparent and shielded address types, allowing users to choose their desired level of privacy and enabling interoperability with systems that require transaction transparency. Shielded transactions use zkSNARKs to prove that the transaction is valid without revealing any details about the amounts or addresses involved, while transparent transactions operate similarly to Bitcoin with full public visibility.
Monero takes a different approach to transaction privacy through a combination of ring signatures, stealth addresses, and confidential transactions that obscure different aspects of transaction data. While not strictly a zero-knowledge proof system, Monero’s privacy techniques achieve similar privacy goals through different cryptographic methods. Ring signatures hide the true sender among a group of possible senders, stealth addresses prevent recipients from being identified, and confidential transactions hide transaction amounts while allowing network validation.
The ecosystem of privacy coins has expanded to include numerous projects exploring different approaches to transaction privacy, each making different trade-offs between privacy strength, performance, regulatory compliance, and usability. Some projects focus on optional privacy features that users can enable when needed, while others implement privacy by default to ensure all transactions receive protection. The diversity of approaches reflects the complex technical and social challenges involved in balancing privacy with other system requirements.
Decentralized Identity and Authentication
Zero-knowledge proofs are revolutionizing digital identity systems by enabling individuals to prove attributes about themselves without revealing unnecessary personal information. Traditional identity verification systems require individuals to disclose far more information than necessary for most verification purposes, creating privacy risks and enabling surveillance that undermines personal autonomy. Zero-knowledge identity systems allow people to prove they meet specific criteria without exposing the underlying data that establishes those criteria.
Age verification represents a compelling example of zero-knowledge identity applications. Rather than requiring individuals to share their exact birth date, address, and other personal information contained in government-issued identification documents, zero-knowledge systems can prove that someone is above a certain age threshold without revealing any additional details. This selective disclosure capability extends to numerous other attributes including citizenship status, professional qualifications, financial standing, and membership in various organizations.
Credential verification systems built on zero-knowledge proofs enable new models of trust and reputation that operate without centralized authorities or comprehensive data collection. Individuals can accumulate cryptographic credentials from various issuers and selectively disclose specific attributes as needed without creating comprehensive profiles that can be tracked across different contexts. This architecture supports privacy-preserving reputation systems where individuals can demonstrate their trustworthiness without exposing their complete history or personal details.
Educational credentials, professional certifications, and specialized qualifications can all be represented as zero-knowledge proofs that allow individuals to demonstrate their achievements without revealing potentially sensitive information about their educational institutions, graduation dates, or specific scores. This approach is particularly valuable for individuals whose educational backgrounds might expose them to discrimination or unwanted attention while still allowing them to prove their qualifications for opportunities that require specific credentials.
The integration of zero-knowledge identity systems with blockchain technology creates opportunities for decentralized autonomous organizations, voting systems, and governance mechanisms that operate on verified but pseudonymous participation. Participants can prove they meet eligibility requirements for voting or participation without revealing their real-world identities, enabling new forms of democratic participation that protect individual privacy while maintaining system integrity.
Scalability Solutions and Layer 2 Networks
Zero-knowledge proofs have emerged as a cornerstone technology for blockchain scalability solutions, offering a path to dramatically increase transaction throughput while maintaining the security and decentralization properties that make blockchain systems valuable. Layer 2 scaling solutions leverage zero-knowledge proofs to compress large batches of transactions into single proofs that can be verified efficiently by the underlying blockchain, achieving scalability improvements of several orders of magnitude compared to direct on-chain execution.
zkRollups represent the most prominent application of zero-knowledge proofs to blockchain scalability challenges. These systems execute transactions off-chain in specialized environments optimized for performance, then generate zero-knowledge proofs that attest to the validity of entire batches of transactions. The underlying blockchain only needs to verify the proof rather than executing each transaction individually, dramatically reducing computational costs and increasing transaction throughput while maintaining the same security guarantees as direct on-chain execution.
The technical architecture of zkRollup systems involves sophisticated coordination between off-chain execution environments, proof generation systems, and on-chain verification contracts. Transactions are collected into batches, executed in specialized virtual machines designed for efficient proof generation, and compressed into single proofs that represent the validity of the entire batch. Advanced traders utilizing layer 2 scaling solutions and zkRollup protocols benefit from dramatically lower transaction costs and faster settlement times while maintaining the security of the underlying layer 1 blockchain.
Data availability represents a critical challenge for zero-knowledge scaling solutions since the underlying blockchain must be able to reconstruct the system state even if off-chain components become unavailable. Different zkRollup implementations take varying approaches to data availability, from storing complete transaction data on-chain to using data availability sampling techniques that reduce storage requirements while maintaining recoverability guarantees. The choice of data availability solution significantly impacts the cost, security, and decentralization properties of the scaling system.
Proof aggregation and recursive proof composition techniques enable zkRollup systems to achieve even greater scalability by combining multiple proofs into single aggregate proofs that represent the validity of numerous transaction batches. This recursive approach allows for theoretically unlimited scalability improvements, though practical considerations around proof generation costs and complexity currently limit the depth of recursion that can be achieved efficiently. Future developments in proof system efficiency and specialized hardware may enable more aggressive aggregation strategies.
Smart Contract Privacy and Confidential Computing
The integration of zero-knowledge proofs with smart contract platforms opens new possibilities for confidential computing applications where sensitive business logic, proprietary algorithms, and confidential data can be processed on public blockchains without revealing implementation details or intermediate computational states. This capability is transforming how organizations think about leveraging blockchain technology for applications that require both transparency and confidentiality.
Private smart contracts enable organizations to automate business processes on public blockchains while protecting confidential information from competitors, regulators, and other parties who should not have access to sensitive details. Zero-knowledge proofs allow these contracts to prove they executed correctly according to predefined rules without revealing the inputs, intermediate calculations, or specific outcomes that might compromise business advantages or violate privacy requirements.
Auction systems represent compelling applications for zero-knowledge smart contracts since traditional auction mechanisms often require participants to reveal their bidding strategies or accept information asymmetries that compromise fairness. Zero-knowledge auction contracts can prove that auctions were conducted fairly and according to specified rules without revealing individual bids until appropriate disclosure times, enabling new auction formats that better protect participant privacy while maintaining transparency around process integrity.
Supply chain applications benefit significantly from zero-knowledge smart contracts that can verify compliance with quality standards, ethical sourcing requirements, and regulatory constraints without exposing proprietary information about suppliers, manufacturing processes, or business relationships. Companies can prove they meet certification requirements or sustainability commitments without revealing competitive information that might benefit rivals or expose vulnerabilities in their operations.
Financial derivatives and complex financial instruments can be implemented as zero-knowledge smart contracts that prove compliance with regulatory requirements and risk management constraints without exposing detailed position information, trading strategies, or counterparty relationships. This capability is particularly valuable for institutional applications where regulatory compliance must be demonstrated while protecting confidential trading information and competitive advantages.
Regulatory Compliance and Selective Disclosure
Zero-knowledge proof systems are reshaping how organizations approach regulatory compliance by enabling selective disclosure mechanisms that satisfy regulatory requirements without compromising unnecessary privacy or exposing competitive information. Traditional compliance approaches often require comprehensive data disclosure that goes far beyond what regulators actually need to verify compliance, creating privacy risks and competitive disadvantages for compliant organizations.
Anti-money laundering and know-your-customer requirements present complex challenges for privacy-preserving blockchain systems since these regulations typically require detailed transaction monitoring and customer identification procedures. Zero-knowledge compliance systems can prove that appropriate due diligence procedures were followed and suspicious activity monitoring was conducted without revealing specific customer details or transaction patterns that are not relevant to regulatory oversight.
Tax compliance represents another area where zero-knowledge proofs can significantly improve privacy while satisfying regulatory requirements. Taxpayers can generate proofs that demonstrate accurate calculation and payment of tax obligations without revealing detailed financial information that might compromise privacy or business confidentiality. These systems can prove compliance with tax laws while protecting sensitive information about income sources, business relationships, and financial strategies.
Financial institutions operating in multiple jurisdictions face particularly complex compliance challenges since different regulatory frameworks often have conflicting requirements around data disclosure, privacy protection, and cross-border information sharing. Zero-knowledge compliance systems can be designed to satisfy multiple regulatory frameworks simultaneously while minimizing the amount of sensitive information that must be disclosed to any single authority.
The development of standardized zero-knowledge compliance frameworks is enabling broader adoption of privacy-preserving blockchain technologies in regulated industries. These frameworks define common approaches to proving compliance with various regulatory requirements while protecting confidential information, reducing the technical barriers and regulatory uncertainty that have historically limited blockchain adoption in highly regulated sectors.
Performance Optimization and Technical Challenges
The practical deployment of zero-knowledge proof systems in production blockchain environments requires sophisticated optimization techniques to manage the computational, storage, and bandwidth costs associated with proof generation and verification. Performance optimization remains an active area of research and development as the theoretical possibilities of zero-knowledge proofs continue to outpace the practical capabilities of current implementations.
Proof generation optimization focuses on reducing the time and computational resources required to create zero-knowledge proofs for complex statements. Modern proof systems employ various techniques including parallel computation, specialized algorithms for specific problem domains, and hardware acceleration through graphics processing units and specialized cryptographic processors. These optimizations have reduced proof generation times from hours or days to minutes or seconds for many practical applications, though significant computational costs remain for complex statements.
Circuit optimization represents a crucial aspect of zero-knowledge proof performance since the efficiency of proof generation and verification depends heavily on how computational problems are translated into the mathematical representations that proof systems can process. Efficient circuit design requires deep understanding of both the problem domain and the underlying cryptographic protocols, leading to the development of specialized compilers and optimization tools that can automatically generate efficient circuit representations from high-level programming languages.
Batching and aggregation techniques enable zero-knowledge systems to achieve better amortized performance by processing multiple proofs or statements together rather than handling each one individually. These approaches can significantly reduce the per-proof costs in systems that need to handle many similar proofs, though they introduce additional complexity around coordination and timing that must be carefully managed in decentralized environments.
Hardware acceleration is becoming increasingly important for zero-knowledge proof systems as specialized processors designed for cryptographic computations can provide significant performance improvements over general-purpose computing hardware. Field-programmable gate arrays, application-specific integrated circuits, and specialized cryptographic processors are all being explored as ways to make zero-knowledge proof generation more efficient and economically viable for large-scale deployments.
Future Applications and Emerging Use Cases
The expanding capabilities of zero-knowledge proof systems are enabling entirely new categories of applications that were previously impossible or impractical due to the limitations of existing privacy and verification technologies. These emerging use cases demonstrate the transformative potential of zero-knowledge proofs across numerous domains beyond their initial applications in cryptocurrency and blockchain systems.
Verifiable machine learning represents a particularly promising application area where zero-knowledge proofs can prove that machine learning models were trained on specific datasets using particular algorithms without revealing the training data, model parameters, or proprietary algorithmic techniques. This capability is crucial for applications where model transparency is required for regulatory or safety reasons while protecting intellectual property and sensitive training data.
Private voting systems built on zero-knowledge proofs can provide mathematically verifiable elections while protecting voter privacy and preventing coercion or vote buying. These systems can prove that votes were counted correctly and that only eligible voters participated without revealing how individual voters cast their ballots, addressing fundamental tensions between transparency and privacy in democratic processes.
Verifiable computation services enable organizations to outsource sensitive computations to untrusted cloud providers while maintaining confidence in the correctness of results without revealing the input data or computational details. This capability is particularly valuable for scientific computing, financial modeling, and other applications where computational requirements exceed local capabilities but data sensitivity prevents traditional cloud computing approaches.
Privacy-preserving analytics and data science applications can leverage zero-knowledge proofs to generate insights from sensitive datasets without exposing individual records or compromising privacy. Organizations can collaborate on research and analysis projects while protecting confidential information, enabling new forms of data sharing and collaborative research that would be impossible with traditional privacy protection techniques.
Technical Evolution and Research Frontiers
The field of zero-knowledge proofs continues to evolve rapidly as researchers address fundamental limitations and explore new possibilities for privacy-preserving computation and verification. Current research frontiers span theoretical advances in cryptographic protocols, practical improvements in system performance, and novel applications that leverage unique properties of zero-knowledge systems.
Post-quantum security represents a critical research area as quantum computing advances threaten the cryptographic foundations underlying current zero-knowledge proof systems. Researchers are developing new proof systems based on cryptographic primitives that remain secure against quantum attacks, ensuring that zero-knowledge privacy technologies will remain viable as computing capabilities evolve. These post-quantum zero-knowledge systems must maintain the efficiency and practical usability that make current systems viable while providing security against both classical and quantum adversaries.
Recursive proof composition techniques are enabling new architectures where proofs can be composed and aggregated in complex hierarchical structures that support unlimited scalability and modularity. These recursive systems allow for the construction of very large proofs from smaller components, enabling applications that would be impractical with monolithic proof systems while maintaining strong security and privacy guarantees.
Universal proof systems that can handle arbitrary computations without requiring custom setups for each application are simplifying the deployment and maintenance of zero-knowledge applications. These systems reduce the technical barriers to adopting zero-knowledge proofs while improving security by eliminating the need for application-specific trusted setup ceremonies that could introduce vulnerabilities.
Cross-system interoperability research focuses on enabling zero-knowledge proofs generated in one system to be verified in different environments, facilitating integration between various blockchain platforms and traditional computing systems. This interoperability is crucial for enabling complex applications that span multiple systems while maintaining end-to-end privacy and security guarantees.
Economic Models and Tokenization
The economic dynamics surrounding zero-knowledge proof systems are creating new models for value creation, resource allocation, and incentive alignment in decentralized systems. These economic considerations are crucial for understanding how zero-knowledge technologies will scale and evolve as they become more widely adopted across various applications and industries.
Proof generation markets are emerging where specialized service providers offer computational resources for generating zero-knowledge proofs on behalf of users who lack the technical expertise or computational resources to create proofs independently. These markets create economic incentives for investing in specialized hardware and optimizing proof generation processes while making zero-knowledge technologies accessible to users who cannot justify the infrastructure investments required for independent proof generation.
Privacy-as-a-service models are developing where organizations can purchase privacy protection through zero-knowledge proof services without needing to understand or implement the underlying cryptographic protocols. These service models are crucial for mainstream adoption of zero-knowledge technologies since they remove technical barriers while providing predictable cost structures that organizations can incorporate into their operational planning.
Token-based incentive systems are being designed to encourage participation in zero-knowledge networks and compensate participants for providing computational resources, maintaining network infrastructure, and developing improved protocols. Market participants tracking privacy token economics and network incentives understand that these tokenization models must carefully balance incentives for different types of network participants while ensuring long-term sustainability and security.
The integration of zero-knowledge proofs with decentralized finance protocols is creating new financial instruments and services that provide privacy protection while maintaining compatibility with existing DeFi infrastructure. These privacy-enhanced financial services can offer confidential trading, private lending, and anonymous yield farming while proving compliance with relevant regulations and risk management requirements.
Challenges and Limitations
Despite their revolutionary potential, zero-knowledge proof systems face significant challenges and limitations that must be addressed for widespread adoption across various applications and industries. Understanding these limitations is crucial for realistic assessment of when and where zero-knowledge technologies can provide practical solutions to real-world problems.
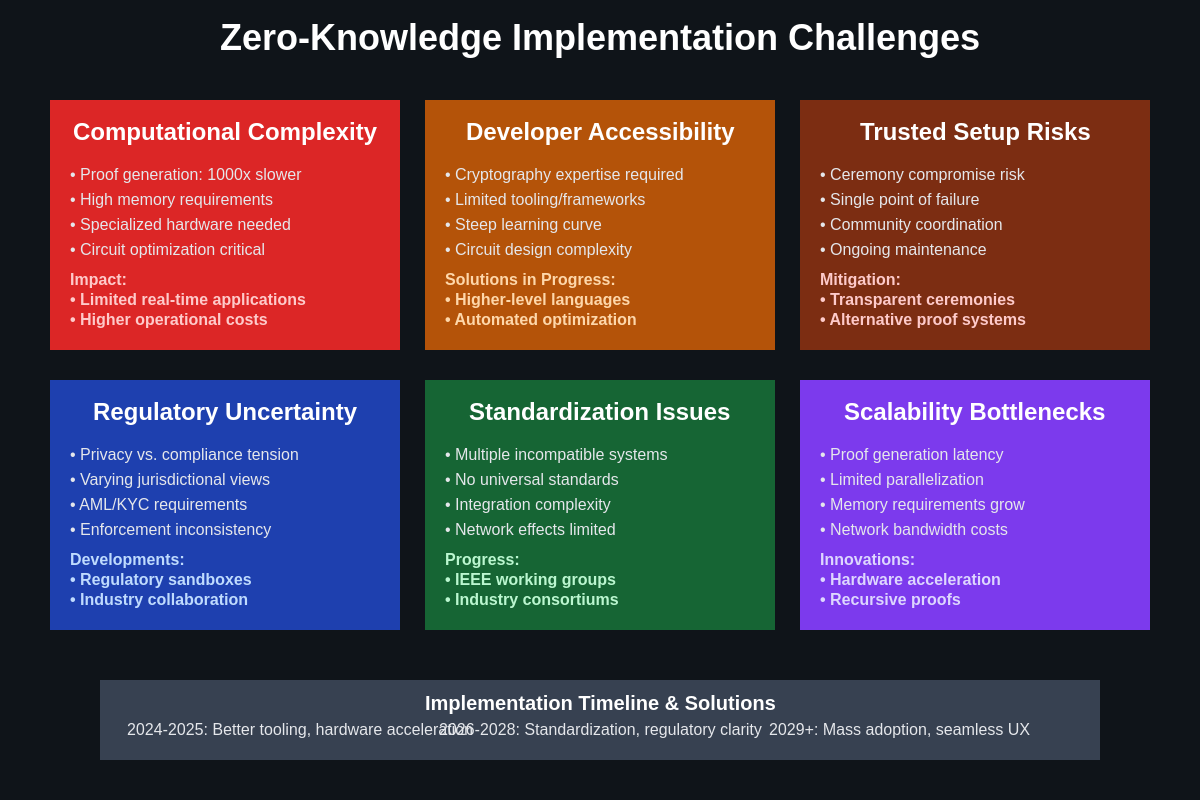
Computational complexity remains one of the most significant barriers to zero-knowledge proof adoption, as proof generation requires substantially more computational resources than traditional cryptographic operations. While verification is typically efficient, the asymmetric cost structure creates economic and practical barriers that limit the types of applications where zero-knowledge proofs are economically viable. Continued research into more efficient proof systems and specialized hardware may address these limitations over time.
Trusted setup requirements in many zero-knowledge proof systems create potential security vulnerabilities and complicate deployment processes. Systems that require trusted setup ceremonies must carefully manage the generation and disposal of secret parameters that could compromise system security if mishandled. While newer proof systems eliminate trusted setup requirements, they often involve trade-offs in proof size or verification efficiency that limit their applicability.
Developer accessibility represents a significant challenge as zero-knowledge proof systems typically require specialized cryptographic knowledge and sophisticated tooling that are not widely available. The complexity of circuit design, proof system selection, and optimization requires expertise that is currently in short supply, creating barriers to adoption and increasing development costs for organizations interested in leveraging zero-knowledge technologies.
Standardization and interoperability challenges arise from the diversity of zero-knowledge proof systems and the lack of widely adopted standards for proof formats, verification procedures, and integration approaches. This fragmentation makes it difficult to build applications that can leverage multiple proof systems or integrate with existing infrastructure, limiting the network effects that could accelerate adoption.
The Path Forward for Privacy-Preserving Blockchain
The future of zero-knowledge proofs in blockchain technology points toward a more nuanced and sophisticated approach to privacy that recognizes the complex trade-offs between transparency, confidentiality, efficiency, and usability. Rather than treating privacy as an all-or-nothing proposition, emerging systems are developing granular privacy controls that allow individuals and organizations to selectively disclose information as needed while protecting sensitive details.
Integration with existing blockchain infrastructure is evolving beyond simple addition of privacy features toward fundamental reimagining of how blockchain systems can balance transparency and confidentiality. Next-generation blockchain platforms are being designed from the ground up to support zero-knowledge proofs efficiently, while existing platforms are incorporating zero-knowledge capabilities through layer 2 solutions and protocol upgrades that maintain backward compatibility.
Regulatory evolution is likely to play a crucial role in shaping the development and adoption of zero-knowledge blockchain technologies as governments and regulatory bodies develop more nuanced approaches to privacy protection that recognize both the benefits and risks of cryptographic privacy techniques. The development of regulatory frameworks that support privacy-preserving technologies while addressing legitimate concerns about illicit activity will be crucial for mainstream adoption.
The convergence of zero-knowledge proofs with other emerging technologies including artificial intelligence, quantum computing, and advanced cryptographic techniques promises to create new possibilities for privacy-preserving computation and verification that extend far beyond current blockchain applications. These technological synergies may enable entirely new categories of applications that leverage the unique properties of zero-knowledge systems in ways that are not yet fully understood or explored.
Professional traders and institutional investors require sophisticated technical analysis tools and market intelligence platforms to navigate the evolving landscape of privacy-focused blockchain technologies and assess the long-term implications of zero-knowledge innovations on digital asset markets, regulatory compliance, and technological development trends.
Disclaimer: This article is for educational and informational purposes only and should not be construed as financial advice. Cryptocurrency investments carry significant risks, including the potential for total loss of capital. The zero-knowledge proof technologies discussed are based on current research and implementations, which may change as the field develops. Always conduct your own research and consult with qualified financial advisors before making investment decisions. The author and publisher are not responsible for any financial losses that may occur from acting on the information provided in this article.